Introduction
This document describes how to use the MITRE framework to view and act on potential threats in a secure Firepower Management Center (FMC).
Background Information
The MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) Framework is an extensive knowledge base and methodology that provides insights into the tactics, techniques, and procedures (TTPs) distributed by threat actors aiming to harm systems. ATT&CK is compiled into matrices that each represent operating systems or a particular platform. Each stage of an attack, known as "tactics", is mapped to the specific methods used to achieve those stages, known as "techniques".
Each technique in the ATT&CK framework is accompanied by information about the technique, associated procedures, probable defences and detections, and real-world examples. The MITRE ATT&CK framework also incorporates Groups to refer to threat groups, activity groups, or threat actors based on the set of tactics and techniques they employ. By using Groups, the framework helps categorize and document behaviors.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Knowledge of Snort
- Secure FMC
- Secure Firepower Threat Defense (FTD)
Components Used
The information in this document is based on these software and hardware versions:
- This document applies to all Firepower platforms
- Secure FTD running software version 7.3.0
- Secure Firepower Management Center Virtual (FMC) running software version 7.3.0
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Benefits of MITRE Framework
- MITRE Tactics, Techniques, and Procedures (TTPs) are added to intrusion events that enable administrators to act on traffic based on the MITRE ATT&CK (Adversary Tactics Techniques and Common Knowledge) framework. This enables administrators to view and handle traffic with more granularity, and they can group rules by vulnerability type, target system, or threat category.
- You can organize intrusion rules according to the MITRE ATT&CK framework. This allows you to customize policies according to specific attacker tactics and techniques.
View the MITRE Framework in your Intrusion Policy
The MITRE framework enables you to navigate through your intrusion rules. MITRE is just another category of rule groups and is part of the Talos rule groups. Rule navigation for several levels of rule groups is supported which provides more flexibility and logical grouping of rules.
1. Choose Policies > Intrusion.
2. Ensure that the Intrusion Policiestab is chosen.
3. Click Snort 3 Versionnext to the intrusion policy you want to view or edit. Close the Snort helper guide that pops up.
4. Click the Group Overrideslayer.
The Group Overrideslayer lists all the categories of rule groups in a hierarchical structure. You can traverse to the last leaf rule group in each rule group.
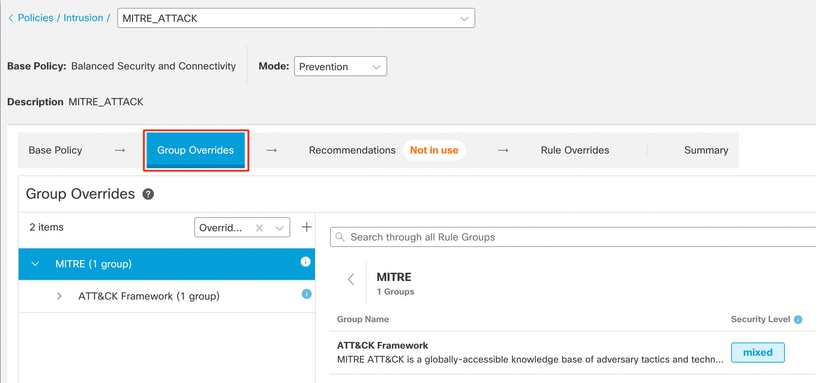
6. Under Group Overrides, ensure that Allis chosen in the drop-down list, so that all the rule groups for the intrusion policy are visible in the left pane.
7. Click MITREin the left pane.

Note: For this example, MITRE is selected, but depending on your specific requirements, you can choose the Rule Categories rule group or any other rule group and subsequent rule groups under it. All the rule groups use the MITRE framework.
