-
-
- Bisync-to-IP Conversion for Automated Teller Machines
- Configuring Serial Tunnel and Block Serial Tunnel
- Overview of IBM Networking
- Configuring Remote Source-Route Bridging
- Configuring Data-Link Switching Plus
- Configuring LLC2 and SDLC Parameters
- Configuring IBM Network Media Translation
- Configuring SNA Frame Relay Access Support
- Configuring NCIA Client/Server
- Configuring the Airline Product Set
- Configuring DSPU and SNA Service Point Support
- Configuring SNA Switching Services
-
Bridging and IBM Networking Configuration Guide, Cisco IOS Release 15S
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- September 9, 2007
Chapter: Configuring SNA Frame Relay Access Support
- Technology Overview
- SNA FRAS Configuration Task List
- Monitoring and Maintaining FRAS
- Configuring FRAS Host
- FRAS Host Configuration Task List
- FRAS and FRAS Host Configuration Examples
- LAN-Attached SNA Devices Example
- SDLC-Attached SNA Devices Example
- FRAS BNN Topology Example
- FRAS BNN Example
- FRAS BAN Example
- SRB over Frame Relay Example
- FRAS DLCI Backup over Serial Interface Example
- FRAS Dial Backup over DLSw+ Example
- Cisco FRAD or FRAS Router Configuration Examples
- FRAS Host CIP Connection to VTAM Configuration Example
- FRAS Host Ethernet Connection to AS/400 Configuration Example
Configuring SNA Frame Relay Access Support
This chapter describes Frame Relay Access Support (FRAS) for Systems Network Architecture (SNA) devices. It also explains how to configure FRAS and how to use a FRAS host to connect Cisco Frame Relay Access Devices (FRADs) to channel-attached mainframes, LAN-attached front-end processors (FEPs), and LAN-attached AS/400s through a Cisco router.
For a complete description of the FRAS commands in this chapter, refer to the "SNA Frame Relay Access Support Commands" chapter of the Cisco IOS Bridging and IBM Networking Command Reference (Volume 1 of 2). To locate documentation of specific commands, use the command reference master index or search online.
This chapter contains the following sections:
•![]() SNA FRAS Configuration Task List
SNA FRAS Configuration Task List
•![]() Monitoring and Maintaining FRAS
Monitoring and Maintaining FRAS
•![]() FRAS Host Configuration Task List
FRAS Host Configuration Task List
•![]() FRAS and FRAS Host Configuration Examples
FRAS and FRAS Host Configuration Examples
To identify the hardware platform or software image information associated with a feature, use the Feature Navigator on Cisco.com to search for information about the feature or refer to the software release notes for a specific release. For more information, see the "Identifying Platform Support for Cisco IOS Software Features" section on page li in the "Using Cisco IOS Software" chapter.
Technology Overview
FRAS, the Cisco IOS software allows branch SNA devices to connect directly to a central site FEP over a Frame Relay network. FRAS converts LAN or Synchronous Data-Link Control (SDLC) protocols to a Frame Relay format understood by the Network Control Program (NCP) that runs in an FEP. The
Cisco IOS software and the NCP support two frame formats:
•![]() RFC 1490 routed format for LLC2, specified in the FRF.3 Agreement from the Frame Relay Forum and known in NCP literature as Frame Relay Boundary Network Node (BNN) support. Support for this feature requires NCP 7.1 or higher.
RFC 1490 routed format for LLC2, specified in the FRF.3 Agreement from the Frame Relay Forum and known in NCP literature as Frame Relay Boundary Network Node (BNN) support. Support for this feature requires NCP 7.1 or higher.
•![]() RFC 1490 802.5 source-route bridged format, known in NCP literature as Frame Relay Boundary Access Node (BAN) support. Support for this feature requires NCP 7.3 or higher.
RFC 1490 802.5 source-route bridged format, known in NCP literature as Frame Relay Boundary Access Node (BAN) support. Support for this feature requires NCP 7.3 or higher.
Management service point support in FRAS allows the SNA network management application, NetView, to manage Cisco routers over the Frame Relay network as if it were an SNA downstream PU.
FRAS provides dial backup over RSRB in case the Frame Relay network is down. While the backup Public Switched Telephone Network (PSTN) is being used, the Frame Relay connection is tried periodically. As soon as the Frame Relay network is up, it will be used.
RFC 1490 Routed Format for LLC2 (BNN)
RFC 1490 specifies a standard method of encapsulating multiprotocol traffic with data link (Level 2 of the OSI model) framing. The encapsulation for SNA data is specified in the FRF.3 Agreement.
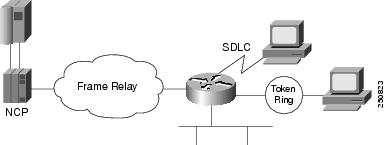
The Frame Relay encapsulation method is based on the RFC 1490 frame format for "user-defined" protocols using Q.933 NLPID, as illustrated in Figure 1.
