Getting Started
About This Guide
This document, which is applicable for onboarding Secure Workload:
-
Introduces the key Secure Workload concepts: Segmentation, Workload labels, Scopes, Hierarchical scope trees, and Policy discovery.
-
Explains the process of creating the first branch of your scope tree using the first-time user experience wizard.
-
Describes the automated process of generating policies for the chosen application that is based on actual traffic flows.
Overview of Secure Workload
Traditionally, network security is aimed at keeping malicious activities out of network with firewalls around the edge of your network. However, you also need to protect your organization from threats that have breached your network or originated within it. Segmentation or microsegmentation of the network helps to protect your workloads through controlling traffic between workloads and other hosts on your network; therefore, allowing only traffic that your organization would require for business purposes, and deny all other traffic.
Cisco Secure Workload uses the organization’s flow data to suggest policies that you can evaluate and approve before enforcing them. Alternatively, you can also manually create these policies for segmenting your network.
For example, you can use policies to prevent all communication between the workloads that host your public-facing web application from communicating with the research and development database in your data center, or to prevent non-production workloads from contacting the production workloads.
Introduction to Security Cloud Control
Cisco Security Cloud Control is a unified platform designed to manage your security products and deliver security outcomes through a single, integrated interface. Using this platform, you can manage Secure Workload along with other security solutions. It offers shared services across all products, eliminating the need for administrators to configure each product individually.
Key common services provided by Security Cloud Control include:
-
User provisioning and role assignment
-
Subscription management for all enrolled products
-
Guided workflows to help your organization quickly implement essential tasks
-
Global search functionality across all onboarded products to maintain consistent security policies
-
Seamless navigation between different products
-
AI-powered assistance to enhance user experience
Manage Secure Workload in Security Cloud Control
This section provides steps for users to access Cisco Secure Workload application from Cisco Security Cloud Control. Follow the steps below to get started:
-
Sign in to Security Cloud Control using the Security Cloud Sign on account. Create an account if you do not have one.
To create a Security Cloud Sign On account, provide an email address to where the account activation email will be sent. Every user account is required to use multifactor authentication (MFA) for account authentication. You can either use a Duo MFA, which is included with Security Cloud Sign On account at no extra charge, or use a one-time password (time-based) from the Google Authenticator application.
For information on how to create a Security Cloud Sign On account, see Security Cloud Sign On.

Note
-
Create an Enterprise and define the preferred region for that enterprise. You can create multiple organizations, each with their own set of users, products, and other organization data.
-
Enter the claim code that you receive in the Security Cloud Control welcome email in order to claim subscriptions for the product instances. For more information, see Claim your Product Subscription. Activate the new product instances.

Note
In case you need to understand the claim subscription process, see the Overview of the Claim Subscription.
-
Choose the home page for your product after you create the organization and claim the product subscription.
-
Add a domain to your product organization. For more information, see Add and Claim your Domain.
-
Integrate the identity provider with the Secure Cloud Sign On account.
For information to integrate the identity provider, see Integrate an Identity Provider.
-
Create users and groups; assign them roles for precise product management and control.
For information on role-based access, see Role-based Access Control.
Procedure
|
Step 1 |
From the Security Cloud Control navigation menu, choose Secure Workload. Please note that an Enterprise administrator will have access to the Cisco Secure Workload application. |
||
|
Step 2 |
After you login to the Secure Workload Dashboard, launch the Secure Workload application by clicking the Launch Secure Workload tab. 
|
||
|
Step 3 |
As the first step towards generating and enforcing policies for an application, access the Quick Start Wizard that introduces the concepts and benefits of labels and scopes. From within the Secure Workload application, access the Quick Start wizard to create the first branch of the scope tree. To access the wizard, do either of the following:
|
What to do next
For more information on how to create scopes and inventory, see Tour of the Wizard.
Tour of the Wizard
Welcome to Secure Workload where assigning labels and grouping your workloads is essential to the power of Secure Workload. In Secure Workload, onboarding is a user-friendly and guided approach to help you set up and deploy applications securely in your environment. You can segment your network to allow only the traffic that is required for your business, and block all other communications.
To help you get started, from the navigation menu, choose Overview to navigate to the Quick Start wizard. The wizard typically prepares Secure Workload to start creating segmentation policies to control traffic on your network, presents a series of steps, each focusing on a specific security aspect, and prompts users to make informed choices for configuring their workload securely.