8. Under MITRE, click ATT&CK Framework to expand it.
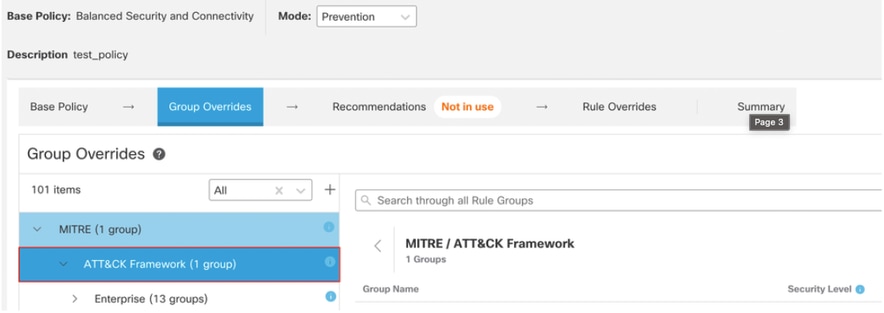
9. Under ATT&CK Framework, click Enterprise to expand it.
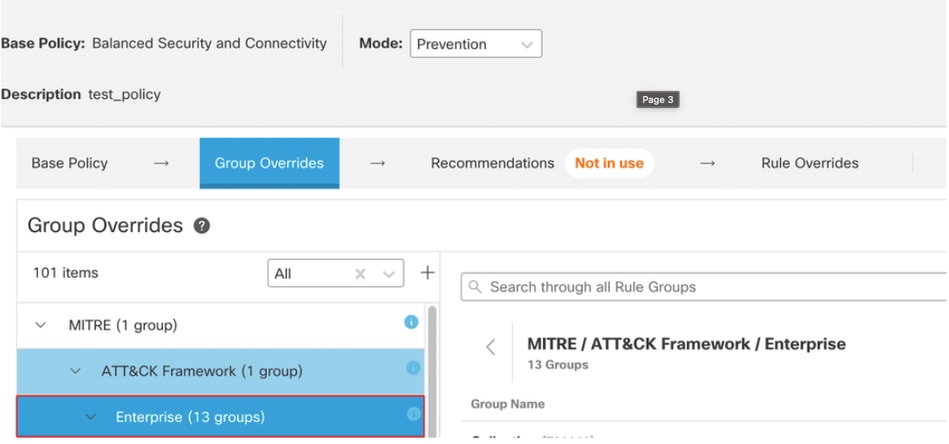
10. Click Edit ( ) next to the Security Level of the rule group to make bulk changes to the security level for all the associated rule groups under the Enterpriserule group category.