Figure 1 Frame Relay Encapsulation Based on RFC 1490


Note ![]() The protocol ID for SNA subarea FID4 is 0x81. The protocol ID for SNA subarea FID2 is 0x82. The protocol ID for APPN FID2 is 0x83.
The protocol ID for SNA subarea FID4 is 0x81. The protocol ID for SNA subarea FID2 is 0x82. The protocol ID for APPN FID2 is 0x83.
FRAS allows the router acting as a FRAD to take advantage of the SNA BNN support for Frame Relay provided by ACF/NCP 7.1 and OS/400 V2R3. Downstream PU 2.0 and PU 2.1 devices can be attached to the router through SDLC, Token Ring, or Ethernet links. The router acting as a FRAD is connected to the Network Control Program (NCP) or AS/400 through a public or private Frame Relay network, as illustrated in Figure 2.
Figure 2 SNA BNN Support for Frame Relay
The frame format that communicates across the Frame Relay BNN link is defined in RFC 1490 for routed SNA traffic. From the perspective of the SNA host (for example an NCP or AS/400), the Frame Relay connection is defined as a switched resource similar to a Token Ring BNN link. Because the frame format does not include link addresses to allow the NCP to distinguish among SNA devices on the same permanent virtual circuit, Cisco supports SAP multiplexing, which allows you to configure unique LLC2 SAPs for each downstream SNA device so that they can share a single permanent virtual circuit to an FEP.
The Cisco IOS software is responsible for terminating the local data-link control frames (such as SDLC and Token Ring frames) and for modifying the data-link control frames to 802.2 compliant LLC frames. The LLC provides a reliable connection-oriented link layer transport required by SNA. (For example, 802.2 LLC is used to provide link-layer acknowledgment, sequencing, and flow control.)
The Cisco IOS software encapsulates these 802.2 LLC frames according to the RFC 1490 format for SNA traffic. The frames are then forwarded to the SNA host on a Frame Relay permanent virtual circuit (PVC). In the reverse direction, the software is responsible for de-encapsulating the data from the Frame Relay PVC, and for generating and sending the appropriate local data-link control frames to the downstream devices.
RFC 1490 Bridged Format for LLC2 (BAN)
BAN provides functionality similar to BNN except that it uses a bridged frame format, as illustrated in Figure 3.
Figure 3 RFC 1490 Bridged Frame Format
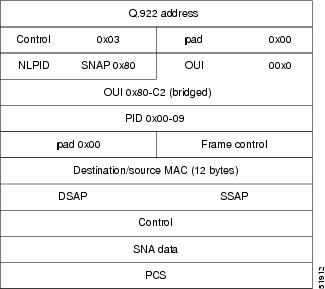
Because it includes the MAC header information in every frame, BAN supports multiple SNA devices sharing a single permanent virtual circuit without requiring SAP multiplexing. BAN also supports load balancing across duplicate data-link connection identifiers to the same or different FEPs at the data center to enhance overall availability. BAN works for devices attached by either Token Ring or Ethernet.
SNA FRAS Configuration Task List
To configure FRAS, perform the tasks described in the following sections:
•![]() Configuring FRAS BNN Statically
Configuring FRAS BNN Statically
•![]() Configuring FRAS BNN Dynamically
Configuring FRAS BNN Dynamically
•![]() Configuring SRB over Frame Relay
Configuring SRB over Frame Relay
•![]() Configuring FRAS Congestion Management
Configuring FRAS Congestion Management
•![]() Configuring Frame Relay RSRB Dial Backup
Configuring Frame Relay RSRB Dial Backup
•![]() Configuring Frame Relay DLSw+ Dial Backup
Configuring Frame Relay DLSw+ Dial Backup
To configure the FRAS host, see the "Configuring FRAS Host" section. For configuration examples, see the "FRAS and FRAS Host Configuration Examples" section.
Configuring FRAS BNN Statically
To configure FRAS BNN statically, use one of the following commands in interface configuration mode, as needed:
In this implementation, you configure and define each end station MAC and SAP address pair statically.
Because Frame Relay itself does not provide a reliable transport as required by SNA, the RFC 1490 support of SNA uses LLC2 as part of the encapsulation to provide link-level sequencing, acknowledgment, and flow control. The serial interface configured for Internet Engineering Task Force (IETF) encapsulation (RFC 1490) accepts all LLC2 interface configuration commands.
Configuring FRAS BNN Dynamically
To configure FRAS BNN dynamically, use one of the following commands in interface configuration mode, as needed:
When you associate an LLC connection with a Frame Relay DLCI, the router "learns" the MAC/SAP information as it forwards packets to the host. The FRAS BNN feature provides seamless processing at the router regardless of end station changes. End stations can be added or deleted without reconfiguring the router.
When you associate an SDLC link with a Frame Relay DLCI, you configure and define each end station MAC and SAP address pair statically.
