Introduction
This document describes procedures to migrate Security Group Tags (SGTs) from Cisco DNA to ISE.
Prerequisites
ISE must be integrated with Cisco DNA.
Requirements
Cisco recommends knowledge in these topics:
- Identity Services Engine
- Cisco DNA
Components Used
The information in this document is based on these software and hardware versions:
- Identity Services Engine (ISE) version 3.3
- Cisco Cisco DNA
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
Security Groups enable effective segmentation for applications or business needs that do not require full network isolation but still demand security policy enforcement within the same virtual network.
By assigning Security Group Tags (SGTs) to endpoints or users, logical groupings are created to enforce policies.
Unlike traditional segmentation with virtual networks alone, SGTs provide micro-segmentation capabilities within a single virtual network, especially in SD-Access environments. They allow devices and users to be logically separated while remaining on the same network. As SGT technology evolves, it continues to deliver richer context and intent for more dynamic and flexible security policies.
Configure
Step 1: Go to Policy > Group-based Access Control > Security groups. Click Start migration as shown:
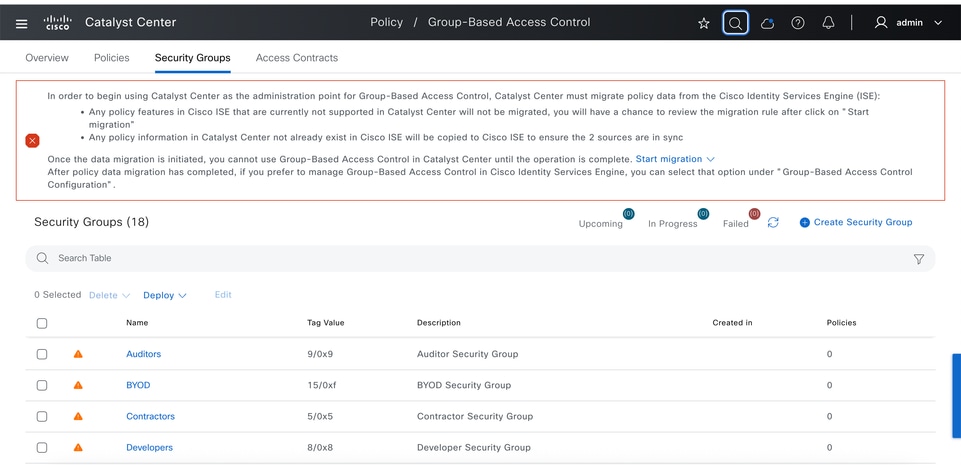
Step 2: A pop up appears. Click Yes.
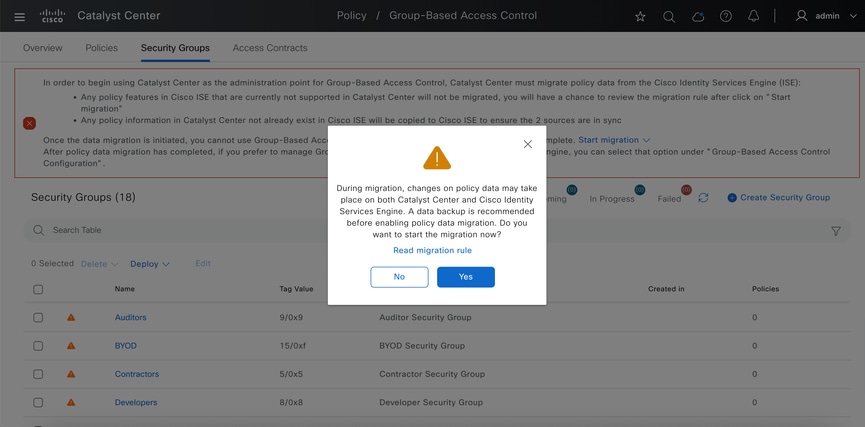
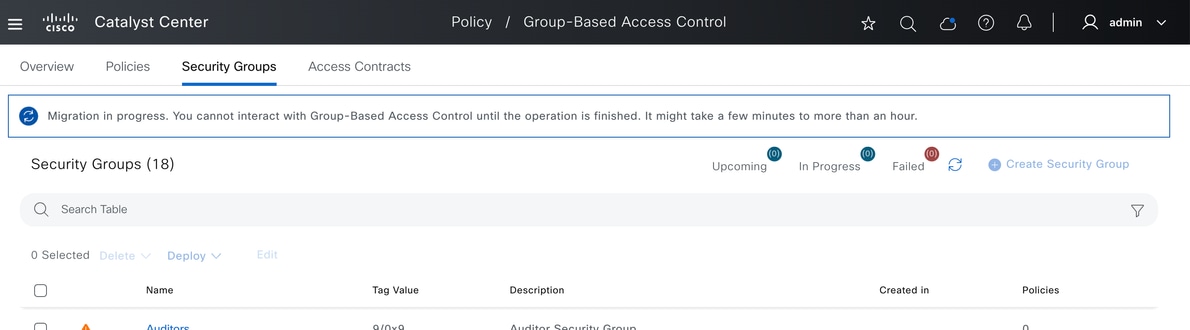
It shows Migration is in progress:
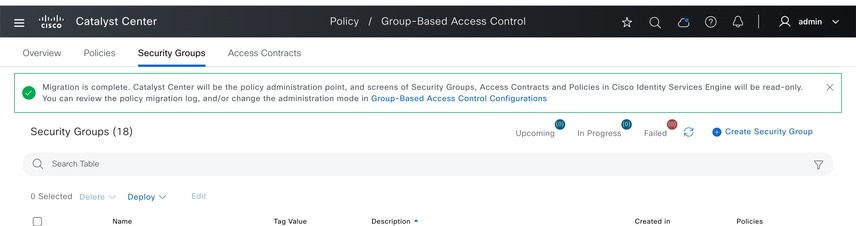