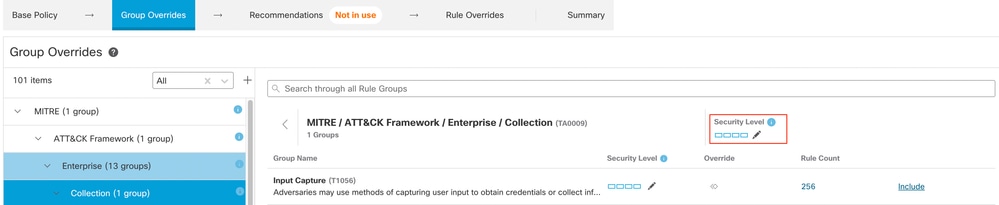 Edit security rule group
Edit security rule group
11. As an example, choose security level 3 in the Edit Security Level window and click Save.
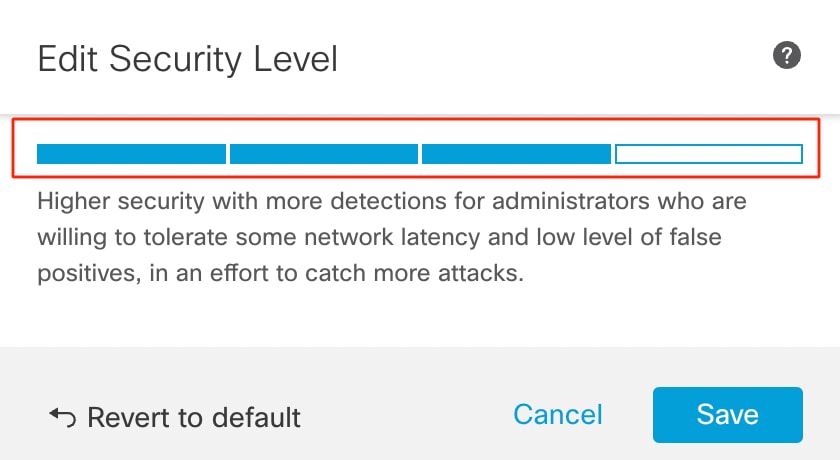 Security level
Security level
12. Under Enterprise, click Initial Accessto expand it.
13. Under Initial Access, click Exploit Public-Facing Application, which is the last leaf group.
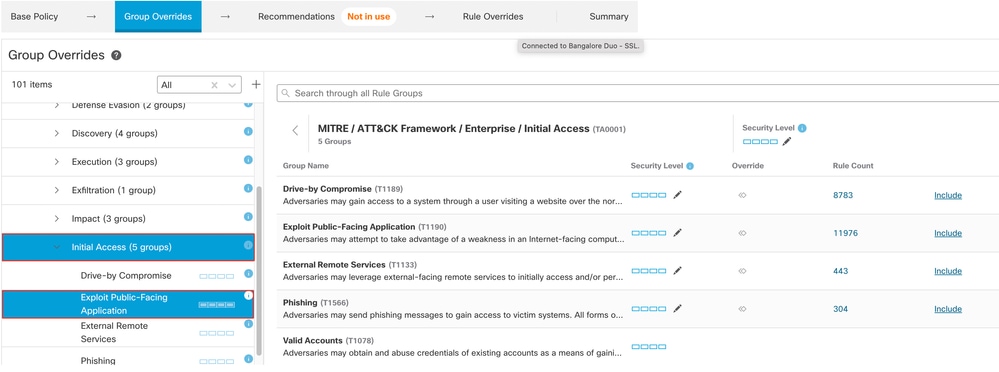 Initial access group
Initial access group
14. Click the View Rules in Rule Overridesbutton to view the different rules, rule details, rule actions, and so on for the different rules.
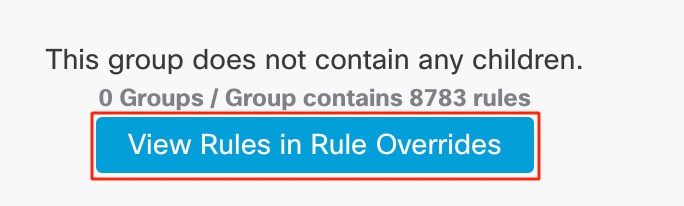 Rules in Rule Overrides
Rules in Rule Overrides
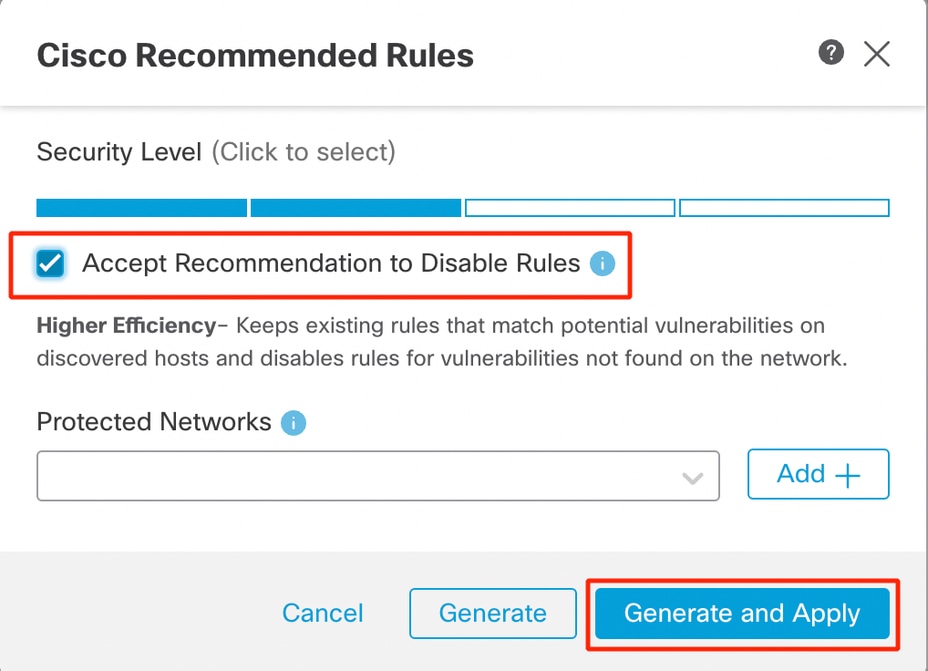
15. Click the Recommendationslayer and then click Start to start using Cisco-recommended rules. You can use the intrusion rule recommendations to target vulnerabilities associated with host assets detected in the network. For more information.