Because Frame Relay itself does not provide a reliable transport as required by SNA, the RFC 1490 support of SNA uses LLC2 as part of the encapsulation to provide link-level sequencing, acknowledgment, and flow control. The serial interface configured for IETF encapsulation (RFC 1490) can take all LLC2 interface configuration commands.
Configuring FRAS BAN Support
To configure Frame Relay BAN, use the following command in interface configuration mode:
|
|
|
|---|---|
Router(config-if)# fras ban local-ring bridge-number ring-group ban-dlci-mac dlci dlci#1 [dlci#2 ... dlci#5] [bni mac-addr] |
Associates a bridge to the Frame Relay BAN. |
BAN simplifies router configuration when multiple LLC sessions are multiplexed over the same DLCI. By comparison, SAP multiplexing requires static definitions and maintenance overhead. By using BAN, the Token Ring MAC address is included in every frame to uniquely identify the LLC session. Downstream devices can be dynamically added and deleted with no configuration changes required on the router.
Configuring SRB over Frame Relay
To configure SRB over Frame Relay, use the following commands in interface configuration mode:
Cisco IOS software offers the ability to encapsulate source-route bridging traffic using RFC 1490 Bridged 802.5 encapsulation. This provides SRB over Frame Relay functionality. This SRB over Frame Relay feature is interoperable with other vendors' implementations of SRB over Frame Relay and with some vendors' implementations of FRAS BAN.
SRB over Frame Relay does not support the following Cisco IOS software functions:
•![]() Proxy explorer
Proxy explorer
•![]() Automatic spanning tree
Automatic spanning tree
•![]() LAN Network Manager
LAN Network Manager
Configuring FRAS Congestion Management
FRAS provides a congestion control mechanism based on the interaction between congestion notification bits in the Frame Relay packet and the dynamic adjustment of the LLC2 send window. This window shows the number of frames the Cisco IOS software can send before waiting for an acknowledgment. The window size decreases with the occurrence of backward explicit congestion notification (BECN) and increases when no BECN frames are received.
To configure congestion management, use the following commands in interface configuration mode:
You can enable the dynamic window mechanism only if you are using Frame Relay IETF encapsulation.
Configuring FRAS DLCI Backup
To configure FRAS DLCI backup, use the following command in interface configuration mode:
|
|
|
|---|---|
Router(config-if)# fras ddr-backup interface interface dlci-number |
Specifies an interface to be used for the backup connection and indicate the DLCI number of the session. |
FRAS DLCI backup is an enhancement to Cisco's FRAS implementation that lets you configure a secondary path to the host to be used when the Frame Relay network becomes unavailable. When the primary Frame Relay link to the Frame Relay WAN fails, the FRAS DLCI backup feature causes the router to reroute all sessions from the main Frame Relay interface to the secondary interface. The secondary interface can be either serial or ISDN and must have a data-link connection identifier (DLCI) configured.
Figure 4 illustrates Frame Relay backup over an ISDN connection.
Figure 4 FRAS DLCI Backup over ISDN
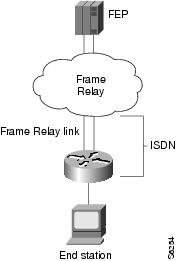

Note ![]() This feature provides backup for the local end of the Frame Relay connection, not the complete end-to-end connection.
This feature provides backup for the local end of the Frame Relay connection, not the complete end-to-end connection.
Configuring Frame Relay RSRB Dial Backup
When the Frame Relay network is down, the Cisco IOS software checks whether the dial backup feature is configured for the particular DLCI number. If it is configured, the software removes the FRAS to the downstream device connection and establishes the RSRB to this downstream device connection.
To configure RSRB dial backup, use the following command in interface configuration mode:
|
|
|
|---|---|
Router(config-if)# fras backup rsrb vmacaddr local-ring-number target-ring-number host-mac-address |
Activates Frame Relay RSRB dial backup. |
Configuring Frame Relay DLSw+ Dial Backup
The FRAS dial backup over DLSw+ feature provides a secondary path that is used when the Frame Relay network becomes unavailable. If preconfigured properly, when the primary link to the Frame Relay WAN fails, FRAS dial backup over DLSw+ feature moves existing sessions to the alternate link automatically. When the primary link is restored, existing sessions are kept on the backup connection so they can be moved non-disruptively to the primary link at the user's discretion.
To enable FRAS dial backup over DLSw+, use the following command in interface configuration mode:
Figure 5 shows a Frame Relay network with FRAS dial backup over DLSw+.
