Supported Versions
|
FTD Device Package Version |
Platform |
FTD/FMC Version |
ACI/APIC Version |
|---|---|---|---|
|
1.0.2 |
Firepower-93xx |
6.2.2 |
2.3(1f) 3.0(1k) |
|
1.0.2 |
Firepower-41xx |
6.2.2 |
2.3(1f) 3.0(1k) |
|
1.0.2 |
Firepower-21xx |
6.2.2 |
2.3(1f) 3.0(1k) |
|
1.0.2 |
vFTD |
6.2.2 |
2.3(1f) 3.0(1k) |
Import the Device Package
Sign in on Cisco.com to download and install the device package software. For instructions, see the Cisco FTD for ACI Quick Start Guide.
New Features in Version 1.0(2)
-
Virtual FTD VLAN trunking support
-
FTD High Availability (HA) support
-
Dynamic EPG update
-
Firepower 21xx support
-
Performance enhancements (FTD-DP scalability)
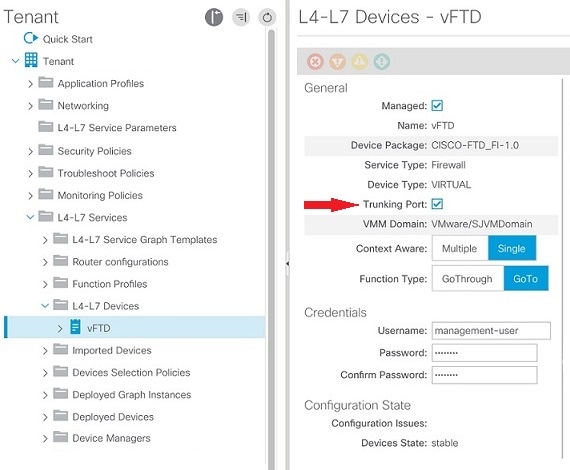
Virtual FTD VLAN Trunking Support
-
Create the L4-L7 Device for the Virtual FTD, and click Submit.
-
Navigate to the newly created vFTD, and notice the Trunking Port check box, which appears only after the virtual device has been created.
-
Select the Trunking Port check box to enable VLAN trunking on the vFTD.
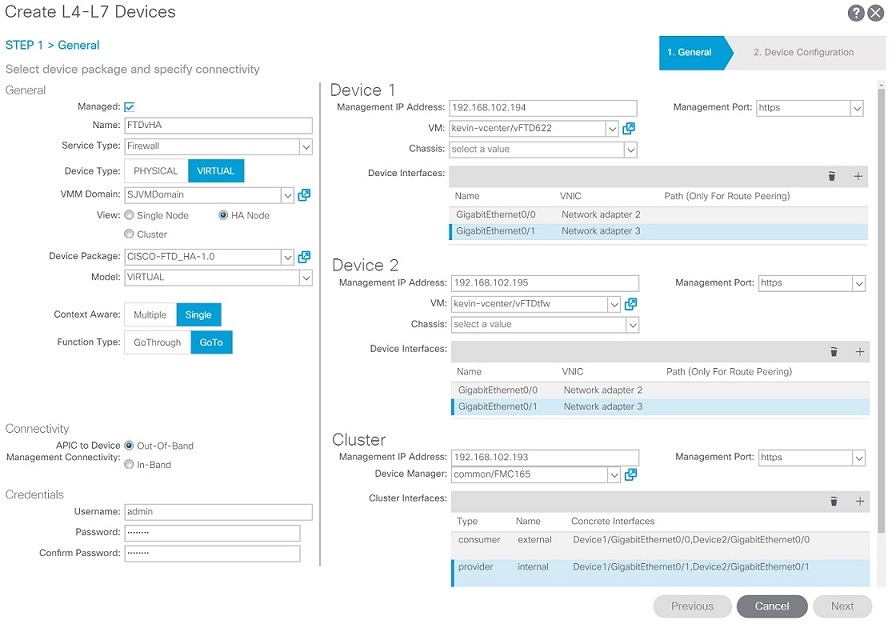
FTD High Availability (HA) Support
Must be pre-configured on the FMC.
On the APIC, when you Create L4-L7 Devices, in the Cluster section:
-
Management IP Address is the IP address of the FMC.
-
Device Manager is pre-defined on the FMC.
-
For Cluster Interfaces, specify the interfaces for both members of the HA pair.
Click "+" to enter information for each interface.
Click Update to add each interface.
