New and Changed Information
The following table provides an overview of the significant changes up to this current release. The table does not provide an exhaustive list of all changes or the new features up to this release.
|
Cisco APIC Release Version |
Feature |
Description |
|---|---|---|
|
Release 3.2(1) |
This feature was introduced |
-- |
About TWAMP
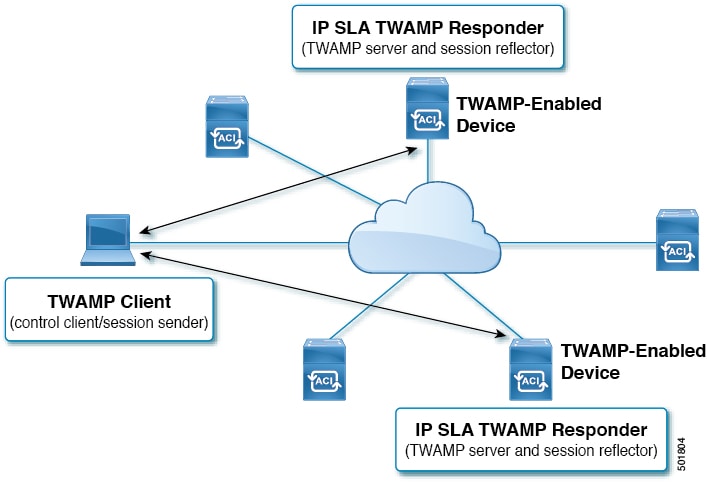
The Two-Way Active Measurement Protocol (TWAMP) defines a standard (RFC 5357) for measuring round-trip network performance between any two devices that support the TWAMP protocols. The TWAMP Server/Reflector is supported as part of the IP SLA responder in NX-OS. Cisco APIC configures the TWAMP support for switch groups and provides the monitoring of the test sessions and connections.
The devices must support the following TWAMP protocols:
-
TWAMP-Control Protocol: Set up performance measurement sessions
-
TWAMP-Test Protocol: Send and receive performance-measurement probes
Guidelines and Limitations for Configuring TWAMP
Follow these guidelines and limitations when configuring and using TWAMP:
-
The TWAMP client resides on an open-source third-party TWAMP utility application that must be reachable by any of the switch nodes through a management port, in-band management port, or L3 Out interface.
TWAMP GUI Configuration
Creating TWAMP Policies Using the GUI
Creating a TWAMP Responder Policy
Procedure
| Step 1 |
Choose Fabric > Fabric Policies. |
| Step 2 |
In the Navigation pane, choose Policies > Switch > TWAMP Responder Policies. |
| Step 3 |
Select the default responder policy or create a new one by performing the following actions:
|
| Step 4 |
Click Submit. |
The new responder policy appears as a row in the TWAMP Responder Policies summary table and is now available to be included in leaf/spine policy groups.
Creating a TWAMP Server Policy
Procedure
| Step 1 |
In the Navigation pane, choose TWAMP Server Policies. |
| Step 2 |
Select the default server policy or create a new one by performing the following actions:
|
| Step 3 |
Click Submit. |
The new server policy appears as a row in the TWAMP Server Policies summary table and is now available to be included in leaf/spine policy groups.
Adding TWAMP Policies to Leaf/Spine Policy Groups Using the GUI
The following procedure associates TWAMP policies with a leaf/spine policy group.
Before you begin
Procedure
| Step 1 |
Choose Fabric > Fabric Policies. |
| Step 2 |
In the Navigation pane, choose Switches > Leaf (or Spine) Switches > Policy Groups. |
| Step 3 |
Select an existing policy group or create and select a new one. |
| Step 4 |
In the Leaf/Spine Policy Group work pane, select a policy from the TWAMP Server Policy drop-down list. |
| Step 5 |
Select a policy from the TWAMP Responder Policy drop-down list. |
| Step 6 |
Click Submit. |
This leaf/spine policy group with the associated TWAMP policies can now be associated with a leaf/spine profile.
Associating a TWAMP-Enabled Leaf/Spine Profile with a Policy Group Using the GUI
Before you begin
You can use the Cisco APIC GUI to associate TWAMP enabled leaf or spine profiles with policy groups.
Procedure
| Step 1 |
Choose Fabric > Fabric Policies. |
| Step 2 |
In the Navigation pane, choose Switches > Leaf (or Spine) Switches > Profiles. |
| Step 3 |
Select an existing profile or create and select a new one. |
| Step 4 |
In the Leaf/Spine Switch Profile work pane, click + in the Switch Associations summary table and perform the following actions:
|
After completing this procedure, a third-party, an open-source TWAMP tool that generates test sessions can now be used. Once the test sessions are initiated, follow the instructions in Viewing TWAMP Connections and Sessions Using the GUI.