Figure 5 FRAS Dial Backup over DLSw+

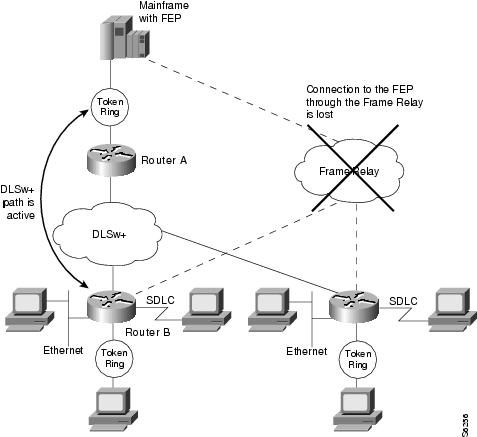
Figure 6 shows the active FRAS dial backup over DLSw+ when the Frame Relay connection to the NCP is lost.
Figure 6 FRAS Dial Backup over DLSw+ when Frame Relay is Unavailable
Monitoring and Maintaining FRAS
To display information about the state of FRAS, use the following command in privileged EXEC mode:
|
|
|
|---|---|
Router# show fras |
Displays the mapping and connection state of the FRAS. |
Configuring FRAS Host
The FRAS host provides a scalable and efficient solution for SNA FRAD access to channel-attached hosts and to LAN-attached hosts. The FRAS host function operates in two modes, which are documented in the following sections:
•![]() FRAS Host LLC2 Passthrough—In this mode, the LLC2 sessions are not locally terminated in the router's LLC2 stack. This is the recommended solution if your scenario includes a Channel Interface Processor (CIP) interface to the mainframe.
FRAS Host LLC2 Passthrough—In this mode, the LLC2 sessions are not locally terminated in the router's LLC2 stack. This is the recommended solution if your scenario includes a Channel Interface Processor (CIP) interface to the mainframe.
•![]() FRAS Host LLC2 Local Termination—In this mode, the LLC2 sessions are locally terminated in the router's LLC2 stack. This is the recommended solution if either of the following is true:
FRAS Host LLC2 Local Termination—In this mode, the LLC2 sessions are locally terminated in the router's LLC2 stack. This is the recommended solution if either of the following is true:
–![]() Your scenario includes a LAN-attached AS/400 or mainframe.
Your scenario includes a LAN-attached AS/400 or mainframe.
–![]() Your scenario includes conversion from RFC1490 encapsulation to DLSw+ encapsulation.
Your scenario includes conversion from RFC1490 encapsulation to DLSw+ encapsulation.
FRAS Host LLC2 Passthrough
The FRAS host LLC passthrough feature combines with a CIP-attached Cisco router's high-speed channel access to provide FEP-class performance at a fraction of what it would cost to achieve similar functionality using a FEP. If the CIP SNA feature is used to interface with the mainframe, then FRAS host LLC2 passthrough mode is the recommended solution. In this topology the LLC2 passthrough solution to the CIP-SNA LLC2 stack provides better performance, is more robust, and responds well to different types of congestion.
To prevent LLC2 session timeout, LLC2 characteristics (windows and timers) may be tuned on the CIP internal LAN adapter. The CIP/SNA LLC2 stack reacts to congestion by dynamically adjusting its LLC2 send window for that LLC2 session in response to dropped frames.
With the FRAS host LLC passthrough feature, you gain performance benefits of a channel attachment without FEP upgrades such as the addition of a Frame Relay interface, an upgrade to NCP (with its associated increase in monthly charges), and a possible increase in system memory.
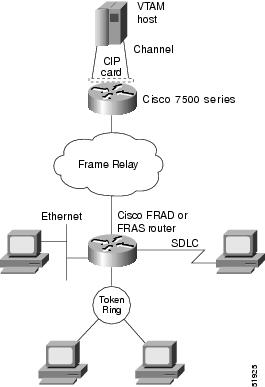
Figure 7 illustrates Cisco FRAD access to a mainframe through a channel-attached Cisco router.
Figure 7 Cisco FRAD Access to a Mainframe through a Cisco 7500
FRAS Host LLC2 Local Termination
If the FRAS host feature is used to allow remote FRADs to communicate with a LAN-attached IBM 3745 or AS/400, then LLC2 termination via DLSw+ local switching is the recommended solution. With this approach, the LLC2 sessions are terminated at the Route Processor. To prevent LLC2 session timeout, LLC2 characteristics (windows and timers) may be tuned on the virtual Token Ring interface. If the dynamic window algorithm is enabled on the virtual Token Ring interface, LLC2 local termination will react to congestion by dynamically adjusting its LLC2 send window in response to occurrence of Frame Relay BECN.
When you use the FRAS host LLC2 local termination feature on a Token Ring-attached FEP, the FRAS host Cisco router shields the FEP from having to manage the interface to the Frame Relay network. This avoids interface, memory, and NCP upgrades. The FRAS host Cisco router simply provides LLC2 sessions to the FEP over the LAN.
If used in an environment with AS/400s, FRAS host LLC2 local termination provides an even more valuable function. The Cisco FRAS host router offloads the management of the Frame Relay connections from the AS/400. This reduces AS/400 system hardware requirements and frees AS/400 CPU cycles for user applications.
