- Preface
- Using the Command-Line Interface
- Preventing Unauthorized Access
- Preventing Unauthorized Access
- Controlling Switch Access with Passwords and Privilege Levels
- Configuring TACACS+
- Configuring RADIUS
- Configuring Kerberos
- Configuring Local Authentication and Authorization
- Configuring Secure Shell (SSH)
- Configuring Secure Socket Layer HTTP
- Configuring IPv4 ACLs
- Configuring IPv6 ACLs
- Configuring DHCP
- Configuring IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Web-Based Authentication
- Configuring Port-Based Traffic Control
- Configuring IPv6 First Hop Security
- Configuring Wireless Guest Access
- Configuring Intrusion Detection System
- Index
Security Configuration Guide, Cisco IOS XE Release 3.6E (Catalyst 3850 Switches)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 1, 2014
Chapter: Configuring Web-Based Authentication
- Finding Feature Information
- Web-Based Authentication Overview
- Default Web-Based Authentication Configuration
- Web-Based Authentication Configuration Guidelines and Restrictions
- Web-Based Authentication Configuration Task List
- Configuring the Authentication Rule and Interfaces
- Configuring AAA Authentication
- Configuring Switch-to-RADIUS-Server Communication
- Configuring the HTTP Server
- Configuring the Web-Based Authentication Parameters
- Configuring a Web-Based Authentication Local Banner
- Configuring Web-Based Authentication without SVI
- Configuring Web-Based Authentication with VRF Aware
- Removing Web-Based Authentication Cache Entries
Configuring Web-Based Authentication
This chapter describes how to configure web-based authentication on the switch. It contains these sections:
- Finding Feature Information
- Web-Based Authentication Overview
- How to Configure Web-Based Authentication
- Monitoring Web-Based Authentication Status
- Feature Information for Web-Based Authentication
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.
Web-Based Authentication Overview
Use the web-based authentication feature, known as web authentication proxy, to authenticate end users on host systems that do not run the IEEE 802.1x supplicant.
 Note | You can configure web-based authentication on Layer 2 and Layer 3 interfaces. |
When you initiate an HTTP session, web-based authentication intercepts ingress HTTP packets from the host and sends an HTML login page to the users. The users enter their credentials, which the web-based authentication feature sends to the authentication, authorization, and accounting (AAA) server for authentication.
If authentication succeeds, web-based authentication sends a Login-Successful HTML page to the host and applies the access policies returned by the AAA server.
If authentication fails, web-based authentication forwards a Login-Fail HTML page to the user, prompting the user to retry the login. If the user exceeds the maximum number of attempts, web-based authentication forwards a Login-Expired HTML page to the host, and the user is placed on a watch list for a waiting period.
 Note | HTTPS traffic interception for central web authentication redirect is not supported. |
 Note | You should use global parameter-map (for method-type, custom, and redirect) only for using the same web authentication methods like consent, web consent, and webauth, for all the clients and SSIDs. This ensures that all the clients have the same web-authentication method. If the requirement is to use Consent for one SSID and Web-authentication for another SSID, then you should use two named parameter-maps. You should configure Consent in first parameter-map and configure webauth in second parameter-map. |
 Note | The traceback that you receive when webauth client tries to do authentication does not have any performance or behavioral impact. It happens rarely when the context for which FFM replied back to EPM for ACL application is already dequeued (possibly due to timer expiry) and the session becomes ‘unauthorized’. |
Based on where the web pages are hosted, the local web authention can be categorozied as follows:
-
Internal—The internal default HTML pages (Login, Success, Fail, and Expire) in the controller are used during the local web authentication.
-
Customized—The customized web pages (Login, Success, Fail, and Expire) are downloaded onto the controller and used during the local web authentication.
-
External—The customized web pages are hosted on the external web server instead of using the in-built or custom web pages.