Viewing TWAMP Connections and Sessions Using the GUI
Procedure
| Step 1 |
Choose Fabric > Inventory. |
| Step 2 |
In the Navigation pane, choose Pod > leaf/spine_name > Protocols > TWAMP. |
| Step 3 |
Select TWAMP Connections to view a summary list of TWAMP connections. Select a specific TWAMP connection to view details. |
| Step 4 |
Select TWAMP Sessions to view a summary list of TWAMP sessions. Select a specific TWAMP session to view details. |
TWAMP NX-OS-Style CLI Configuration
Creating TWAMP Responder and Server Policies Using the NX-OS-Style CLI
Procedure
| Step 1 |
Enter the global configuration mode. Example: |
| Step 2 |
Create a new TWAMP responder policy. Example:In the following command, a TWAMP responder policy named "resp-1" is created: |
| Step 3 |
Enable the newly created TWAMP responder policy Example:In the following command, the new TWAMP responder policy is enabled: |
| Step 4 |
(Optional) Configure a timeout for the responder policy. Example:In the following command example, a timeout of 600 seconds (10 minutes) is configured for the responder policy: |
| Step 5 |
Exit from the TWAMP responder policy mode. Example: |
| Step 6 |
Create a new TWAMP server policy. Example:In the following command, a TWAMP server policy named "serv-1" is created: |
| Step 7 |
Enable the newly created TWAMP responder policy Example:In the following command, the new TWAMP responder policy is enabled: |
| Step 8 |
(Optional) Configure an inactivity timer for the server policy. Set the value to the number of seconds after which the server checks the activity of a responder test session. If the test session is inactive, the server marks it for "clean up" at the next interval. Command characteristics:
Example:In the following command example, an inactivity timer of 600 seconds (10 minutes) is configured for the server policy: |
The new responder and server policies are now available to be included in leaf/spine policy groups.
Adding TWAMP Policies to Leaf/Spine Policy Groups Using the NX-OS-Style CLI
Before you begin
Procedure
| Step 1 |
Enter the global configuration mode. Example: |
||
| Step 2 |
Enter the internal fabric configuration mode. Example: |
||
| Step 3 |
(Optional) Enter a leaf policy group configuration mode. Example:In the following command, the configuration mode of a leaf policy group named "lpg-1" is entered: |
||
| Step 4 |
(Optional) Enter a spine policy group configuration mode. Example:In the following command, the configuration mode of a spine policy group named "spg-1" is entered: |
||
| Step 5 |
Enter the TWAMP policy you want associated with the leaf or spine policy group. Example:In the following command, TWAMP server policy named "serv-1" is associated with the spine policy group:
|
Associating a Leaf Profile with a TWAMP-Enabled Leaf Policy Group Using the NX-OS-Style CLI
Procedure
| Step 1 |
Enter the global configuration mode. Example: |
| Step 2 |
Enter the internal fabric configuration mode. Example: |
| Step 3 |
Create or enter a leaf profile configuration mode. Example:In the following command, the configuration mode of a leaf profile named "leaf-prof-1" is entered: |
| Step 4 |
Enter a leaf group configuration mode. Example:In the following command, the configuration mode of a leaf group named "leaf-group-1" is entered: |
| Step 5 |
Enter the name of the leaf policy group containing the TWAMP policies. Example:In the following command, a leaf policy group named "lpg-1" is associated with the leaf profile: |
Associating a Spine Profile with a TWAMP-Enabled Spine Policy Group Using the NX-OS-Style CLI
Procedure
| Step 1 |
Enter the global configuration mode. Example: |
| Step 2 |
Enter the internal fabric configuration mode. Example: |
| Step 3 |
Create or enter a spine profile configuration mode. Example:In the following command, the configuration mode of a spine profile named "spine-prof-1" is entered: |
| Step 4 |
Enter a spine group configuration mode. Example:In the following command, the configuration mode of a spine group named "spine-group-1" is entered: |
| Step 5 |
Enter the name of the spine policy group containing the TWAMP policies. Example:In the following command, a spine policy group named "spg-1" is associated with the spine profile: |
Viewing TWAMP Connections and Sessions Using the NX-OS-Style CLI
Before you begin
Procedure
| Step 1 |
View a TWAMP connection. Example:Resulting in the following output: |
| Step 2 |
View a TWAMP session. Example:Resulting in the following output: |
TWAMP REST API Configuration
Creating TWAMP Policies Using the REST API
Procedure
|
Create a TWAMP responder and server policy. Example:Example: |
Adding TWAMP Policies to Leaf/Spine Policy Groups Using the REST API
Before you begin
Procedure
|
Add a TWAMP responder and server policy to a leaf and spine policy group. Example:Example: |
Associating a Leaf/Spine Profile with a TWAMP-Enabled Policy Group Using the REST API
Before you begin
Procedure
|
Associate a leaf profile with a TWAMP-enabled leaf policy group or a spine profile with a TWAMP-enabled spine policy group. Example:Example: |
Viewing TWAMP Connections and Sessions Using the REST API
Procedure
|
View TWAMP connection or session information for a specific leaf or spine. Example:Example: |
 Feedback
Feedback