Introduction
This document describes SAML Authentication with Azure identity provider for multiple connection profiles on Cisco FTD managed by FMC.
Prerequisites
Requirements
Cisco recommends knowledge of these topics:
- Secure Client configuration on Next Generation Firewall (NGFW) managed by Firepower Management Center (FMC)
- SAML and metatada.xml values
Components Used
The information in this document is based on these software and hardware versions:
- Firepower Threat Defense (FTD) version 7.4.0
- FMC version 7.4.0
- Azure Microsoft Entra ID with SAML 2.0
- Cisco Secure Client 5.1.7.80
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
This configuration allows FTD to authenticate secure client users using two different SAML application on Azure idp with a single SAML object configured on FMC.
In a Microsoft Azure environment, multiple applications can share the same Entity ID. Each application, typically mapped to a different tunnel group, necessitates a unique certificate, requiring the configuration of multiple certificates within the FTD side’s IdP configuration under a single SAML IdP object. However, Cisco FTD does not support the configuration of multiple certificates under one SAML IdP object, as detailed in Cisco bug ID CSCvi29084.
To overcome this limitation, Cisco has introduced the IdP certificate override feature, available from FTD version 7.1.0 and ASA version 9.17.1. This enhancement offers a permanent solution to the issue and complements the existing workarounds described in the bug report.
Configurations