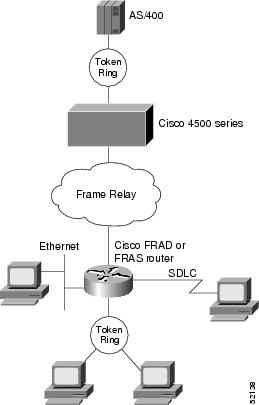
Figure 8 illustrates Cisco FRAD access to a LAN-attached SNA host through a Cisco router.
Figure 8 Cisco FRAD Access to a LAN-Attached AS/400 through a Cisco 4500
Congestion Management
Both passthrough and local acknowledgment environments support frame discard eligibility (DE) for additional congestion management. In both environments, you can further tune the interface to the Frame Relay network by taking advantage of the Cisco IOS Frame Relay features. Taken together, these features increase overall throughput dramatically by comparison to generic FRADs, which typically cannot use the network with the same degree of efficiency.
FRAS Host Configuration Task List
To configure the FRAS host migration feature, perform the tasks in the following sections:
•![]() Creating a Virtual Token Ring Interface
Creating a Virtual Token Ring Interface
•![]() Configuring Source-Route Bridging on the Virtual Token Ring Interface
Configuring Source-Route Bridging on the Virtual Token Ring Interface
•![]() Accepting Default LLC2 Passthrough or Enabling LLC2 Local Termination
Accepting Default LLC2 Passthrough or Enabling LLC2 Local Termination
•![]() Enabling the FRAS Host Feature for BAN or BNN
Enabling the FRAS Host Feature for BAN or BNN
•![]() Monitoring LLC2 Sessions Using FRAS Host
Monitoring LLC2 Sessions Using FRAS Host
See the "FRAS and FRAS Host Configuration Examples" section for examples.
Creating a Virtual Token Ring Interface
To configure a virtual Token Ring interface, use the following command in interface configuration mode:
|
|
|
|---|---|
Router(config-if)# interface virtual-tokenring number |
Configures a virtual Token Ring interface. |
Configuring Source-Route Bridging on the Virtual Token Ring Interface
To configure SRB on the Token Ring interface, use the following commands beginning in global configuration mode:

Note ![]() If you are using LLC2 passthrough with an Ethernet-attached host, you must configure the Cisco source-route translational bridging (SR/TLB) feature.
If you are using LLC2 passthrough with an Ethernet-attached host, you must configure the Cisco source-route translational bridging (SR/TLB) feature.
Accepting Default LLC2 Passthrough or Enabling LLC2 Local Termination
LLC2 passthrough is the default operational mode for all FRAS host connections that use a virtual Token Ring interface. You do not need to perform any configuration to accept the default LLC2 passthrough mode.
To enable LLC2 local termination for FRAS host connections using the virtual Token Ring, use the following commands beginning in global configuration mode:
Enabling the FRAS Host Feature for BAN or BNN
To enable the FRAS host for BAN or BNN, use the following commands in interface configuration mode:
Monitoring LLC2 Sessions Using FRAS Host
To display the status of LLC2 sessions using FRAS host, use the following command in privileged EXEC mode:
|
|
|
|---|---|
Router# show fras-host [interface] [dlci dlci-num] [detail] |
Displays the status of LLC2 sessions using FRAS host. |
FRAS and FRAS Host Configuration Examples
The following sections provide both FRAS and FRAS host configuration examples:
•![]() LAN-Attached SNA Devices Example
LAN-Attached SNA Devices Example
•![]() SDLC-Attached SNA Devices Example
SDLC-Attached SNA Devices Example
•![]() FRAS DLCI Backup over Serial Interface Example
FRAS DLCI Backup over Serial Interface Example
•![]() FRAS Dial Backup over DLSw+ Example
FRAS Dial Backup over DLSw+ Example
•![]() Cisco FRAD or FRAS Router Configuration Examples
Cisco FRAD or FRAS Router Configuration Examples
•![]() FRAS Host CIP Connection to VTAM Configuration Example
FRAS Host CIP Connection to VTAM Configuration Example
•![]() FRAS Host Ethernet Connection to AS/400 Configuration Example
FRAS Host Ethernet Connection to AS/400 Configuration Example
LAN-Attached SNA Devices Example
Figure 9 illustrates the configuration of SNA devices attached to a LAN.
Figure 9 LAN-Attached SNA Devices
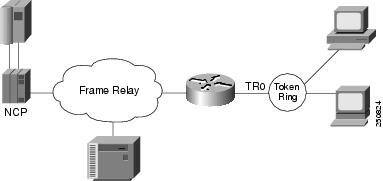
The configuration for the network shown in Figure 9 is as follows:
interface tokenring 0
no ip address
no keepalive
ring-speed 16
fras map llc 0800.5a8f.8802 4 4 serial 0 frame-relay 200 4 4
!
interface serial 0
mtu 2500
no ip address
encapsulation frame-relay IETF
keepalive 12
frame-relay lmi-type ansi
frame-relay map llc2 200
SDLC-Attached SNA Devices Example
Figure 10 illustrates the configuration of SDLC-attached SNA devices.
