-
CEPM User Guide
-
Preface
-
Cisco Enterprise Policy Manager
-
Overview of the PAP Console
-
Login Page and Home Page
-
Manage Entities
-
Manage Entitlements
-
Auditing and Reporting
-
System Config
-
Delegated Administration
-
Policy Combining Algorithm and Obligation
-
PAP User Login Authentication Using LDAP and SSO
-
Open Source License Acknowledgements
-
Table Of Contents
Entitlement Management by Users
Set attributes to be returned as obligation
Dynamic generation of policy attributes
Entitlement Management by Groups
Policy Combining Algorithm for a Resource
Add attributes to be returned as Obligation
Entitlement Management by Roles
Policy Combining Algorithm for a Resource
Add attributes to be returned as Obligation
Entitlement Management by Resources
Create Policies for a Resource
Policy Combining Algorithm for a Resource
Add attributes to be returned as Obligation
Creating Multiple Policies for a Role Using Map Expression
Importing Policies into PAP from XML File
Exporting Policies from the PAP to XML File
Entitlement Management by Policies
Create Policies by Entity (User, Group, and Role)
Policy Combining Algorithm for a Resource
Add Attributes to be returned as Obligation
Create Multiple Policies for a Role
Policy Combining Algorithm for a Resource
Add attributes to be returned as Obligation
Manage Entitlements
This chapter explains the various operations that you can perform on the Manage Entitlements section in the PAP administration console. You can perform the following activities under this section:
•
By Users—Create user-based entitlement policies.
•
By Group—Create group-based entitlement policies.
•
By Role—Create role-based entitlement policies.
•
By Resource—Create resource-based entitlement policies.
•
By Policy—Create entitlement policies by entities (user, role, group, and so on).
•
Bulk resources to a role—Assign multiple resources to a role.
•
List entitlements—Display a list of all the entitlements for the selected application group/application.
Apart from creating policies you can also perform the following operations in each of the above selection:
•
Set policy combining algorithm and obligations on the resource.
•
Edit policies.
•
Configure simple and complex rules for the policies.
•
Set policy attributes and conditional return of these attributes.
Entitlement Management by Users
This section allows the policy administrator to create user-based entitlements. You can configure exclusive permit or deny policies for a user. For example, if you wish to allow Mary to Account no:0011 exclusively, you can do so by using this feature. Furthermore, to avoid any duplicate user conflict, a rule can be configured on this policy using the available attributes, such as user attributes and resource attributes.
Create Policies for a User
To create policies for a user, you must:
Step 1
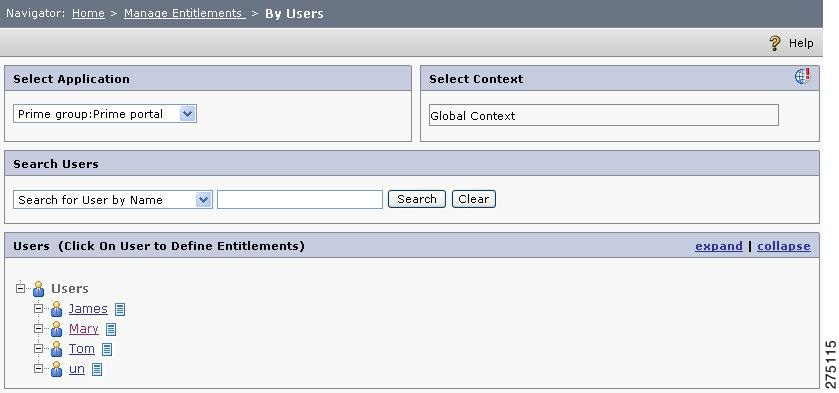
Choose Manage Entitlements > By Users.
The Policy Management By User page is displayed.
Figure 5-1 Manage Entitlement by Users
Step 2
From the Select Application list, select an appropriate application, application group, or Global.
The list of users associated with the selected application, application group, or Global is displayed in the List Users section.
Step 3
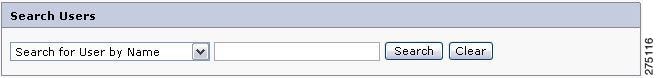
Search for a particular user in the Search section.
Figure 5-2 Search User
This section allows you to search for specific users depending upon the search criteria selected from the list box and the search value entered in the text box. The various search criteria are as follows:
•
Search for user by User Name
•
Search for user by First Name
•
Search for user by Last Name
•
Search for user by Email Id
•
Default
•
User attributes created under the selected application (if any)
Enter the value to search in the text box that is next to the search criteria list. You can also use the asterisk wild card character (*), as part of the search value.
For example, to get a list of all the users having M as the first character in their first name, select the search criteria of Search for User by First Name, enter a search value of M*, and click Search button. The list of users who match the search criteria and search value is displayed in the List Users section.
Click the Clear button to clear the value entered in the search value text box.
Step 4
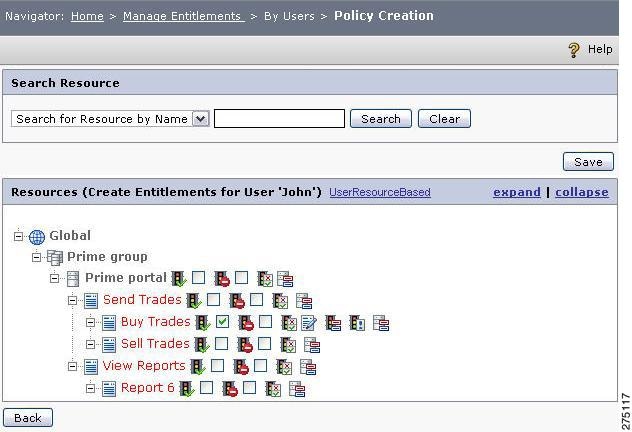
Click the user name link for whom the entitlements are to be created.
A page containing the list of all the resources under the selected application is displayed. You can click the expand link to view all the resources that are in the list.
Figure 5-3 Policy Creation
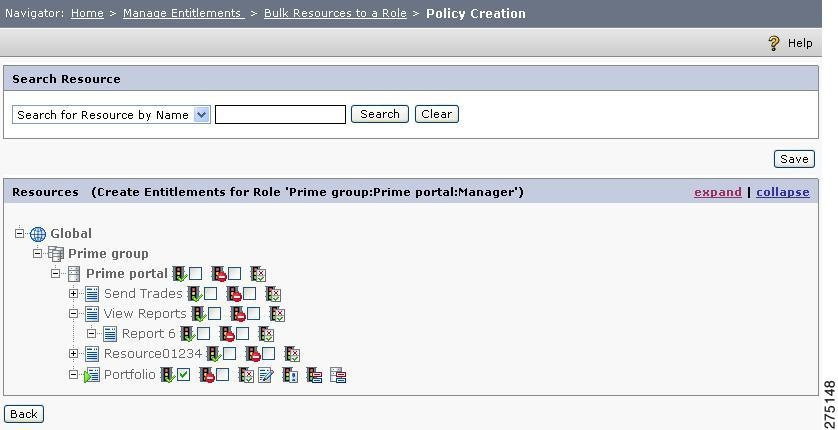
While creating policies, when you expand a tree node and assign few policies by selecting the resource check boxes, ensure that you save the policy creation before expanding the next tree node. Otherwise, you might not find the policy configuration done on the previous node.
You can click the following icons on the Policy Creation page to perform the operations described here:
Note
Three icons, Edit Policy, Policy Attributes on Resource, and Add Rules appear near the resource name after the policy is created on that resource.
Check the check box near the Allow Policy icon for the resource, to assign the Allow policy to the selected user for that resource.
Check the check box near the Deny Policy icon for the resource, to assign the Deny policy to the selected user for that resource.
Click the Policy Combining Algorithm icon to set the policy.
Click the Attributes icon to configure the resource attributes to return.
Click the Edit Policy icon to edit the policy.
Click the Set Policy Attributes on resource icon to configure policy attributes.
Click the Add Rules icon to set rules for this policy.
UserResourceBased
Click this button to go to the Policy Creation page, which is the same as Home > Manage Entities > Users > Assign Resources page. For more information, refer to Assigning Resources to a User, page 4-10.
Policy Combining Algorithm
Refer to Appendix A, "Policy Combining Algorithm and Obligation" for more details about PCA and obligation.