This section outlines the process for configuring SAML authentication with Azure as the identity provider (IdP) for multiple connection profiles on Cisco Firepower Threat Defense (FTD) managed by Firepower Management Center (FMC). The IdP certificate override feature is utilized to set this up effectively.
Configuration Overview:
Two connection profiles are to be configured on Cisco FTD:
In this configuration sample, the VPN gateway URL (Cisco Secure Client FQDN) is set to nigarapa2.cisco.com
Configure
Configuration on Azure IdP
To configure your SAML enterprise applications for Cisco Secure Client effectively, ensure all parameters are set correctly for each tunnel group by completing these steps:
Access SAML Enterprise Applications:
Navigate to the administrative console of your SAML provider where your enterprise applications are listed.
Select the Appropriate SAML Application:
Identify and select the SAML applications corresponding to the Cisco Secure Client tunnel groups you intend to configure.
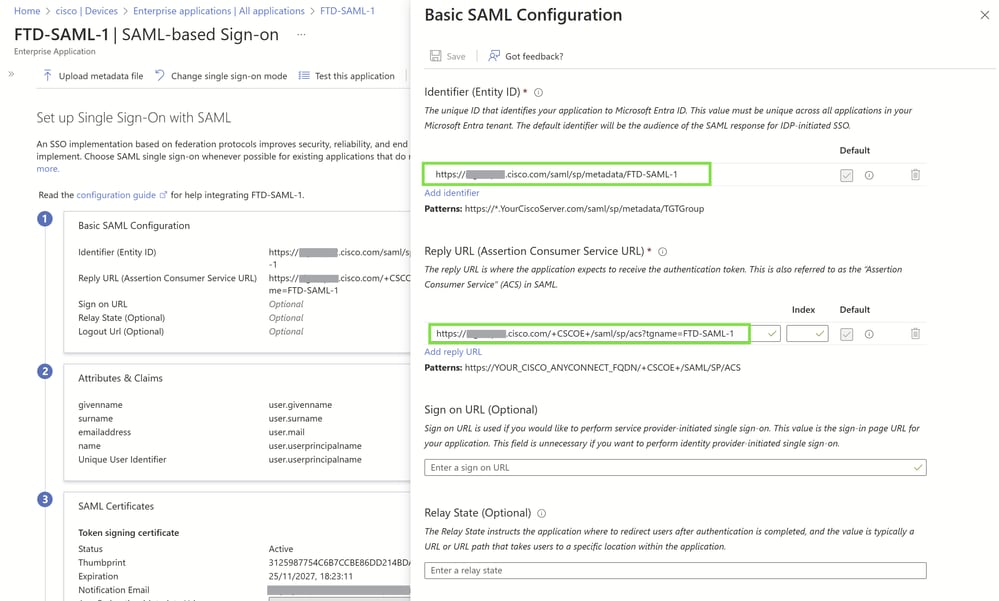
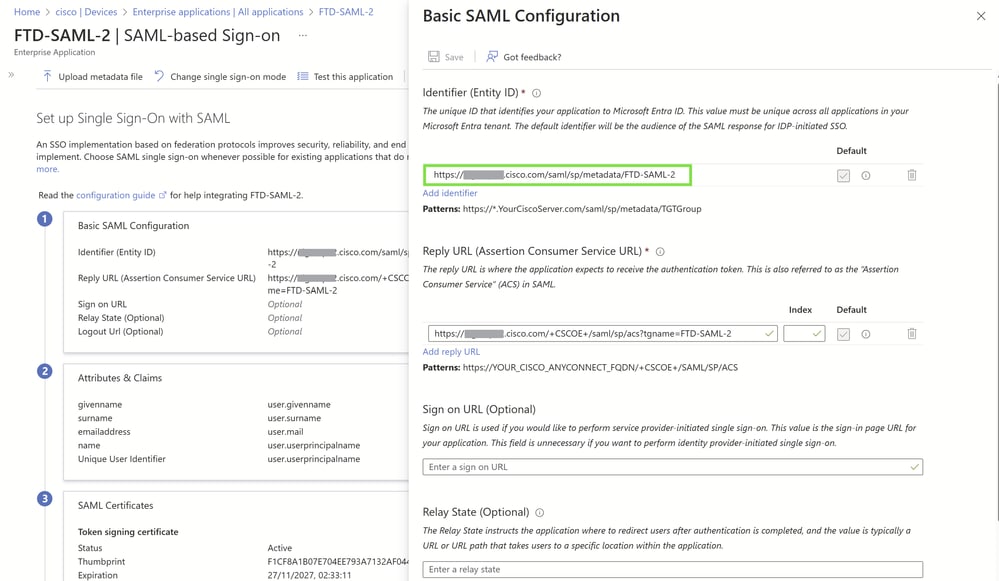
Configure the Identifier (Entity ID):
Set the Identifier (Entity ID) for each application. This must be the Base URL, which is your Cisco Secure Client Fully Qualified Domain Name (FQDN).
Set the Reply URL (Assertion Consumer Service URL):
Configure the Reply URL (Assertion Consumer Service URL) using the correct Base URL. Ensure it aligns with the Cisco Secure Client FQDN.
Append the connection profile or tunnel group name to the base URL to ensure specificity.
Verify Configuration:
Double-check that all URLs and parameters are correctly entered and correspond to the respective tunnel groups.
Save changes and, if possible, perform a test authentication to ensure the configuration is working as expected.
