-
CEPM User Guide
-
Preface
-
Cisco Enterprise Policy Manager
-
Overview of the PAP Console
-
Login Page and Home Page
-
Manage Entities
-
Manage Entitlements
-
Auditing and Reporting
-
System Config
-
Delegated Administration
-
Policy Combining Algorithm and Obligation
-
PAP User Login Authentication Using LDAP and SSO
-
Open Source License Acknowledgements
-
Table Of Contents
PAP User Login Authentication Using LDAP and SSO
PAP User Authentication through LDAP
PAP User Authentication through SSO
PAP User Login Authentication Using LDAP and SSO
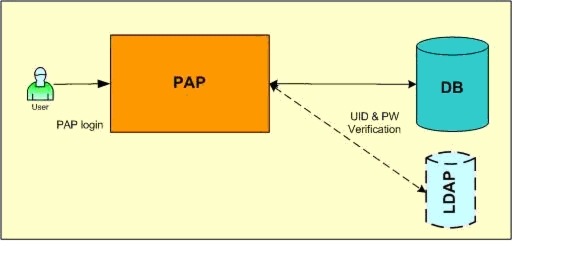
When you log in to CEPM PAP, user authentication is done by verifying the existing user ID and password in the CEPM database. During that process, when a user enters the user ID and password, the CEPM searches the user ID first followed by the password against that User ID.
CEPM supports additional user login authentication through LDAP or single-sign-on (SSO). This is done by updating the pap_config.xml file.
Figure B-1 PAP User Authentication
PAP User Authentication through LDAP
You can enable PAP user authentication through LDAP by updating the <authentication> tag in the pap_config.xml file.
To enable this feature:
1.
Open the pap_config.xml file from /CEPM-V3.3.0.0/config folder. Check the <authentication> tag, in which the authenticationtype= element is set to db by default. (This tag also carries sample authentication properties for LDAP and SSO, which are in commented state. You can uncomment the LDAP properties and update them with the actual values).
Example B-1 Following is a sample <authentication> tag:
<authentication type="ldap" class="net.securent.util.db.LocalLDAPAuthenticator"><properties refer="false" name="default"><property name="ldap-type">SunOne</property><property name="ldapdn">dc=cisco,dc=com</property><property name="userdn">uid=admin,ou=administrators,ou=topologymanagement,o=netscaperoot</proper ty><property name="password" encrypted="false">admin</property><property name="url">ldap://localhost</property><property name="port">389</property><property name="superuser-role">Test</property></properties></authentication>2.
Update the following elements in the <authentication> tag:
•
The authentication type element to ldap and set the class name as net.securent.util.db.LocalLDAPAuthenticator.
•
The refer element to false for authentication from the specified LDAP. If set to true, regardless of the value set in the authenticationtype, the authentication is done from the CEPM database. The name property has no bearing if the refer element is set to false.
•
The ldap-type with the type of LDAP. CEPM supports LDAP types, such as Sun One Server, Novell eDirectory, and Active Directory. For example, if you are using the Active Directory Server, specify the <ldap-type> as AD.
•
The ldapdn property with the required LDAP DN.
•
The userdn in the following format:
Example B-2 For Sun One:
User DN: cn=administrator,cn=users,dc=win2k-ad,dc=win2k-ad,dc= cisco,dc=comExample B-3 For Active Directory:
User DN: uid=admin,ou=administrators,ou=topologymanagement,o=netscaperoot•
For the password property, enter normal password if encrypted is set to false. Else, enter the encrypted password by using the encryption.bat(sh) file. (Refer Chapter 15 of the CEPM Installation and Configuration Guide for more information on generating encrypted password).
•
The <url> tag in the format ldap://host url
•
The <port> tag with the port number of the LDAP URL.
•
The <superuser-role> tag with the name of the superuser.
3.
Save and close the pap_config.xml.
When you start the server, the PAP user authentication is done from the specified LDAP.
PAP User Authentication through SSO
You can enable PAP user authentication through single-sign-on by updating the <authentication> tag in the pap_config.xml file.To do this, you must:
1.
Open the pap_config.xml file from /CEPM-V3.3.0.0/config folder. Check the <authentication> tag, in which the authenticationtype= element is set to db by default. (This tag also carries sample authentication properties for LDAP and SSO, which are in commented state.You can uncomment the LDAP properties and update them with the actual values).
Example B-4 Sample <authentication> tag:
<authentication type="db" class="net.securent.util.db.SSOAuthenticator"><properties refer="true" name="default"><property name="request">sm_user</property></properties></authentication>2.
Update the following elements of the <authentication> tag:
•
The authentication type element to sso and set the class name as net.securent.util.db.SSOAuthenticator.
•
The refer element to false to perform authentication from the SSO. If set to true, regardless whatever value set in the authenticationtype, the authentication is done from the CEPM database. The name property has no bearing if refer element is set to false.
•
The property name to either request or session. If request is set, do not change the attribute value sm_user from where the user name is picked up for authentication. In case of session, you can set your own attribute value.

 Feedback
Feedback