Integrate ISE 3.3 with WSA Using External CA
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes procedures to integrate ISE 3.3 with Cisco Secure Web Appliance (WSA) using pxGrid connections.
Prerequisites
Requirements
Cisco recommends knowledge in these topics:
- Identity Services Engine
- Cisco Secure Web Appliance (WSA)
- Platform Exchange Grid (pxGrid)
- TLS/SSL Certificates.
- PKI on Windows Server 2016
Components Used
The information in this document is based on these software and hardware versions:
- Identity Services Engine (ISE) version 3.3 patch 4
- Cisco Secure Web Appliance version 15.2.0-116
- Windows server 2016 as an External Certificate Authority (CA) server.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Configure
Section A: Cisco Identity Services Engine 3.3 Certificate Configuration
Step 1: Generate anISEServer pxGrid Certificate
Generate a CSR for an ISE server pxGrid certificate:
1.Log into Cisco Identity Services Engine (ISE) GUI.
2.NavigatetoAdministration > System > Certificates > Certificate Management >Certificate Signing Requests.
3. SelectGenerate Certificate Signing Request (CSR).
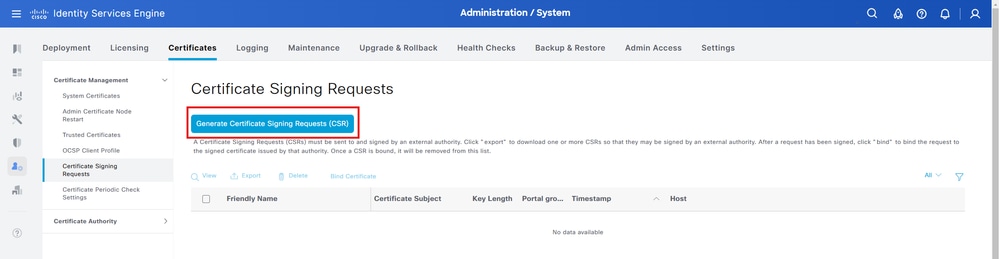
4. SelectpxGridin the Certificate(s) is used for field.
5. SelectISE nodefor which the certificate is generated.
6.Fillin other certificates details as necessary.
7. ClickGenerate.

8. ClickExportandSavethe file locally.
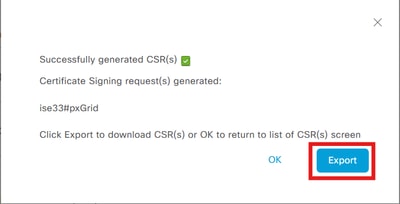
Step 2: Create an ISE Server pxGrid Certificate Using an External CA
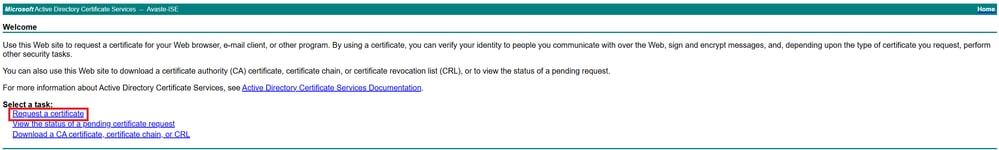
1.Navigate to MS Active Directory Certificate Service,https://server/certsrv/, where server is IP or DNS of your MS Server.
2. ClickRequest a certificate.
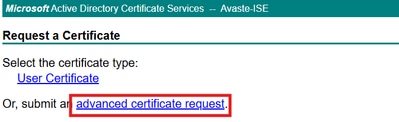
3. Choose to submit anadvanced certificate request.
4.Copythe contents of the CSR generated in the previous section into theSaved Request field.
5. SelectpxGridas theCertificate Template, then clickSubmit.
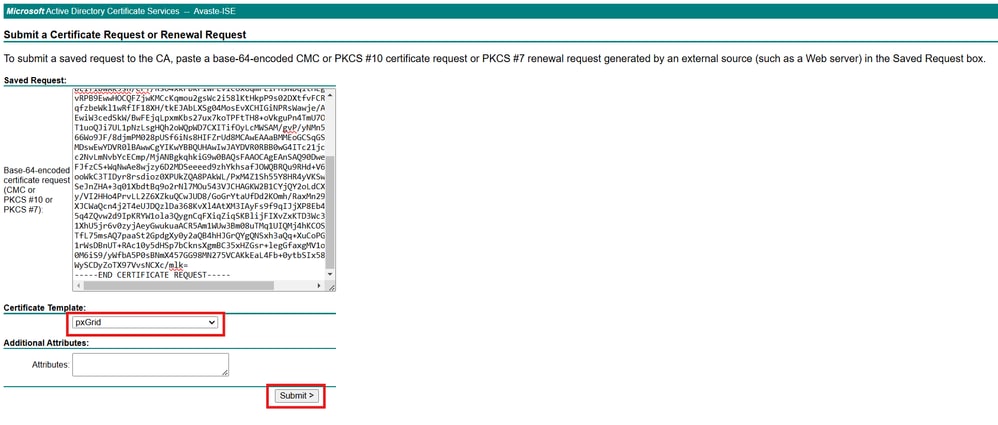