Based on the various web authentication pages, the types of web authentication are as follows:
-
Webauth—This is a basic web authentication. Herein, the controller presents a policy page with the user name and password. You need to enter the correct credentials to access the network.
-
Consent or web-passthrough—Herein, the controller presents a policy page with the Accept or Deny buttons. You need to click the Accept button to access the network.
-
Webconsent—This is a combination of webauth and consent web authentication types. Herein, the controller presents a policy page with Accept or Deny buttons along with user name or password. You need to enter the correct credentials and click the Accept button to access the network.
 Note | The Wireless web authentication feature does not support the bypass type. |
- Device Roles
- Host Detection
- Session Creation
- Authentication Process
- Local Web Authentication Banner
- Web Authentication Customizable Web Pages
- Web-based Authentication Interactions with Other Features
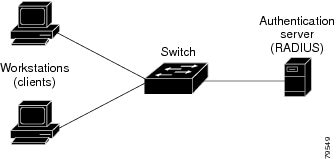
Device Roles
With web-based authentication, the devices in the network have these specific roles:
Client—The device (workstation) that requests access to the LAN and the services and responds to requests from the switch. The workstation must be running an HTML browser with Java Script enabled.
Authentication server—Authenticates the client. The authentication server validates the identity of the client and notifies the switch that the client is authorized to access the LAN and the switch services or that the client is denied.
Switch—Controls the physical access to the network based on the authentication status of the client. The switch acts as an intermediary (proxy) between the client and the authentication server, requesting identity information from the client, verifying that information with the authentication server, and relaying a response to the client.
Host Detection
The switch maintains an IP device tracking table to store information about detected hosts.
 Note | By default, the IP device tracking feature is disabled on a switch. You must enable the IP device tracking feature to use web-based authentication. |
For Layer 2 interfaces, web-based authentication detects IP hosts by using these mechanisms:
Session Creation
When web-based authentication detects a new host, it creates a session as follows:
-
If the host IP is included in the exception list, the policy from the exception list entry is applied, and the session is established.
Reviews for authorization bypass
If the host IP is not on the exception list, web-based authentication sends a nonresponsive-host (NRH) request to the server.
If the server response is access accepted, authorization is bypassed for this host. The session is established.
Sets up the HTTP intercept ACL
If the server response to the NRH request is access rejected, the HTTP intercept ACL is activated, and the session waits for HTTP traffic from the host.
Authentication Process
When you enable web-based authentication, these events occur:
-
The HTTP traffic is intercepted, and authorization is initiated. The switch sends the login page to the user. The user enters a username and password, and the switch sends the entries to the authentication server.
-
If the authentication succeeds, the switch downloads and activates the user’s access policy from the authentication server. The login success page is sent to the user.
-
If the authentication fails, the switch sends the login fail page. The user retries the login. If the maximum number of attempts fails, the switch sends the login expired page, and the host is placed in a watch list. After the watch list times out, the user can retry the authentication process.
-
If the authentication server does not respond to the switch, and if an AAA fail policy is configured, the switch applies the failure access policy to the host. The login success page is sent to the user.
-
The switch reauthenticates a client when the host does not respond to an ARP probe on a Layer 2 interface, or when the host does not send any traffic within the idle timeout on a Layer 3 interface.
-
The feature applies the downloaded timeout or the locally configured session timeout.

Note
Beginning with Cisco IOS XE Denali 16.1.1 and later, the default session timeout value for web-based authentication on WLC is 1800 seconds. The default session timeout value was infinite seconds, prior to Cisco IOS XE Denali 16.1.1.
-
If the terminate action is RADIUS, the feature sends a nonresponsive host (NRH) request to the server. The terminate action is included in the response from the server.
-
If the terminate action is default, the session is dismantled, and the applied policy is removed.
Local Web Authentication Banner
With Web Authentication, you can create a default and customized web-browser banners that appears when you log in to a switch.