To define the Policy Combining Algorithm and Obligations, you must:
Step 1
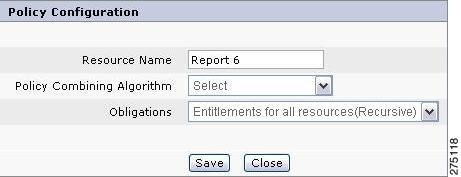
In the resource hierarchy, click the Policy Combining Algorithm icon near the application name or resource name. A pop-up page is displayed.
Step 2
Select the appropriate Policy Combining Algorithm and Obligations from the corresponding list boxes.
Figure 5-4 Policy Combining Algorithm
Step 3
Click Save to save the selected Policy Combining Algorithm and obligations configuration details in the PAP.
Set attributes to be returned as obligation
You can set attributes for an application and for a resource, the values of which can be returned as obligations by the PDP in XACML response after evaluation of the policy. You can select:
•
Application or resource type attributes
•
User or role or group or PIP attributes
The PDP will return all the attributes based on the decision type (allow/deny).
To add attributes for an to be returned for a resource, you must:
Step 1
In the resource hierarchy, click the Attributes icon near the application name or resource name. A pop-up page is displayed that contains three list boxes.
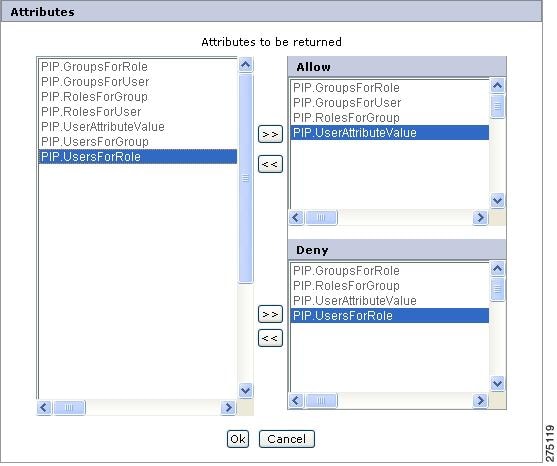
Figure 5-5 Set attributes to be returned as obligation
The list box on the left contains all entity type attributes that you can select to return as part of the PDP response. Based on the decision type, the PDP returns the specified list of attributes as identified in the list boxes (Allow or Deny) on the right. You can add same attributes in both Allow and Deny list box. This means an attribute can be a part of either Allowed response or Denied response or both.
Step 2
To configure an attribute to be returned for Allow policy on the specified resource, check that attribute in the list box on the left side and click the Allowed Response Attributes button (>>) that is near the Allow list box. The selected attribute is moved from the list box on the left side to the Allow list box.
Step 3
To configure an attribute to be returned for Denied policy on the specified resource, select that attribute in the left side list box and click the Denied Response Attributes button (>>) that is near the Deny list box. The selected attribute is moved from the left side list box to the Deny list box.
Step 4
You can unselect the attribute that is selected in the Allow or Deny list to return in the response, by clicking that attribute name and then clicking the Unselect icon (<<). This will unselect the selected attribute and it is moved from the Allow/Deny list to the unselected attributes list on the left side.
Step 5
Click OK to complete the operation of configuring the attributes to be returned as part of the XACML response.
Note
At any point time, if any of the selected attributes participating in this feature is deleted, the entire selection is cleared off. For example, a user type attribute `Age' is selected as one of the attributes to be returned in the `Allow' list box. If this attribute is deleted (in Home > Manage Entities > Entity Types > User Types > List Attributes page), all other attributes listed in both `Allow' and `Deny' list boxes will get deleted. You must reset the attributes to be returned in order to avail the benefits of this feature.
Edit Policy Configurations
You can define a time range with or without modelling a recurring event for the policy by using the Edit Policy button. The policy would be applicable on the resource accordingly. Apart from this, you can also apply `Not Applicable Toggle' on the policy. To edit the policy configurations, follow these steps:
Step 1
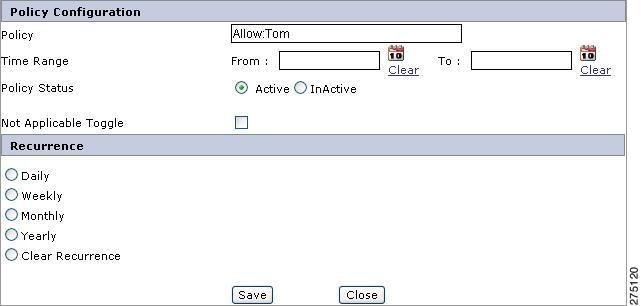
In the resource hierarchy, click the Edit icon near the policy name. A pop-up page containing the following policy information is displayed.
Figure 5-6 Edit Policy Configuration
•
Time Range—For a single instance of recurrence, enter the date and time duration using the calendar icon to restrict the policy to be in effect (active) for the specified time frame.
•
Policy Status—Select Active to activate the policy, otherwise select InActive.In case if the policy status is set to Inactive, it will not evaluate the policy and return Deny.
•
Not Applicable Toggle—This functionality comes into effect when a policy has a rule and that rule evaluates to false. If a resource has an Allow policy and while policy evaluation, the rule configured on that policy returns false, the decision would be "Not Applicable". For example, if Role1 has a Deny policy on View reports and the rule returns false, the decision is to permit. If the Not Applicable Toggle option is checked, then the decision is to deny even if the rule fails.
Similarly, if Role2 has Deny policy on View Reports and the rule returns false, applying the toggle effect, the resultant decision will be "Not Applicable" only if "Not Applicable Toggle" is checked in the "Edit Policy" pop-up window. If this option is unchecked, the decision will be Permit.
•
Recurrence—For multiple instances of recurrence, you can model the recurrence relationship for these settings in order to avail the same entitlements to the selected user (to whom you have delegated your entitlements) on every recurrence period.
Note
The recurrence period is in effect unless and until anything contrary to it is defined. You can also disable recurrence by selecting Clear Recurrence from this list.
The following recurrence period can be defined for this purpose:
•
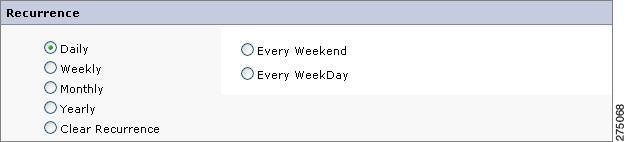
Daily—This enables the recurrence of the copied entitlements on daily basis. Either you can assign your entitlements to the copied user every weekday or only on the weekends by selecting the corresponding option.
Figure 5-7 Recurrence-Daily
•
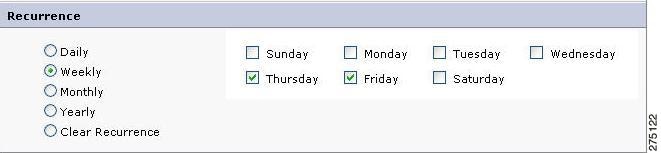
Weekly—If the From Time and To Time falls within the same week and Weekly is selected, the copy entitlement is in effect on a weekly basis on the defined recurrence time period.
Figure 5-8 Recurrence-Weekly
You can select multiple days of a week on which the copied user can utilize your entitlements.
•
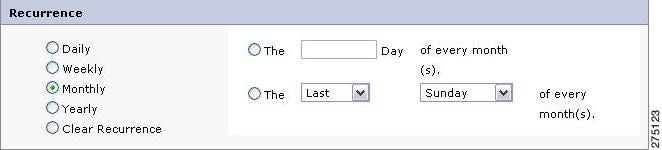
Monthly—You can set the recurrence of the copy entitlement on monthly basis in the following ways:
Figure 5-9 Recurrence-Monthly
–
You can set the monthly recurrence period to a particular day of every month. To do this you must select the first option and enter a number (in between 1 and 31) on which all your entitlements are available for the copied user.
–
You can select first/second/third/fourth/last day (Monday to Sunday) of the month for recurrence of the copied entitlements.
•
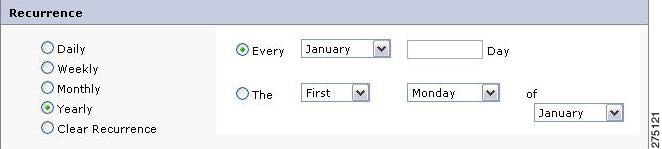
Yearly: You can set the recurrence of the copy entitlement on a yearly basis.