Note: Certificate Template pxGrid used needs both Client authentication and server authentication in the Enhanced Key Usage field.
6.Downloadthe generated certificate inBase-64format andSaveit as ISE_pxGrid.cer.
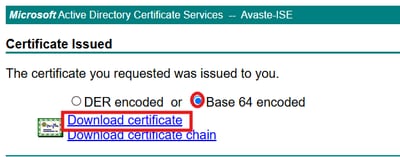
Step 3: Import the CA Root Certificate into the ISE Trust Store
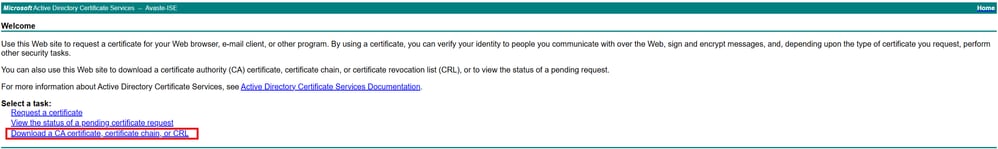
1.Navigate to MS Active Directory Certificate Servicehome page and selectDownload a CA certificate, certificate chain, or CRL.
2. SelectBase-64format, then clickDownloadCA certificate.
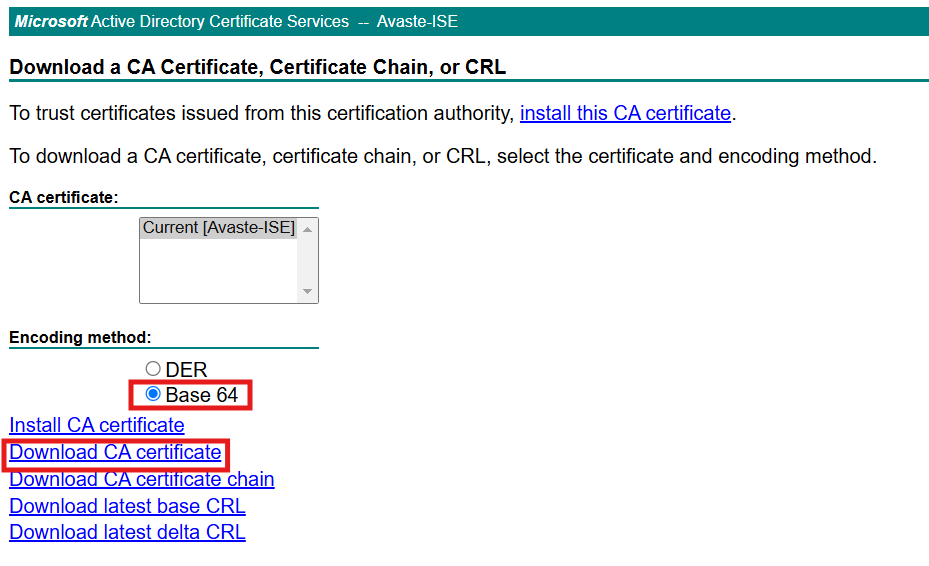
3.Savethe certificate as CA_Root.cer.
4.Log into Cisco Identity Services Engine (ISE) GUI.
5. SelectAdministration > System > Certificates > Certificate Management >Trusted Certificates.
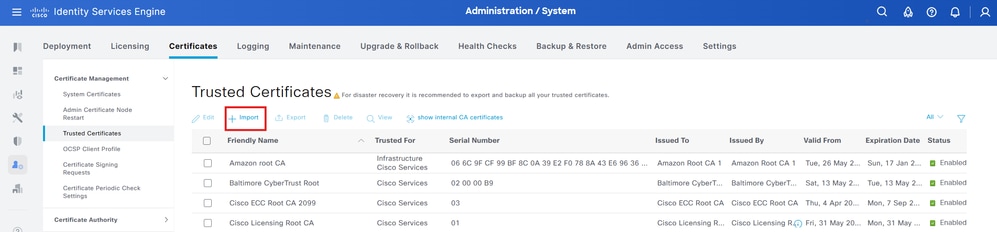
6. SelectImport > Certificate fileandImportthe root certificate.
7. Ensure theTrust for authentication within ISEcheck box is selected.
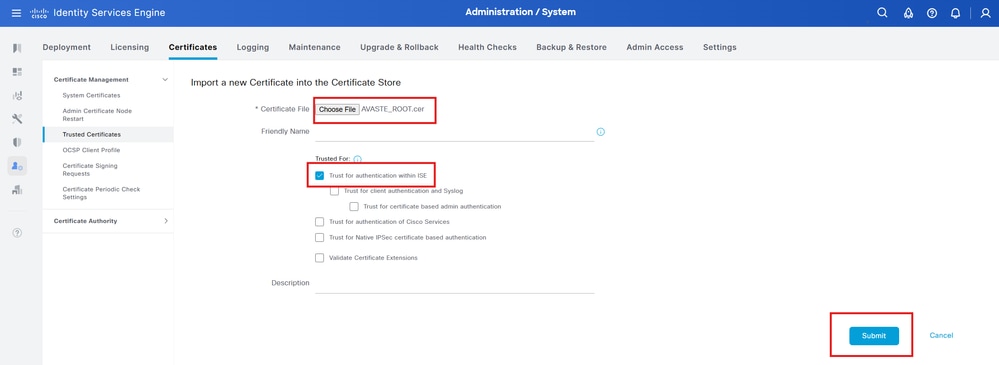
8. ClickSubmit.