The banner appears on both the login page and the authentication-result pop-up pages. The default banner messages are as follows:
The Local Web Authentication Banner can be configured in legacy CLIs as follows:
-
Legacy mode—Use the ip admission auth-proxy-banner http global configuration command.
-
New-style mode—Use the parameter-map type webauth global bannerglobal configuration command.
The default banner Cisco Systems and Switch host-name Authentication appear on the Login Page. Cisco Systems appears on the authentication result pop-up page.
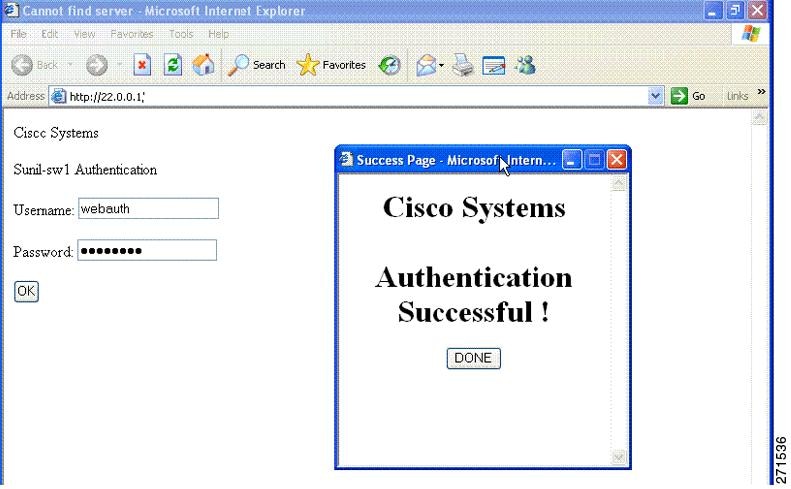
The banner can be customized as follows:
-
Add a message, such as switch, router, or company name to the banner:
-
Add a logo or text file to the banner:
-
Legacy mode—Use the ip admission auth-proxy-banner http file-path global configuration command.
-
New-style mode—Use the parameter-map type webauth global banner global configuration command
Figure 3. Customized Web Banner 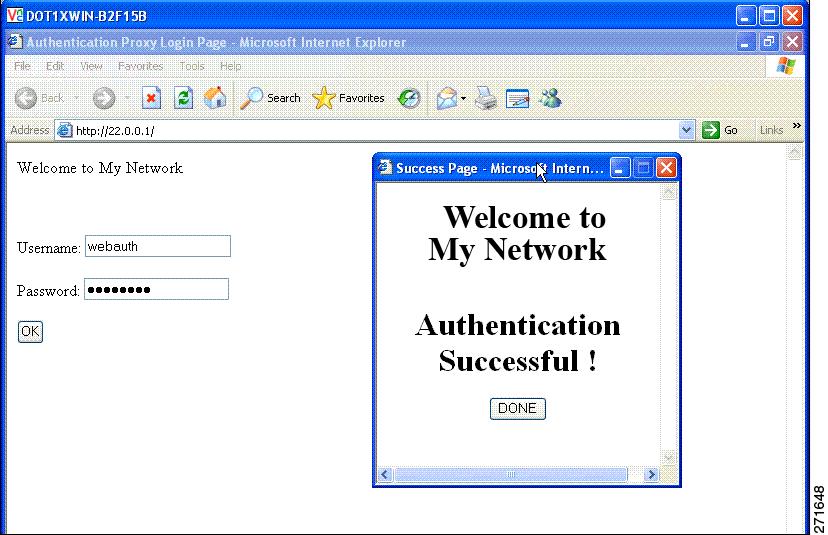
-
If you do not enable a banner, only the username and password dialog boxes appear in the web authentication login screen, and no banner appears when you log into the switch.
For more information, see the Session Aware Networking Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) Session Aware Networking Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches) and the Web Authentication Enhancements - Customizing Authentication Proxy Web Pages.