The following user roles can access the wizard:
-
Site Administrator: Provides the ability to manage users, agents, and more. The site administrator can view and edit all features and data. There must be at least one site admin.
-
Customer Support: Provides access to cluster maintenance features. Allows the same access as a Site Administrator but cannot modify users. Typically for Technical Support or Advanced Services roles.
-
Scope Owner: Manages and defines the scope of workloads, ensures policy compliance, and oversees workload security within the designated scope.
For more information on roles and responsibilities, see the Secure Workload User Guide.
Install Software Agents
Cisco Secure Workload supports various types of software agents for different environments, including virtual machines, bare metal servers, containers, Windows servers, Windows desktops, Linux servers, Kubernetes, AIX, and Solaris systems. These agents provide deep visibility and enforcement capabilities. The agent installer can be downloaded directly from Secure Workload, and it supports installation, upgrade, and monitoring functionalities. For more information see the Cisco Secure Workload Guide.
You can install software agents on your application workloads. The software agents collect information about the network interfaces and the active processes running on the host system.
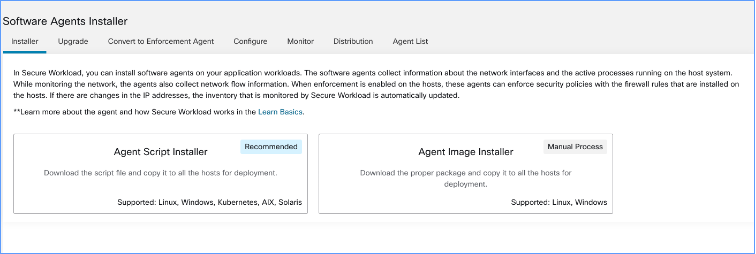
There are two ways how you can install the software agents:
-
Agent Script installer: Use this method for installing, tracking, and troubleshooting of issues while installing the software agents. Supported platforms are Linux, Windows, Kubernetes, AIX, and Solaris.
-
Agent Image installer: Download the software agent image to install a specific version and software agent type for your platform. Supported platforms are Linux and Windows.
The onboarding wizard walks you through the process of installing the agents based on the selected installer method. For information on software agent installation, see the instructions on the Secure Workload UI and the Secure Workload User Guide.
Group and Label Workloads
The organization assigns labels to a group of workloads to create a scope. The hierarchical scope tree helps to divide the workloads into smaller groups, while reserving the lowest branch in the scope tree for individual applications.
Select a parent scope from the scope tree to create a new scope, which contains a subset of the members from the parent scope.
On this window, organize your workloads into groups in a hierarchical structure. Break down your network into hierarchical groups to allow more flexibility and scalable policy discovery and definition.
The wizard helps to apply labels to their workloads, which are key parameters that describe a workload or endpoint represented as a key-value pair. These labels are then grouped into scopes, and workloads are automatically grouped into scopes based on their associated labels. You can define segmentation policies based on scopes.
Hover over each block or scope in the tree for more information about the type of workloads or hosts it includes.
 Note |
In the Get Started with Scopes and Labels window, Organization, Infrastructure, Environment and Application are the keys and the text in the gray boxes in-line with each key are the values. For example, all workloads belonging to Application 1 are defined by these set of labels:
|
Power of Labels and Scope Trees
Labels drive the power of Secure Workload, and the scope tree created from your labels is more than just a summary of your network. Few of the benefits of using labels are:
-
Labels let you instantly understand your policies, for example:
"Deny all traffic from Pre-Production to Production"Compare the same policy without labels, which is:
"Deny all traffic from 172.16.0.0/12 to 192.168.0.0/16" -
Policies based on labels automatically apply (or stop applying) when you add labeled workloads to (or removed from) inventory. Over time, these dynamic groupings based on labels greatly reduce the amount of effort required to maintain your deployment.
-
Workloads are grouped into scopes based on their labels. These groupings let you easily apply policy to related workloads. For example, you can easily apply policy to all applications in the Pre-Production scope.
-
After you create policies in a single scope, the policies can automatically be applied to all workloads in descendant scopes in the tree, minimizing the number of policies you must manage.
For example, you can easily define and apply policy broadly to all workloads in your organization or narrowly (which is on just the workloads that are part of a specific application) or to any level in between, for example, to all workloads in a data center.
-
You can assign responsibility for each scope to different administrators, delegating policy management to the people who are more familiar with your network.