For more detailed guidance, refer to the "Add Cisco Secure Client from the Microsoft App Gallery" in the Cisco documentation: Configure ASA Secure Client VPN with Microsoft Azure MFA through SAML
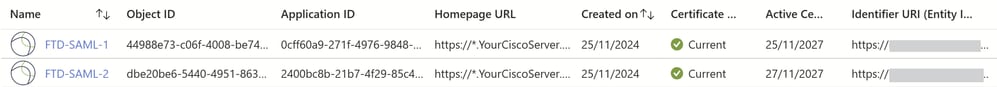
FTD-SAML-1
FTD-SAML-2
Now please ensure you have the necessary information and files for configuring SAML authentication with Microsoft Entra as your identity provider:
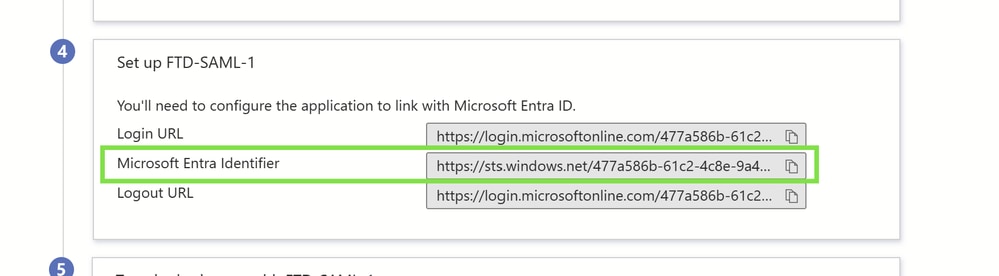
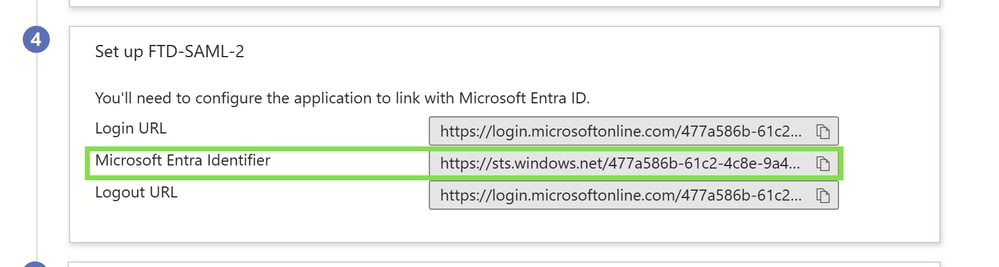
Locate the Microsoft Entra Identifier:
Access the settings for both SAML enterprise applications within your Microsoft Entra portal.
Note the Microsoft Entra Identifier, which remains consistent across both applications and is crucial for your SAML configuration.
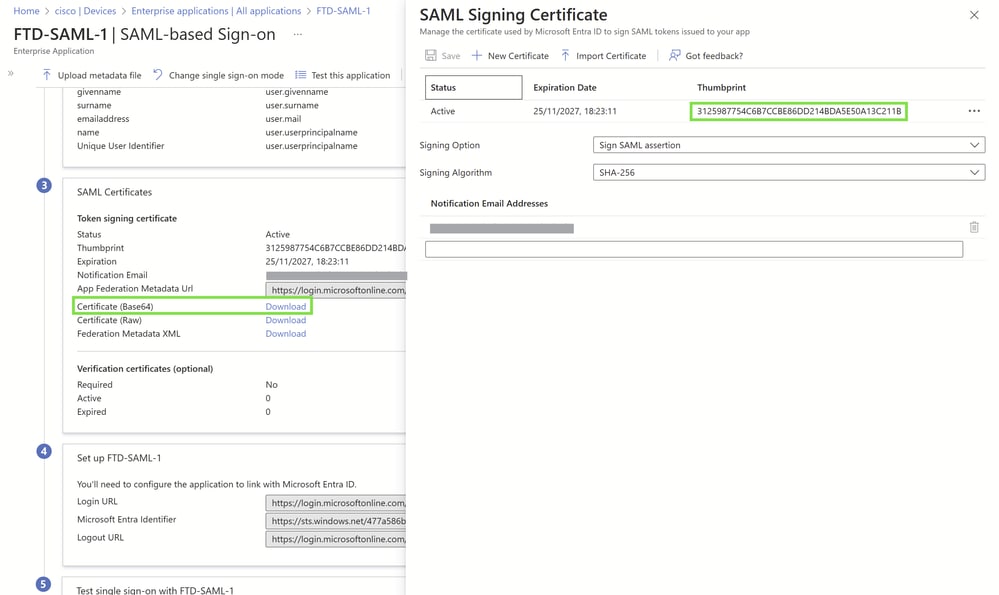
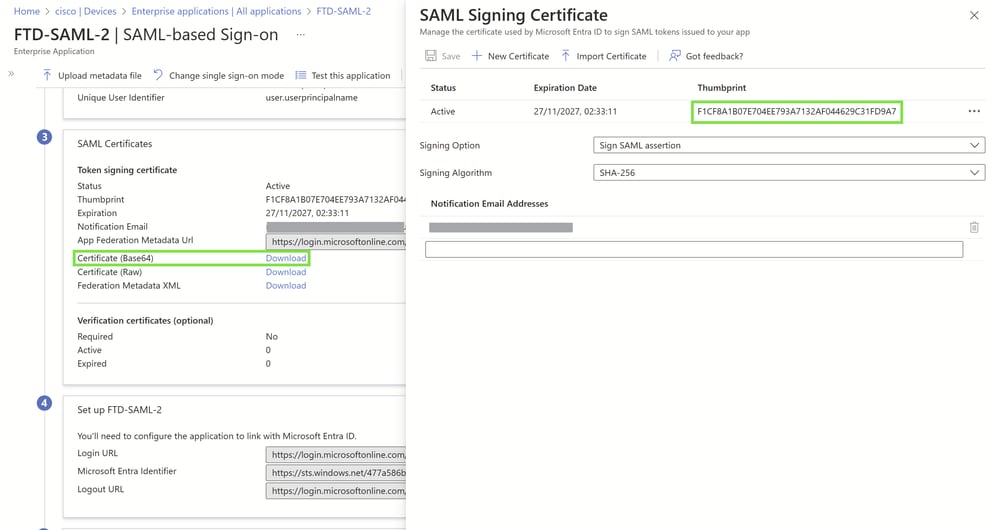
Download Base64 IdP Certificates:
Navigate to each configured SAML enterprise application.
Download the respective Base64-encoded IdP certificates. These certificates are essential for establishing trust between your identity provider and your Cisco VPN setup.

Note: All these SAML configurations required for the FTD connection profiles can also be sourced from the metadata.xml files provided by your IdP for the respective applications.