Web Authentication Customizable Web Pages
During the web-based authentication process, the switch internal HTTP server hosts four HTML pages to deliver to an authenticating client. The server uses these pages to notify you of these four-authentication process states:
Guidelines
-
You can substitute your own HTML pages for the default internal HTML pages.
-
You can use a logo or specify text in the login, success, failure, and expire web pages.
-
You must include an HTML redirect command in the success page to access a specific URL.
-
The URL string must be a valid URL (for example, http://www.cisco.com). An incomplete URL might cause page not found or similar errors on a web browser.
-
If you configure web pages for HTTP authentication, they must include the appropriate HTML commands (for example, to set the page time out, to set a hidden password, or to confirm that the same page is not submitted twice).
-
The CLI command to redirect users to a specific URL is not available when the configured login form is enabled. The administrator should ensure that the redirection is configured in the web page.
-
If the CLI command redirecting users to specific URL after authentication occurs is entered and then the command configuring web pages is entered, the CLI command redirecting users to a specific URL does not take effect.
-
Configured web pages can be copied to the switch boot flash or flash.
-
On stackable switches, configured pages can be accessed from the flash on the stack master or members.
-
The login page can be on one flash, and the success and failure pages can be another flash (for example, the flash on the stack master or a member).
-
The banner page has no effect if it is configured with the web page.
-
All of the logo files (image, flash, audio, video, and so on) that are stored in the system directory (for example, flash, disk0, or disk) and that must be displayed on the login page must use web_auth_<filename> as the file name.
-
The configured authentication proxy feature supports both HTTP and SSL.
You can substitute your HTML pages for the default internal HTML pages. You can also specify a URL to which users are redirected after authentication occurs, which replaces the internal Success page.
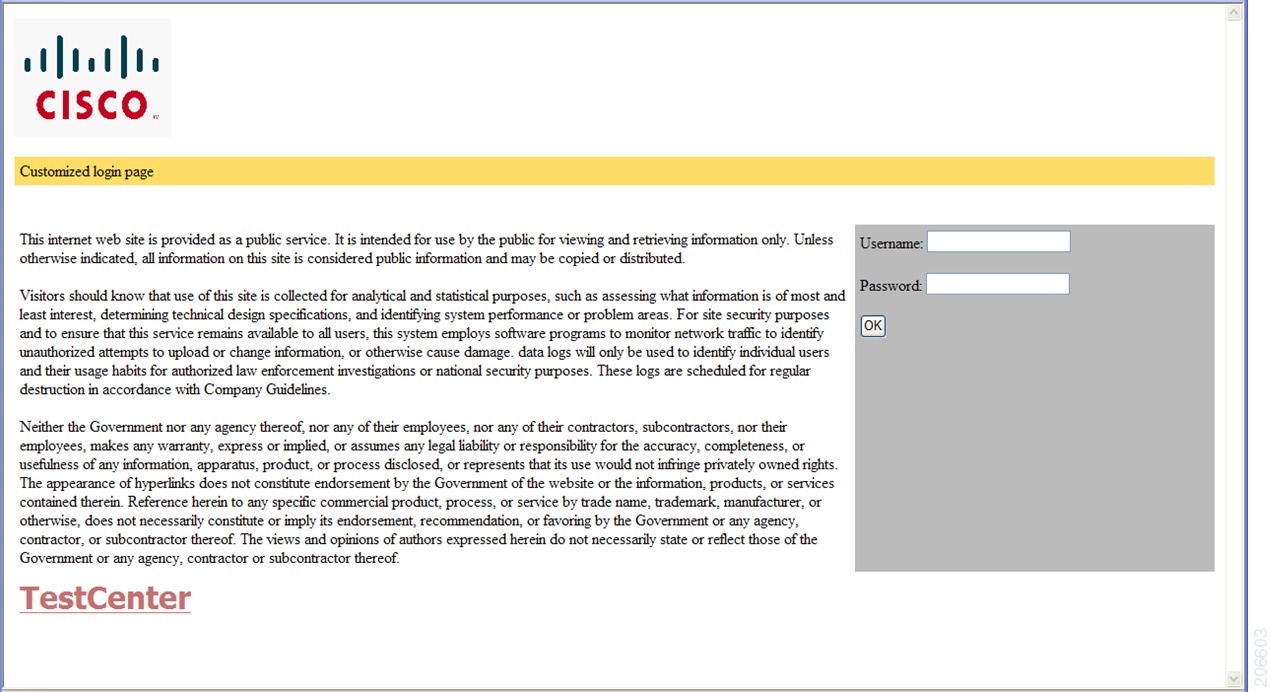
Authentication Proxy Web Page Guidelines
When configuring customized authentication proxy web pages, follow these guidelines:
-
To enable the custom web pages feature, specify all four custom HTML files. If you specify fewer than four files, the internal default HTML pages are used.