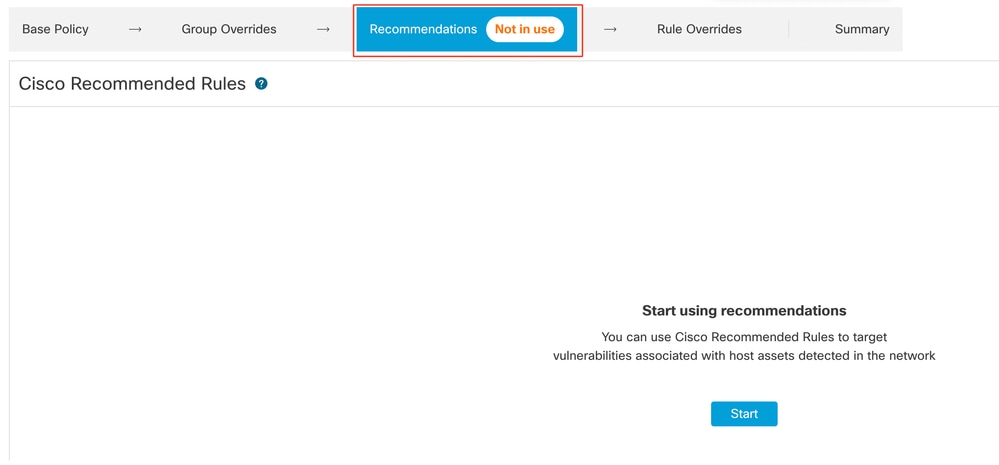 Recommendations
Recommendations
16. Click the Summarylayer for a holistic view of the current changes to the policy. You can view the rule distribution of the policy, group overrides, rule overrides, and so on.
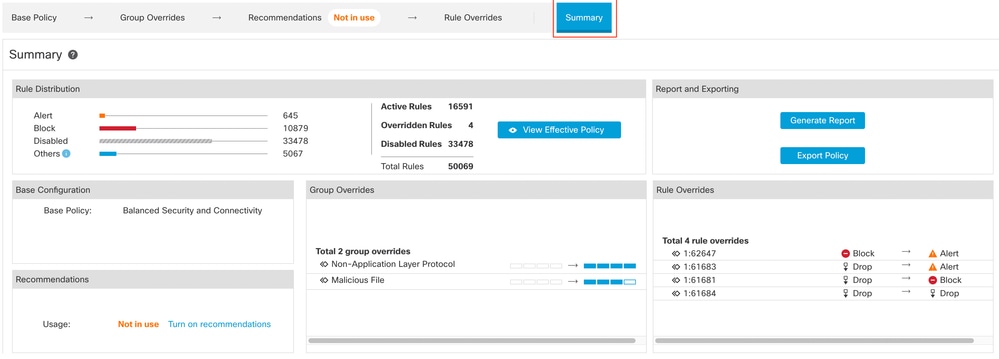 Policy summary
Policy summary
View Intrusion Events
You can view the MITRE ATT&CK techniques and rule groups in the intrusion events in the Classic Event Viewer and Unified Event Viewer. Talos provides mappings from Snort rules (GID:SID) to MITRE ATT&CK techniques and rule groups. These mappings are installed as part of the Lightweight Security Package (LSP).
Before you begin, Intrusion and access control policies must be deployed to detect and log events triggered by Snort rules.