Note: To use a custom IdP certificate, you need to upload the custom-generated IdP certificate to both the IdP and FMC. For Azure IdP, ensure the certificate is in PKCS#12 format. On the FMC, upload only the Identity certificate from the IdP, not the PKCS#12 file. For detailed instructions, refer to the section "Upload the PKCS#12 File on Azure and FDM" in the Cisco documentation: Configure Multiple RAVPN Profiles with SAML Authentication on FDM
Configuration on the FTD via FMC
Enroll IdP Certificates:
Navigate to the certificates management section within FMC and enroll the downloaded Base64-encoded IdP certificates for both SAML applications. These certificates are vital for establishing trust and enabling SAML authentication.
For detailed guidance, please refer to the first two steps under "Configuration on the FTD via FMC" in the Cisco documentation available at: Configure Secure Client with SAML Authentication on FTD Managed via FMC.
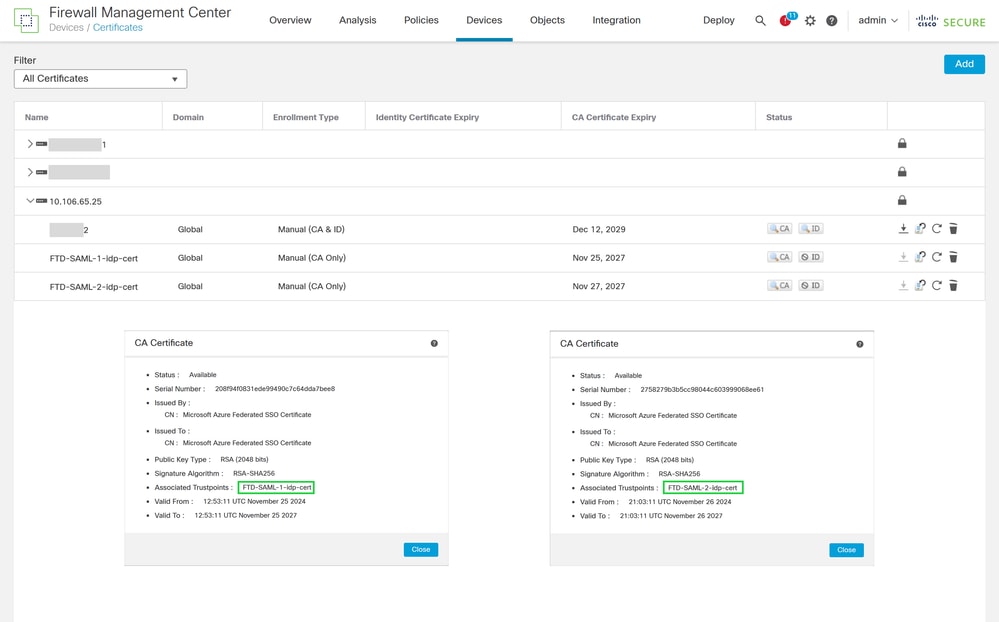

Note: The image has been edited to display both certificates simultaneously for better viewing. It is not possible to open both certificates at the same time on FMC.