-
Name: external
Type: consumer
Concrete Interfaces: Select Device1/GigabitEthernet0/0 and Device2/GigabitEthernet0/0
-
Name: internal
Type: provider
Concrete Interfaces: Select Device1/GigabitEthernet0/1 and Device2/GigabitEthernet0/1
-
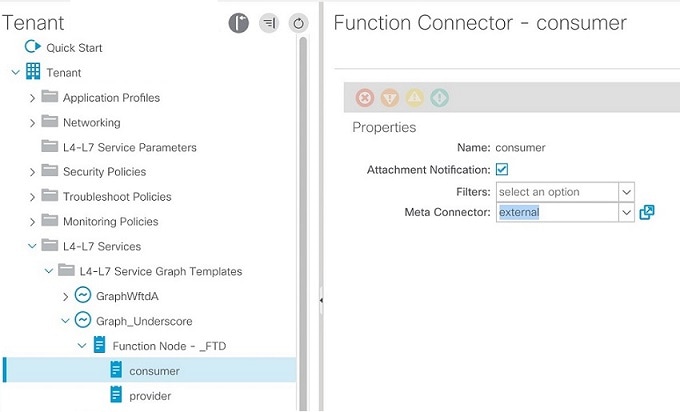
Dynamic EPG Update
Select the Attachment Notification check box to enable Dynamic EPG on the APIC:
Resolved Enhancement Requests in Version 1.0(2)
|
Caveat |
Description |
|---|---|
|
CSCvd94266 |
Handling serviceAudit call improved in FTD-DP ftd-device-pkg |
|
CSCvf02605 |
Support automatic HA deployment in FTD-DP |
|
CSCvf71967 |
Support VLAN Trunking on virtual FTDs ftd-device-pkg |
|
CSCvf91529 |
Changed the '+' sign in the logical interface name to '_' |
|
CSCvg50981 |
Add BVI logical name for IRB traffic to flow |
Resolved Caveats in Version 1.0(2)
|
Caveat |
Description |
|---|---|
|
CSCvd88598 |
Default MTU not getting updated in ftd-device-pkg |
|
CSCvd88725 |
Logical name is not being cleared during inline graph dissassociation |
|
CSCve40048 |
Stacktrace when device package gets 429 response code |
|
CSCve40111 |
In command_interaction.py there is an error with function remove_value_from_dict |
|
CSCve75140 |
Misspelling and incorrect description in device model file |
|
CSCvg33615 |
Access rule not created if same name existed in another policy |
|
CSCvg57189 |
Add upper limit for the number of retries when FMC gives 429-error |
|
CSCvg58964 |
Interfaces associated with BVI shut down when IP address changed by FTD DP |
|
CSCvg73120 |
Associated interfaces deleted if BVI interface ID changed |
Open Caveats in Version 1.0(2)
|
Caveat |
Description |
|---|---|
|
CSCve00407 |
Java Exception failure from FMC when GET request sent, graph fails to deploy |
|
CSCvg06100 |
VLAN Trunking fails in Transparent mode on virtual FTD |
|
CSCvg84142 |
Deployment error due to "Object Not Found" error on FMC |
Bug Search
As a registered Cisco.com user, sign in to view more information about each bug or caveat using the Cisco Bug Search Tool.
Features Not Supported in Version 1.0(2)
The APIC cannot configure the following features using the FTD device package:
-
Dynamic routing
-
Static routing
-
Port-channels
-
Deploy configuration to FTD devices in clustering mode
-
Access control policy rule ports, IPs, or inspections
-
Network Address Translation (NAT)
 Note |
For any unsupported FTD feature, we recommended that you clean up the configuration manually before removing a service graph or deleting the tenant. |
Known Issues
This section describes known issues and their workarounds.
CSCvf88494
When deleting a tenant with a large configuration, the device package process is killed before it can finish the service call, resulting in a configuration that may not be completely cleaned up on the FMC. This may occur when:
-
Using the FTD device package, version 1.0.2
-
The tenant contains a device that has more than 50 service graphs deployed
-
Deleting the tenant directly before detaching the service graphs
Workaround
Detach the service graphs before deleting the tenant, or increase various timeout values on the APIC using its REST API. The REST payload is like this:
<polUni>
<infraInfra>
<vnsMDev vendor=CISCO model=FTD_FI version=1.0>
<vnsDevScript auditTimeout=10800 modifyTimeout=10800 watchdogTimeout=10800/>
</vnsMDev>
</infraInfra>
</polUni>
You can use the Cisco-provided Python script to access the APIC REST API and modify the timeout values:
-
Before deleting the tenant, run the script to change the timeout value to its maximum number:
set_timeout.py <APIC_IP> <USERNAME> <PASSWORD> maximum -
Delete the tenant from the APIC.
-
Monitor the debug.log from the APIC to verify that the service call has completed. Or check the FMC to verify that all relevant configuration data has been cleaned up (such as access rules, security zones, sub-interfaces, and inline sets).
-
Run the script again to change the timeout value back to its default number. Otherwise, unexpected behavior may occur.
set_timeout.py <APIC_IP> <USERNAME> <PASSWORD> default
 Note |
Note: If the “CISCO-FTD_FI-1.0” device package is not installed on the APIC, running the script results in a “Bad Request” error. This error message can be safely ignored, as the script is designed to affect this particular device package only. |
For more information, see CSCvg00515, opened to track this issue.
CSCvg06100
VLAN trunking fails in Transparent mode on a virtual FTD.
Workaround
Opened to track the FMC issue in CSCvf90086.
Enable the trunking port after creating the L4-L7 device. Then, apply the service graph.
If the deployment fails:
-
On the FMC:
-
Navigate to Devices, and select the FTD.
