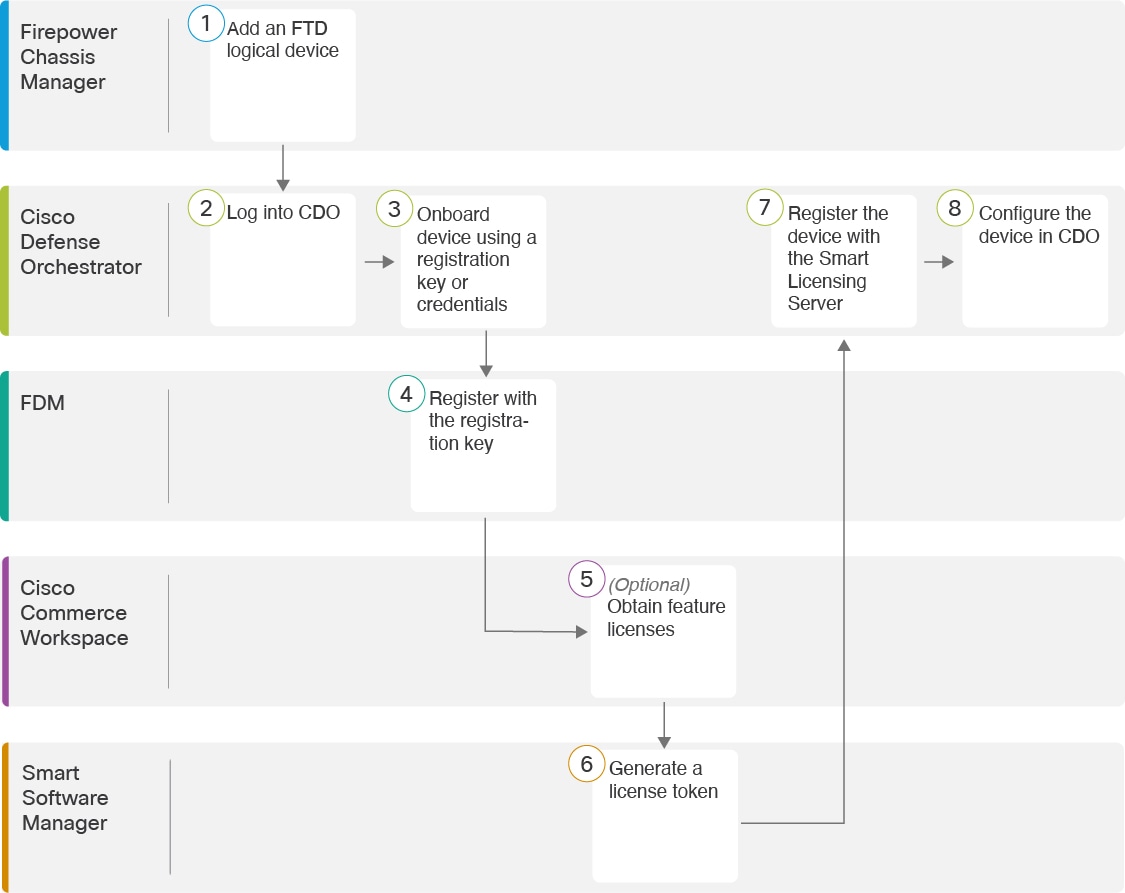
End-to-End Procedure
See the following tasks to deploy an FTD logical device and onboard the device to CDO.
