Introduction
This document describes FTD 7.7 Use Recovery-config Mode for Emergency on-device Configuration.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco Firepower Threat Defense (FTD)
- Cisco Firepower Management Center (FMC)
Components Used
The information in this document is based on these software and hardware versions:
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background
This feature has been introduced in version 7.7.0 and can be used to make out-of-band configuration changes when the management connection is down.
These configuration changes are performed directly at the device CLI to:
Once management connection is restored:
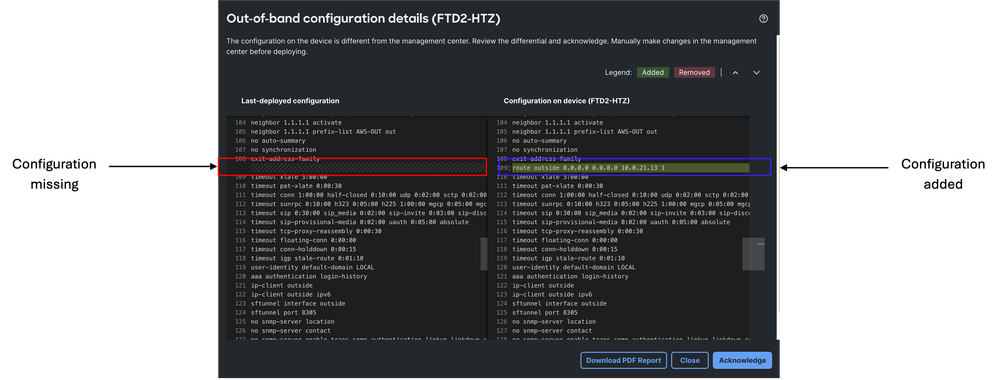
- You need to acknowledge the configuration differences shown in the out of band configuration alert.
- Perform the same changes in the FMC before deploying, because local changes are always overwritten by the FMC deployment.
You can configure these feature areas at the diagnostic CLI in recovery-config mode:
Configuration Example
Lab background
In this scenario, an FTD device registered to an FMC (using data-interface as management interface) has lost management connection and, to fix this issue, a static route is added to the FTD using the recovery-config feature.
FMC has two threat defense devices registered (10.0.21.72 and 10.0.21.73), but only one of those is reachable as shown in the next images (cli and GUI).
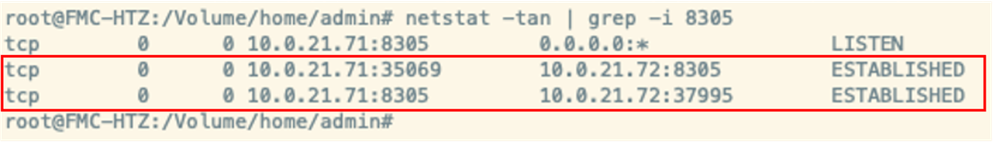
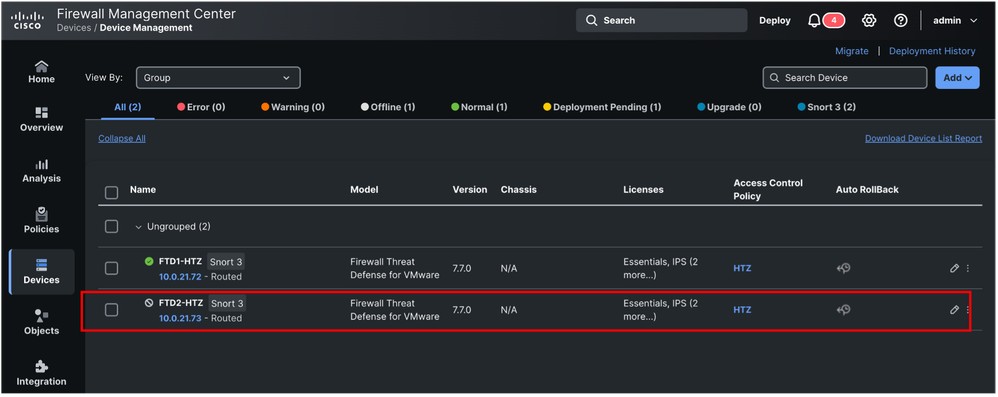
FTD is using data interface for the registration process to FMC.
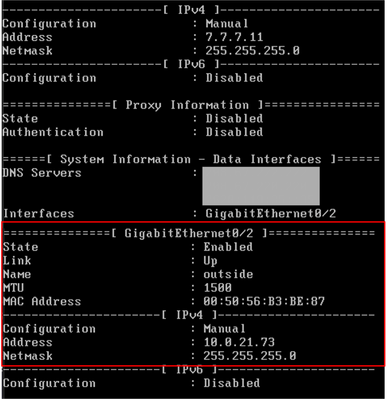
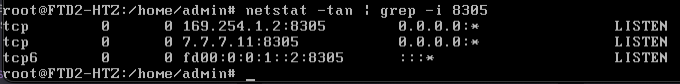
FTD also has not connection to FMC through sftunnel .