Figure 5-10 Recurrence-Yearly
This is similar to the monthly recurrence period with an additional option of selecting the month so that the copied entitlements is in force on the specified days of the every month.
•
Clear Recurrence: When you click this option and save the setting, the recurrence of copy entitlement is terminated.
Note
If you do not specify the Time Range and set the Recurrence to any (Daily/Weekly/Monthly/Yearly), it will execute the policy and give decisions on the set recurrence only. For example, consider a policy, Allow:Test with recurrence set to Daily > Every Weekend. When you execute this policy every weekend, the decision would be to allow permission and when you execute this policy on weekdays, the decision would be to deny permission.
Step 2
Click Save to save the above configurations into PAP.
Set Policy Attributes
After a policy is created, you can set attributes on the policy by clicking the `Set Policy Attributes' icon of the selected policy. These attribute values are returned by the PDP in XACML response after evaluating the policy. You also have an option to select or deselect default attributes to be returned on the specified resource along with these policy attributes. In addition to this, you can also set rule for conditional return of these attributes. The PDP will return these attributes only if the rules configured evaluates to true.
Note
It is important to note that the rules configured in this section is different from the rules created on the policy.
To create policy attributes, follow these steps:
Step 1
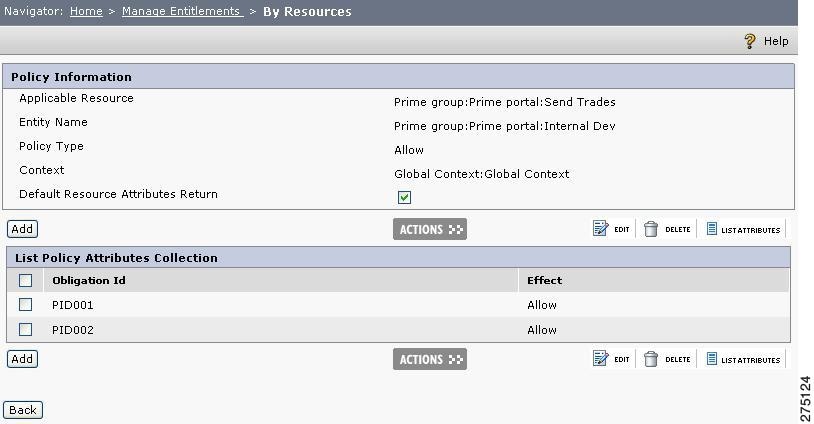
In the resource hierarchy, click the Set Policy Attributes icon near the policy name. The Policy Attributes page is displayed.
Figure 5-11 Set Policy Attributes By Resources
Resource page contains policy information, such as applicable resource, entity name, policy type, and context. The `Default Resource Attributes Return' option is checked by default. This means the resource type attributes created on the specified resource are returned along with the attributes created on the policy. If unchecked, only the policy attributes are returned.
You can also add one or more policy attributes collections. To add a policy attribute collection:
Step 1
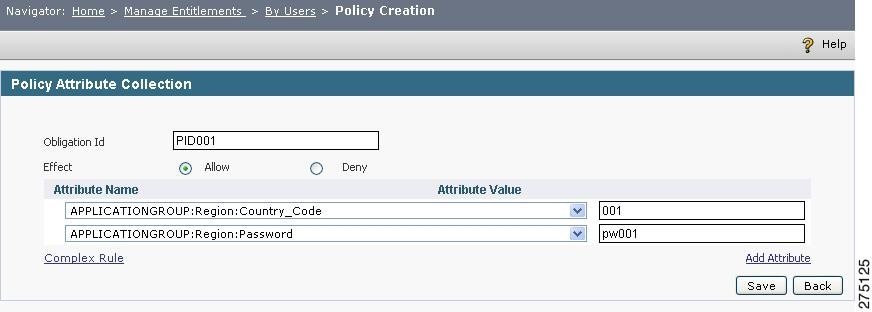
Click the Add button. The Policy Attribute Collection page appears.
Figure 5-12 Policy Attribute Collection
Step 2
Enter the Obligation ID.
Step 3
Select the appropriate Effect. If you select Allow, the specified policy attributes are returned when the policy is evaluated as Allow. Similarly, if Deny is selected, the attributes are returned when the policy is evaluated to Deny.
Step 4
Select an attribute from the Attribute Name drop-down. This drop-down contains all existing attributes created under the application. Enter the value for the attribute selected in the previous step in the Attribute Value field.
Step 5
Click Add Attribute link to add more attribute key-value pairs under the selected obligation ID.
Step 6
You can save the policy attribute collection with or without configuring a rule on it. If a rule is configured the policy attributes are returned only if the rule is satisfied. This is also called conditional return of attributes. The procedure for creating a rule is the same as inthe case of creating a rule on a policy such as configuring simple and complex rules. Finally a complex rule that will be evaluated for conditional return of attributes. Refer Add Rules to a Policy, page 5-11 . For information on how to create rule. After configuring the complex rule and selecting the appropriate Simple Association, click Set Rule. This takes you back to the Policy Attributes Collection page.
Step 7
Click Save.
Dynamic generation of policy attributes
Policy attributes can be dynamically generated and CEPM allows specific syntax for the definition of a policy attribute that is dynamically generated. A policy attribute value might contain strings of the form {s} - note '{' and '}', where 's' is one of the following -
1.
the strings, "subject-id" or "resource-id" or "action-id". For example, the attribute value can be "{subject-id}", without quotes in which case, the policy attribute value is the attribute value for 'urn:oasis:names:tc:xacml:1.0:subject:subject-id' in the XACML request. The "resource-id" and "action-id" follow the same syntax.
2.
the pattern, "x-attribute=y z", where 'x' is one of the strings, "subject", "resource", "action", "message" and 'y' is the attribute identifier value from the XACML request. 'z' is key-value pair of comma separated properties that are used to further qualify the identification of the attribute value.
For example, policy attribute value can be "{subject-attribute=urn:cisco:uc:1.0:employee-record xpath=//Employee/Name/text()}". In this case, 'urn:cisco:uc:1.0:employee-record' is an attribute with XML attribute value in the XACML request shown below -
<Request>...<Subject..><Attribute AttributeId="urn:cisco:uc:1.0:employee-record" Datatype="..#string"><AttributeValue><Employee><Name>Sam</Name></Employee></AttributeValue></Attribute>...</Subject>...</Request>The key-value pair, "xpath=//Employee/Name/text()", qualifies the policy attribute further to be the value "Sam".
3.
the pattern "x z", where 'x' is a PIP attribute reference (an FQN) and 'z' is comma separated list of one of (1), (2) or a constant string.
For example, a policy attribute value can be "{JavaPIP.beginsWith {subject-attribute=urn:cisco:uc:1.0:employee-record xpath=//Employee/Name/text()} Sa}"
In this case, a Java PIP attribute, namely 'JavaPIP.beginsWith', is passed the parameters '{subject-attribute=urn:cisco:uc:1.0:employee-record xpath=//Employee/Name/text()}' and 'Sa'. The return value of the Java PIP is the policy attribute value.
Example of a policy attribute:
<cixml version="1.0"><example>{JavaPIP.beginsWith {subject-attribute=urn:cisco:uc:1.0:employee-record xpath=//Employee/Name/text()} Sa}</example></cixml>- which evaluates to
<cixml version="1.0"><example>true</example></cixml>- where the Java PIP returns "true" for the example in clause (3) above.
Add Rules to a Policy
Rules provide a finer level of authorization while evaluating a policy. A policy can be configured for executing more than one rule. In CEPM, rules are of two types, simple and complex.
A simple rule comprises one or more conditions that are composed by LHS(Left Hand Side) and RHS (Right Hand Side) expressions using—in, not in, equal to, not equal to, greater than, less than, greater than or equal to, lesser than or equal to functions and match operators. LHS and RHS contain attributes from the XACML request context, PIP attributes, and XPath references over request context.
Regular expression comparison can be done in a rule definition. For example, if the UserID of Mary is US 009, you can configure a rule, such as "User-ID"—"matches"—[a-z]* [0-9]*.