Configuring SAML Server Settings on Cisco FTD via FMC
To configure the SAML server settings on your Cisco Firepower Threat Defense (FTD) using the Firepower Management Center (FMC), implement these steps:
- Navigate to Single Sign-on Server Configuration:
- Navigate to Objects > Object Management > AAA Servers > Single Sign-on Server.
- Click Add Single Sign-on Server to begin configuring a new server.
- Configure SAML Server Settings:
- Using the parameters collected from your SAML enterprise applications or from the metadata.xml file downloaded from your Identity Provider (IdP), fill in the necessary SAML values in the New Single Sign-on Server form.
- Key parameters to configure include:
- SAML Provider Entity ID: entityID from metadata.xml
- SSO URL: SingleSignOnService from metadata.xml.
- Logout URL: SingleLogoutService from metadata.xml.
- BASE URL: FQDN of your FTD SSL ID Certificate.
- Identity Provider Certificate: IdP Signing Certificate.
- Under the Identity Provider Certificate section, attach one of the enrolled IdP certificates
- For this use case, we are using the IdP certificate from the FTD-SAML-1 application.
- Service Provider Certificate: FTD Signing Certificate.
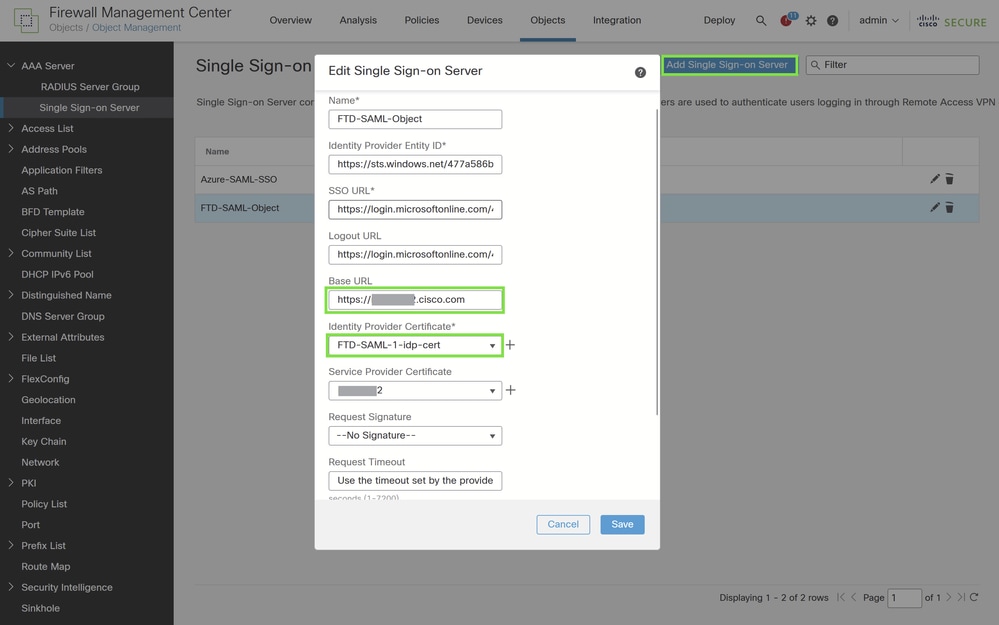

Note: In the current configuration, only the Identity Provider certificate can be overridden from the SAML object within the connection profile settings. Unfortunately, features such as "Request IdP re-authentication on login" and "Enable IdP only accessible on internal network" cannot be individually enabled or disabled for each connection profile.