1. Click Analysis > Intrusions > Events.
2. Click the Table View of Eventstab as shown in the image.
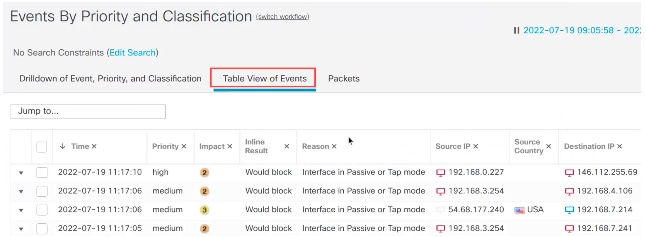 Events
Events
3. In the MITRE ATT&CKcolumn header, you can see the techniques for an intrusion event.
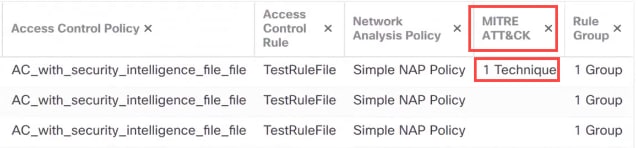 Mitre column header
Mitre column header
4. Click 1 Techniqueto view the MITRE ATT&CK Techniques, as shown in this figure. In this example, Exploit Public-Facing Applicationis the technique.
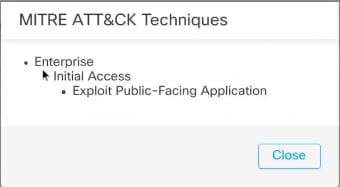 MITRE ATT&CK Techniques
MITRE ATT&CK Techniques
5. Click Close.
6. Click Analysis > Unified Events.
7. You can click the column selector icon to enable the MITRE ATT&CKand Rule Groupcolumns.
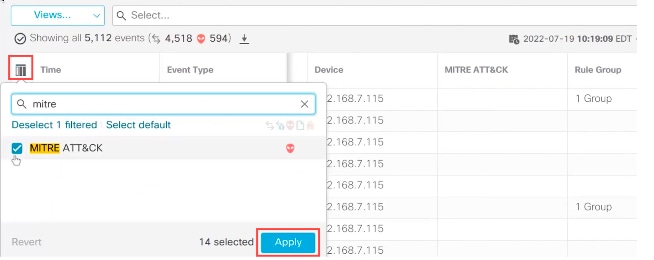 Enable the Mitre Attack
Enable the Mitre Attack
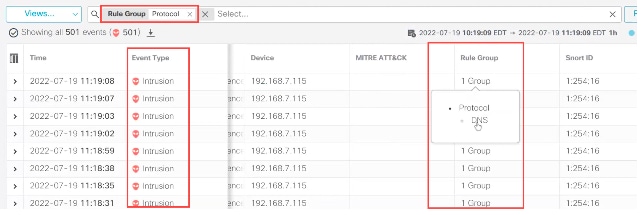
8. As shown in the example here, the intrusion event was triggered by an event that is mapped to one rule group. Click 1 Group under the Rule Groupcolumn.
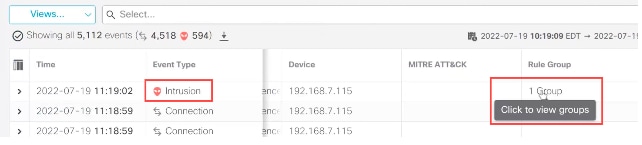 Rule group
Rule group
9. As an example, you can view Protocol, which is the parent rule group, and the DNS rule group under it.
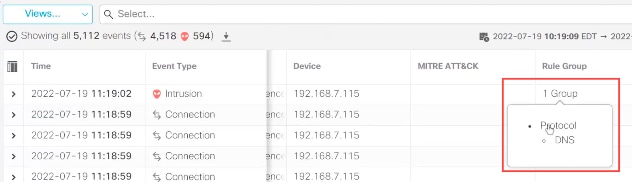 View protocol
View protocol
10. You can click Protocol to search for all the intrusion events that have at least one rule group, that is Protocol > DNS . The search results are displayed, as shown in the example here.
 Rule group protocol
Rule group protocol



















 Feedback
Feedback