Cisco Crosswork Optimization Engine 1.2.1.x Release Notes
This document provides an overview of Cisco Crosswork Optimization Engine, new features, and any limitations for this release.
Overview of Cisco Crosswork Optimization Engine
Network operators are facing challenges to support the exponential growth of network traffic while addressing the pressure to efficiently run network operations. Providing quick service and network resolutions is vital for the business to remain viable. Network operators need a toolset to help automate bandwidth optimization and efficiently steer traffic with little operator intervention. Cisco Crosswork Optimization Engine fulfills this need by providing real-time network optimization capabilities that allow operators to effectively maximize network utility as well as increase service velocity.
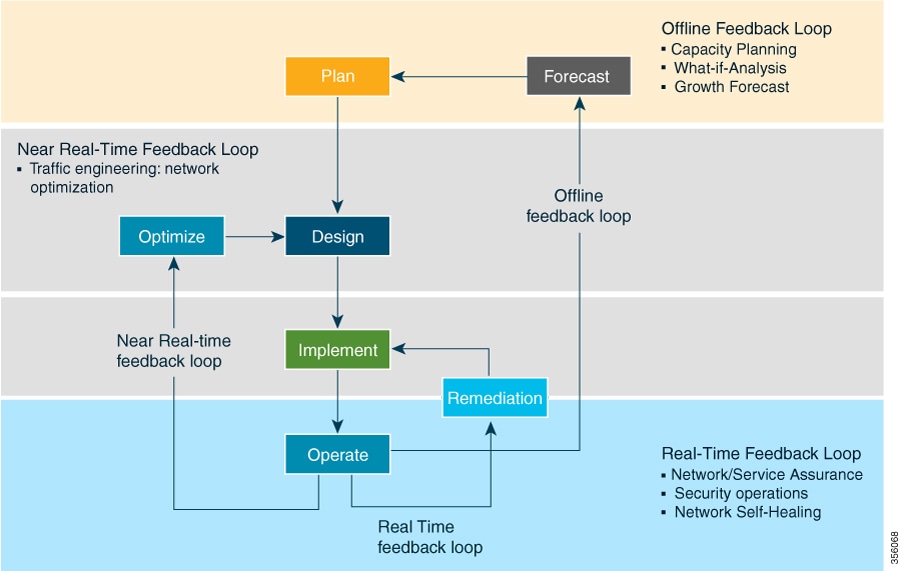
In a typical lifecycle, there is always a feedback loop that traditionally is done manually through human intervention. With network automation, the objective is to automate the feedback loop to enable quicker reaction to network events and faster determination on actions to perform on the network. Looking at the following figure, Crosswork Optimization Engine is built to fulfill the need for a closed-loop optimization loop as described under “Near Real-Time Feedback Loop”. Through Crosswork Optimization Engine, the operator would be able to define the optimization intent, implement the intent, and continuously monitor, track, and react to maintain the original intent.
Real-time Visibility
End-to-end visibility is important to any network operator to run their network effectively. Crosswork Optimization Engine not only provides this visibility, but also the ability to visualize the network across different layers (optical to IP) and the relationship between each layer. Crosswork Optimization Engine leverages IETF-standard BGP-LS protocol to discover IP network automatically, including the following features:
-
Real-time visibility: Provides the network operator with a true representation of the actual topology
-
Hierarchical topology view: Enables operators to define the different levels of granularity in the topology visualization
Simplified SR-TE Policy and RSVP-TE Tunnel Lifecycle Management
Crosswork Optimization Engine also provides an easy to use UI to manage the TE tunnel lifecycle. The UI enables the network operator to perform the following tasks:
-
Create, modify, and remove TE tunnels using an intuitive workflow
-
Continuously track TE tunnel dynamic path computations to maintain SLA objectives
-
Preview a TE tunnel before deploying it to the network
Extensibility through Function Packs
There are two function packs available for purchase: Bandwidth on Demand (BWoD) and Bandwidth Optimization (BWopt). For information on these function packs and instructions on how to use and enable them, see the Cisco Crosswork Optimization Engine Function Packs document.