-
The four custom HTML files must be present on the flash memory of the switch. The maximum size of each HTML file is 8 KB.
-
Any images on the custom pages must be on an accessible HTTP server. Configure an intercept ACL within the admission rule.
-
Any external link from a custom page requires configuration of an intercept ACL within the admission rule.
-
To access a valid DNS server, any name resolution required for external links or images requires configuration of an intercept ACL within the admission rule.
-
If the custom web pages feature is enabled, a configured auth-proxy-banner is not used.
-
If the custom web pages feature is enabled, the redirection URL for successful login feature is not available.
-
To remove the specification of a custom file, use the no form of the command.
Because the custom login page is a public web form, consider these guidelines for the page:
Redirection URL for Successful Login Guidelines
When configuring a redirection URL for successful login, consider these guidelines:
-
If the custom authentication proxy web pages feature is enabled, the redirection URL feature is disabled and is not available in the CLI. You can perform redirection in the custom-login success page.
-
If the redirection URL feature is enabled, a configured auth-proxy-banner is not used
-
To remove the specification of a redirection URL, use the no form of the command.
-
If the redirection URL is required after the web-based authentication client is successfully authenticated, then the URL string must start with a valid URL (for example, http://) followed by the URL information. If only the URL is given without http://, then the redirection URL on successful authentication might cause page not found or similar errors on a web browser.
Web-based Authentication Interactions with Other Features
Port Security
You can configure web-based authentication and port security on the same port. Web-based authentication authenticates the port, and port security manages network access for all MAC addresses, including that of the client. You can then limit the number or group of clients that can access the network through the port.
LAN Port IP
You can configure LAN port IP (LPIP) and Layer 2 web-based authentication on the same port. The host is authenticated by using web-based authentication first, followed by LPIP posture validation. The LPIP host policy overrides the web-based authentication host policy.
If the web-based authentication idle timer expires, the NAC policy is removed. The host is authenticated, and posture is validated again.
Gateway IP
You cannot configure Gateway IP (GWIP) on a Layer 3 VLAN interface if web-based authentication is configured on any of the switch ports in the VLAN.
You can configure web-based authentication on the same Layer 3 interface as Gateway IP. The host policies for both features are applied in software. The GWIP policy overrides the web-based authentication host policy.
ACLs
If you configure a VLAN ACL or a Cisco IOS ACL on an interface, the ACL is applied to the host traffic only after the web-based authentication host policy is applied.
For Layer 2 web-based authentication, it is more secure, though not required, to configure a port ACL (PACL) as the default access policy for ingress traffic from hosts connected to the port. After authentication, the web-based authentication host policy overrides the PACL. The Policy ACL is applied to the session even if there is no ACL configured on the port.
You cannot configure a MAC ACL and web-based authentication on the same interface.
You cannot configure web-based authentication on a port whose access VLAN is configured for VACL capture.
Context-Based Access Control
Web-based authentication cannot be configured on a Layer 2 port if context-based access control (CBAC) is configured on the Layer 3 VLAN interface of the port VLAN.