|
Workspace |
Steps |
|
|---|---|---|
|
|
Firepower Chassis Manager |
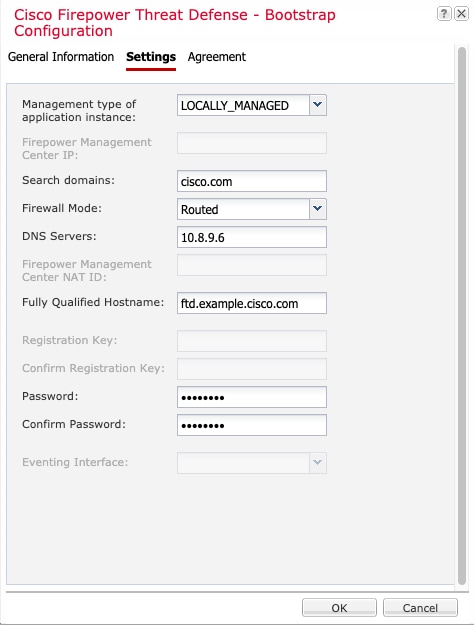
Firepower Chassis Manager: Add a Firepower Threat Defense Logical Device. |
|
|
Cisco Defense Orchestrator |
|
|
|
Cisco Defense Orchestrator |
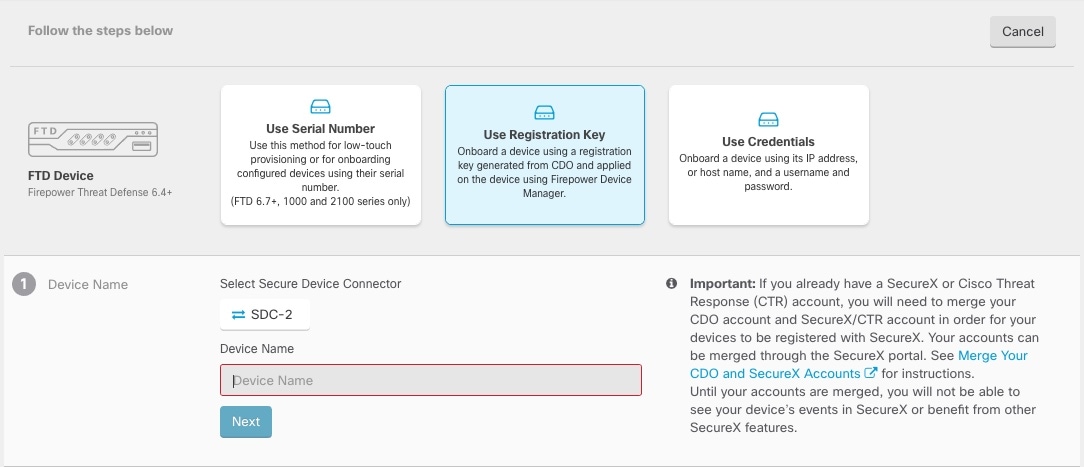
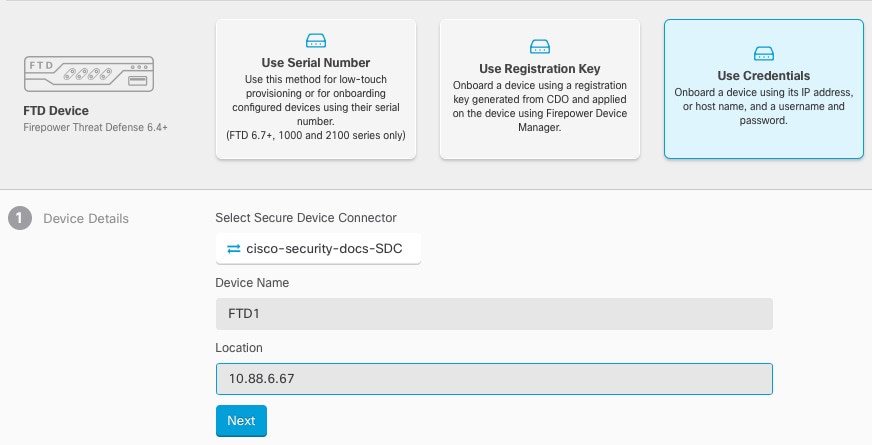