A complex does multiple simple rules built together into one by the conjunctions - AND and OR. The simple rule does not get evaluated unless and otherwise it is associated with a complex rule. Irrespective of the number of complex rules configured for a policy, the evaluation is done on the basis of only one complex rule validation that is selected as the simple association in the Rules Creation page.
To add rules to a policy:
Step 1
Click Set Rules button of the policy on the rules to be created. This page contains three sections - Policy Information, Complex Rules, and Association Rules to Policy.
Step 2
Click the Simple Rules link located in the Policy Configuration section.
Step 3
Enter the name of the rule.
Step 4
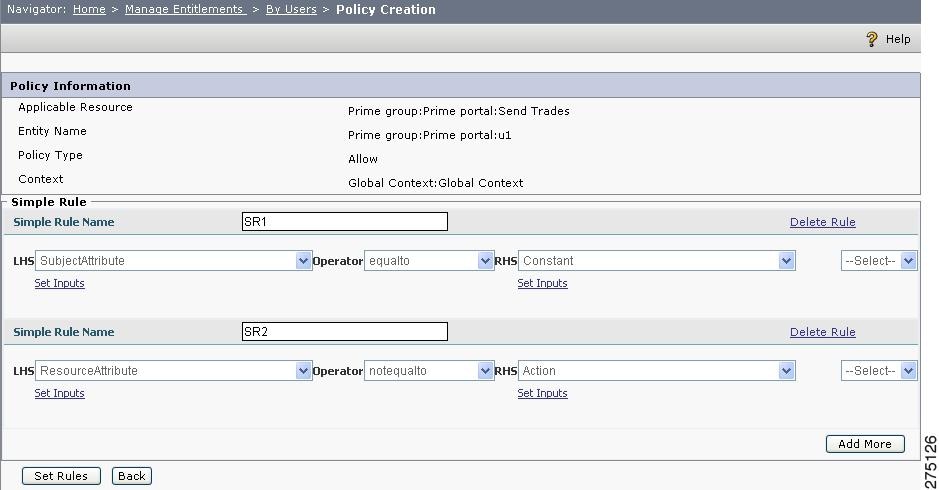
Select the LHS and RHS parameters along with the necessary operator. Consider the following example, where two simple rules called SR1 and SR2 are defined. Each condition has an LHS value, an operator, and an RHS value.
Note
RHS—This is an enterable as well as selectable list box.You can enter the value for the condition to check. If you select a particular attribute type (Resource attribute, Subject attribute, Message attribute, or Action attribute), you need to specify the attribute name by clicking the Set Inputs link, which opens a pop-up page, where you can enter the appropriate attribute name.You can set your own inputs for LHS and RHS. For example, if you want to define your own rule "subject equal to Mary", then select the subject in the LHS, Equal to as the operator, and click Select in the RHS, and enter Mary. Then this rule might look like:
Example of a simple rule:
LHS value = Subject_attribute, Operator = equals to, RHS = ConstantMultiple simple rules can be configured and joined together using AND and OR operators.
The Figure 5-13Add Rules to Policy describes a simple rule configuration in the PAP.
Figure 5-13 Add Rules to Policy
Step 5
Click Set Rules after the simple rules are created. The Policy creation page is displayed.
Step 6
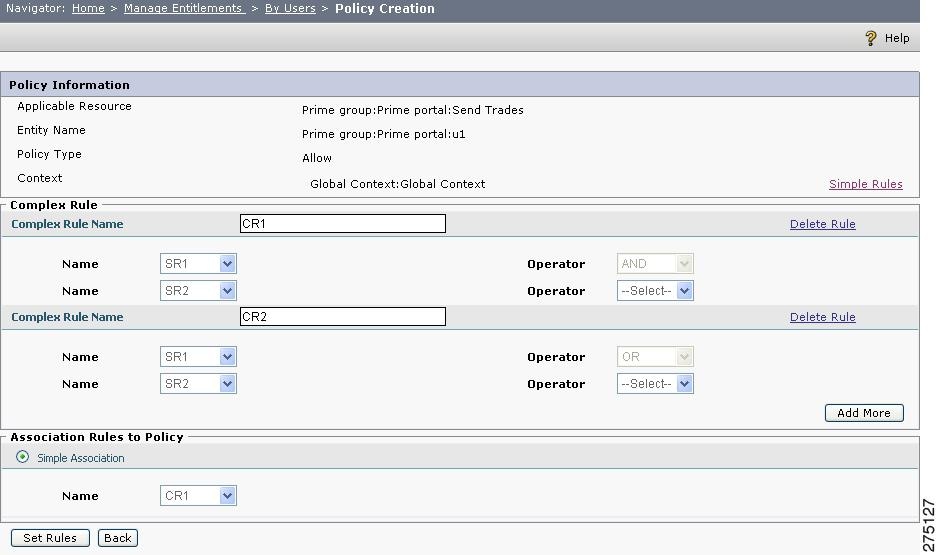
Compose complex rules using the already configured simple rules and complex rules using AND or OR operators.
While creating a complex rule, the Name list box contains all simple rules and complex rules existing under the selected application. These include simple and complex rules configured while creating dynamic roles (groups), rules configured for conditional return of attributes, and rules created on any other policies under the application.
Step 7
After creating the required number of complex rules, move into Association Rules to Policy section in the same page and check the simple association check box and select a complex rule from the Name list box.
See Figure 5-14Complex Rule or a sample complex rule:
Figure 5-14 Complex Rule
I
InFigure 5-14Complex Rule the complex rule CR1 is selected as the final rule to be associated with the policy and the condition becomes, in the PEP request, check if the `Subject_attribute is equal to Constant' and `Resourcetype is not equal to Action'. If both the conditions are satisfied, then Allow access to this resource to the requesting user. If not, then Deny access to this resource to the requesting user.
Rules can be Shared or Reused
Rules are reusable and can be referenced by more than one policy. You can create generic or shared rules that can be used in multiple policies. This feature restrains the policy administrator from creating duplicate rules manually in each policy and keeps them in sync if the rules are changed. Any change in the base rule will updates all the associated policies.
For example, if a rule called R1 is created in a policy called P1 and reused in another policy P2, any change in R1 updates both P1 and P2.
Similarly, any existing rule can be referenced by another rule, and again that rule is referenced by another. For example, a rule R1 is created in policy P1. In policy P2 a rule called R2 is created which references R1. Furthermore, in another policy P3, a rule R3 is created which references R2.
P1 --> R1
P2 --> R2 --> references R1
P3 --> R3 --> references R2
Any change in R1 updates P1, P2, and P3.
Rule Deletion:
Deletion of a rule has a cascading effect on all complex rules and referenced rules where the deleted rule has been reused or shared. If any of the rules, whether it is a simple rule or a complex rule is deleted, a warning message is displayed that cautions you about its impact over the reused and referenced rules.
For example, if there are two simple rules SR1 and SR2 and two complex rules CR1 and CR2 are configured using these simple rules in the following manner:
CR1 --> SR1 AND SR2
CR2 --> CR1 OR SR2
- If SR1 is deleted, it has a cascading effect, and both CR1 and CR2 are deleted.
- If SR2 is deleted, both CR1 and CR2 are deleted.
- If CR1 is deleted, only CR2 is deleted, but not SR1 and SR2.
- If CR2 is deleted, it has no impact on the remaining rules.
Entitlement Management by Groups
This section is used to create policies for groups, edit policies, configure Policy Combining Algorithm and obligations, add attributes to return, add policy attributes, and configure rules for policies.
Create Policies for a Group
To create entitlements for a group, you must:
Step 1
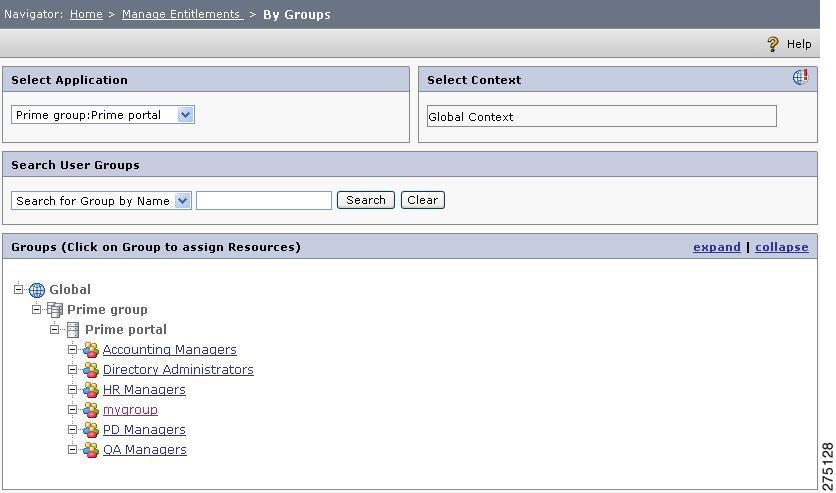
Choose Manage Entitlements > By Groups.