Build the Hierarchy for Your Organization
Start building your hierarchy or scope tree; this involves identifying and categorizing the assets, determining the scope, defining roles and responsibilities, developing policies and procedures to create a branch of the scope tree.
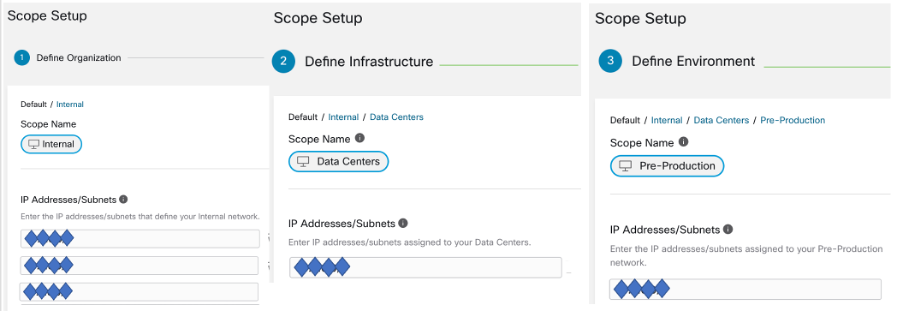
The wizard guides you through creating a branch of the scope tree. Enter IP addresses or subnets for each blue-outlined scope, the labels are automatically applied based on the scope tree.
Pre-requisites:
-
Gather IP Addresses or Subnets associated with your Pre-Production environment, your data centers, and your Internal network.
-
Gather as many IP addresses or subnets as you can, you can add the additional IP addresses or subnets later.
-
As you build your tree, you can add IP addresses or subnets for the other scopes in the tree (the gray blocks).
To create the scope tree, perform the following tasks:
Define the Internal Scope
The internal scope includes all IP addresses that define your organization's internal network, including public and private IP addresses.
The wizard walks you through adding IP addresses to each scope in the tree branch. As you add addresses, the wizard assigns labels to each address that defines the scope.
Organization=InternalBy default, the wizard adds the IP addresses in the private internet address space as defined in RFC 1918
 Note |
All the IP addresses need not be entered at once, but you must include the IP addresses associated with your chosen application, you can add the rest of the IP addresses at a later time. |
Define the Data Center Scope
This scope includes the IP addresses that define your on-premises data centers. Enter the IP addresses/subnets that define your internal network
 Note |
Scope names should be short and meaningful. |
On this window, enter the IP addresses that you have entered for the organization, these addresses must be a subset of the addresses for your internal network. If you have multiple data centers, include all of them in this scope so you can define a single set of policies.
 Note |
You can always add more addresses at a later stage. For instance, the wizard assigns these labels to each of the IP addresses: |
Define the Pre-Production Scope
This scope includes IP addresses of non-production applications and hosts, such as development, lab, test, or staging systems.
 Note |
Ensure you do not include addresses of any applications that are used to conduct actual business, use them for the production scope that you define later. |
The IP addresses you enter on this window must be a subset of the addresses you entered for your data centers, include the addresses of your chosen application. Ideally, they should also include pre-production addresses that are not part of the chosen application.
 Note |
You can always add more addresses at a later stage. |
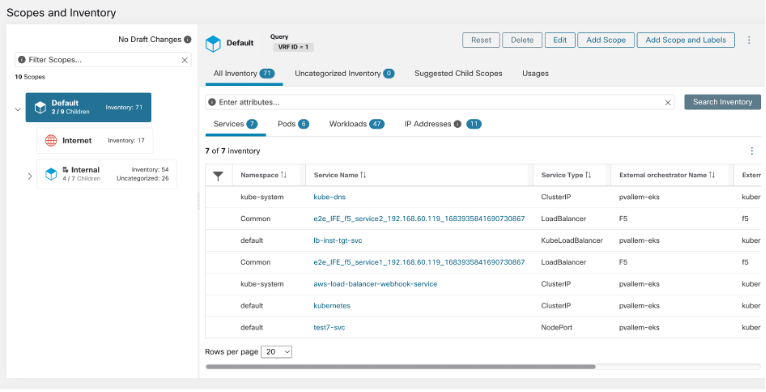
Review Scope Tree, Scopes, and Labels
Before you start creating the scope tree, review the hierarchy that you can see on the left window. The root scope shows labels that were automatically created for all configured IP addresses and subnets. At a later stage in the process, applications are added to this scope tree.
