Unlock transformation with frictionless zero trust access
Make zero trust progress while optimizing the digital experience. Zero trust enables secure access for users and devices and within apps, across networks, and clouds. Embed zero trust across the fabric of your multi-environment IT by securing access in a way that frustrates attackers, not users.
For business and security leaders struggling to reduce risk at scale, we can help create and enforce zero trust policies across all control points without compromising user experience or team productivity.
Functional requirements for zero trust
First, accurately establish trust. Strongly verify user and device trust before granting access. Second, consistently enforce trust-based access, based on the principle of least privilege. Third, because change is inevitable, continuously verify trust, and instantly adjust access based on risk. And fourth, dynamically respond to change in trust, and then investigate and orchestrate incident response.
Secure access to the edge and beyond
Our solutions are focused on a secure and seamless user experience to deliver strong security and high productivity. We meet you where you are to deliver zero trust with visibility and control embedded at every layer, from campus to data center to cloud to edge. We've also embarked on zero trust for ourselves. Cisco's rollout of zero trust has unlocked about $4M in annual savings from increased productivity and IT helpdesk support costs. We are also able to prevent 86K system compromises each month by enabling users with self-remediation of out-of-compliance devices.
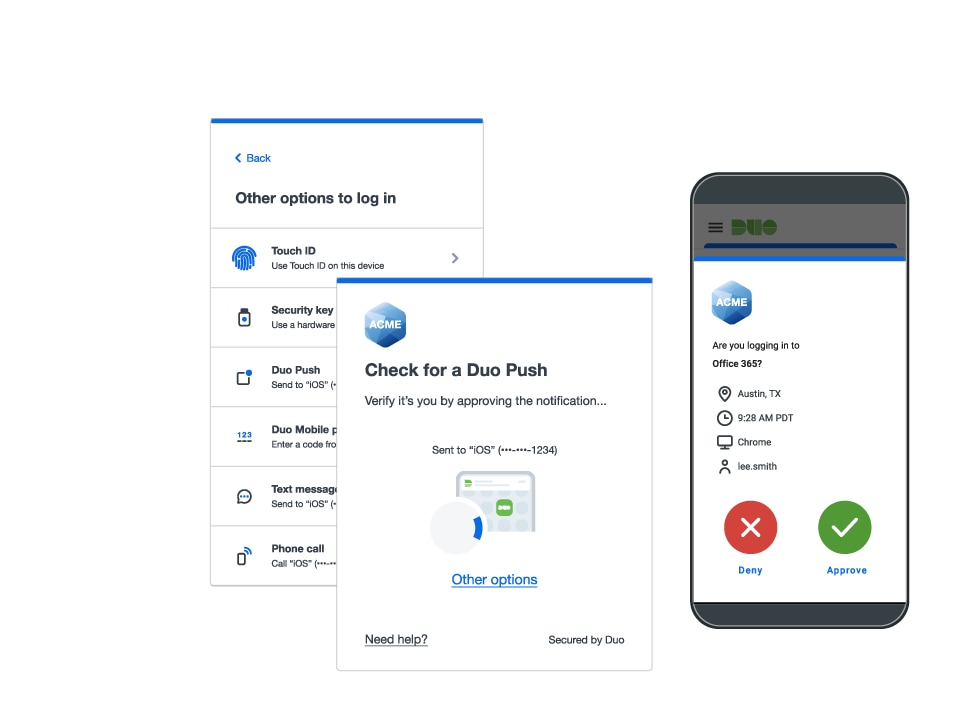
Secure app access first, but don't end there
More than 57% of teams we surveyed embarked on zero trust by securing user and device access to apps from anywhere. This is considered least disruptive, most critical to managing risk, and aligned to the business. Securing user and device access to apps—anywhere they are located—can also drastically improve the user experience while increasing visibility into user and device behavior and contextual risk.
Identity Services Engine (ISE)
Leverage intel from across your stack to enforce policy, manage endpoints, and deliver trusted access.
Cisco Umbrella
Gain visibility and control into web traffic to secure access to SaaS apps with cloud-based security.
Secure Firewall
Gain efficiencies with automated policy enforcement for network, microsegmentation, and AppSec integrations.
Secure Network Analytics
Analyze existing network data to detect threats that bypass existing controls before they do damage.
Secure Workload
Automate and implement a zero trust model for microsegmentation based on app behavior and telemetry.
Secure Cloud Analytics
Monitor workloads across all major clouds, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud.
Add value to your security solutions
Cisco Secure Choice Enterprise Agreement
Instant savings
Buy only what you need with one flexible and easy-to-manage agreement.
Services for security
Let the experts secure your business
Get more from your investments and enable constant vigilance to protect your organization.