Configuration Steps
1. To be able to use recovery-config feature, you need to log in to FTD CLI and go to lina mode (system support diagnostic-cli).
2. Run the configure recovery-config command.
3. If you type question mark (?), all the supported commands are listed, as shown in the next list.
firepower(recovery-config)# ?
access-list Configure an access control element
as-path BGP autonomous system path filter
bfd BFD configuration commands
bfd-template BFD template configuration
cluster Cluster configuration
community-list Add a community list entry
crypto Configure IPSec, ISAKMP, Certification authority, key
end Exit from configure mode
exit Exit from config mode
extcommunity-list Add a extended community list entry
group-policy Configure or remove a group policy
interface Select an interface to configure
ip Configure IP address pools
ipsec Configure transform-set, IPSec SA lifetime and PMTU
Aging reset timer
ipv6 Configure IPv6 address pools
ipv6 Global IPv6 configuration commands
isakmp Configure ISAKMP options
jumbo-frame Configure jumbo-frame support
management-interface Management interface
mtu Specify MTU(Maximum Transmission Unit) for an interface
no Negate a command or set its defaults
policy-list Define IP Policy list
prefix-list Build a prefix list
route Configure a static route for an interface
route-map Create route-map or enter route-map configuration mode
router Enable a routing process
sla IP Service Level Agreement
sysopt Set system functional options
tunnel-group Create and manage the database of connection specific
records for IPSec connections
vpdn Configure VPDN feature
vrf Configure a VRF
zone Create or show a Zone

Warning: You are expected to know the commands that are required for recovery or emergency use. If you are unsure about the which command must be used, it is recommended that you contact Cisco TAC for guidance.
4. After you run the configure recovery-config command, an alert is displayed and you are asked to confirm and proceed.
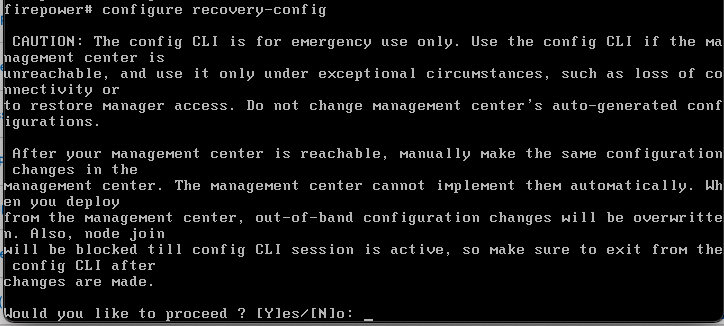
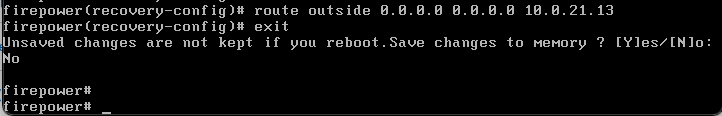
5. Once confirmed, you can start using the available config commands. In this scenario, a static route is added to the outside interface. After config is completed, run the exit command to exit from the recovery mode.
You are asked now to save changes and an alert is shown informing that changes are not kept if the device is rebooted.
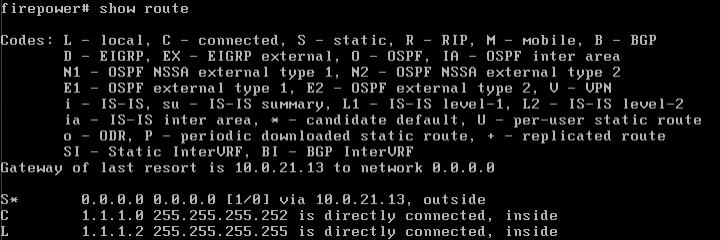
6. You can confirm the configuration has been applied. In this case, showing routes.
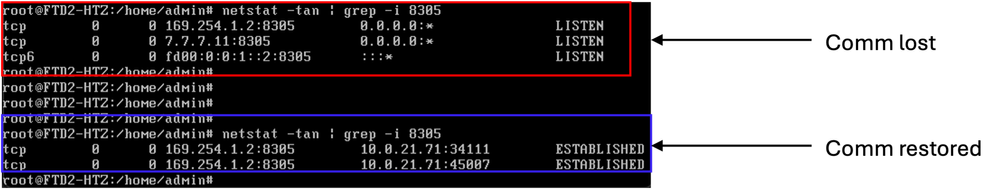
7. After several minutes, this change restores the communication with FMC. The next images show connection established, first in FTD and next in FMC CLI.