-
Delete the new BVI and the associated sub-interfaces. Click Save. Click Deploy.
-
Wait for the FMC to complete the deployment.
-
-
On the APIC:
-
In the node tree on the left, navigate to L4-L7 Devices, and select the device.
-
Verify that the Trunking Port check box is selected.
-
Right-click the device, and select Re-Query For Device Validation.
-
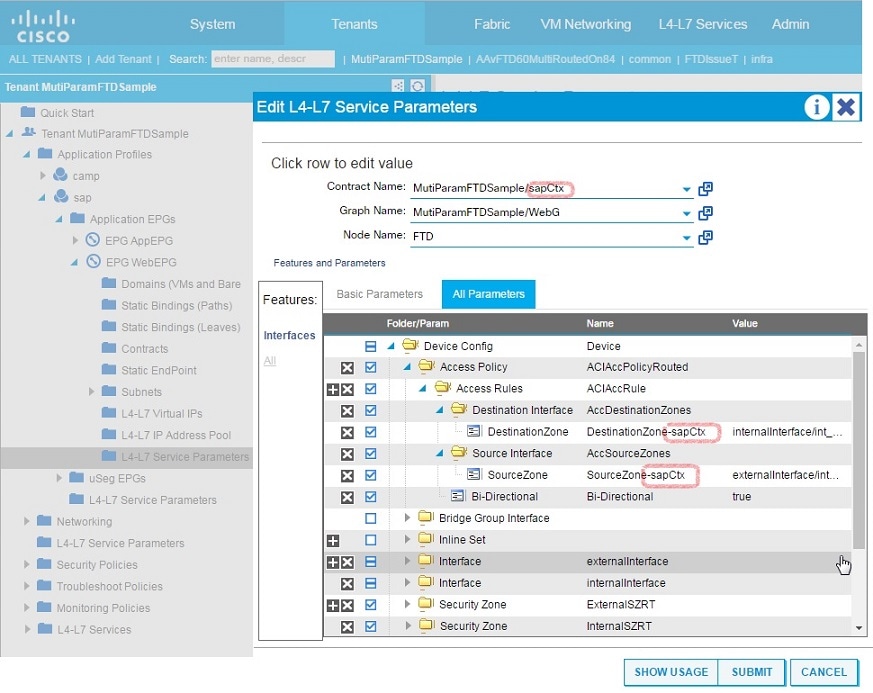
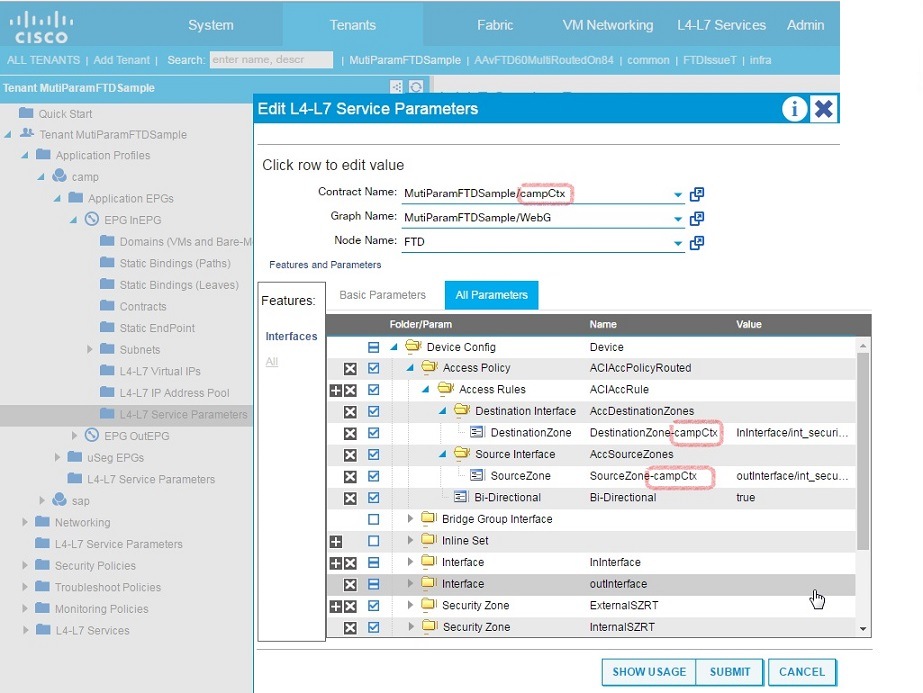
CSCvc46536
Multiple graph deployment needs a different parameter name for an access rule.
Workaround
For instance, Access Rules is a common APIC configuration parameter that can be shared across multiple graph deployments on the same L4-L7 device. In order to attach each graph deployment's interface security zones to a common access rule, provide different names for the SourceZone and DestinationZone parameters. For example, append each parameter with a matching suffix name, such as SourceZone-campCtx and DestinationZone-campCtx in one case and SourceZone-sapCtx and DestinationZone-sapCtx in another.
For more information, see the FMC Configuration Guide in Related Documentation.
 Feedback
Feedback