EtherChannel
You can configure web-based authentication on a Layer 2 EtherChannel interface. The web-based authentication configuration applies to all member channels.
How to Configure Web-Based Authentication
Default Web-Based Authentication Configuration
Web-Based Authentication Configuration Guidelines and Restrictions
-
You can configure web-based authentication only on access ports. Web-based authentication is not supported on trunk ports, EtherChannel member ports, or dynamic trunk ports.
-
External web authentication, where the switch redirects a client to a particular host or web server for displaying login message, is not supported.
-
You cannot authenticate hosts on Layer 2 interfaces with static ARP cache assignment. These hosts are not detected by the web-based authentication feature because they do not send ARP messages.
-
By default, the IP device tracking feature is disabled on a switch. You must enable the IP device tracking feature to use web-based authentication.
-
You must configure at least one IP address to run the switch HTTP server. You must also configure routes to reach each host IP address. The HTTP server sends the HTTP login page to the host.
-
Hosts that are more than one hop away might experience traffic disruption if an STP topology change results in the host traffic arriving on a different port. This occurs because the ARP and DHCP updates might not be sent after a Layer 2 (STP) topology change.
-
Web-based authentication does not support VLAN assignment as a downloadable-host policy.
-
Web-based authentication supports IPv6 in Session-aware policy mode. IPv6 Web-authentication requires at least one IPv6 address configured on the switch and IPv6 Snooping configured on the switchport.
-
Web-based authentication and Network Edge Access Topology (NEAT) are mutually exclusive. You cannot use web-based authentication when NEAT is enabled on an interface, and you cannot use NEAT when web-based authentication is running on an interface.
-
Web-based authentication NRH (Non-Responsive Host) is not supported for voice devices.
-
Only the Password Authentication Protocol (PAP) is supported for web-based RADIUS authentication on controllers. The Challenge Handshake Authentication Protocol (CHAP) is not supported for web-based RADIUS authentication on controllers.
-
Identify the following RADIUS security server settings that will be used while configuring switch-to-RADIUS-server communication:
The combination of the IP address and UDP port number creates a unique identifier, that enables RADIUS requests to be sent to multiple UDP ports on a server at the same IP address. If two different host entries on the same RADIUS server are configured for the same service (for example, authentication) the second host entry that is configured functions as the failover backup to the first one. The RADIUS host entries are chosen in the order that they were configured.
-
When you configure the RADIUS server parameters:
-
For key string, specify the authentication and encryption key used between the switch and the RADIUS daemon running on the RADIUS server. The key is a text string that must match the encryption key used on the RADIUS server.
-
When you specify the key string, use spaces within and at the end of the key. If you use spaces in the key, do not enclose the key in quotation marks unless the quotation marks are part of the key. This key must match the encryption used on the RADIUS daemon.
-
You can globally configure the timeout, retransmission, and encryption key values for all RADIUS servers by using with the radius-server host global configuration command. If you want to configure these options on a per-server basis, use the radius-server timeout, radius-server transmit, and the radius-server key global configuration commands. For more information, see the Cisco IOS Security Configuration Guide, Release 12.4 and the Cisco IOS Security Command Reference, Release 12.4.
Web-Based Authentication Configuration Task List
Configuring the Authentication Rule and Interfaces
Examples in this section are legacy-style configurations. For new-style configurations, see the Session Aware Networking Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)
Follow these steps to configure the authentication rule and interfaces:
1.
enable
3.
ip admission
name
name
proxy
http
6.
ip admission
name
11.
copy running-config
startup-config
DETAILED STEPS
Configuring AAA Authentication
line vty 0 4 authorization commands 15 abc aaa authorization commands 15 abc group tacacs+
line vty 0 4 aaa authorization commands 15 default group tacacs+
Follow these steps to configure AAA authentication:
 Note | Use default list for AAA authorization, if you are planning to use features such as dACL. |
1.