Step 4: Binding the ISE certificate to the Certificate Signing Request (CSR).
1.Log into Cisco Identity Services Engine (ISE) GUI.
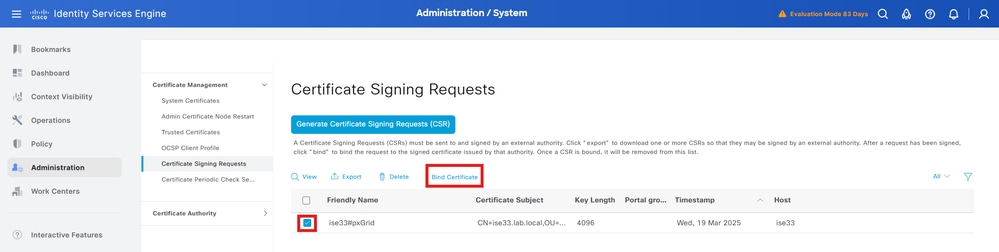
2. SelectAdministration > System > Certificates > Certificate Management >Certificate Signing Requests.
3. Select the CSR generated in the previous section, then clickBind Certificate.
4. On the Bind CA Signed Certificate form,choosethe ISE_pxGrid.cer certificate generated previously.
5. Give the certificate a friendly name, then clickSubmit.
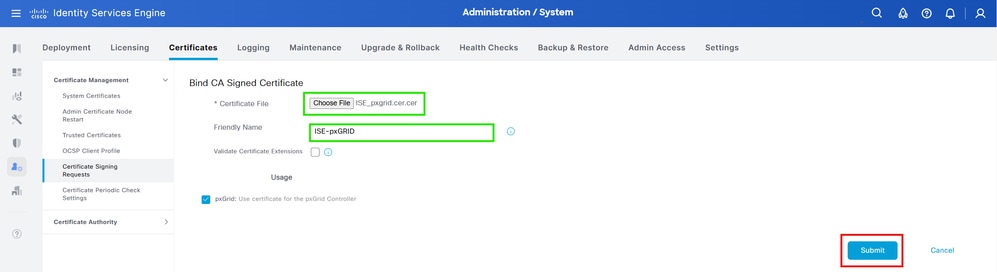
7. ClickYesif the system asks to replace the certificate.
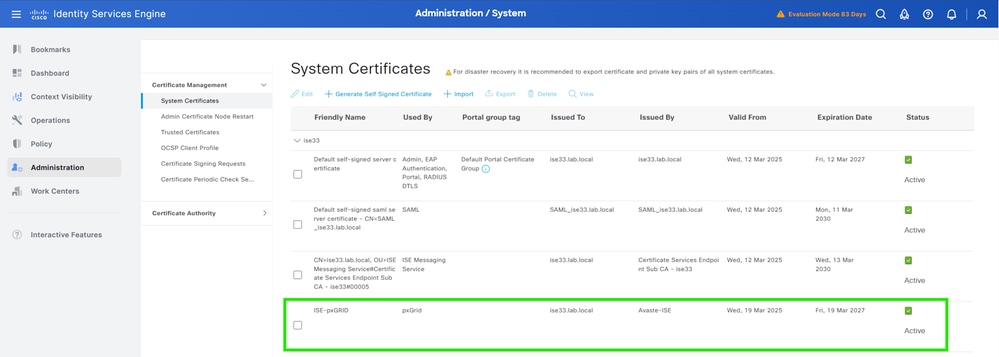
8. SelectAdministration > System > Certificates > System Certificates.
9. You can see the created pxGrid certificate signed by the external CA in the list.
Section B: Adding CA Root Certificate to WSA Certificate Trust Store
Add CA Root Certificate to WSA Trusted Store:
1.Log into Web Security Appliance (WSA) GUI.
2. Navigate to Network > Certificate Management > Manage Trusted Root Certificates.