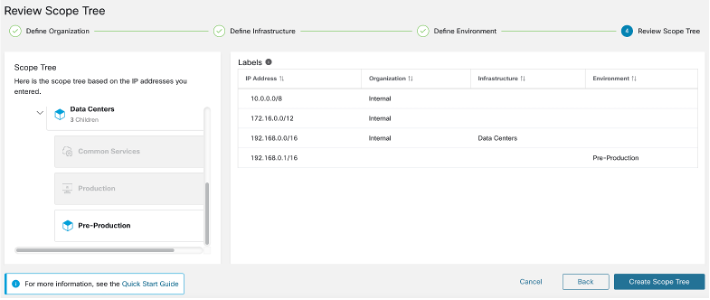
You can expand and collapse branches and scroll down to choose a specific scope. Onthe right pane, you can see the IP addresses and labels assigned to the workloads for the specific scope. On this window, you can review, modify the scope tree before you add an application to this scope.
 Note |
If you want to view this information after you exit the wizard, from the navigation menu, choose . |
Review Scope Tree
Before you start creating the scope tree, you must review the scope hierarchy. The root scope shows labels that were automatically created for all configured IP addresses and subnets. At a later stage in the process, applications are added to this scope tree.

You can expand and collapse branches and scroll down to choose a specific scope. On the right pane, you can see the IP addresses and labels assigned to the workloads for the specific scope. In this window, you can review and modify the scope tree before you add an application to the scope.
 Note |
If you want to view this information after you exit the wizard, from the navigation pane, choose Organize > Scopes and Inventory. |
Create Scope Tree
After you review the scope tree, create the scope tree.
For information on the scope tree, see the Scopes and Inventory section in the Secure Workload User Guide.
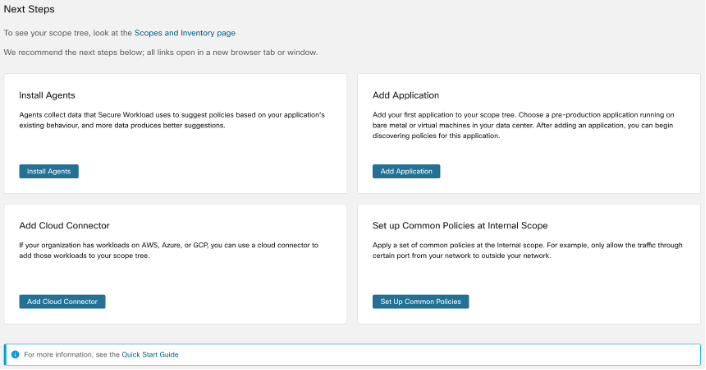
Next Steps
Install Agents
Install the SecureWorkload agents on the workloads associated with your chosen application.The data that the agents gather is used to generate suggested policies based on the existing traffic on your network. More the data, more accurate policies are produced. For details, see the Software Agents section in the Secure Workload user guide.
Add Application
Add the first application to your scope tree. Choose a pre-production application running on bare metal or virtual machines in your data center. After adding an application, you can begin discovering policies for this application. For more information, see the Scopes and Inventory section of the Secure Workload user guide.
Set up Common Policies at Internal Scope
Apply a set of common policies at the Internal scope. For example, only allow the traffic through certain port from your network to outside your network.
Users can define policies manually using Clusters, Inventory Filters and Scopes or these can be discovered and generated from flow data using Automatic Policy Discovery.
After you install agents and allow at least a few hours for traffic flow data to accumulate, you can enable Secure Workload to discover policies based on that traffic. For details, see Automatically Discover Policies section of the Secure Workload User Guide.
Apply these policies at Internal (or Inside or Root) scope to effectively review policies.
Add Cloud Connector
If your organization has workloads on AWS, Azure, or GCP, use a cloud connector to add the workloads to your scope tree. For more information, see the Cloud Connectors section in the Secure Workload User Guide.