The Policy Management By Group page is displayed.
Figure 5-15 Manage Entitlement by Group
Step 2
From the Select Application list, select an appropriate application, application group, or Global.
The list of groups associated with the selected application, application group, or Global is displayed in the List Groups section in the same page. You can click the expand link to view all the groups that are in the list.
Step 3
Search for a particular group in the Search section.
Figure 5-16 Search Group
Enter the value to search in the text box. You can also use the asterisk wild card character (*), as part of the search value.
For example, to get a list of all the groups having M as the first character in their name, enter a search value of M*, and click Search. The list of groups that have M as the first character in their names are displayed in the List Groups section. Click Clear to clear the value entered in the search value field.
Step 4
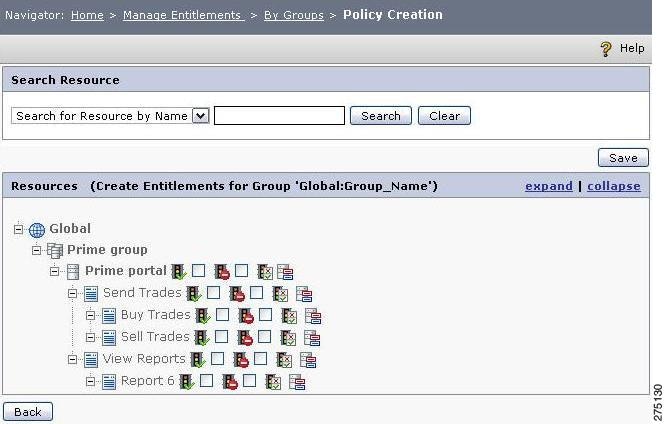
Click the group name link of the group for whom the entitlements are to be created.
A page that contains a list of all the resources under the selected application, application group, or Global is displayed. You can click the expand link to view all the resources that are in the list.
Figure 5-17 Poilicy creation by groups
Step 5
To create the Allow/Deny policy, check the appropriate check box, Allow or Deny that is next to that resource name, and click Save.
The policy for the selected group and selected resources gets created.
You can click the icons described in NoteThe icons appear next to the resource name only after you select one of the check boxes, Allow or Deny, that are next to that resource name and click Save. to perform the operations described here:
Note
The icons appear next to the resource name only after you select one of the check boxes, Allow or Deny, that are next to that resource name and click Save.
Policy Combining Algorithm for a Resource
Refer to Policy Combining Algorithm, page 5-4.
Add attributes to be returned as Obligation
Refer to Set attributes to be returned as obligation, page 5-5.
Edit Policy Configurations
Refer to Edit Policy Configurations, page 5-6.
Set Policy Attributes
Refer to Set Policy Attributes, page 5-8.
Add Rules to a Policy
Refer to Add Rules to a Policy, page 5-11.
Entitlement Management by Roles
This section describes the following functionalities provided by the PAP.
•
Create policies for roles
•
Edit policies
•
Configure Policy Combining Algorithm and obligations
•
Add attributes to return
•
Add policy attributes
•
Configure rules for policies
Create Policies for a Role
To create entitlements for a role, you must:
Step 1
Choose Manage Entitlements > By Roles.
The Policy Management By Role page is displayed.
Figure 5-18 Manage Entitlement by Roles
Step 2
From the Select Application list, select an appropriate application, application group, or Global.
Step 3
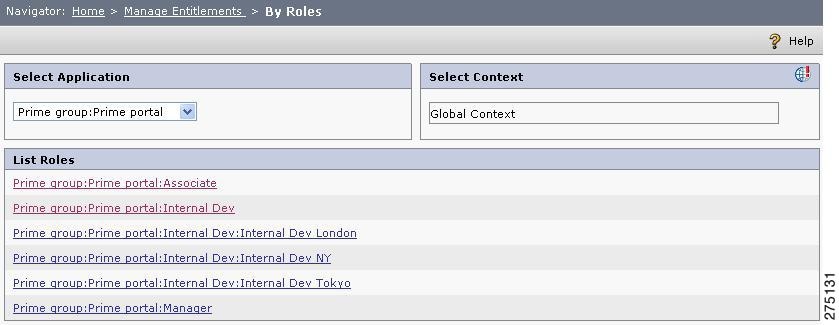
Assign a context for the role-resource association that you are going to create by clicking the Context icon. A list of contexts is displayed. Select the appropriate context from the list.
The list of roles associated with the selected application, application group, or Global is displayed in the List Roles section.
Step 4
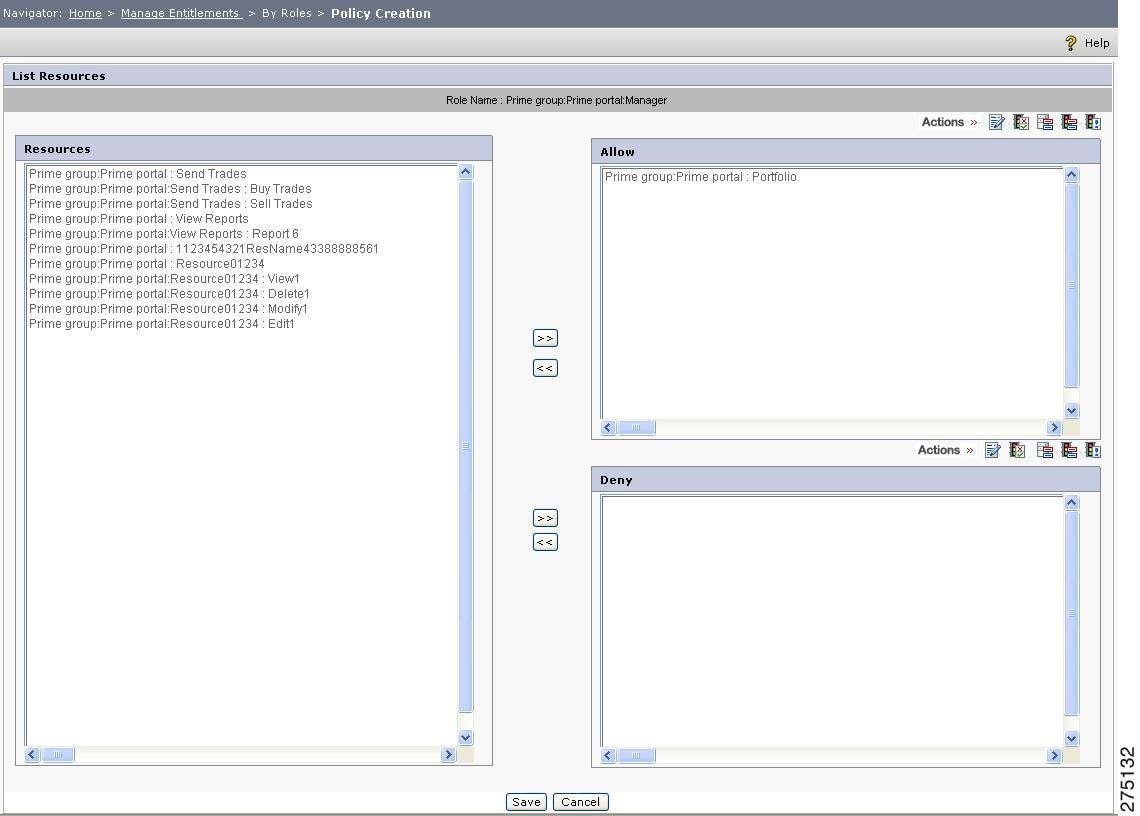
Click the role name link for the role for whom the entitlements are to be created.