Configuring Connection Profiles on Cisco FTD via FMC
To finalize the SAML authentication setup, you need to configure the connection profiles with the appropriate parameters and set AAA authentication to SAML using the previously configured SAML server.
For more detailed guidance, refer to the fifth step under "Configuration on the FTD via FMC" in the Cisco documentation: Configure Secure Client with SAML Authentication on FTD Managed via FMC.
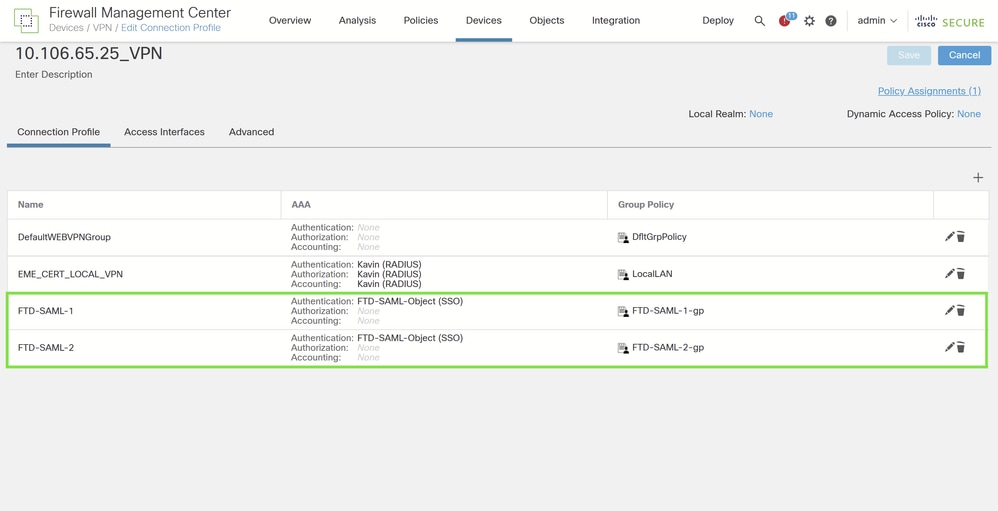
Extract of AAA Configuration for First Connection Profile
Here is an overview of the AAA configuration settings for the first connection profile:
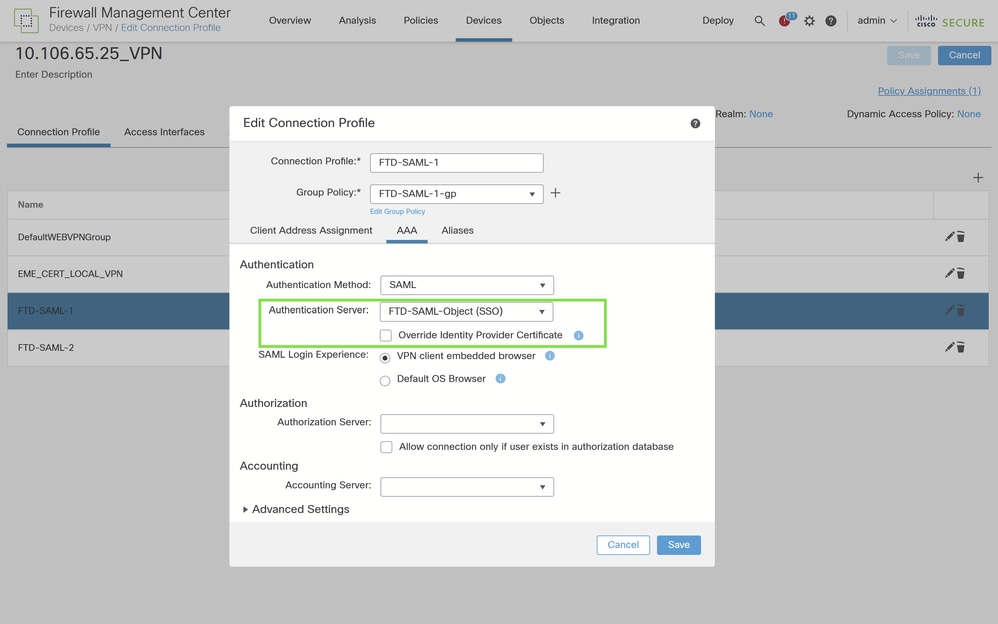
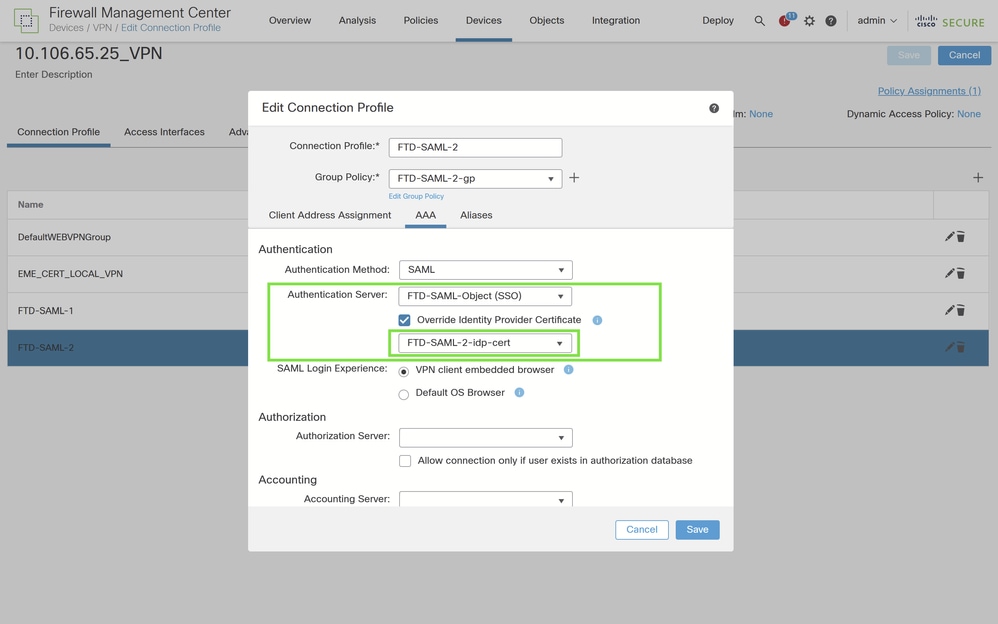
Configuring the IdP Certificate Override for the Second Connection Profile on Cisco FTD
To ensure the correct Identity Provider (IdP) certificate is used for the second connection profile, enable the IdP certificate override by completing these steps:
Within the connection profile settings, locate and enable the option "Override Identity Provider Certificate" to allow the use of a different IdP certificate than the one configured for the SAML server.
From the list of enrolled IdP certificates, select the certificate specifically enrolled for the FTD-SAML-2 application. This selection ensures that when an authentication request is made for this connection profile, the correct IdP certificate is used.
Deployment of configuration
Navigate toDeploy > Deploymentand select the proper FTD to apply the SAML Authentication VPN changes.