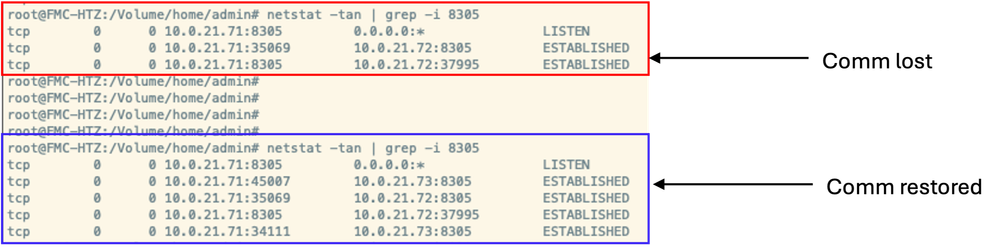
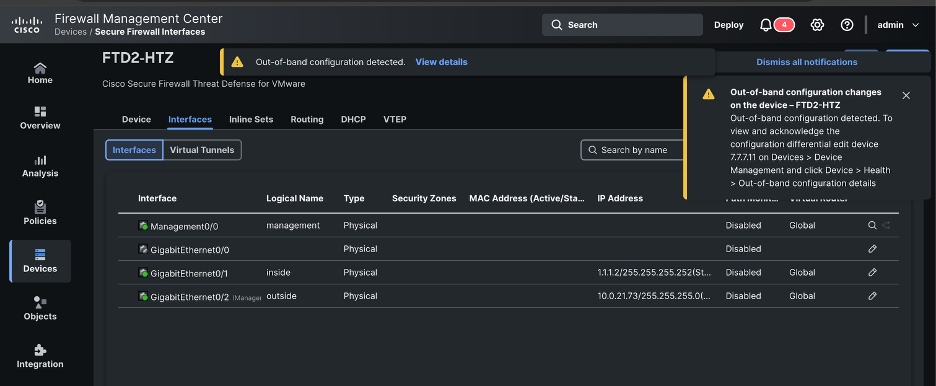
8. After configuration is restored, in FMC GUI you can naviate to Device > Device Management and click on your device (in this case it is FTD2-HTZ).
There you can see the Out-of-band configuration detected alert. Click in View details to see configuration differences.
9. Review Out-of-band configuration details and acknowledge differences.
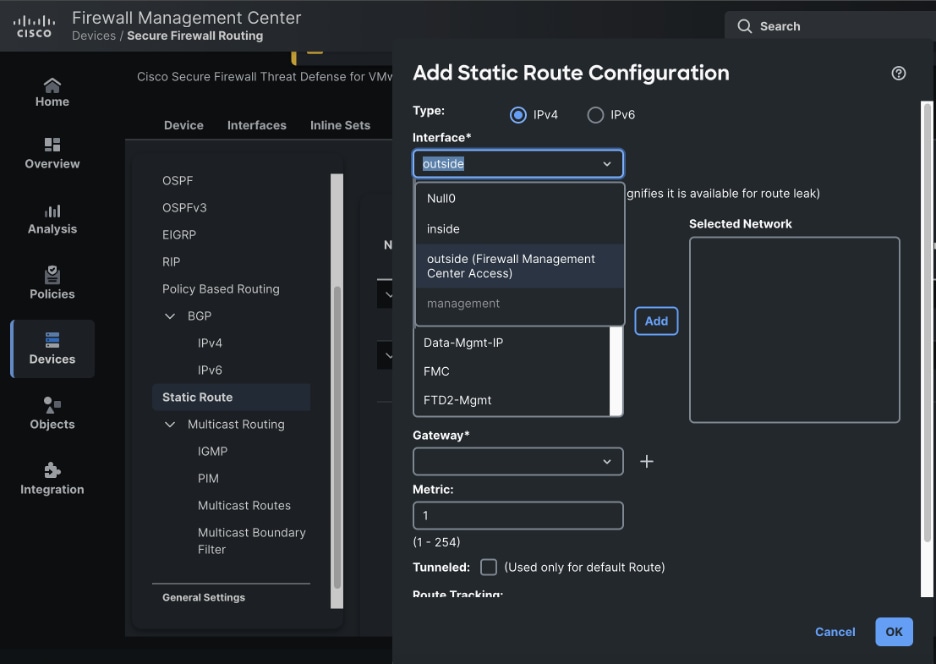
10. After configuration differences are acknowledge, proceed to configure the same changes done in the recovery mode, but now through FMC GUI. In this scenario, a static route is added.