Quick Start Workflow
|
Step |
Do This |
Details |
|---|---|---|
|
1 |
(Optional) Take an annotated tour of the wizard |
|
|
2 |
Choose an application to start your segmentation journey. |
For best results, follow the guidelines in Choose an Application. |
|
3 |
Gather IP addresses. |
The wizard will request 4 groups of IP addresses. For more information, see Gather IP Addresses. |
|
4 |
Run the wizard |
To view requirements and access the wizard, see Run the Wizard. |
|
5 |
Allow time for the agents to gather flow data. |
More data produces more accurate policies. The minimum amount of time required depends on how actively your application is used. |
|
6 |
Generate ("discover") policies based on your actual flow data. |
For information on how to generate policies, see Automatically Generate Policies. |
Gather IP Addresses
-
Addresses that define your internal network
By default, the wizard uses the standard addresses reserved for private internet use.
-
Addresses that are reserved for your data centers.
This does not include addresses used by employee computers, cloud or partner services, and centralized IT services.
-
Addresses that define your nonproduction network.
-
Addresses of the workloads that comprise your chosen nonproduction application.
For now, you do not need to have all the addresses; you can always add more addresses later.
 Important |
Because each of the four bulleted lists represents a subset of the IP addresses list, include IP addresses in each bulleted list among the IP addresses of the list. |
Choose an Application
Choose an application for the wizard. An application typically consists of multiple workloads that provide different services such as web services or databases, primary and backup servers. Together, these workloads provide the application's functionality to its users.
Guidelines for Choosing Your Application
Secure Workload supports workloads running on a wide range of platforms and operating systems, including cloud-based and containerized workloads. However, for this wizard, choose an application with workloads that are:
-
Running in your data center.
-
Running on bare metal and or on virtual machines.
-
Running on Windows, Linux, or AIX platforms supported with Secure Workload agents, see Compatibility Matrix.
-
Deployed in a preproduction environment.
 Note |
You can run the wizard even if you have not chosen an application and gathered IP addresses, but you cannot complete the wizard without doing these things. |
 Note |
If you do not complete the wizard before signing out (or timing out) or navigate to a different part of the Secure workload application (use the left navigation bar), the wizard configurations are not saved. |
For details about how to add a scope or add Scope and Labels, see the Scopes and Inventory section of the Cisco Secure Workload User Guide.
Run the Wizard
You can run the wizard whether or not you have chosen an application and gathered IP addresses, but you won't be able to complete the wizard without doing these things.
 Important |
If you don't complete the wizard before signing out (or timing out) of Secure Workload, or if you navigate to a different part of the application using the left navigation bar, wizard configurations are not saved. |
Before you begin
The following user roles can access the wizard:
-
site admin
-
customer support
-
scope owner
Procedure
|
Step 1 |
Sign in to Secure Workload. |
|
Step 2 |
Start the wizard: If you do not currently have any scopes defined, the wizard appears automatically when you sign in to Secure Workload. Alternatively:
If you have already created scopes, you cannot access the wizard again unless you delete all existing scopes. To do this, see (Optional) Reset the Scope Tree. |
|
Step 3 |
The wizard explains the things you need to know.
|
Automatically Generate Policies
Secure Workload generates or discovers policies based on existing traffic between workloads and other hosts. You can modify, supplement, analyze, and eventually approve and enforce policies on the workloads.
Before you begin
-
Install agents on your application's workloads.
-
Allow some time after agent installation for flow data to accumulate.
Procedure
|
Step 1 |
On the Next Steps page of the quick start wizard, click Automatically Generate Policies. Alternatively, you can do the following:
|
|
Step 2 |
Choose Manage Policies. |
|
Step 3 |
Choose Automatically Discover Policies. |
|
Step 4 |
Choose the time range for the flow data that you want to include: |
|
Step 5 |
Choose Discover Policies, the generated policies appear on this page. |
(Optional) Reset the Scope Tree
(Optional) You can delete the scopes, labels, and scope tree you created using the wizard and run the wizard again.
 Tip |
If you want to remove some of the created scopes and not run the wizard again, delete individual scopes instead of resetting the entire scope tree. To delete a scope, choose Scope and click Delete. |
Before you begin
Make sure you have the scope owner privileges for the root scope.
 Note |
If you have created more workspaces, policies, or other dependencies, see the Secure Workload user guide for complete information about resetting the scope tree. |
Procedure
|
Step 1 |
From the navigation menu, choose . |
|
Step 2 |
Click the scope at the top of the tree. |
|
Step 3 |
Click Reset. |
|
Step 4 |
Confirm your choice. |
|
Step 5 |
Refresh the browser page if the Reset button changes to Pending Reset. |
More Information
For more information about concepts in the wizard, see the Secure Workload User Guide.
 ).
).
 Feedback
Feedback