Onboard the device using a registration key or credentials (Onboard the FTD to CDO). |
|
|
Firepower Device Manager |
Register with the registration key (Onboard the FTD to CDO). If you onboard using credentials, you do not need to log into FDM. |
|
|
Cisco Commerce Workspace |
(Optional) Obtain feature licenses (Configure Licensing). |
|
|
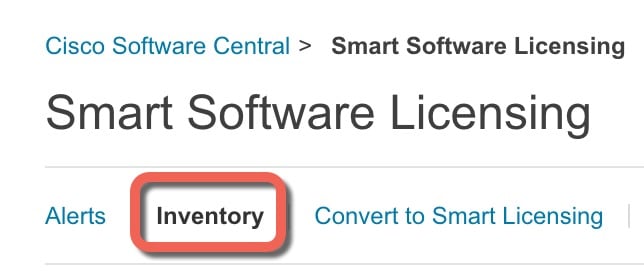
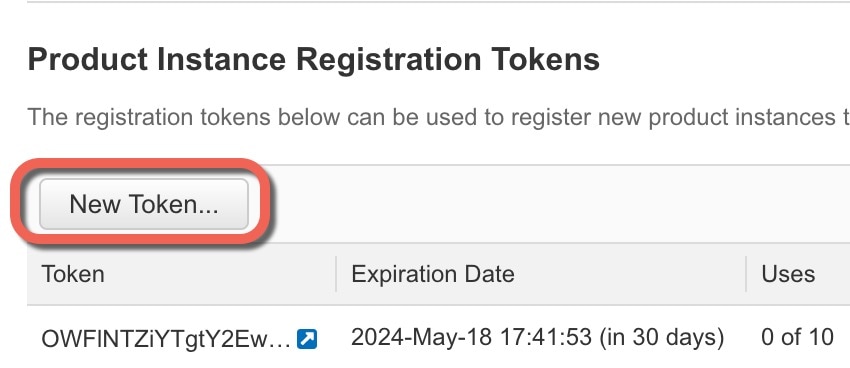
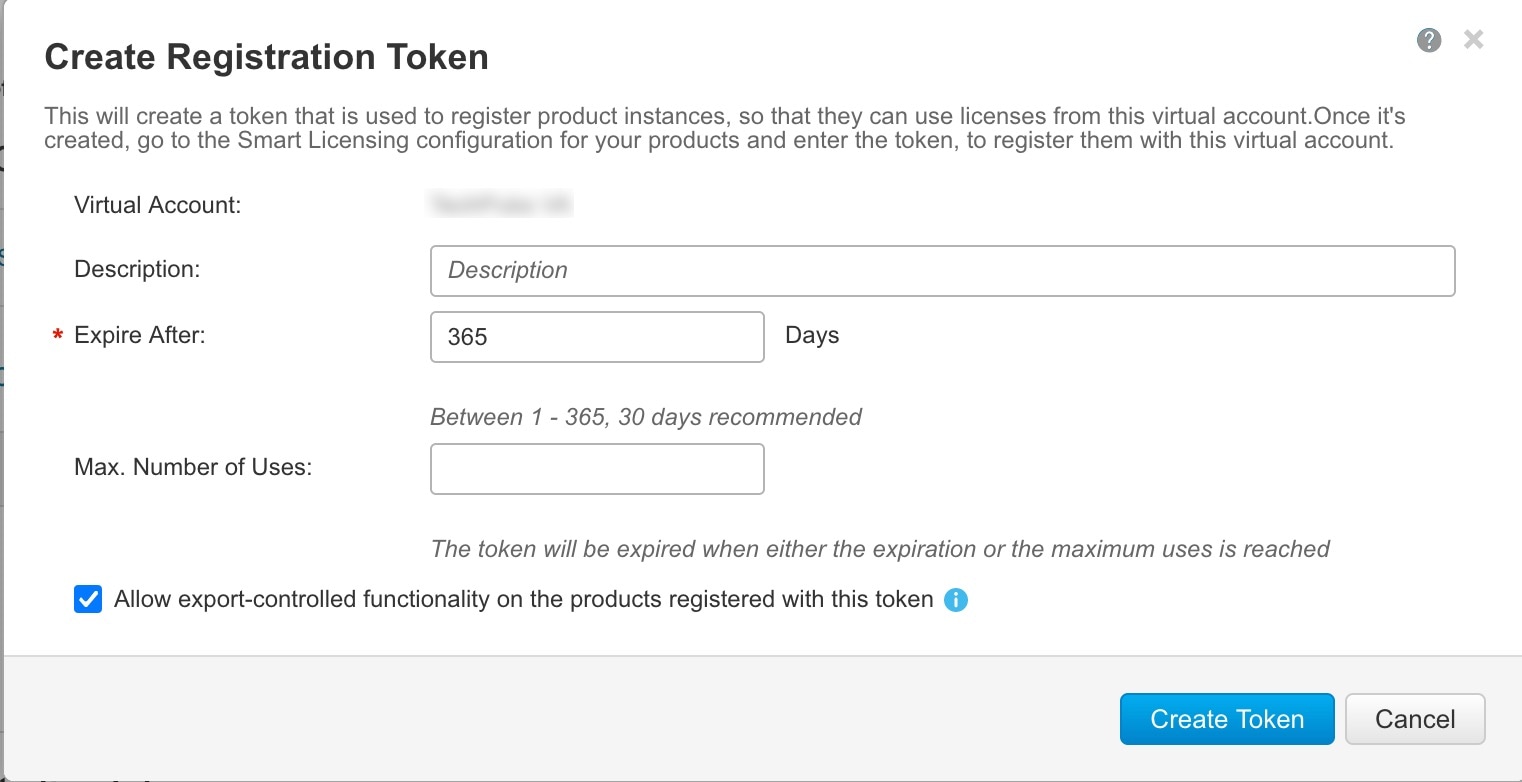
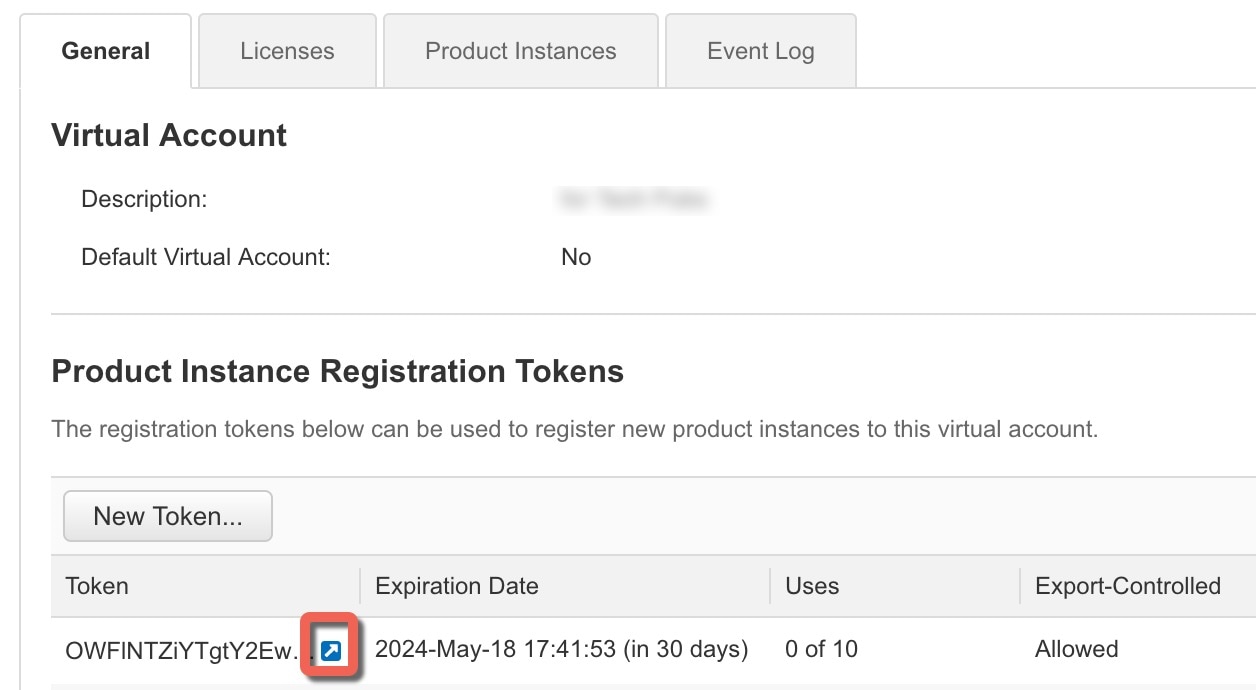
Smart Software Manager |
Generate a license token for the FTD (Configure Licensing). |
|
|
Cisco Defense Orchestrator |
Register the FTD with the Smart Licensing server, and enable feature licenses (Configure Licensing). |
