Prerequisites for Private VLANs
The following are prerequisites for configuring private VLANs:
-
When you configure private VLANs on switches running VTP, the switch must be in VTP transparent mode.
-
When configuring private VLANs on the switch, always use the default Switch Database Management (SDM) template to balance system resources between unicast routes and Layer 2 entries. If another SDM template is configured, use the sdm prefer default global configuration command to set the default template.
Secondary and Primary VLAN Configuration
Follow these guidelines when configuring private VLANs:
-
Private VLANs are supported in transparent mode for VTP 1, 2 and 3. If the device is running VTP version 1 or 2, you must set VTP to transparent mode. After you configure a private VLAN, you should not change the VTP mode to client or server. VTP version 3 supports private VLANs in all modes.
-
With VTP version 1 or 2, after you have configured private VLANs, use the copy running-config startup config privileged EXEC command to save the VTP transparent mode configuration and private-VLAN configuration in the device startup configuration file. Otherwise, if the device resets, it defaults to VTP server mode, which does not support private VLANs. VTP version 3 does support private VLANs.
-
VTP version 1 and 2 do not propagate private-VLAN configuration. You must configure private VLANs on each device where you want private-VLAN ports unless the devices are running VTP version 3, as VTP3 propagate private vlans.
-
You cannot configure VLAN 1 or VLANs 1002 to 1005 as primary or secondary VLANs. Extended VLANs (VLAN IDs 1006 to 4094) can belong to private VLANs.
-
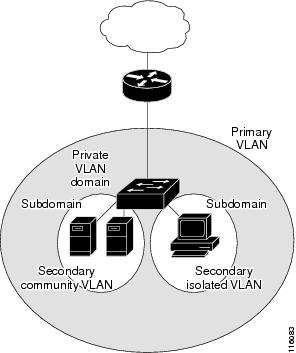
A primary VLAN can have one isolated VLAN and multiple community VLANs associated with it. An isolated or community VLAN can have only one primary VLAN associated with it.
-
Although a private VLAN contains more than one VLAN, only one Spanning Tree Protocol (STP) instance runs for the entire private VLAN. When a secondary VLAN is associated with the primary VLAN, the STP parameters of the primary VLAN are propagated to the secondary VLAN.
-
When copying a PVLAN configuration from a tftp server and applying it on a running-config, the PVLAN association will not be formed. You will need to check and ensure that the primary VLAN is associated to all the secondary VLANs.
You can also use configure replace flash:config_file force instead of copy flash:config_file running-config .
-
You can enable DHCP snooping on private VLANs. When you enable DHCP snooping on the primary VLAN, it is propagated to the secondary VLANs. If you configure DHCP on a secondary VLAN, the configuration does not take effect if the primary VLAN is already configured.
-
When you enable IP source guard on private-VLAN ports, you must enable DHCP snooping on the primary VLAN.
-
We recommend that you prune the private VLANs from the trunks on devices that carry no traffic in the private VLANs.
-
You can apply different quality of service (QoS) configurations to primary, isolated, and community VLANs.
-
Note the following considerations for sticky ARP:
-
Sticky ARP entries are those learned on SVIs and Layer 3 interfaces. These entries do not age out.
-
The ip sticky-arp global configuration command is supported only on SVIs belonging to private VLANs.
-
The ip sticky-arp interface configuration command is only supported on:
-
Layer 3 interfaces
-
SVIs belonging to normal VLANs
-
SVIs belonging to private VLANs
For more information about using the ip sticky-arp global configuration and the ip sticky-arp interface configuration commands, see the command reference for this release.
-
-
-
You can configure VLAN maps on primary and secondary VLANs. However, we recommend that you configure the same VLAN maps on private-VLAN primary and secondary VLANs.
-
PVLANs are bidirectional. They can be applied at both the ingress and egress sides.
When a frame inLayer-2 is forwarded within a private VLAN, the VLAN map is applied at the ingress side and at the egress side. When a frame is routed from inside a private VLAN to an external port, the private-VLAN map is applied at the ingress side. Similarly, when the frame is routed from an external port to a Private VLAN, the private-VLAN is applied at the egress side.
Bridging
-
For upstream traffic from secondary VLAN to primary VLAN, the MAP of the secondary VLAN is applied on the ingress side and the MAP of the primary VLAN is applied on the egress side.
-
For downstream traffic from primary VLAN to secondary VLAN, the MAP of the primary VLAN is applied in the ingress direction and the MAP of the secondary VLAN is applied in the egress direction.
Routing
If we have two private VLAN domains - PV1 (sec1, prim1) and PV2 (sec2, prim2). For frames routed from PV1 to PV2:
-
The MAP of sec1 and L3 ACL of prim1 is applied in the ingress port .
-
The MAP of sec1 and L3 ACL of prim2 is applied in the egress port.
-
For packets going upstream or downstream from isolated host port to promiscuous port, the isolated VLAN’s VACL is applied in the ingress direction and primary VLAN’S VACL is applied in the egress direction. This allows user to configure different VACL for different secondary VLAN in a same primary VLAN domain.
To filter out specific IP traffic for a private VLAN, you should apply the VLAN map to both the primary and secondary VLANs.
-
-
You can apply router ACLs only on the primary-VLAN SVIs. The ACL is applied to both primary and secondary VLAN Layer 3 traffic.
-
Although private VLANs provide host isolation at Layer 2, hosts can communicate with each other at Layer 3.
-
Private VLANs support these Switched Port Analyzer (SPAN) features:
-
You can configure a private-VLAN port as a SPAN source port.
-
You can use VLAN-based SPAN (VSPAN) on primary, isolated, and community VLANs or use SPAN on only one VLAN to separately monitor egress or ingress traffic.
-
Private VLAN Port Configuration
Follow these guidelines when configuring private VLAN ports:
-
Use only the private VLAN configuration commands to assign ports to primary, isolated, or community VLANs. Layer 2 access ports assigned to the VLANs that you configure as primary, isolated, or community VLANs are inactive while the VLAN is part of the private VLAN configuration. Layer 2 trunk interfaces remain in the STP forwarding state.
-
Do not configure ports that belong to a PAgP or LACP EtherChannel as private VLAN ports. While a port is part of the private VLAN configuration, any EtherChannel configuration for it is inactive.
-
Enable Port Fast and BPDU guard on isolated and community host ports to prevent STP loops due to misconfigurations and to speed up STP convergence. When enabled, STP applies the BPDU guard feature to all Port Fast-configured Layer 2 LAN ports. Do not enable Port Fast and BPDU guard on promiscuous ports.
-
If you delete a VLAN used in the private VLAN configuration, the private VLAN ports associated with the VLAN become inactive.
-
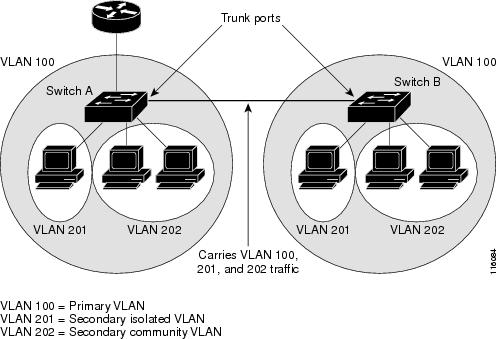
Private VLAN ports can be on different network devices if the devices are trunk-connected and the primary and secondary VLANs have not been removed from the trunk.

 Feedback
Feedback