Change History
The following table lists updates since the initial release of Crosswork Optimization Engine 1.2.1.
|
Date |
Change |
||
|---|---|---|---|
|
2021-03-25 |
For the Crosswork Optimization Engine 1.2.1 version released on July 2020, the following patches must be installed sequentially to resolve CSCvtx24465 (A new interface field (IF Alias) has been added to the Link Details window to indicate circuit IDs for operational needs):
You must follow the steps and activate each patch as described in Crosswork Patch Framework. Confirm that each patch status message states
|
Crosswork Patch Framework
There are three types of patches in Crosswork Optimization Engine:
-
Crosswork Application Patching (PATCH_IMAGE): This is a patch on the Crosswork applications such as Crosswork Optimization Engine, and the configuration packages within the application layer. One or more applications can be patched simultaneously.
-
Crosswork Data Gateway Patching (PATCH_CDG): This is a patch on the collector images for Cisco Crosswork Data Gateway VM.
-
Crosswork Data Patching (PATCH_DATA): This is a patch to dynamically update the pre-built set of fundamental data such as YANG models and system MIB packages used by the Crosswork applications.
The patch versioning is done in the [MAJOR: MINOR: PATCH] format, where MAJOR corresponds to every major release of the Crosswork Optimization Engine, MINOR corresponds to every critical (backward incompatible) change made during a release, and PATCH corresponds to every patch created in a release.
The unit of a patch is a TAR file. The TAR file consists of the patch metadata, list of docker images, checksum and signature. The metadata contains platform and product details, patch version, type of patch and other creation details. Signature is a security requirement in order to safeguard the patch; the signature is verified by the patch framework. It also helps to perform error correction mechanisms and detect if the patch is corrupted or not.
The platform orchestrator (such as Robot orchestrator) maintains and manages the lifecycle of all applications in the Crosswork platform. Each Crosswork product has its own centralized manifest file <orchmanifest.json> which contains the list of applications and the corresponding configurations. When the orchestrator is up, it goes through the manifest. Along with the manifest, the dependency diagram <orch.yaml> explains the logical grouping of applications and their dependencies. Currently, simultaneous application patching is possible as the applications are independent of each other. Patching the Collection Infra is a system-wide change and requires shutting down other dependent applications. A patch on the Core Infra is not allowed and is considered as a VM upgrade. Schema changes are not allowed during patching. Users are recommended to take backup of the system before patching, to restore in case of any error.
Patching Activation Workflow:
Each stage of the patching workflow, performed using APIs, are explained below:
-
Validate
-
API: /crosswork/platform/v1/patch/validate
-
User downloads the patch to any reachable host from the Crosswork VM. After the download, the patch is validated for accuracy and compatibility to the product version.
-
-
Add
-
API: /crosswork/platform/v1/patch/add
-
After the patch is validated, it is added to the corresponding registry in the system, such as updating the IMAGE registry in case of an IMAGE patch. The add operation prepares the system for the patch to be activated. It is an asynchronous operation and may take around 15 mins. Once add is initiated, user receives a corresponding job ID and the operation is performed in the background.
-
-
Status
-
There are 2 status APIs:
-
Status - which displays the current status of the Patch framework.
-
API: /crosswork/platform/v1/patch/status
-
This API displays the current status of the patch framework, such as if add is successful or ongoing, or if activate has been triggered.
-
-
Job Status - which displays the specific job status.
-
API: /crosswork/platform/v1/patch/jobstatus
-
This API return the status of a specific job based on the Job ID.
-
-
-
Activate
-
API: /crosswork/platform/v1/patch/activate
-
After successful addition, the patching is locked. If a patch is added, it needs to be activated before another patch can be added to the application. Activate, like add, is an asynchronous operation that generates a job ID for the user and continues the process in the background. Activation takes the backup of the current state and updates the configuration. If the patch fails, the auto-roll back functionality rolls back to the previous version and the status is updated with the failure details.
-
-
Summary
-
API: /crosswork/platform/v1/patch/summary
-
Summary provides the overall summary of the Patch framework, and summary of the different patch types including patch version. This information changes each time a new patch is added and activated:
-
PATCH_IMAGE - Patch version and the applications changed as part of the patch.