enable
4.
aaa authentication login default group {tacacs+ | radius}
5.
aaa authorization auth-proxy default group {tacacs+ | radius}
6.
tacacs-server host {hostname | ip_address}
7.
tacacs-server key {key-data}
10.
copy running-config
startup-config
DETAILED STEPS
Configuring Switch-to-RADIUS-Server Communication
Follow these steps to configure the RADIUS server parameters:
1.
enable
3.
ip radius
source-interface
vlan
vlan interface
number
4.
radius-server host
{hostname |
ip-address}
test username
username
DETAILED STEPS
Configuring the HTTP Server
To use web-based authentication, you must enable the HTTP server within the Switch. You can enable the server for either HTTP or HTTPS.
 Note | The Apple psuedo-browser will not open if you configure only the ip http secure-server command. You should also configure the ip http server command. |
Follow these steps to enable the server for either HTTP or HTTPS:
DETAILED STEPS
Customizing the Authentication Proxy Web Pages
You can configure web authentication to display four substitute HTML pages to the user in place of the Switch default HTML pages during web-based authentication.
For the equivalent Session Aware Networking configuration example for this feature, see the section "Configuring a Parameter Map for Web-Based Authentication" in the chapter, "Configuring Identity Control Policies." of the book, "Session Aware Networking Configuration Guide, Cisco IOS XE Release 3SE (Catalyst 3850 Switches)."
Follow these steps to specify the use of your custom authentication proxy web pages:
Store your custom HTML files on the Switch flash memory.
1.
enable
3.
ip admission proxy
http login page file
device:login-filename
4.
ip admission proxy
http success page file
device:success-filename
5.
ip admission proxy
http failure page file
device:fail-filename
6.
ip admission proxy
http login expired page file
device:expired-filename
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip admission proxy
http login page file
device:login-filename
Example: Switch(config)# ip admission proxy http login page file disk1:login.htm |
Specifies the location in the Switch memory file system of the custom HTML file to use in place of the default login page. The device: is flash memory. |
| Step 4 | ip admission proxy
http success page file
device:success-filename
Example: Switch(config)# ip admission proxy http success page file disk1:success.htm |
Specifies the location of the custom HTML file to use in place of the default login success page. |
| Step 5 | ip admission proxy
http failure page file
device:fail-filename
Example: Switch(config)# ip admission proxy http fail page file disk1:fail.htm |
Specifies the location of the custom HTML file to use in place of the default login failure page. |
| Step 6 | ip admission proxy
http login expired page file
device:expired-filename
Example:
Switch(config)# ip admission proxy http login expired page file disk1:expired.htm
|
Specifies the location of the custom HTML file to use in place of the default login expired page. |
| Step 7 | end
Example: Switch(config)# end |
Specifying a Redirection URL for Successful Login
Follow these steps to specify a URL to which the user is redirected after authentication, effectively replacing the internal Success HTML page:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip admission proxy
http success redirect
url-string
Example: Switch(config)# ip admission proxy http success redirect www.example.com |
Specifies a URL for redirection of the user in place of the default login success page. |
| Step 4 | end
Example: Switch(config)# end |
Configuring the Web-Based Authentication Parameters
Follow these steps to configure the maximum number of failed login attempts before the client is placed in a watch list for a waiting period:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip admission max-login-attempts
number
Example: Switch(config)# ip admission max-login-attempts 10 |
Sets the maximum number of failed login attempts. The range is 1 to 2147483647 attempts. The default is 5. |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show running-config
Example: Switch# show running-config | |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring a Web-Based Authentication Local Banner
Follow these steps to configure a local banner on a switch that has web authentication configured.
