- Catalyst 3750-X and 3560-X Switch Software Configuration Guide, Cisco IOS 15.0(2)SE and Later
- Table of Contents
- Preface
- Overview
- Using the Command-Line Interface
- Configuring Cisco IOS Configuration Engine
- Assigning the Switch IP Address and Default Gateway
- Managing Switch Stacks
- Clustering Switches
- Administering the Switch
- Configuring SDM Templates
- Managing Catalyst 3750-X Stack Power
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring MACsec Encryption
- Configuring Web-Based Authentication
- Configuring Cisco TrustSec
- Configuring Interface Characteristics
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLANs
- Configuring Private VLANs
- Configuring IEEE 802.1Q and Layer 2 Protocol Tunneling
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Resilient Ethernet Protocol
- Configuring Flex Links
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring IPv6 MLD Snooping
- Configuring CDP
- Configuring Port-Based Traffic Control
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging and Smart Logging
- Configuring SNMP
- Configuring Embedded Event Manager
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring IPv6 ACLs
- Configuring EtherChannels and Link-State Tracking
- Configuring TelePresence E911 IP Phone Support
- Configuring IP Unicast Routing
- Configuring IPv6 Unicast Routing
- Configuring HSRP and VRRP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Flexible NetFlow
- Configuring Enhanced Object Tracking
- Configuring WCCP
- Configuring IP Multicast Routing
- Implementing IPv6 Multicast
- Configuring MSDP
- Configuring Fallback Bridging
- Troubleshooting
- Configuring Online Diagnostics
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 15.0(2)SE
- Index
Catalyst 3750-X and Catalyst 3560-X Switch Software Configuration Guide, Cisco IOS Release 15.0(2)SE and Later
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- September 24, 2014
Chapter: Configuring Voice VLANs
Configuring Voice VLAN
This chapter describes how to configure the voice VLAN feature on the Catalyst 3750-X or 3560-X switch. Unless otherwise noted, the term switch refers to a Catalyst 3750-X or 3560-X standalone switch and to a Catalyst 3750-X switch stack. Voice VLAN is referred to as an auxiliary VLAN in some Catalyst 6500 family switch documentation.

Note![]() For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
For complete syntax and usage information for the commands used in this chapter, see the command reference for this release.
Understanding Voice VLAN
The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. When the switch is connected to a Cisco 7960 IP Phone, the phone sends voice traffic with Layer 3 IP precedence and Layer 2 class of service (CoS) values, which are both set to 5 by default. Because the sound quality of an IP phone call can deteriorate if the data is unevenly sent, the switch supports quality of service (QoS) based on IEEE 802.1p CoS. QoS uses classification and scheduling to send network traffic from the switch in a predictable manner. For more information on QoS, see Chapter1, “Configuring QoS”
The Cisco 7960 IP Phone is a configurable device, and you can configure it to forward traffic with an IEEE 802.1p priority. You can configure the switch to trust or override the traffic priority assigned by a Cisco IP Phone.
The Cisco IP Phone contains an integrated three-port 10/100 switch as shown in Figure 1-1. The ports provide dedicated connections to these devices:
- Port 1 connects to the switch or other voice-over-IP (VoIP) device.
- Port 2 is an internal 10/100 interface that carries the IP Phone traffic.
- Port 3 (access port) connects to a PC or other device.
Figure 1-1 shows one way to connect a Cisco 7960 IP Phone.
Figure 1-1 Cisco 7960 IP Phone Connected to a Switch
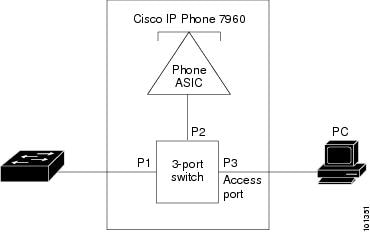
Cisco IP Phone Voice Traffic
You can configure an access port with an attached Cisco IP Phone to use one VLAN for voice traffic and another VLAN for data traffic from a device attached to the phone. You can configure access ports on the switch to send Cisco Discovery Protocol (CDP) packets that instruct an attached phone to send voice traffic to the switch in any of these ways:
- In the voice VLAN tagged with a Layer 2 CoS priority value
- In the access VLAN tagged with a Layer 2 CoS priority value
- In the access VLAN, untagged (no Layer 2 CoS priority value)