Figure 10 SDLC-Attached SNA Devices
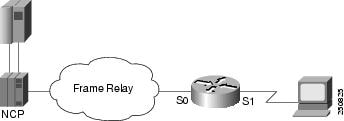
The configuration file for the network shown in Figure 10 is as follows:
interface serial 1
no ip address
encapsulation sdlc
no keepalive
clockrate 56000
sdlc address C1
sdlc xid C1 05D01501
sdlc role primary
fras map sdlc C1 serial 0 frame-relay 200 4 4
!
interface serial 0
mtu 2500
no ip address
encapsulation frame-relay ietf
keepalive 12
frame-relay lmi-type ansi
frame-relay map llc2 200
FRAS BNN Topology Example
FRAS BNN transports SNA traffic across different media through a Cisco router and then through a Frame Relay link to the host. SNA PU 2.0 and PU 2.1 devices may be attached to the remote router through Token Ring, SDLC, or Ethernet to access the Frame Relay network. The FRAS BNN topology is illustrated in Figure 11.
Figure 11 FRAS BNN Topology
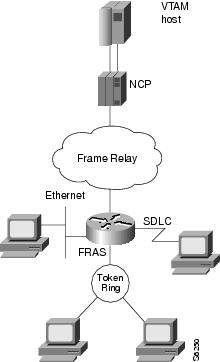
The original Frame Relay BNN feature transports traffic from multiple PUs over a single DLCI. This function is called SAP multiplexing. The router uses a unique SAP address (fr-lsap) for each downstream PU when communicating with the host. In this implementation, each end station's MAC/SAP address pair must be statically defined to the router. Consequently, the router must be reconfigured each time an end station is moved, added, or deleted. The configuration overhead for this implementation can be high.
The FRAS BNN feature, where the router "learns" the MAC/SAP information as it forwards packets to the host, offers several advantages over the original FRAS BNN implementation. The BNN enhancement alleviates the need to reconfigure the router when end stations are moved, added, or deleted. The configuration is simple: one map definition in the router is sufficient for multiple downstream devices. The router "learns" the addresses of the downstream devices in the normal course of communication (as shown in Figure 12).
Figure 12 illustrates the Frame Relay BNN configuration for both the original implementation and the enhanced implementation.
Figure 12 Frame Relay BNN Support
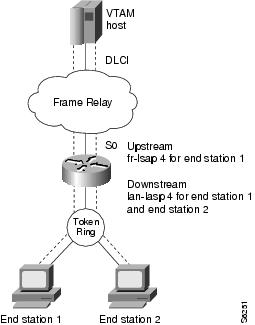
If the end station initiates the LLC session, the router acquires the Token Ring address and the SAP value of the end station from the incoming frame. Instead of mapping the end station's MAC/SAP address pair (as was done in the original FRAS BNN implementation), the destination MAC/SAP address pair of the incoming frame is mapped to the Frame Relay DLCI. If the destination SAP specified by the end station is equal to the lan-lsap address, the router associates the LLC (LAN) connection with the Frame Relay DLCI. The MAC address and the SAP address of the end station are no longer required in the router configuration. Thus, in the enhanced FRAS BNN implementation one configuration command achieves the same result for the end stations as did multiple configuration commands in the original FRAS BNN implementation.
FRAS BNN Example
The following configuration example enables the FRAS BNN feature. The topology is illustrated in Figure 13.
Figure 13 FRAS BNN Configuration
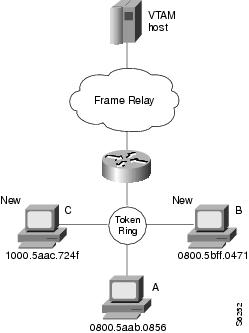
interface Serial0
no ip address
encapsulation frame-relay IETF
frame-relay lmi-type ansi
frame-relay map llc2 16
!
interface TokenRing0
no ip address
ring-speed 16
fras map llc 0800.5aab.0856 04 04 Serial 0 frame-relay 16 04 04
fras map llc 04 Serial 0 frame-relay dlci 16 04

Note ![]() In this configuration example, the second to last line describes the old configuration for workstation A. The last line describes the configuration for the new workstations B and C.
In this configuration example, the second to last line describes the old configuration for workstation A. The last line describes the configuration for the new workstations B and C.