|
|
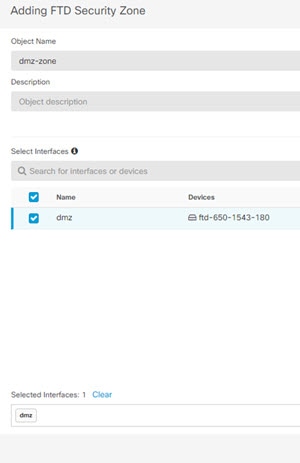
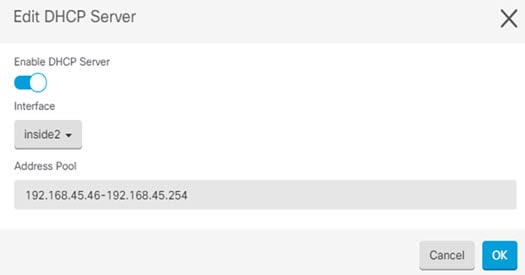
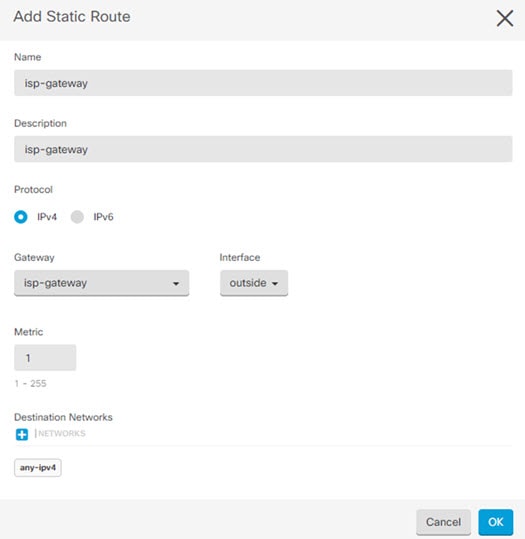
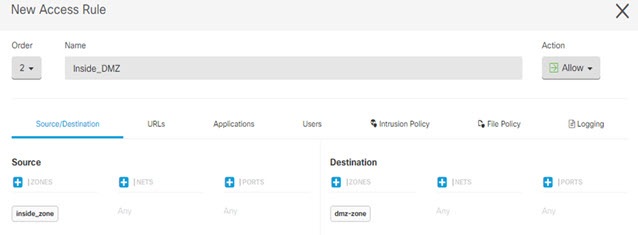
Cisco Defense Orchestrator |
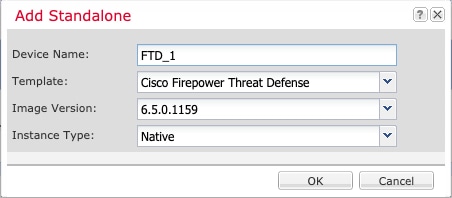
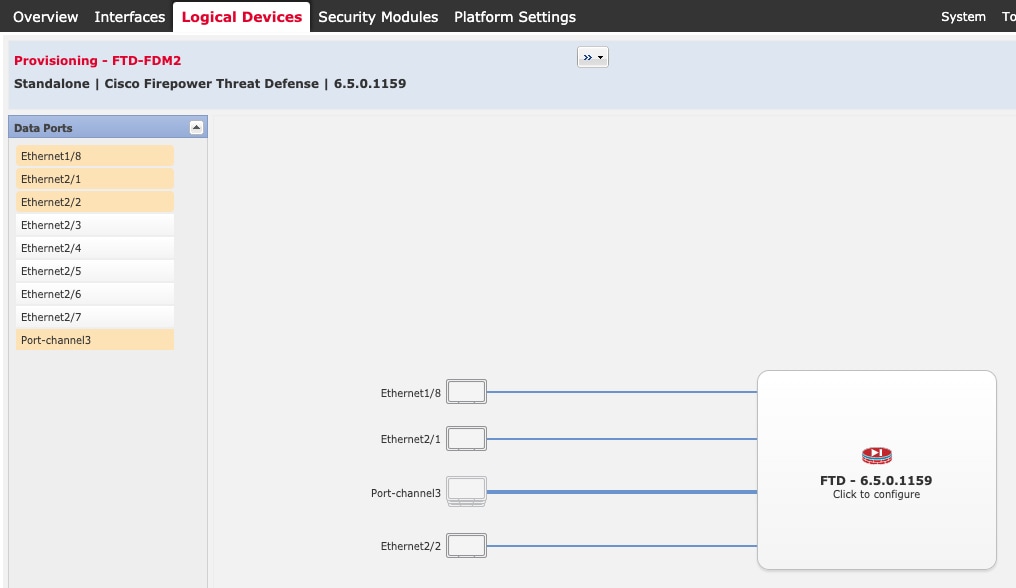