A page that contains a list of all the resources under the selected application, application group, or Global is displayed in the resources list.
Figure 5-19 Assign Roles
The page contains three list boxes. The Resources list box contains the resources that are not assigned to the role. On the right side, the Allow and Deny list boxes contain the resources that are assigned to the role, with the Allowed permission and Denied permission respectively.
Step 5
To assign a resource to the role with Allowed permission, select that resource in the Resources list box and click the Assign Allow icon. The selected resource is moved from the Resources list to the Allow list.
Step 6
To assign a resource to the role with Denied permission, select that resource in the Resources list box and click the Assign Deny icon. The selected resource is moved from the Resources list to the Deny list.
Step 7
To unassign the assigned resources in the Allow or Deny list box, click the resource name and click the Unassign icon. The selected resource is unassigned and is moved from the Allow or Deny list to the Resources list.
Step 8
For the role-resource association, you can also assign rules, configure Policy Combining Algorithm, set attributes to return, and set policy attributes. You can also edit the existing policy.
Select the assigned resource and click the appropraite icon next to the action label as described in Table 5-2Resourece Icons:
Step 9
Click OK to complete the role-based policy creation.
Policy Combining Algorithm for a Resource
Refer to Policy Combining Algorithm, page 5-4 .
Add attributes to be returned as Obligation
Refer to Set attributes to be returned as obligation, page 5-5.
Edit Policy Configurations
Refer to Edit Policy Configurations, page 5-6.
Set Policy Attributes
Refer to Set Policy Attributes, page 5-8.
Add Rules to a Policy
Refer to Add Rules to a Policy, page 5-11.
Entitlement Management by Resources
This section describes the following functionalities provided by PAP.
•
Create policies for resource
•
Edit policy
•
Configure Policy Combining Algorithm and obligations
•
Add attributes to return
•
Add policy attributes
•
Configure rules for policies.
Create Policies for a Resource
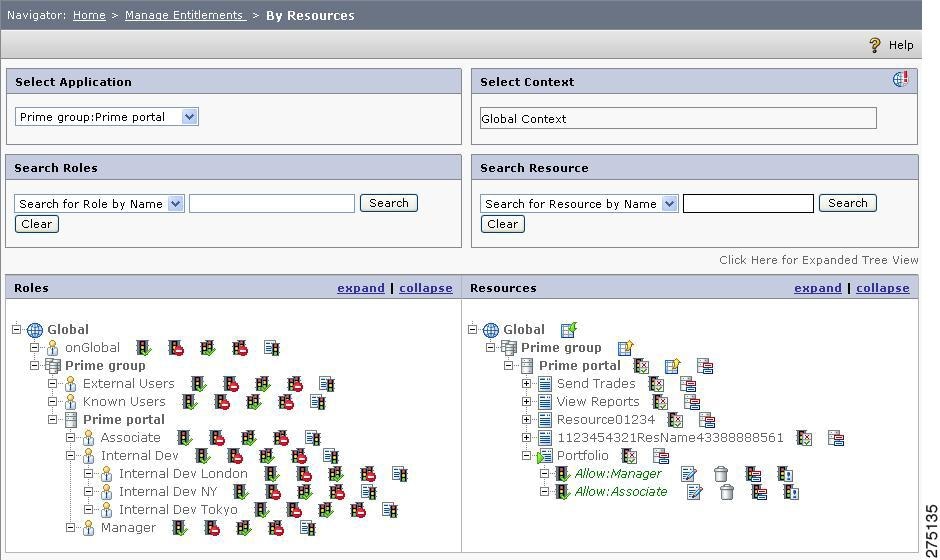
To create entitlements by resource (basically it is a role-based policy creation), you must:
Step 1
Choose Manage Entitlements > By Resource.
The Policy Management by Resource page is displayed.
Figure 5-20 Manage Entitlement by Resources
Step 2
From the Select Application list, select an appropriate application, application group, or Global.
Step 3
Assign a context for the role-resource association that you are going to create by clicking the Context icon. A list of contexts is displayed. Select the appropriate context from the list to apply the context to the role-resource association.
A list of roles and resources is displayed side-by-side. You can click the expand link in the upper right corner of the list boxes to view all the roles and resources pertaining to the selected application group/application.
Step 4
To search for a particular role or resource by name in this page, enter the appropriate search value in the Search section. You can use the asterisk (*) wild card character while searching a particular role and resource by name.
Figure 5-21 Search Resources
The Table 5-3Expected outcomes for search option lists the sample search parameters and the expected outcomes of the search options
Table 5-3 Expected outcomes for search option
Step 5
To create Allow policy, double-click the Map Allow Policy button next to the role name for which you want to create the Allow policy for a particular resource. A blue label
is displayed next to the cursor and moves with the cursor.
To create Deny policy, double-click the Map Deny Policy button next to the role name for which you want to create the Deny policy for a particular resource. A blue label
is displayed next to the cursor and moves with the cursor.
Step 6
Click the resource name for which the policy is to be created. The policy is created under the selected resource. Policy name has the following format.
For Allow policy: Allow:[Role for which this policy is created]
For Deny policy: Deny:[Role for which this policy is created]
Figure 5-22Role-Resource mapping shows the sample Allow policy created by the Internal Dev role over the Report 6 resource.
Figure 5-22 Role-Resource mapping
Step 7
For this role-resource association, you can also assign rules, configure Policy Combining Algorithm, set attributes to return, set policy attributes, and revoke policy. You can also edit the existing policy.
To do this, you must select the appropriate icon next to the resource name for which the policy is created or select the icons next to the policy name, as explained .
Policy Combining Algorithm for a Resource
Refer to Policy Combining Algorithm, page 5-4 .
Add attributes to be returned as Obligation
Refer to Set attributes to be returned as obligation, page 5-5.
Edit Policy Configurations
Refer to Edit Policy Configurations, page 5-6.
Set Policy Attributes
Refer to Set Policy Attributes, page 5-8.
Add Rules to a Policy
Refer to Add Rules to a Policy, page 5-11.
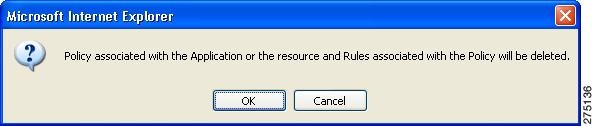
Revoke a Policy
To revoke a policy, you must:
Step 1
Click the Revoke Policy icon that is next to the policy name. You are asked to confirm deleting/revoking the selected policy.
Figure 5-23 Revoke Policy
Step 2
Click OK to delete/revoke the selected policy. Otherwise click Cancel.
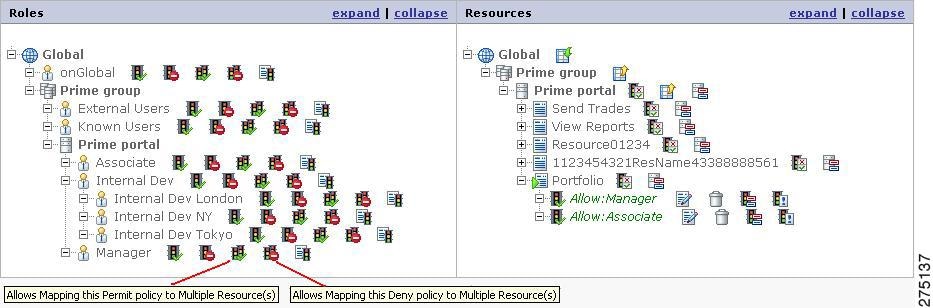
Creating Multiple Policies for a Role Using Map Expression
You can create multiple policies (Allow or Deny) for a role by executing a single map expression. This eliminates the need to create policies repeatedly for a single role for multiple resources in the resource hierarchy.