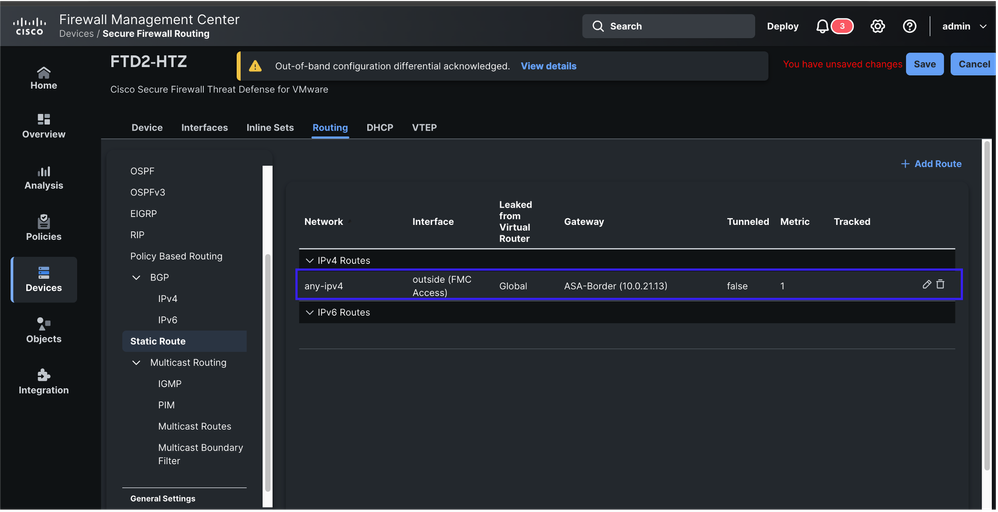
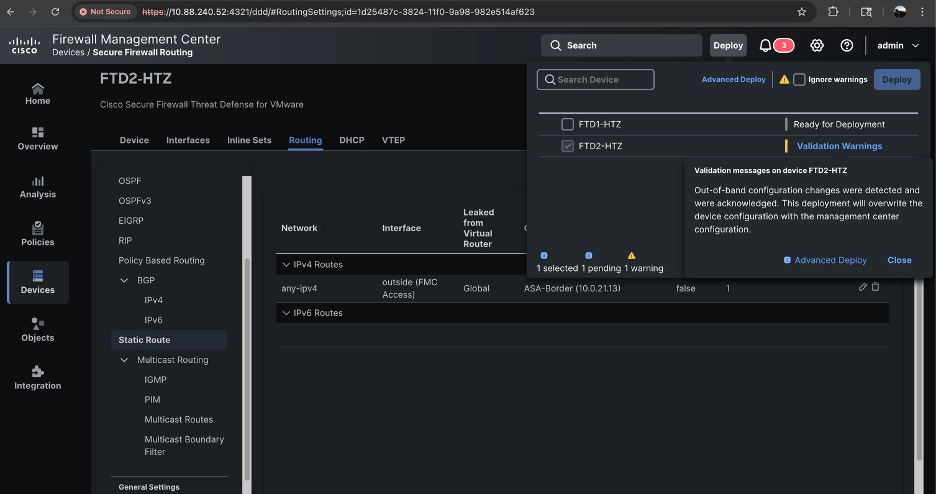
11. Once configuration changes are saved, proceed to deploy the changes. Another alert is shown informing Out-of-band configuration changes were detected and acknowledged, and that the changes are overridden by the current deployment.
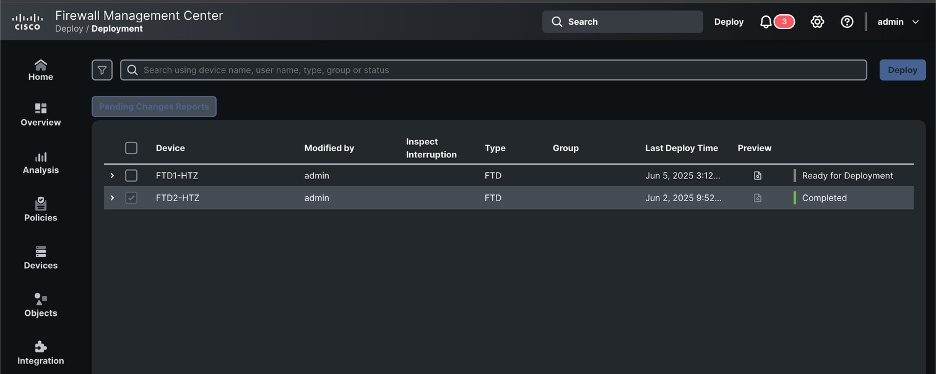
Once the deployment succeeds, the configuration is in sync again.
References

















 Feedback
Feedback