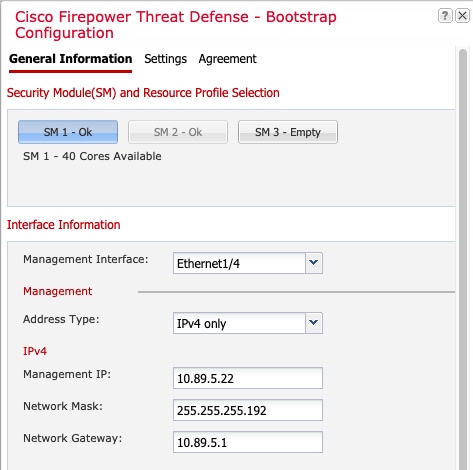

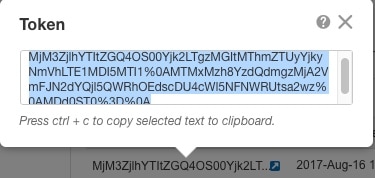

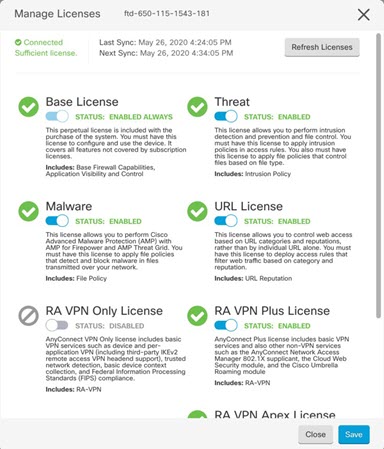
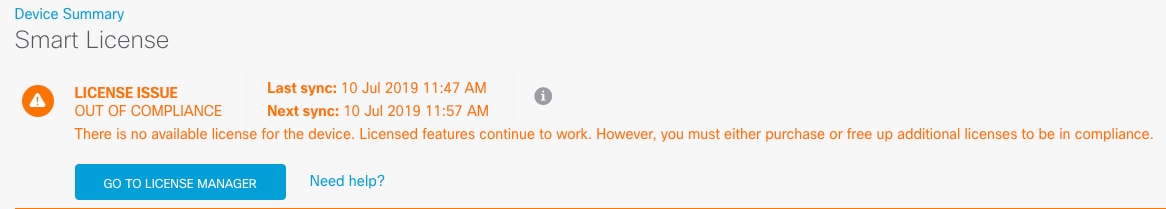
 ) for each interface you want to configure and give the interface a
) for each interface you want to configure and give the interface a 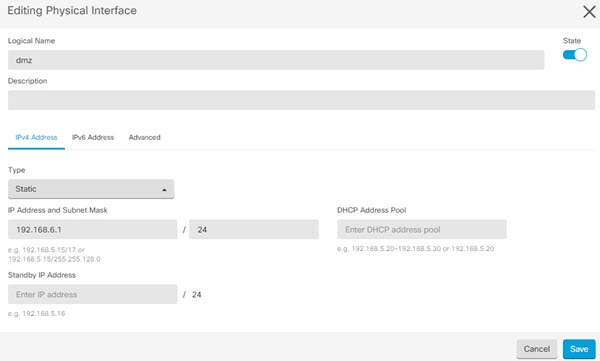
 Feedback
Feedback