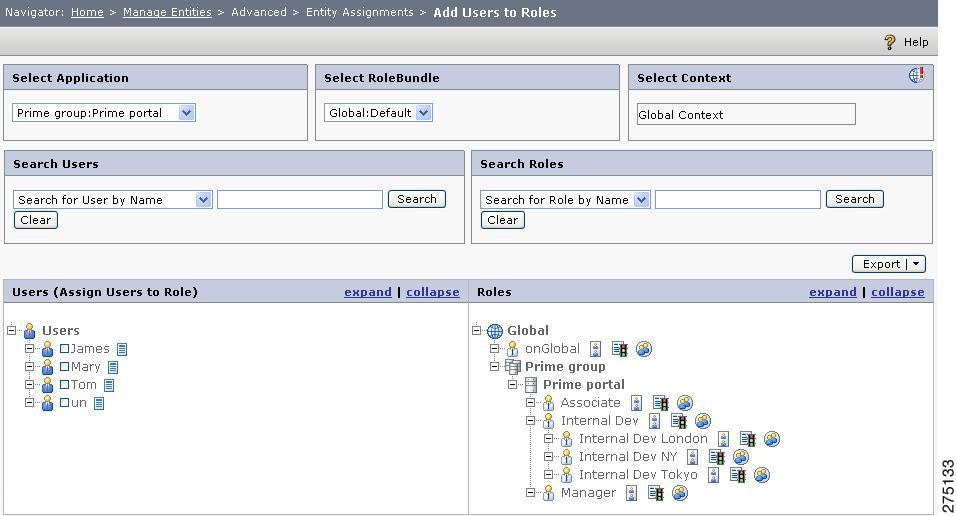
To create policies using the map expression for a role, you must::
Step 1
In Policy Management By Resource page (Manage Entitlements > By Resource), search for the role for which multiple policies using map expression are to be created.
Figure 5-24 Multiple policies for a role using map expression
Step 2
To define a map expression for creating Allow policies, click the icon that is next to the role name for which you want to create multiple Allow policies. To define a map expression for creating Deny policies, click the icon.
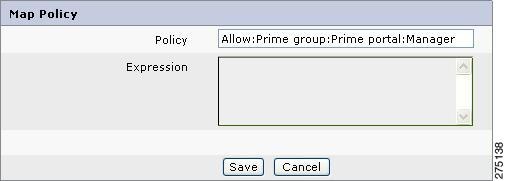
A pop-up page is displayed where you can enter the policy creation expression. Figure 5-25Map Policy shows the sample Allow Policy Map Expression page.
Figure 5-25 Map Policy
Examples of a map expressions:
Example 5-2 Consider the Allow Expression value, Prime group:Prime portal:*, configured for Role1. This results in the creation of Allow: Role1 policies for all the resources and their child resources under the Prime portal application.
Example 5-3 Consider the Allow Expression value, Prime group:Prime portal:*:Report 6, configured for Role1. This results in the creation of Allow: Role1 policies for all the resources having the name Report 6. Here, * refer to all resources.
Example 5-4 Consider the Allow Expression value, Send Trades:#:Report 1, configured for Role1. Note that only resource names can be mentioned before and after #. This results in the creation of Allow: Role1 policies for the immediate level of the given resources, that is, all subresources with the name Report 1 under the resource Send Trades.
Step 3
After configuring the required map expression, click Save. This creates the Allow/Deny policies for the selected role for the specified resources.
Importing Policies into PAP from XML File
The PAP provides the functionality to import policies from an XML file into an application in the PAP. If the PAP and PDP are the non-shared mode and communicate via JMS, the imported data is not synchronized unless and until a PDP is associated with that application.
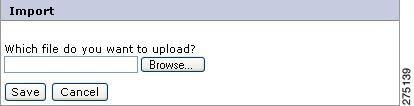
To import the policies into the PAP, you must:
Step 1
In Policy Management By Resource page (Manage Entitlements > By Resource), in the Resources list section, click the Import icon next to Global.
A pop-up page is displayed where you can select the XML file that contains the policies to be imported.
Figure 5-26 Import using XML file
Step 2
Click Save. The policies in the XML file are created in the PAP.
Exporting Policies from the PAP to XML File
The PAP provides the functionality to export policies from the PAP application or application group to an XML file.
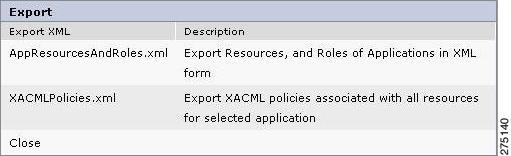
To export the policies from the PAP, you must:
Step 1
In Policy Management By Resource page (Manage Entitlements > By Resource), in the Resources list section, click the Export icon next to the application group or application for which the policies need to be exported to an XML file.
A pop-up page is displayed where you can click any of the following links to save the appropriate information in the XML file.
Figure 5-27 Export using XML file
•
AppResourcesAndRoles.xml—Click this link to export the resources and roles of the selected application group or application to the XML file.
•
XACMLPolicies.xml—Click this link to export the XACML policies associated with all resources for the selected application group or application to the XML file.
Step 2
Click Close when you are done with the export process.
View Entitlements for a Role
The PAP provides the functionality to display the entitlements for a role.
To view all the entitlements for a role, you must:
Step 1
In Policy Management By Resource page (Manage Entitlements > By Resource), search for the role for which you want to view the entitlements.
Step 2
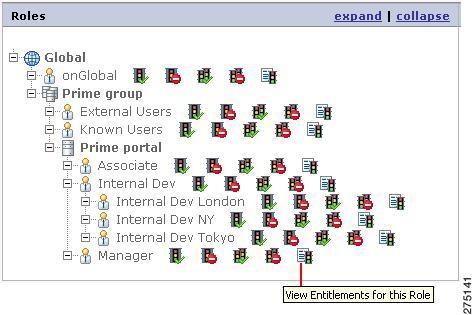
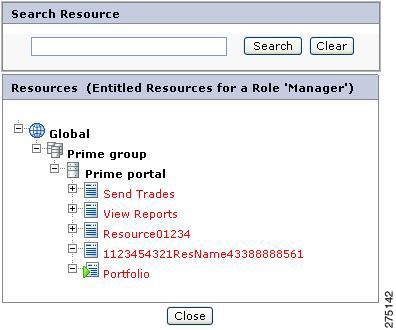
Click the View Entitlements for Role icon which is next to the role name, for which you want to view the entitlements.
Figure 5-28 View Entitlement for Role
The Allowed Resource page is displayed, which contains a list of all the resources in the selected application group, or application.
Figure 5-29 Allowed Resource
All permissible resources (having Allowed permission) within the Resource list are shown in green while the remaining resources (having Denied permission) are shown in red.
Entitlement Management by Policies
This section describes the following functionalities provided by the PAP:
•
Create policies for entities such as users, groups, and roles at a single place
•
Edit policies
•
Configure Policy Combining Algorithm and obligations
•
Add Attributes to return
•
Add Policy attributes
•
Configure rules for policies
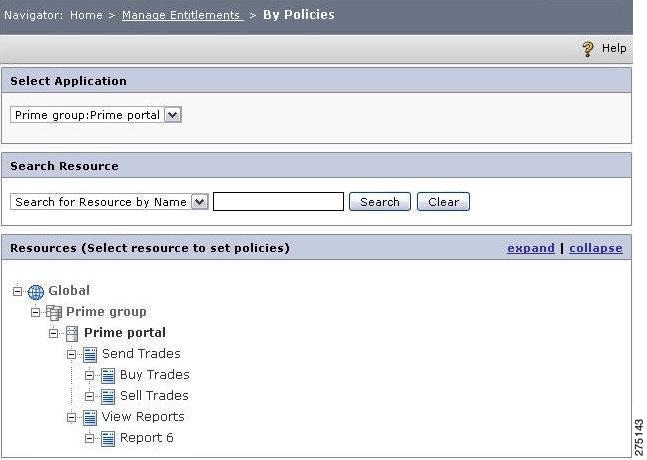
Create Policies by Entity (User, Group, and Role)
The PAP provides the functionality to create policies for users, groups, and roles in a single place.
To create a policy for any of these entities (users, groups, and roles) in a single place, you must:
Step 1
Choose Manage Entitlements > By Policies.
The Policy Management By Policies page is displayed.
Figure 5-30 Manage Entitlement by Policies
Step 2
From the Select Application list, select an appropriate application or application group.
The list of resources associated with the above selected application/application group is displayed in the List Resources section. You can click the expand link to view all the resources that are in the list.
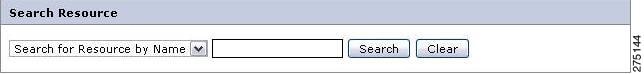
Step 3
Search for a particular resource in the Search section.