-
PATCH_CDG - Patch version
-
PATCH_DATA - Patch version and the applications to which the new data has been uploaded.
-
-
-
Remove
-
API: /crosswork/platform/v1/patch/remove
-
A patch can be removed in 2 ways:
-
Flow 1: A patch can be removed after it is validated and added. For example, if user chooses to cancels after the add is successful, remove can be used.
-
Flow 2: A patch can be removed after it is validated, added and activated. For example, if user chooses to go back to a previous version after a patch is applied successfully, remove can be used.
-
-
For more information, refer the Swagger file for Payload in https://developer.cisco.com/docs/crosswork/#!platform.
Upon successful activation of a patch, user can verify the health of the application using the Crosswork Manager or Data Gateway Management feature in Crosswork Optimization Engine, depending on the type of the patch. For more information, see the Perform Administrative Tasks chapter in the Cisco Crosswork Optimization Engine User Guide .
Documentation
The following documents are available:
What's New in Cisco Crosswork Optimization Engine 1.2.1
This section lists new features and changes delivered in Cisco Crosswork Optimization Engine 1.2.1. For compatibility information, see Compatibility Information. For Cisco Crosswork Optimization Engine 1.2.1 updates since its initial release, see Change History.
Installation
-
Upgrade support from Cisco Crosswork Optimization Engine 1.1 to 1.2.1.
-
Support for the following deployments: IPv4 Network, IPv6 Network, IPv4 Network on a Single Interface, and IPv6 Network on a Single interface.
Multiple Cisco SR-PCE HA Pairs
You can now configure up to three Cisco SR-PCE pairs (total of six SR-PCEs) to ensure high availability (HA).
Audit Logging
New audit logs map user information in Cisco Crosswork Optimization Engine with all the critical user actions performed in the system.
Function Packs
New Optimizer Event Threshold advanced option in Bandwidth on Demand (BWoD). If the Optimizer runs longer than the entered value, an alert is sent to the UI.
User Interface
-
Provider configuration has been moved under the Admin menu.
-
Tag configuration has been moved under the Admin menu.
Compatibility Information
The following table lists hardware and software versions that have been tested and are known to be compatible with Cisco Crosswork Optimization Engine. For complete installation requirements, see the Cisco Crosswork Optimization Engine Installation Guide for this release.
| Hardware/Software | Supported Version | ||
|---|---|---|---|
|
Hardware platform |
Cisco Unified Computing System (UCS) B or C series |
||
|
Hypervisor and vCenter |
|
||
|
Cisco Network Services Orchestrator(Cisco NSO) |
|
||
|
Software platform |
|
||
|
Cisco Crosswork Data Gateway |
Version 1.1.3 |
||
|
Browsers |
|
Cisco Bug Search Tool
You can use the Cisco Bug Search Tool to search for a specific bug or to search for all bugs in a release.
-
Go to the Cisco Bug Search Tool.
-
Enter your registered Cisco.com username and password, and click Log In.
The Bug Search page opens.

Note -
Use any of these options to search for bugs, and then press Enter (Return) to initiate the search:
— To search for a specific bug, enter the bug ID in the Search For field.
— To search for bugs based on specific criteria, enter search criteria, such as a problem description, a feature, or a product name, in the Search For field.
— To search for bugs based on products, enter or choose the product from the Product list. For example, enter Cisco Crosswork Optimization Engine.
— To search for bugs based on releases, in the Releases list choose whether to search for bugs affecting a specific release, bugs that were fixed in a specific release, or both. Then enter one or more release numbers in the Releases field.
-
When the search results are displayed, use the filter tools to narrow the results. You can filter the bugs by status, severity, and so on.
 Tip |
To export the results to a spreadsheet, click Export Results to Excel. |
Accessibility Features
For a list of accessibility features in Cisco Crosswork Optimization Engine, visit https://www.cisco.com/c/en/us/about/accessibility/voluntary-product-accessibility-templates.html (VPAT) website, or contact accessibility@cisco.com.
All product documents except for some images, graphics, and charts are accessible. If you would like to receive the product documentation in audio format, braille, or large print, contact accessibility@cisco.com.
 Feedback
Feedback