Verify
Configuration on the FTD command line
firepower# sh run webvpn
webvpn
enable outside
http-headers
hsts-server
enable
max-age 31536000
include-sub-domains
no preload
hsts-client
enable
x-content-type-options
x-xss-protection
content-security-policy
Secure Client image disk0:/csm/Secure Client-win-4.10.08025-webdeploy.pkg 1 regex "Windows"
Secure Client enable
saml idp https://sts.windows.net/477a586b-61c2-4c8e-9a41-1634016aa513/
url sign-in https://login.microsoftonline.com/477a586b-61c2-4c8e-9a41-1634016aa513/saml2
url sign-out https://login.microsoftonline.com/477a586b-61c2-4c8e-9a41-1634016aa513/saml2
base-url https://nigarapa2.cisco.com
trustpoint idp FTD-SAML-1-idp-cert
trustpoint sp nigarapa2
no signature
force re-authentication
tunnel-group-list enable
cache
disable
error-recovery disable
firepower#
firepower# sh run tunnel-group FTD-SAML-1
tunnel-group FTD-SAML-1 type remote-access
tunnel-group FTD-SAML-1 general-attributes
address-pool secure-client-pool
default-group-policy FTD-SAML-1-gp
tunnel-group FTD-SAML-1 webvpn-attributes
authentication saml
group-alias FTD-SAML-1 enable
saml identity-provider https://sts.windows.net/477a586b-61c2-4c8e-9a41-1634016aa513/
firepower#
firepower# sh run tunnel-group FTD-SAML-2
tunnel-group FTD-SAML-2 type remote-access
tunnel-group FTD-SAML-2 general-attributes
address-pool secure-client-pool
default-group-policy FTD-SAML-2-gp
tunnel-group FTD-SAML-2 webvpn-attributes
authentication saml
group-alias FTD-SAML-2 enable
saml identity-provider https://sts.windows.net/477a586b-61c2-4c8e-9a41-1634016aa513/
saml idp-trustpoint FTD-SAML-2-idp-cert
firepower#
Sign-in logs from Azure entra identifier
Access the Sign-in Logs section under enterprise application. Look for authentication requests related to the specific connection profiles, such as FTD-SAML-1 and FTD-SAML-2. Verify that users are successfully authenticating through the SAML applications associated with each connection profile.
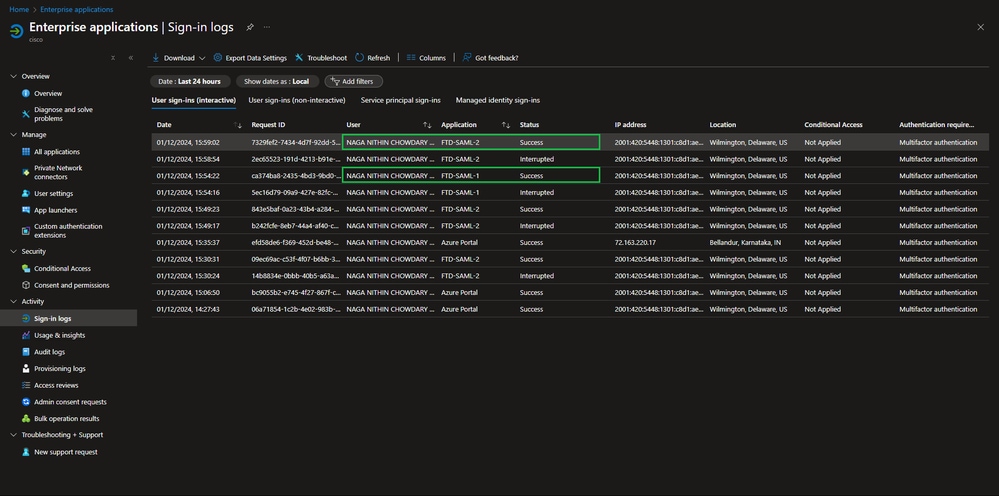 Sign-in Logs on Azure IdP
Sign-in Logs on Azure IdP
Troubleshoot
- You can troubleshoot using DART from the Secure Client user PC.
- To troubleshoot a SAML authentication issue, utilize this debug:
firepower# debug webvpn saml 255
- Verify the Secure Client configuration as explained above; this command can be used to check the certificate.
firepower# show crypto ca certificate















 Feedback
Feedback