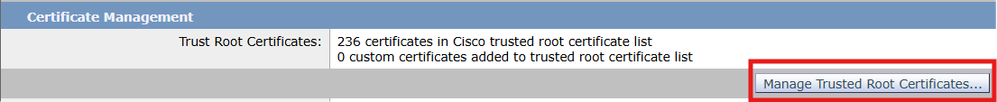
3. Import and upload the CA root certificate, then click Submit.

4. Click Commit Changes to Apply the changes.

Certificates are now deployed, proceed for Integration.
Integration
Before proceeding to integrate, ensure that:
For Cisco ISE under Administration > pxGrid Services > SettingsandCheck Automatically approve new certificate-based accounts for Client request to Auto-approve andSave.

Section A: Enable WSA for ISE integration and generate CSR for WSA Client Certificate.
1.Log into Web Security Appliance (WSA) GUI.
2. Navigate to Network > Identification Services >Identification Service Engine.

3.Click Enable and Edit Settings.
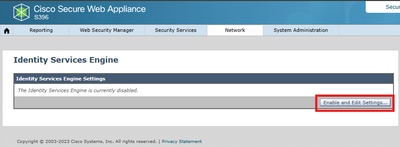
4.Enter the Primary ISE pxGrid Node IP address or FQDN.
5.Upload the CA root certificate for the primary pxGrid node.
6.Enter the Secondary ISE pxGrid Node IP address or FQDN.(Optional)
7.Upload the CA root certificate for the secondary pxGrid node. (Optional)


Note: There can be only two pxGrid nodes per ISE deployment. This serves as a pxGrid Active-Standby configuration; only one ISE+pxGrid node can be active at a time. In a pxGrid Active-Standby configuration, all information is passed through the PPAN, where the second ISE+pxGrid node remains inactive.
8. Scroll to the Web Appliance Client Certificate section and click Generate New Certificate and Key.

9. Fillin certificate details as necessary and Click Generate.


Note: Duration of certificate must be an integer between 24 and 60 months and Country must be a ISO two character country code (uppercase letters only).
10. Click Download Certificate Signing Request.