Figure 5-31 Search Resources
Enter the value to search in the text box. You can also use the asterisk (*) wild card character, as part of the search value.
For example, to get the list of all the resources having M as the first character in their name, enter a search value of M*, and click Search. A list of resources that have M as the first character in their name is displayed in the List Resources section.
Click Clear to clear the value entered in the search value field.
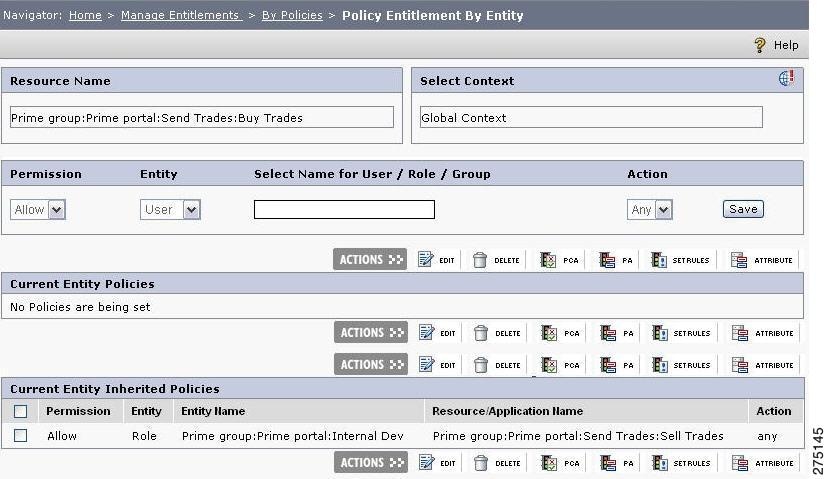
Step 4
Click the resource name link for the resource for whom the entitlements are to be created. The Policy Entitlement By Entity page is displayed. The page displays a list of all the policies for all the users, groups, and roles for the selected resource.
Figure 5-32 Policy Entitlement by Entity
Step 5
You can update the existing policy by checking the check box that is next to policy permission (Allow/Deny). You can click any of the icons decsribed in Table 5-5Policy icons:
Step 6
To create a new policy on this page for a user, group, or role for the selected resource, you must:
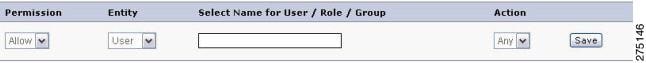
Figure 5-33 New Policy
a.
Select an appropriate context for the policy by clicking the Context icon. A list of contexts is displayed. Select the appropriate context from the list.
b.
Select an appropriate permission for the policy, Allow/Deny.
c.
Select the entity for which the policy is to be created—user/group/role.
d.
Enter the name for the selected entity, that is, name of the user (Mary), name of the group (Systems Group), or name of the role (Internal Dev).
e.
Select the appropriate action of the selected resource for which the policy is to be created.
f.
Click Save. The new policy with this information gets created.
Policy Combining Algorithm for a Resource
Refer to Policy Combining Algorithm, page 5-4 .
Add Attributes to be returned as Obligation
Refer to Set attributes to be returned as obligation, page 5-5.
Edit Policy Configurations
Refer to Edit Policy Configurations, page 5-6.
Set Policy Attributes
Refer to Set Policy Attributes, page 5-8.
Add Rules to a Policy
Refer to Add Rules to a Policy, page 5-11.
Add Bulk Resources to a Role
This section describes the following functionalities provided by the PAP.
•
Create policies for roles in bulk
•
Edit policies
•
Configure Policy Combining Algorithm and obligations
•
Add attributes to return
•
Add policy attributes
•
Configure rules for policies
Create Multiple Policies for a Role
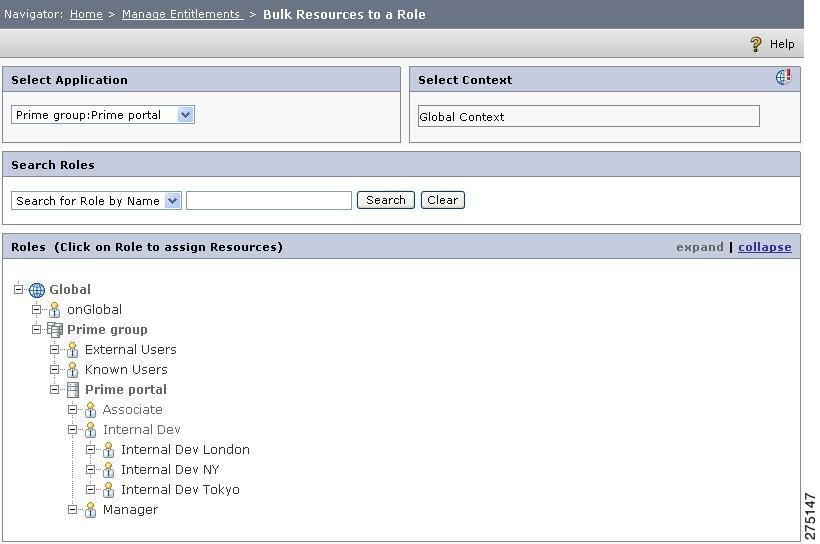
To create multiple policies for a role on a single page in the PAP, follow these steps:
Step 1
Choose Manage Entitlements > Bulk Resources to a Role.
The Policy Management by Role page is displayed.
Figure 5-34 Bulk Resources to a Role
Step 2
Select application, application group, or Global under which the role to be assigned to the resources exist. If you select Global, all the global roles are displayed. If you select Application group, roles belonging to the global level as well as under the selected application group are displayed. Similarly, if you select an application, a list of roles that includes all roles present under Global, application group, and application level.
Step 3
Click the role name for which you want to assign multiple resources (that is, create multiple policies).
The Policy Management By Role page is displayed, which contains a list of all the resources under the selected application, application group, or Global.
Figure 5-35 Policy Creation by Role
Step 4
To create the Allow/Deny policy, check the appropriate check box, Allow or Deny, that is next to that resource name, and click Save.
The policy for the selected role and selected resources gets created.
You can click the icons described in Table 5-5Role icons to perform various operations.
Note
The three icons appears next to the resource name only after you create the policy, that is, check one of the check boxes, Allow or Deny, that are next to that resource name, and then click Save.
Policy Combining Algorithm for a Resource
Refer to Policy Combining Algorithm, page 5-4 .
Add attributes to be returned as Obligation
Refer to Set attributes to be returned as obligation, page 5-5.
Edit Policy Configurations
Refer to Edit Policy Configurations, page 5-6.
Set Policy Attributes
Refer to Set Policy Attributes, page 5-8.
Add Rules to a Policy
Refer to Add Rules to a Policy, page 5-11.
List Entitlements
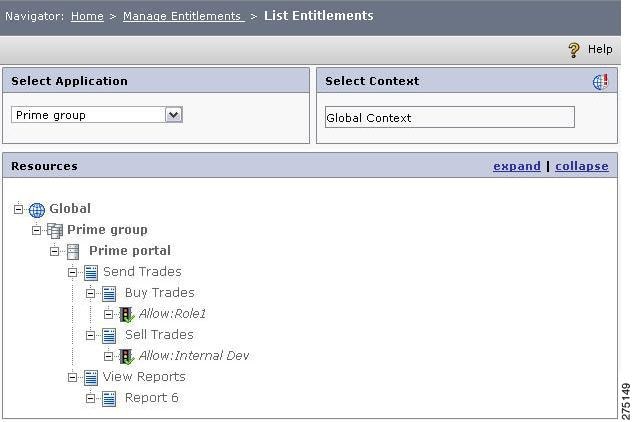
The PAP provides the functionality to view a list of all the entitlements for all the resources in an application or application group.
To view a list of entitlements, you must:
Step 1
Choose Manage Entitlements > List Entitlements.
The List Entitlements page is displayed.
Step 2
Select the application or application group for which you want to view the entitlements.
Step 3
Select the appropriate context for which you want to view the entitlements by clicking the Context icon. A list of contexts is displayed. Select the appropriate context from the list.
Step 4
The list of resources associated with the selected application or application group and context is displayed with their entitlements in the List Resources section. You can click the expand link to view all the resources that are in the list.
Figure 5-36 List Entitlement

 Feedback
Feedback