Step 3: Click Create security group and create the security group that you would like to push to ISE.
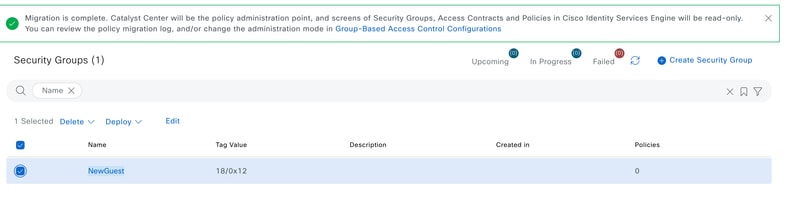
Once processed, it shows successfully the added security group.
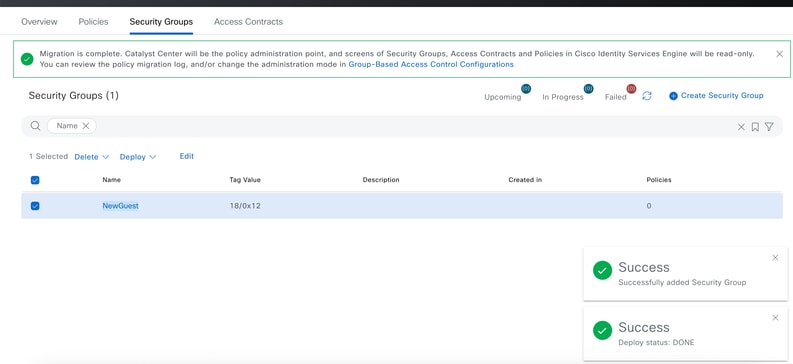
Verify
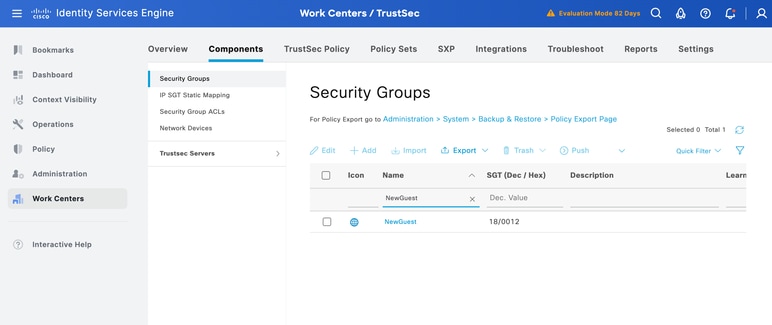
Validate in ISE that the NewGuest SGT tag is reflected under Workcenters > Trustsec > Security Groups as shown:
Troubleshooting
Logs Analysis from ISE
Security Group Tag NewGuest was created and published to ISE:
2025-06-08 16:45:55,671 INFO [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- Saving to UPS: NewGuest
2025-06-08 16:45:55,672 DEBUG [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- Created UPS security group NewGuest with ID 97f12c12-82ae-41c3-a20e-50c56e6bd304
2025-06-08 16:45:55,673 INFO [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- SGT NewGuest has 0 default SGACLs
2025-06-08 16:45:55,673 INFO [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- Adding 0 SGACLs to SGT NewGuest
2025-06-08 16:45:55,675 INFO [pool-27182-thread-1][[]] mnt.dbms.datadirect.impl.DatadirectServiceImpl -:::::- Executing getStatus - datadirectSettings
2025-06-08 16:45:55,676 INFO [pool-27182-thread-1][[]] mnt.dbms.datadirect.impl.DatadirectServiceImpl -:::::- Executing getStatus - datadirectSettings
2025-06-08 16:45:55,676 INFO [pool-27182-thread-1][[]] com.cisco.epm.jms.AQMessgeHandler -:::::- Publishing message for event [TxnCommit / commit] and message class[com.cisco.cpm.deployment.replication.ups.UPSChangeSet]
Security Group Tag NewGuest was inserted in the ISE database:
2025-06-08 16:45:55,678 DEBUG [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.NSFAdminUtil -:::::- Host Name kavinise33ppan
2025-06-08 16:45:55,679 DEBUG [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.NSFAdminUtil -:::::- Host Name kavinise33ppan
2025-06-08 16:45:55,681 INFO [pool-27182-thread-1][[]] cpm.trustsec.securitygroup.service.SgtNotificationRedirect -:::::- Got post commit for UPS actions INSERT,INSERT
2025-06-08 16:45:55,681 DEBUG [pool-27182-thread-1][[]] cpm.trustsec.securitygroup.service.SgtNotificationRedirect -:::::- Constructed NSF notification for SGT NewGuest ID 97f12c12-82ae-41c3-a20e-50c56e6bd304 action INSERT
2025-06-08 16:45:55,681 INFO [pool-27182-thread-1][[]] acs.nsf.config.trustsec.CTSNotificationsService -:::::- Got post commit for UPS actions:
2025-06-08 16:45:55,681 INFO [pool-27182-thread-1][[]] acs.nsf.config.trustsec.CTSNotificationsService -:::::- [ Class: SecurityGroupData, ActionType: INSERT ]
Security Group Tag NewGuest was created and updated in ISE SGT database:
2025-06-08 16:45:55,685 DEBUG [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- end transaction :: saving SGT
2025-06-08 16:45:55,685 INFO [pool-27182-thread-1][[]] cisco.cpm.nsf.impl.SecGroup -:::::- created SGT : NewGuest
2025-06-08 16:45:59,238 DEBUG [com.cisco.cpm.prrt.impl.PrRTNotificationHandler@11d54366_DelayedSingle][[]] cisco.cpm.prrt.impl.PrRTConfigurator -:::::- ProtocolRuntime: Configuring SecGroup NewGuest: value: 18, genId: 00, Is From SGT Range: false








 Feedback
Feedback