11. Click Submit.
12. Click Commit Changes to Apply the changes.

Warning: If you do not submit and commit mentioned changes and directly upload the signed certificate and perform commit, you can face issues during the integration.
Section B: Sign an WSA client CSR Using an External CA
1.Navigate to MS Active Directory Certificate Service,https://server/certsrv/, where server is IP or DNS of your MS Server.
2. ClickRequest a certificate.

3. Choose to submit an advanced certificate request.
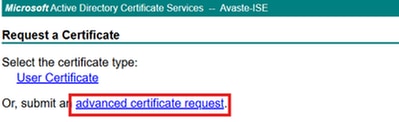
4.Copythe contents of the CSR generated in the previous section into theSaved Request field.
5. SelectpxGridas theCertificate Template, then clickSubmit.


Note: Note: Certificate Template pxGrid used needs both Client authentication and server authentication in the Enhanced Key Usage field.
6.Downloadthe generated certificate inBase-64format andSaveit as WSA-Client.cer.

Section C: Binding the WSA client certificate to the Certificate Signing Request (CSR) and integrating.
1.Navigateto Web Security Appliance (WSA) GUI.
2. Navigate to Network > Identification Services >Identification Service Engine.
3.Click Edit Settings.
4.Navigate to Web Appliance Client Certificate section.
5.Under the signed certificate section, Upload the signed certificate WSA-Client.cer
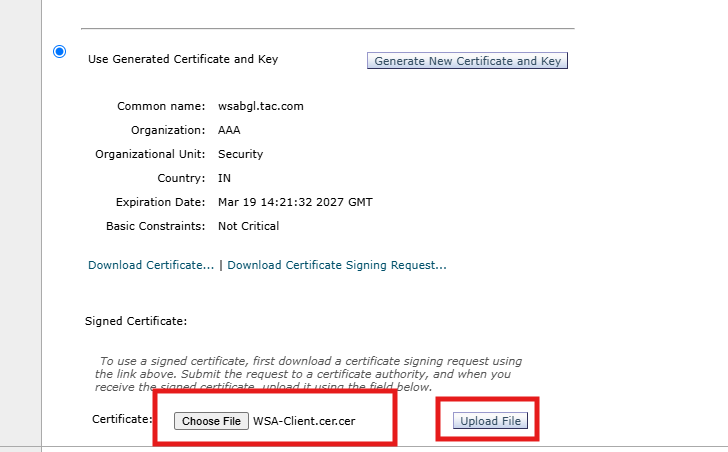
6.Click Submit.
7.Click Commit Changes to Apply the changes.
8.Click Edit Settings.
9.Scroll to Test Communication with ISE Nodes and click Start Test, which can result as follows:
- Test Communication with ISE Nodes
- Test Communication with ISE Nodes
Checking DNS resolution of ISE pxGrid Node hostname(s) ...
Success: Resolved '10.127.197.128' address: 10.127.197.128
Validating WSA client certificate ...
Success: Certificate validation successful
Validating ISE pxGrid Node certificate(s) ...
Success: Certificate validation successful
Checking connection to ISE pxGrid Node(s) ...
Trying primary PxGrid server...
SXP not enabled.
ERS not enabled.
Preparing TLS connection...
Completed TLS handshake with PxGrid successfully.
Trying download user-session from (https://ise33.lab.local:8910)...
Failure: Failed to download user-sessions.
Trying download SGT from (https://ise33.lab.local:8910)...
Able to Download 17 SGTs.
Skipping all SXP related service requests as SXP is not configured.
Success: Connection to ISE pxGrid Node was successful.
Test completed successfully.
Verify
On Cisco ISE, navigate toAdministration >pxGrid Services > Client Management > Clients.
This generates the WSA as a pxgrid client with the statusEnabled.

