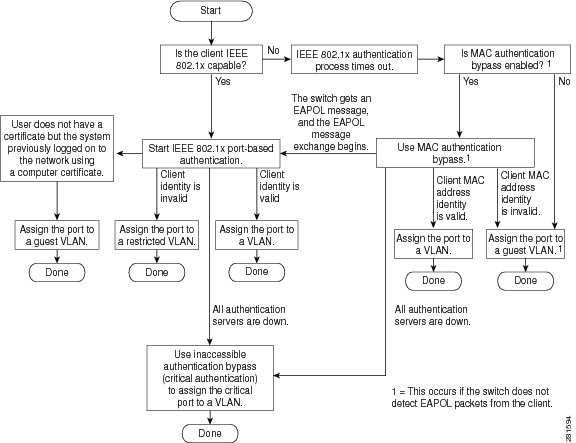
Restrictions for IEEE 802.1x Port-Based Authentication
-
Switchports are always unauthorized when used with private VLANs. Dynamic VLANs pushed from the Authentication, Authorization, and Accounting (AAA) server is not supported on private VLAN ports. The data client session is expected to authorize on the secondary VLAN of the private VLAN dot1x port.
-
Only interface-configured private VLAN-based authorization and dynamic VLAN on a normal access VLAN port is supported.
-
If the dot1q tag vlan native command is configured globally, the dot1x reauthentication will fail on trunk ports.
-
Do not configure the same VLAN ID for both voice VLAN and access VLAN at the same time, because it may cause authentication failures.
-
If a downloadable ACL contains any type of duplicate entries, the entries are not auto merged. As a result, the 802.1X session authorization fails. Ensure that the downloadable ACL is optimized without any duplicate entries, for example port-based and name-based entries for the same port.
-
Port security is not supported with IEEE 802.1x port-based authentication.
-
If you overwrite the running configuration of interfaces with a configuration file loaded in flash, some ports may fail to authenticate the endpoints.
-
Wake-on-LAN (WoL) feature is not supported.

 Feedback
Feedback