FRAS BAN Example
The following configuration shows FRAS BAN support for Token Ring and serial interfaces. You must specify the source-bridge ring-group global command before you configure the fras ban interface command. When Token Ring is configured, the source-bridge interface command includes the local-ring, bridge-number, and the target-ring values. The source-bridge command enables local source-route bridging on a Token Ring interface.
source-bridge ring-group 200
!
interface serial 0
mtu 4000
encapsulation frame-relay ietf
frame-relay lmi-type ansi
frame-relay map llc2 16
frame-relay map llc2 17
fras ban 120 1 200 4000.1000.2000 dlci 16 17
!
interface tokenring 0
source-bridge 100 5 200
For SDLC connections, you must include SDLC configuration commands as follows:
!
interface Serial1
description SDLC line PU2.0
mtu 265
no ip address
encapsulation sdlc
no keepalive
clockrate 9600
sdlc role primary
sdlc vmac 4000.0000.0000
sdlc address C2
sdlc xid C2 05D01502
sdlc partner 4000.0000.2345 C2
sdlc address C8
sdlc xid C8 05D01508
sdlc partner 4000.0000.2345 C8
sdlc address C9
sdlc xid C9 05D01509
sdlc partner 4000.0000.2345 C9
fras ban frame-relay Serial0 4000.0000.2345 dlci 16
!
interface Serial2
description SDLC line PU2.1
no ip address
encapsulation sdlc
no keepalive
clockrate 19200
sdlc role prim-xid-poll
sdlc vmac 2000.0000.0000
sdlc address C6
sdlc partner 1000.2000.3000 C6
fras ban frame-relay serial0 1000.2000.3000 dlci 16
SRB over Frame Relay Example
Figure 14 illustrates the interoperability provided by SRB over Frame Relay. FRADs B and C forward frames from their locally attached Token Rings over the Frame Relay network using SRB.
Figure 14 FRAD Using SRB over Frame Relay to Connect to a Cisco Router
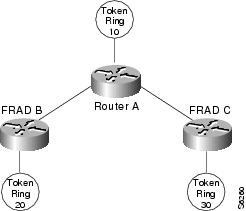
Figure 14 illustrates a network with the following characteristics:
•![]() Virtual ring number of Router A = 100
Virtual ring number of Router A = 100
•![]() Virtual ring number of FRAD B = 200
Virtual ring number of FRAD B = 200
•![]() Virtual ring number of FRAD C = 300
Virtual ring number of FRAD C = 300
•![]() DLCI number for the partner's virtual ring (PVC) between Router A and FRAD B = 30
DLCI number for the partner's virtual ring (PVC) between Router A and FRAD B = 30
•![]() DLCI number for PVC between Router A and FRAD C = 31
DLCI number for PVC between Router A and FRAD C = 31
In this example we configure a new option, conserve-ring, on the source-bridge interface configuration command. When this option is configured, the SRB software does not add the ring number associated with the Frame Relay PVC to outbound explorer frames. This option is permitted for Frame Relay subinterfaces only.
The router configures the partner FRAD's virtual ring number as the ring number for the PVC.
This approach does not require a separate ring number per DLCI. The router configures the partner FRAD's virtual ring number as the ring number for the PVC.
FRAD B configures its virtual ring as 200 and the ring for the PVC as 100. FRAD C configures its virtual ring as 300 and the ring for the PVC as 100.
FRAS DLCI Backup over Serial Interface Example
The following example shows a configuration for FRAS DLCI backup over a serial interface:
interface serial0
mtu 3000
no ip address
encapsulation frame-relay IETF
bandwidth 56
keepalive 11
frame-relay map llc2 277
frame-relay map llc2 278
frame-relay lmi-type ansi
fras ddr-backup interface serial1 188
!
interface serial1
mtu 3000
no ip address
encapsulation frame-relay IETF
no cdp enable
frame-relay map llc2 188
frame-relay lmi-type ansi
!
interface serial2
no ip address
encapsulation sdlc
no keepalive
clock rate 19200
sdlc role prim-xid-poll
sdlc address D6
fras map sdlc D6 s0 frame-relay 277 8 4
!
interface tokenring0
no ip address
ring-speed 16
fras map llc 0000.f63a.2f70 4 4 serial0 frame-relay 277 4 4
Router A
source-bridge ring-group 100
!
interface Serial1
encapsulation frame-relay
!
interface Serial1.1 point-to-point
frame-relay interface-dlci 30 ietf
source-bridge 200 1 100 conserve-ring
source-bridge spanning
!
interface Serial1.2 point-to-point
frame-relay interface-dlci 31 ietf
source-bridge 300 1 100 conserve-ring
source-bridge spanning
!
interface TokenRing0
source-bridge 500 1 100
FRAS Dial Backup over DLSw+ Example
The following examples show configurations for FRAS dial backup over DLSw+:
FRAS Dial Backup on a Subinterface
source-bridge ring-group 200
dlsw local-peer peer-id 10.8.8.8
dlsw remote-peer 0 tcp 10.8.8.7 dynamic
interface ethernet0
ip address 10.8.8.8 255.255.255.0
!
interface serial0
no ip address
encapsulation frame-relay IETF
frame-relay lmi-type ansi
!
interface Serial0.1 point-to-point
description fras backup dlsw+ listening on dlci 16 configuration example
no ip address
frame-relay interface-dlci 16
fras backup dlsw 4000.1000.2000 200 1000.5aed.1f53
!