To verify topic subscription on Cisco ISE, navigate toAdministration >pxGrid Services > Diagnostics > Websocket > Clients:

Cisco ISE Pxgrid-server.log TRACE level.reference.
{"timestamp":1742395398803,"level":"INFO","type":"WS_SERVER_CONNECTED","host":"ise33","client":"wsabgl.lab.local_ised","server":"wss://ise33.lab.local:8910/pxgrid/ise/pubsub","message":"WebSocket connected. session\u003d[id\u003d4,client\u003dwsabgl.lab.local_ised,server\u003dwss://ise33.lab.local:8910/pxgrid/ise/pubsub]"}
TRACE [Thread-8][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Drop. exclude=[id=3,client=~ise-fanout-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub]
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.config.MyX509Filter -::::::- Authenticating null
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.config.MyX509Filter -::::::- Certs up to date. user=~ise-pubsub-ise33
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.config.MyX509Filter -::::::- preAuthenticatedPrincipal = ~ise-pubsub-ise33, trying to authenticate
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.config.MyX509Filter -::::::- X.509 client authentication certificate subject:CN=ise33.lab.local, OU=AAA, O=Cisco, L=Bangalore, ST=KA, C=IN, issuer:CN=Avaste-ISE, DC=avaste, DC=local
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.config.MyX509Filter -::::::- Authentication success: PreAuthenticatedAuthenticationToken [Principal=org.springframework.security.core.userdetails.User [Username=~ise-pubsub-ise33, Password=[PROTECTED], Enabled=true, AccountNonExpired=true, credentialsNonExpired=true, AccountNonLocked=true, Granted Authorities=[ROLE_USER]], Credentials=[PROTECTED], Authenticated=true, Details=WebAuthenticationDetails [RemoteIpAddress=10.127.197.128, SessionId=null], Granted Authorities=[ROLE_USER]]
DEBUG [Thread-8][[]] cisco.cpm.pxgridwebapp.data.AuthzDaoImpl -::::::- requestNodeName=wsabgl.lab.local_ised serviceName=com.cisco.ise.pubsub operation=subscribe /topic/com.cisco.ise.session
DEBUG [Thread-13][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Adding subscription=[id=my-id,topic=/topic/com.cisco.ise.session]
INFO [Thread-13][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Pubsub subscribe. subscription=[id=my-id,topic=/topic/com.cisco.ise.session] session=[id=4,client=wsabgl.lab.local_ised,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub]
TRACE [WsIseClientConnection-804][[]] cpm.pxgrid.ws.client.WsEndpoint -::::::- Send. session=[id=34eae17d-594f-4dcd-b3e6-f2f644317eda,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] frame=[command=SEND,headers=[content-length=395, trace-id=6d3dcbc0a34346eeb9bafccd570f8090, destination=/topic/com.cisco.ise.pxgrid.admin.log],content-len=395] content={"timestamp":1742395398821,"level":"INFO","type":"PUBSUB_SERVER_SUBSCRIBE","host":"ise33","client":"wsabgl.lab.local_ised","server":"wss://ise33.lab.local:8910/pxgrid/ise/pubsub","message":"Pubsub subscribe. subscription\u003d[id\u003dmy-id,topic\u003d/topic/com.cisco.ise.session] session\u003d[id\u003d4,client\u003dwsabgl.lab.local_ised,server\u003dwss://ise33.lab.local:8910/pxgrid/ise/pubsub]"}
TRACE [Thread-3][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Received frame=[command=SEND,headers=[content-length=395, trace-id=6d3dcbc0a34346eeb9bafccd570f8090, destination=/topic/com.cisco.ise.pxgrid.admin.log],content-len=395], content={"timestamp":1742395398821,"level":"INFO","type":"PUBSUB_SERVER_SUBSCRIBE","host":"ise33","client":"wsabgl.lab.local_ised","server":"wss://ise33.lab.local:8910/pxgrid/ise/pubsub","message":"Pubsub subscribe. subscription\u003d[id\u003dmy-id,topic\u003d/topic/com.cisco.ise.session] session\u003d[id\u003d4,client\u003dwsabgl.lab.local_ised,server\u003dwss://ise33.lab.local:8910/pxgrid/ise/pubsub]"}