1.
enable
3.
ip admission
auth-proxy-banner http [banner-text |
file-path]
6.
copy running-config
startup-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | ip admission
auth-proxy-banner http [banner-text |
file-path]
Example: Switch(config)# ip admission auth-proxy-banner http C My Switch C |
(Optional) Create a custom banner by entering C banner-text C (where C is a delimiting character), or file-path that indicates a file (for example, a logo or text file) that appears in the banner. |
| Step 4 | end
Example: Switch(config)# end | |
| Step 5 | show running-config
Example: Switch# show running-config | |
| Step 6 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring Web-Based Authentication without SVI
You configure the web-based authentication without SVI feature to redirect the HTML login page to the client without creating an IP address in the routing table. These steps are optional.
1.
enable
3.
parameter-map type webauth global
4.
l2-webauth-enabled
7.
copy running-config
startup-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | parameter-map type webauth global
Example: Switch (config)# parameter-map type webauth global
| Creates a parameter map and enters parameter-map webauth configuration mode. The specific configuration commands supported for a global parameter map defined with the global keyword differ from the commands supported for a named parameter map defined with the parameter-map-name argument. |
| Step 4 | l2-webauth-enabled
Example: Switch (config-params-parameter-map)# l2-webauth-enabled
|
Enables the web-based authentication without SVI feature |
| Step 5 | end
Example: Switch(config)# end | |
| Step 6 | show running-config
Example: Switch# show running-config | |
| Step 7 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Configuring Web-Based Authentication with VRF Aware
You configure the web-based authentication with VRF aware to redirect the HTML login page to the client. These steps are optional.
1.
enable
3.
parameter-map type webauth global
4.
webauth-vrf-aware
7.
copy running-config
startup-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | configure
terminal
Example: Switch# configure terminal | |
| Step 3 | parameter-map type webauth global
Example: Switch (config)# parameter-map type webauth global
| Creates a parameter map and enters parameter-map webauth configuration mode. The specific configuration commands supported for a global parameter map defined with the global keyword differ from the commands supported for a named parameter map defined with the parameter-map-name argument. |
| Step 4 | webauth-vrf-aware
Example: Switch (config-params-parameter-map)# webauth-vrf-aware
|
Enables the web-based authentication VRF aware feature on SVI. |
| Step 5 | end
Example: Switch(config)# end | |
| Step 6 | show running-config
Example: Switch# show running-config | |
| Step 7 | copy running-config
startup-config
Example:
Switch# copy running-config startup-config
|
(Optional) Saves your entries in the configuration file. |
Removing Web-Based Authentication Cache Entries
Follow these steps to remove web-based authentication cache entries:
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example:
Switch> enable
|
Enables privileged EXEC mode. Enter your password if prompted. |
| Step 2 | clear ip auth-proxy
cache {* |
host ip
address}
Example: Switch# clear ip auth-proxy cache 192.168.4.5 |
Delete authentication proxy entries. Use an asterisk to delete all cache entries. Enter a specific IP address to delete the entry for a single host. |
| Step 3 | clear ip admission
cache {* |
host ip
address}
Example: Switch# clear ip admission cache 192.168.4.5 |
Delete authentication proxy entries. Use an asterisk to delete all cache entries. Enter a specific IP address to delete the entry for a single host. |
Monitoring Web-Based Authentication Status
Use the commands in this topic to display the web-based authentication settings for all interfaces or for specific ports.
|
Command |
Purpose |
|---|---|
|
Displays the web-based authentication settings for all interfaces for fastethernet, gigabitethernet, or tengigabitethernet |
|
|
show wireless client mac-address a.a.a detail |
Displays the session specific wireless information and wireless states. |
|
show authentication sessions interface type slot/port[details] |
Displays the web-based authentication settings for the specified interface for fastethernet, gigabitethernet, or tengigabitethernet. In Session Aware Networking mode, use the show access-session interface command. |
Feature Information for Web-Based Authentication
| Release | Feature Information |
|---|---|
| Cisco IOS XE 3.2SE
|
This feature is introduced. |
 Feedback
Feedback