interface TokenRing0
no ip address
ring-speed 16
fras map llc 0000.f63a.2f50 4 4 Serial0.1 frame-relay 16 4 4
FRAS Dial Backup on a Main Interface
source-bridge ring-group 200
dlsw local-peer peer-id 10.8.8.8
dlsw remote-peer 0 tcp 10.8.8.7 dynamic
interface ethernet0
ip address 10.8.8.8 255.255.255.0
!
interface serial0
no ip address
encapsulation frame-relay IETF
frame-relay lmi-type ansi
frame-relay map llc2 16
fras backup dlsw 4000.1000.2000 200 1000.5aed.1f53
!
interface Serial1
ip address 10.8.8.8
!
interface tokening0
no ip address
ring-speed 16
fras map llc 0000.f63a.2f50 4 4 Serial0 frame-relay 16 4 4
Cisco FRAD or FRAS Router Configuration Examples
This section provides the following configuration examples (see Figure 15):
•![]() Cisco FRAD or FRAS Router A with BNN Configuration Example
Cisco FRAD or FRAS Router A with BNN Configuration Example
•![]() Cisco FRAD or FRAS Router B with BAN Configuration Example
Cisco FRAD or FRAS Router B with BAN Configuration Example
•![]() Cisco FRAD or FRAS Router C with BAN Configuration Example
Cisco FRAD or FRAS Router C with BAN Configuration Example
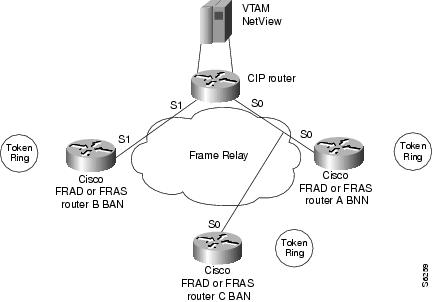
Figure 15 FRAS Host CIP Connection to VTAM
Cisco FRAD or FRAS Router A with BNN Configuration Example
interface Serial0
encapsulation frame-relay IETF
frame-relay map llc2 16
!
interface TokenRing0
fras map llc 4001.2222.0000 4 4 Serial0 frame-relay 16 4 4
Cisco FRAD or FRAS Router B with BAN Configuration Example
source-bridge ring-group 200
!
interface Serial0
encapsulation frame-relay IETF
frame-relay map llc2 37
fras ban 10 1 200 4000.3745.0000 dlci 37
!
interface TokenRing0
source-bridge 20 1 200
Cisco FRAD or FRAS Router C with BAN Configuration Example
source-bridge ring-group 400
!
interface Serial0
encapsulation frame-relay IETF
frame-relay map llc2 46
fras ban 50 1 400 4000.3745.0220 dlci 46 bni 4001.3745.1088
!
interface TokenRing0
source-bridge 60 1 400
FRAS Host CIP Connection to VTAM Configuration Example
The following example shows the configuration for the network shown in Figure 16.
source-bridge ring-group 100
!
interface Serial0/1
encapsulation frame-relay IETF
frame-relay map llc2 16
frame-relay map llc2 46
!
interface Serial0/2
encapsulation frame-relay IETF
!
interface Serial0/2.37 point-to-point
frame-relay interface-dlci 37
!
interface Channel4/0
no keepalive
!
interface Channel4/1
no keepalive
lan TokenRing 0
source-bridge 104 1 100
adapter 0 4001.3745.1008
!
interface Virtual-TokenRing0
source-bridge 47 1 100
source-bridge spanning
fras-host bnn Serial 0/1 fr-lsap 04 vmac 4005.3003.0000 hmac 4001.3745.1088
fras-host ban Serial 0/1 hmac 4001.3745.1088 bni 4001.3745.1088
fras-host ban Serial 0/2.37 hmac 4001.3745.1088
FRAS Host Ethernet Connection to AS/400 Configuration Example
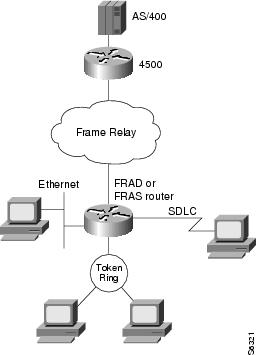
The configuration example in this section is shown in Figure 16.
Figure 16 FRAS Host Ethernet Connection to AS/400
source-bridge ring-group 226
dlsw local-peer
dlsw bridge-group 1
!
interface Ethernet0
bridge-group 1
!
interface Serial2
encapsulation frame-relay IETF
frame-relay map llc2 502
frame-relay lmi-type ansi
!
interface Virtual-TokenRing0
no ip address
ring-speed 16
source-bridge 1009 1 226
fras-host dlsw-local-ack
fras-host bnn Serial2 fr-lsap 04 vmac 4000.1226.0000 hmac 0800.5ae1.151d
 Feedback
Feedback