TRACE [Thread-3][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Authorized to send (cached). session=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] topic=/topic/com.cisco.ise.pxgrid.admin.log
TRACE [Thread-3][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute from=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] topic=/topic/com.cisco.ise.pxgrid.admin.log content={"timestamp":1742395398821,"level":"INFO","type":"PUBSUB_SERVER_SUBSCRIBE","host":"ise33","client":"wsabgl.lab.local_ised","server":"wss://ise33.lab.local:8910/pxgrid/ise/pubsub","message":"Pubsub subscribe. subscription\u003d[id\u003dmy-id,topic\u003d/topic/com.cisco.ise.session] session\u003d[id\u003d4,client\u003dwsabgl.lab.local_ised,server\u003dwss://ise33.lab.local:8910/pxgrid/ise/pubsub]"}
TRACE [Thread-3][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute distributed. subscription=[id=0,topic=/topic/com.cisco.ise.pxgrid.admin.log]
TRACE [Thread-3][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute distributed. subscription=[id=2,topic=/topic/wildcard]
TRACE [sub-sender-1][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionSender -::::::- Send. subscription=[id=2,topic=/topic/wildcard] from=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] to=[id=1,client=~ise-fanout-ise33,server=wss://localhost:8910/pxgrid/ise/pubsub] message=[command=MESSAGE,headers=[content-length=395, trace-id=6d3dcbc0a34346eeb9bafccd570f8090, destination=/topic/com.cisco.ise.pxgrid.admin.log, message-id=37248],content-len=395]
TRACE [sub-sender-0][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionSender -::::::- Send. subscription=[id=0,topic=/topic/com.cisco.ise.pxgrid.admin.log] from=null to=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] message=[command=MESSAGE,headers=[content-length=395, trace-id=6d3dcbc0a34346eeb9bafccd570f8090, destination=/topic/com.cisco.ise.pxgrid.admin.log, message-id=37248],content-len=395]
DEBUG [Grizzly(1)][[]] cpm.pxgrid.ws.client.WsSubscriber -::::::- onStompMessage session=[id=34eae17d-594f-4dcd-b3e6-f2f644317eda,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] subscription=[id=0,topic=/topic/com.cisco.ise.pxgrid.admin.log]
DEBUG [Grizzly(1)][[]] cpm.pxgrid.ws.client.WsSubscriber -::::::- onStompMessage session=[id=4b4d7de4-b960-49f7-afac-9adab3238481,client=~ise-fanout-ise33,server=wss://localhost:8910/pxgrid/ise/pubsub] subscription=[id=2,topic=/topic/wildcard]
TRACE [Grizzly(1)][[]] cpm.pxgrid.ws.client.WsEndpoint -::::::- Send. session=[id=dd1d138d-a640-4f4f-bd4d-169d0cf5d937,client=~ise-fanout-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] frame=[command=SEND,headers=[content-length=570, destination=/topic/distributed, from=~ise-fanout-ise33, via=~ise-fanout-ise33],content-len=570] content=MESSAGE
TRACE [Grizzly(1)][[]] cpm.pxgridwebapp.ws.distributed.FanoutDistributor -::::::- DownstreamHandler sent frame for upstream. frame=[command=SEND,headers=[content-length=570, destination=/topic/distributed, from=~ise-fanout-ise33, via=~ise-fanout-ise33],content-len=570]
TRACE [Thread-10][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Received frame=[command=SEND,headers=[content-length=570, destination=/topic/distributed, from=~ise-fanout-ise33, via=~ise-fanout-ise33],content-len=570], content=MESSAGE
TRACE [Thread-10][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Authorized to send (cached). session=[id=3,client=~ise-fanout-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] topic=/topic/distributedTroubleshooting
Problem
Unknown CA Issue, On the WSA the test for ISE connection fails with error. Failure: Connection to ISE PxGrid server timed out.