Note![]() In all configurations, the voice traffic carries a Layer 3 IP precedence value (the default is 5 for voice traffic and 3 for voice control traffic).
In all configurations, the voice traffic carries a Layer 3 IP precedence value (the default is 5 for voice traffic and 3 for voice control traffic).
Cisco IP Phone Data Traffic
The switch can also process tagged data traffic (traffic in IEEE 802.1Q or IEEE 802.1p frame types) from the device attached to the access port on the Cisco IP Phone (see Figure 1-1). You can configure Layer 2 access ports on the switch to send CDP packets that instruct the attached phone to configure the phone access port in one of these modes:
- In trusted mode, all traffic received through the access port on the Cisco IP Phone passes through the phone unchanged.
- In untrusted mode, all traffic in IEEE 802.1Q or IEEE 802.1p frames received through the access port on the Cisco IP Phone receive a configured Layer 2 CoS value. The default Layer 2 CoS value is 0. Untrusted mode is the default.

Note![]() Untagged traffic from the device attached to the Cisco IP Phone passes through the phone unchanged, regardless of the trust state of the access port on the phone.
Untagged traffic from the device attached to the Cisco IP Phone passes through the phone unchanged, regardless of the trust state of the access port on the phone.
Configuring Voice VLAN
These sections contain this configuration information:
- Default Voice VLAN Configuration
- Voice VLAN Configuration Guidelines
- Configuring a Port Connected to a Cisco 7960 IP Phone
Default Voice VLAN Configuration
The voice VLAN feature is disabled by default.
When the voice VLAN feature is enabled, all untagged traffic is sent according to the default CoS priority of the port.
The CoS value is not trusted for IEEE 802.1p or IEEE 802.1Q tagged traffic.
Voice VLAN Configuration Guidelines
These are the voice VLAN configuration guidelines:
- Voice VLAN configuration is only supported on switch access ports; voice VLAN configuration is not supported on trunk ports.

Note![]() Trunk ports can carry any number of voice VLANs, similar to regular VLANs. The configuration of voice VLANs is not required on trunk ports.
Trunk ports can carry any number of voice VLANs, similar to regular VLANs. The configuration of voice VLANs is not required on trunk ports.
- The voice VLAN should be present and active on the switch for the IP phone to correctly communicate on the voice VLAN. Use the show vlan privileged EXEC command to see if the VLAN is present (listed in the display). If the VLAN is not listed, see “Configuring VLANs,” for information on how to create the voice VLAN.
- Do not configure voice VLAN on private VLAN ports.
- The Power over Ethernet (PoE) switches are capable of automatically providing power to Cisco pre-standard and IEEE 802.3af-compliant powered devices if they are not being powered by an AC power source. For information about PoE interfaces, see the “Configuring a Power Management Mode on a PoE Port” section.
- Before you enable voice VLAN, we recommend that you enable QoS on the switch by entering the mls qos global configuration command and configure the port trust state to trust by entering the mls qos trust cos interface configuration command. If you use the auto-QoS feature, these settings are automatically configured. For more information, see Chapter1, “Configuring QoS”
- You must enable CDP on the switch port connected to the Cisco IP Phone to send the configuration to the phone. (CDP is globally enabled by default on all switch interfaces.)
- The Port Fast feature is automatically enabled when voice VLAN is configured. When you disable voice VLAN, the Port Fast feature is not automatically disabled.
- If the Cisco IP Phone and a device attached to the phone are in the same VLAN, they must be in the same IP subnet. These conditions indicate that they are in the same VLAN:
–![]() They both use IEEE 802.1p or untagged frames.
They both use IEEE 802.1p or untagged frames.
–![]() The Cisco IP Phone uses IEEE 802.1p frames, and the device uses untagged frames.
The Cisco IP Phone uses IEEE 802.1p frames, and the device uses untagged frames.
–![]() The Cisco IP Phone uses untagged frames, and the device uses IEEE 802.1p frames.
The Cisco IP Phone uses untagged frames, and the device uses IEEE 802.1p frames.
–![]() The Cisco IP Phone uses IEEE 802.1Q frames, and the voice VLAN is the same as the access VLAN.
The Cisco IP Phone uses IEEE 802.1Q frames, and the voice VLAN is the same as the access VLAN.
- The Cisco IP Phone and a device attached to the phone cannot communicate if they are in the same VLAN and subnet but use different frame types because traffic in the same subnet is not routed (routing would eliminate the frame type difference).
- Voice VLAN ports can also be these port types:
–![]() Dynamic access port. See the “Configuring Dynamic-Access Ports on VMPS Clients” section for more information.
Dynamic access port. See the “Configuring Dynamic-Access Ports on VMPS Clients” section for more information.
–![]() IEEE 802.1x authenticated port. See the “Configuring 802.1x Readiness Check” section for more information.
IEEE 802.1x authenticated port. See the “Configuring 802.1x Readiness Check” section for more information.

Note If you enable IEEE 802.1x on an access port on which a voice VLAN is configured and to which a Cisco IP Phone is connected, the phone loses connectivity to the switch for up to 30 seconds.
–![]() Protected port. See the “Configuring Protected Ports” section for more information.
Protected port. See the “Configuring Protected Ports” section for more information.
–![]() A source or destination port for a SPAN or RSPAN session.
A source or destination port for a SPAN or RSPAN session.
–![]() Secure port. See the “Configuring Port Security” section for more information.
Secure port. See the “Configuring Port Security” section for more information.

Note When you enable port security on an interface that is also configured with a voice VLAN, you must set the maximum allowed secure addresses on the port to two plus the maximum number of secure addresses allowed on the access VLAN. When the port is connected to a Cisco IP Phone, the phone requires up to two MAC addresses. The phone address is learned on the voice VLAN and might also be learned on the access VLAN. Connecting a PC to the phone requires additional MAC addresses.
Configuring a Port Connected to a Cisco 7960 IP Phone
Because a Cisco 7960 IP Phone also supports a connection to a PC or other device, a port connecting the switch to a Cisco IP Phone can carry mixed traffic. You can configure a port to decide how the Cisco IP Phone carries voice traffic and data traffic.
Configuring Cisco IP Phone Voice Traffic
You can configure a port connected to the Cisco IP Phone to send CDP packets to the phone to configure the way in which the phone sends voice traffic. The phone can carry voice traffic in IEEE 802.1Q frames for a specified voice VLAN with a Layer 2 CoS value. It can use IEEE 802.1p priority tagging to give voice traffic a higher priority and forward all voice traffic through the native (access) VLAN. The Cisco IP Phone can also send untagged voice traffic or use its own configuration to send voice traffic in the access VLAN. In all configurations, the voice traffic carries a Layer 3 IP precedence value (the default is 5).
Beginning in privileged EXEC mode, follow these steps to configure voice traffic on a port:
This example shows how to configure a port connected to a Cisco IP Phone to use the CoS value to classify incoming traffic and to accept voice and data priority traffic tagged with VLAN ID 0:
To return the port to its default setting, use the no switchport voice vlan interface configuration command.
This example shows how to enable switchport voice detect on a Cisco IP Phone:
This example shows how to disable switchport voice detect on a Cisco IP Phone:
Configuring the Priority of Incoming Data Frames
You can connect a PC or other data device to a Cisco IP Phone port. To process tagged data traffic (in IEEE 802.1Q or IEEE 802.1p frames), you can configure the switch to send CDP packets to instruct the phone how to send data packets from the device attached to the access port on the Cisco IP Phone. The PC can generate packets with an assigned CoS value. You can configure the phone to not change (trust) or to override (not trust) the priority of frames arriving on the phone port from connected devices.
Beginning in privileged EXEC mode, follow these steps to set the priority of data traffic received from the nonvoice port on the Cisco IP Phone:
This example shows how to configure a port connected to a Cisco IP Phone to not change the priority of frames received from the PC or the attached device:
To return the port to its default setting, use the no switchport priority extend interface configuration command.
Displaying Voice VLAN
To display voice VLAN configuration for an interface, use the show interfaces interface-id switchport privileged EXEC command.
 Feedback
Feedback