Cisco ISE Pxgrid-server.log TRACE level.reference.
ERROR [Thread-8][[]] cisco.cpm.pxgrid.cert.LoggingTrustManagerWrapper -::::::- checkClientTrusted exception.message=PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target principle=CN=wsabgl.lab.local, OU=Security, O=AAA, C=IN
TRACE [WsIseClientConnection-804][[]] cpm.pxgrid.ws.client.WsEndpoint -::::::- Send. session=[id=34eae17d-594f-4dcd-b3e6-f2f644317eda,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] frame=[command=SEND,headers=[content-length=338, trace-id=0f31b9311a2940a9bdeb0c8c647f6083, destination=/topic/com.cisco.ise.pxgrid.admin.log],content-len=338] content={"timestamp":1742395129748,"level":"ERROR","host":"ise33","message":"checkClientTrusted exception.message\u003dPKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target principle\u003dCN\u003dwsabgl.lab.local, OU\u003dSecurity, O\u003dAAA, C\u003dIN"}
TRACE [Thread-9][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Received frame=[command=SEND,headers=[content-length=338, trace-id=0f31b9311a2940a9bdeb0c8c647f6083, destination=/topic/com.cisco.ise.pxgrid.admin.log],content-len=338], content={"timestamp":1742395129748,"level":"ERROR","host":"ise33","message":"checkClientTrusted exception.message\u003dPKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target principle\u003dCN\u003dwsabgl.lab.local, OU\u003dSecurity, O\u003dAAA, C\u003dIN"}
TRACE [Thread-9][[]] cpm.pxgridwebapp.ws.pubsub.StompPubsubEndpoint -::::::- Authorized to send (cached). session=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] topic=/topic/com.cisco.ise.pxgrid.admin.log
TRACE [Thread-9][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute from=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] topic=/topic/com.cisco.ise.pxgrid.admin.log content={"timestamp":1742395129748,"level":"ERROR","host":"ise33","message":"checkClientTrusted exception.message\u003dPKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target principle\u003dCN\u003dwsabgl.lab.local, OU\u003dSecurity, O\u003dAAA, C\u003dIN"}
TRACE [Thread-9][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute distributed. subscription=[id=0,topic=/topic/com.cisco.ise.pxgrid.admin.log]
TRACE [Thread-9][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionDistributor -::::::- Distribute distributed. subscription=[id=2,topic=/topic/wildcard]
TRACE [sub-sender-1][[]] cpm.pxgridwebapp.ws.pubsub.SubscriptionSender -::::::- Send. subscription=[id=2,topic=/topic/wildcard] from=[id=0,client=~ise-admin-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] to=[id=1,client=~ise-fanout-ise33,server=wss://localhost:8910/pxgrid/ise/pubsub] message=[command=MESSAGE,headers=[content-length=338, trace-id=0f31b9311a2940a9bdeb0c8c647f6083, destination=/topic/com.cisco.ise.pxgrid.admin.log, message-id=37180],content-len=338]
DEBUG [Grizzly(2)][[]] cpm.pxgrid.ws.client.WsSubscriber -::::::- onStompMessage session=[id=4b4d7de4-b960-49f7-afac-9adab3238481,client=~ise-fanout-ise33,server=wss://localhost:8910/pxgrid/ise/pubsub] subscription=[id=2,topic=/topic/wildcard]
TRACE [Grizzly(2)][[]] cpm.pxgrid.ws.client.WsEndpoint -::::::- Send. session=[id=dd1d138d-a640-4f4f-bd4d-169d0cf5d937,client=~ise-fanout-ise33,server=wss://ise33.lab.local:8910/pxgrid/ise/pubsub] frame=[command=SEND,headers=[content-length=513, destination=/topic/distributed, from=~ise-fanout-ise33, via=~ise-fanout-ise33],content-len=513] content=MESSAGE
The reason for the failure can be seen with packet captures,

Solution
1. Ensure the Web Appliance signed certificate is bind successfully on the WSA and changes have been committed.
2. Ensure the issuer or the Root CA certificate of WSA Client certificate is part of Trusted Store on Cisco ISE.
Known Defects
| Cisco Bug ID | Description |
| Cisco bug ID 23986 | Pxgrid getUserGroups API request return empty response. |
| Cisco bug ID 77321 | WSA receives SIDs instead of AD groups from ISE. |
Revision History
| Revision | Publish Date | Comments |
|---|---|---|
1.0 |
26-Mar-2025
|
Initial Release |
Contributed by Cisco Engineers
- Anurag VasteTechnical Consulting Engineer
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback