Introduction
This document describes the steps required to integrate Cisco Identity Services Engine with Catalyst Center to enable TACACS+ authentication.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
-
Administrator access to both Cisco ISE and Cisco Catalyst Center.
-
Basic understanding of AAA (Authentication, Authorization, and Accounting) concepts.
-
Working knowledge of TACACS+ protocol.
-
Network connectivity between Catalyst Center and the ISE server.
Components Used
The information in this document is based on these hardware and software version:
-
Cisco Catalyst Center version 2.3.7.x
-
Cisco Identity Services Engine (ISE) version 3.x (or later)
-
TACACS+ protocol for external user authentication
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
This integration allows external users to log in to Catalyst Center for administrative access and management.
Configure
Cisco Identity Services Engine (ISE)
License and Enable the TACACS+ Services
Before you start with the TACACS+ configuration in ISE, you must confirm that the correct license is installed and the feature is enabled.
-
Verify that you have the PID license L-ISE-TACACS-ND= in the Cisco Smart Software Manage or Cisco License Central portal.
Enable Device Administration in the ISE Licensing portal.
- The Device Admin license (PID: L-ISE-TACACS-ND=) enables TACACS+ services on a Policy Service Node (PSN).
-
Navigate to:
Administration > System > Licensing
- Check the box for Device Admin under the Tier options.
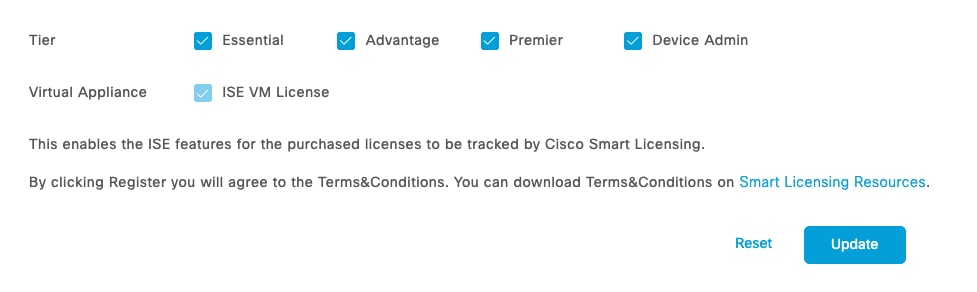 Device Admin
Device Admin
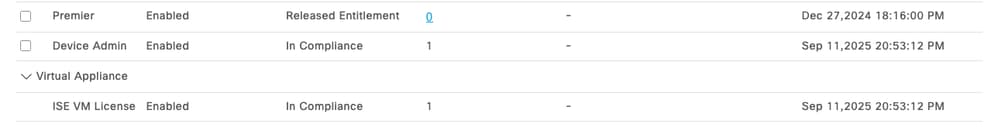 License Device Admin
License Device Admin
3. Enable the Device Admin Service on the ISE node that runs the TACACS+ service.
Administration > System > Deployment > Select the node
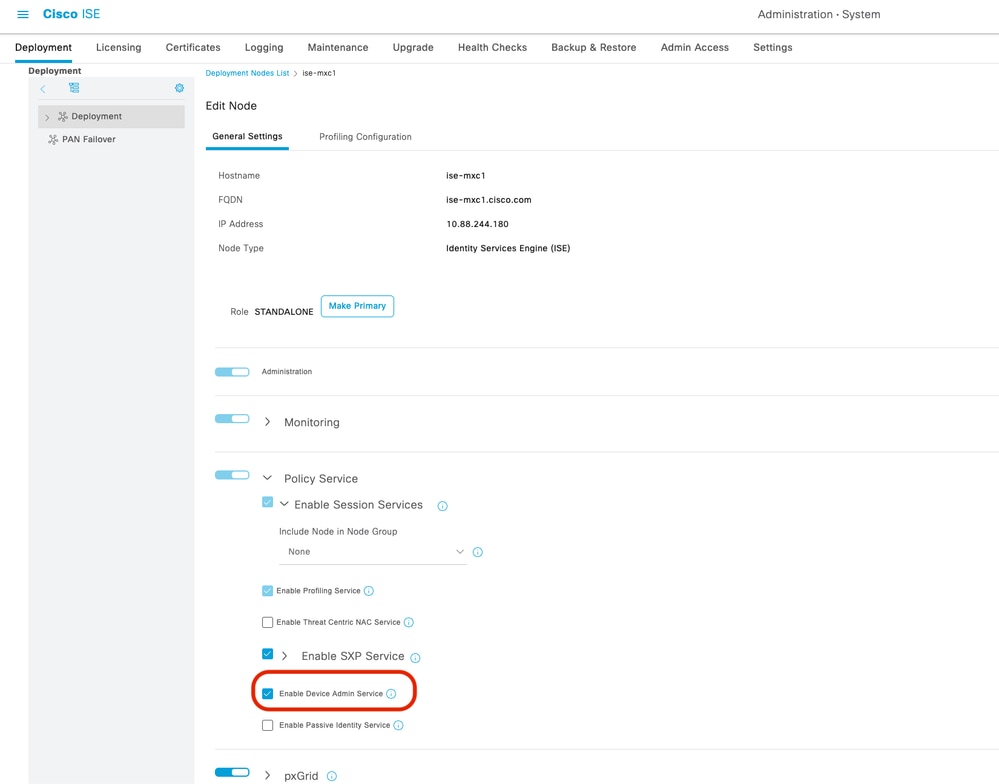 Enable Device Admin Service
Enable Device Admin Service
Create Admin User and Add Network Device
1. Create the Admin User.
Work Centers > Network Access > Identities > Network Access User
-
Add a new user (for example, catc-user).
-
If the user already exists, proceed to the next step.
2. Create the Network Device.
Work Centers > Network Access > Identities > Network Resource
-
Add the IP address of Catalyst Center, or define the subnet where the Catalyst Center IP is located.
-
If the device already exists, verify that it contains the parameters:
-
TACACS Authentication Settings are enabled.
-
The Shared Secret is configured and known (save this value, as it is required later in Catalyst Center).
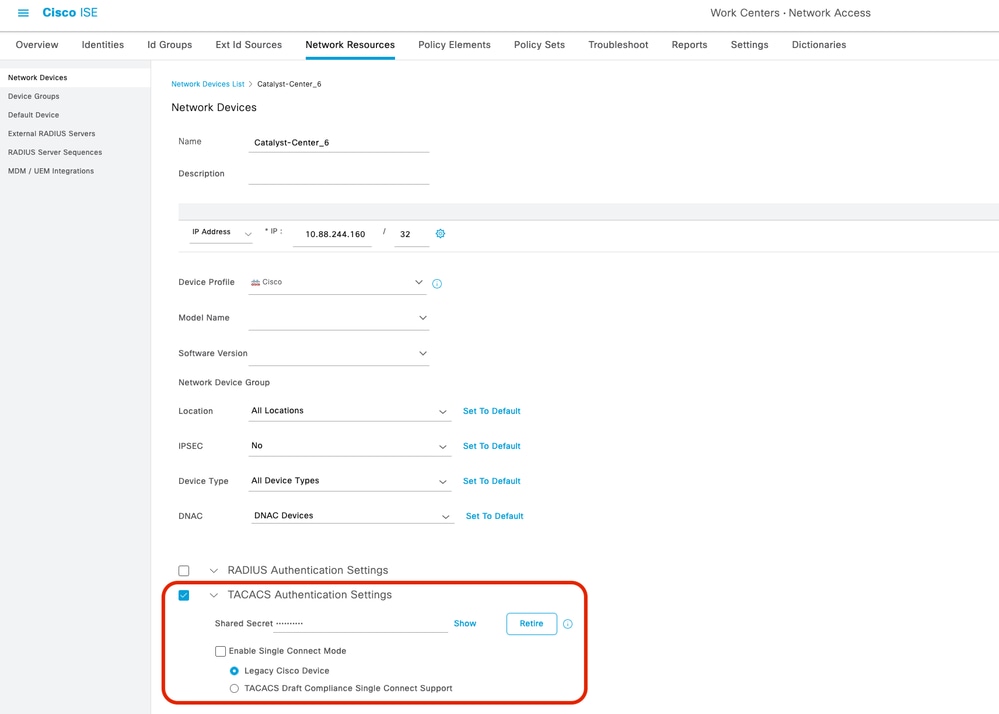 TACACS Authentication Settings
TACACS Authentication Settings
Configure TACACS+ Profile
1. Create a New TACACS+ Profile.
Work Centers > Device Administration > Policy Elements > Results > TACACS Profiles
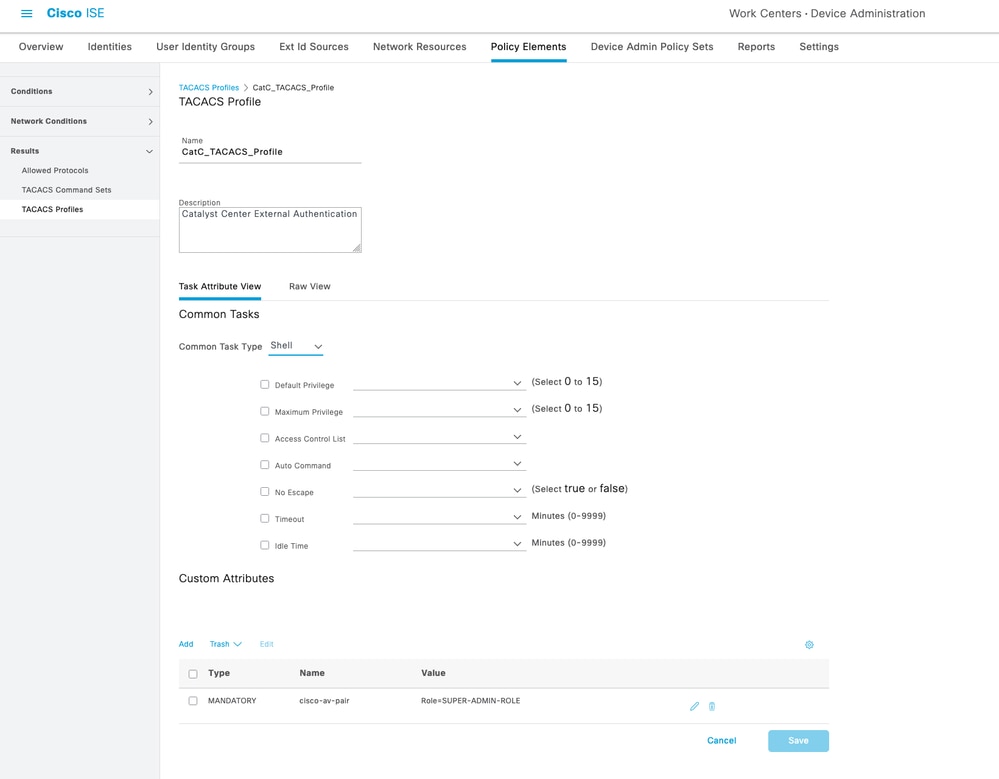 TACACS+ Profile
TACACS+ Profile

Note: Cisco Catalyst Center supports external Authentication, Authorization and Accounting (AAA) servers for access control. If you are using an external server for authentication and authorization of external users, you can enable external authentication in Cisco Catalyst Center. The default AAA attribute setting matches the default user profile attribute.
TACACS protocol default AAA attribute value is cisco-av-pair.
RADIUS protocol default AAA attribute value is Cisco-AVPair.
Change is only required if your AAA server has a custom attrribute in the user profile. On the AAA server, the format of the AAA attribute value is Role=role1. On the Cisco Identity Services Engine (Cisco ISE) server, while configuring RADIUS or TACACS profile, the user can select or input cisco av-pair as AAA attribute.
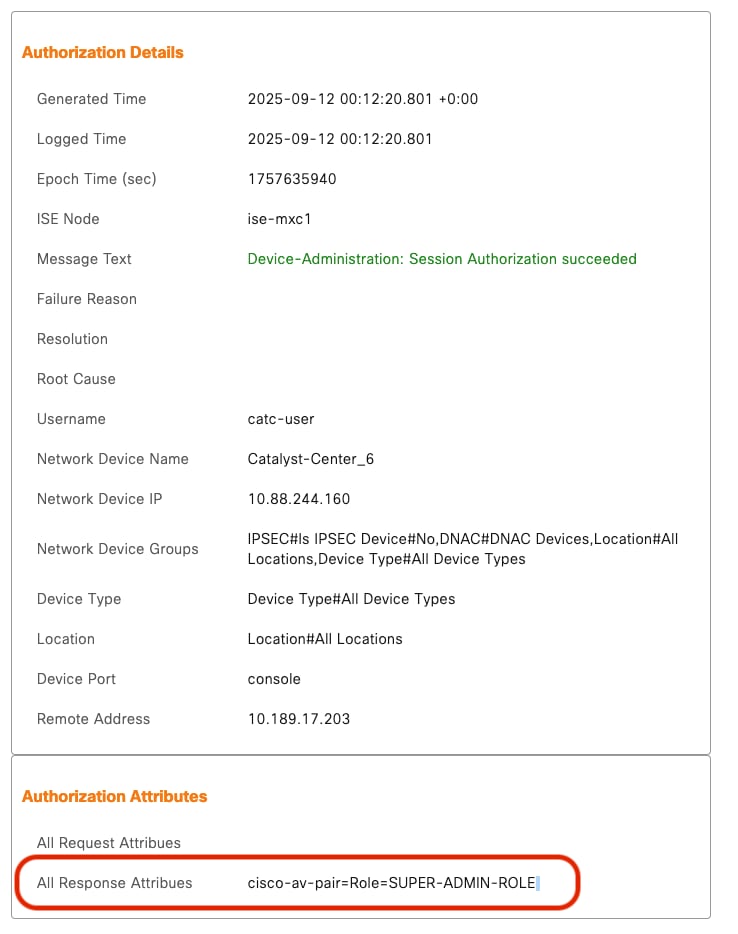
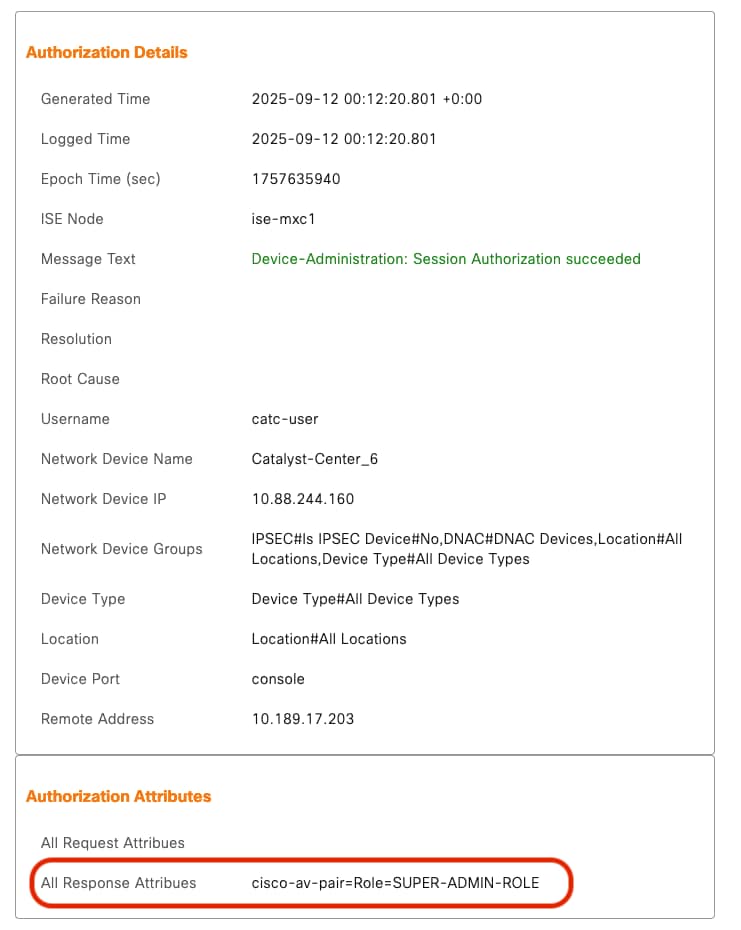
For example, you can manually select & configure the AAA attribute as cisco-av-pair=Role=SUPER-ADMIN-ROLE or Cisco-AVPair=Role=SUPER-ADMIN-ROLE.
2. Create a TACACS+ Command Set.
Work Centers > Device Administration > Policy Elements > Results > TACACS Command Sets
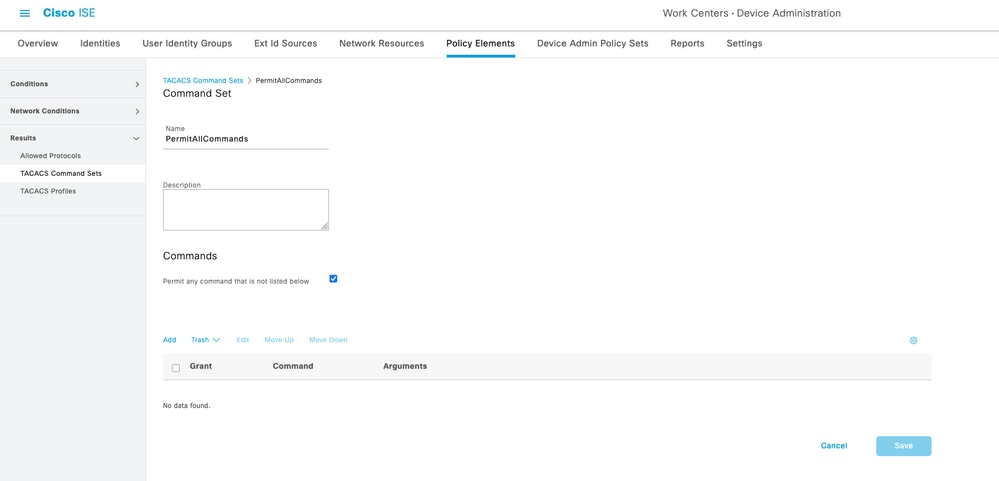 TACACS Command Sets
TACACS Command Sets
Configure TACACS+ Policies
1. Create a New TACACS+ Policy Set.
Work Centers > Device Administration > Device Admin Policy Set
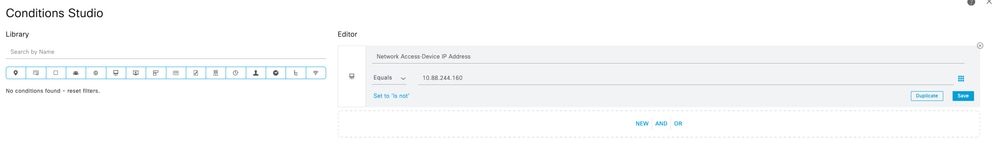 Catalyst Center IP address
Catalyst Center IP address
1.3 On the Allowed Protocols / Server Sequence Select Default Device Admin.
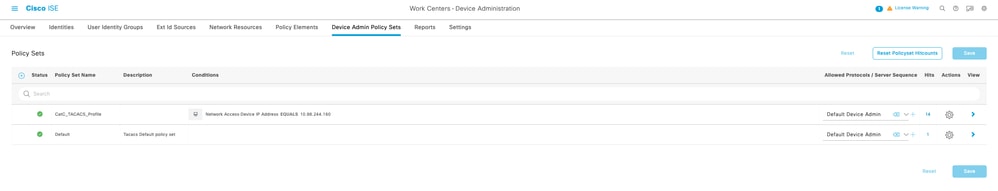 Select Default Device Admin
Select Default Device Admin
2. Configure the Policy Set.
-
Click the arrow ( > ) on the right to expand and configure the Policy Set.
-
Add a new Rule under Authorization Policy.
-
Configure the new rule as follows:
-
Name: Enter a descriptive rule name.
-
Condition: For this example, the condition matched All Device Types.
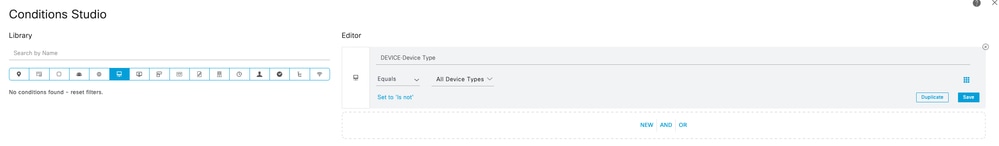 All Device Types
All Device Types
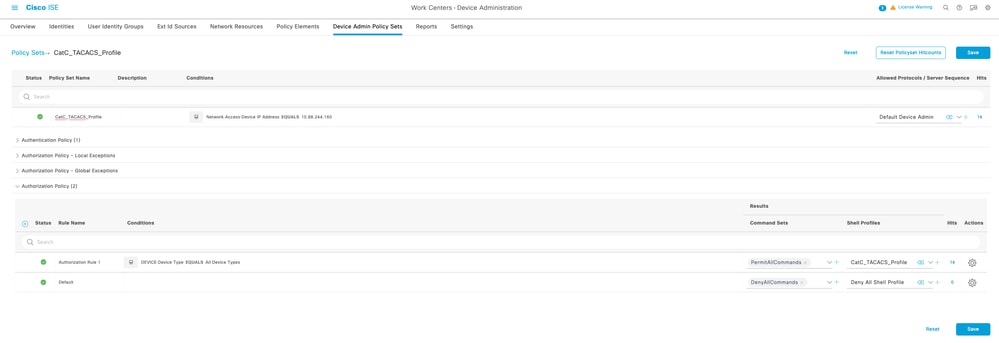 TACACS+ Command Set
TACACS+ Command Set
Cisco Catalyst Center
Configure the ISE / AAA Server
1. Log in to the Catalyst Center web interface.
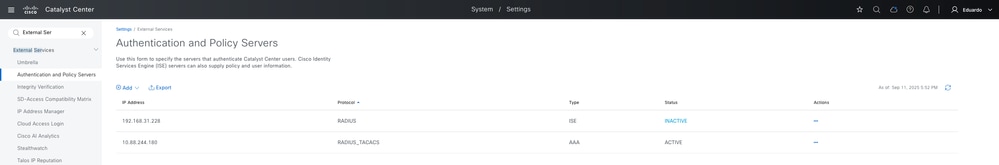
Main menu > System > Settings > External Services > Authentication and Policy Servers
2. Add a new server. You can select either ISE or AAA.
- For this demo, the AAA server option is used.

Note: A Catalyst Center cluster can have only one ISE cluster configured.
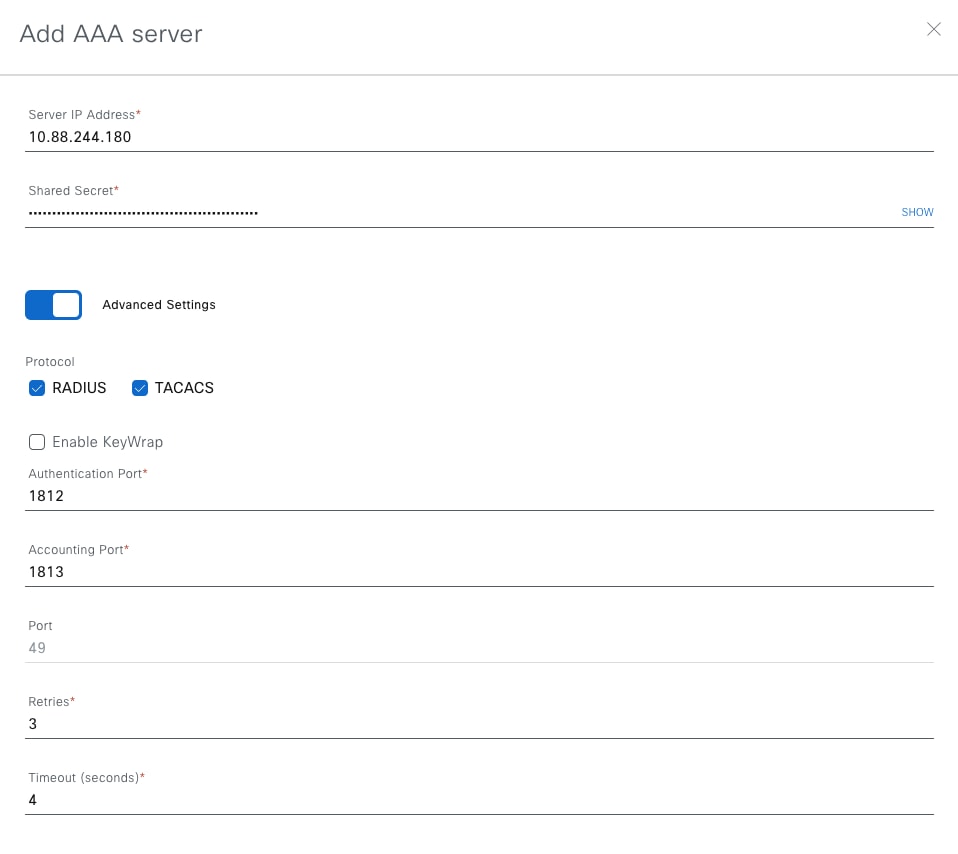
3. Configure these options and then save:
-
Enter the IP address of the AAA server.
-
Add the Shared Secret (the same secret configured in the Cisco ISE Network Resource).
-
Toggle Advanced Settings to On.
-
Check the TACACS option.
 Authentication and Policy Servers
Authentication and Policy Servers
 Advanced Settings
Advanced Settings
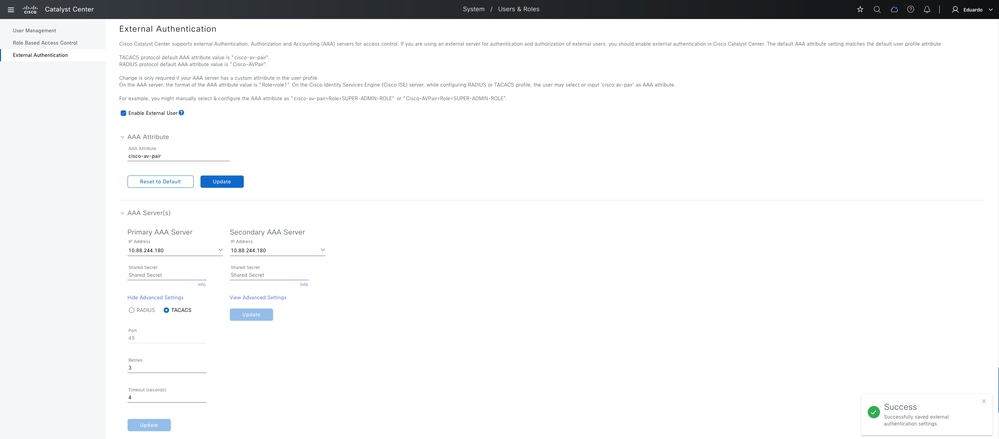
Enable and Configure the External Authentication.
1. Navigate to the External Authentication page:
Main menu > System > User & Role > External Authentication
2. Add the AAA attribute cisco-av-pair and click Update to save the changes.

Note: This step is not mandatory since the default attribute for TACACS+ is already cisco-av-pair, but it is considered a best practice to configure it explicitly.
3. Under Primary AAA Server, select the AAA server configured earlier.
-
Click View Advanced Settings to display additional options.
-
Select the TACACS+ option.
-
Enter the Shared Secret configured in Cisco ISE’s Network Resource.
-
Click Update to save the changes.
4. Enable the External User checkbox.
 External Authentication
External Authentication
Verify
-
Open a new browser session or use Incognito Mode and log in to the Catalyst Center web page with the user account configured in Cisco ISE.
-
From Catalyst Center, confirm that the login is successful.
 Log In Configure Catalyst Center External Authentication TACACS with ISE
Log In Configure Catalyst Center External Authentication TACACS with ISE
-
From Cisco ISE, validate the logs:
Operations > TACACS > Live Logs
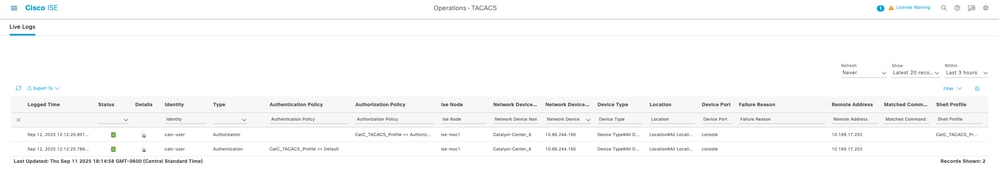 Live Logs
Live Logs
-
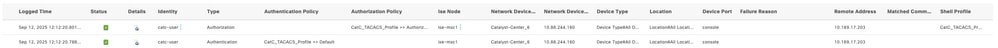
In the Authorization Details, compare with the next output :
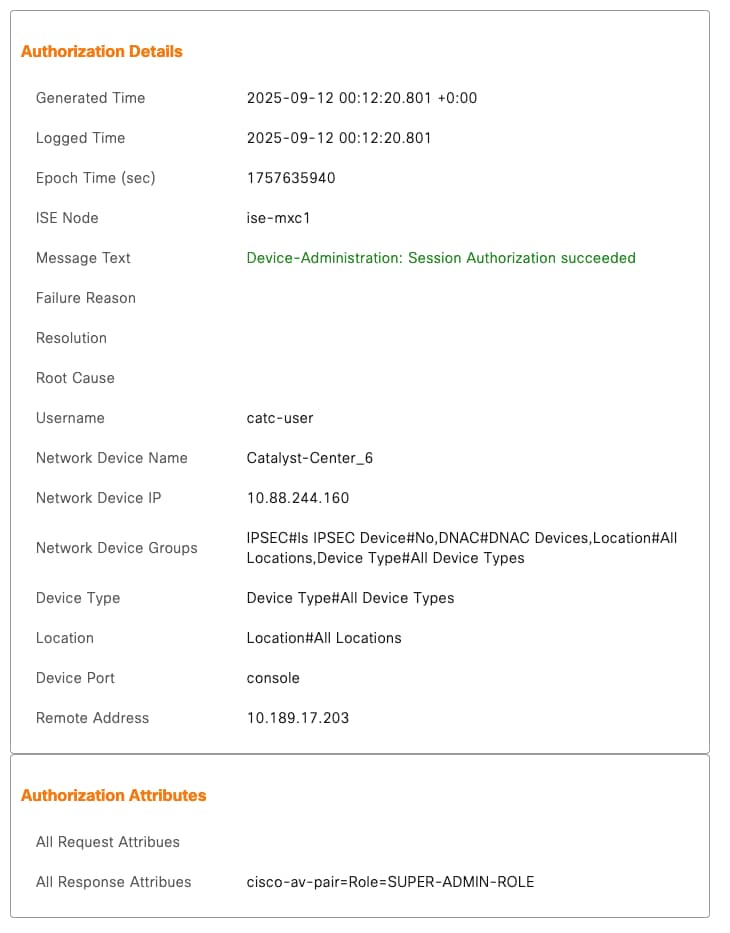 cisco-av-pair=Role=SUPER-ADMIN-ROLE
cisco-av-pair=Role=SUPER-ADMIN-ROLE
Troubleshoot
Here are some common issues you can encounter during the integration and how to identify them:
1. Attribute Misconfiguration
Symptom in Catalyst Center: Invalid login credentials
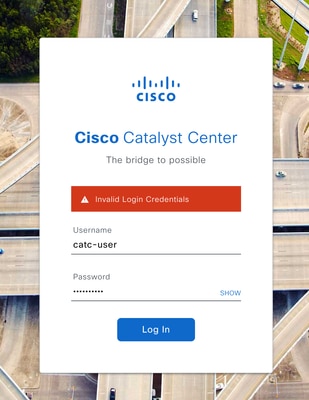 Attribute Misconfiguration
Attribute Misconfiguration
 Attribute Misconfiguration
Attribute Misconfiguration
Example:
 Attribute Misconfiguration
Attribute Misconfiguration
 Attribute Misconfiguration
Attribute Misconfiguration
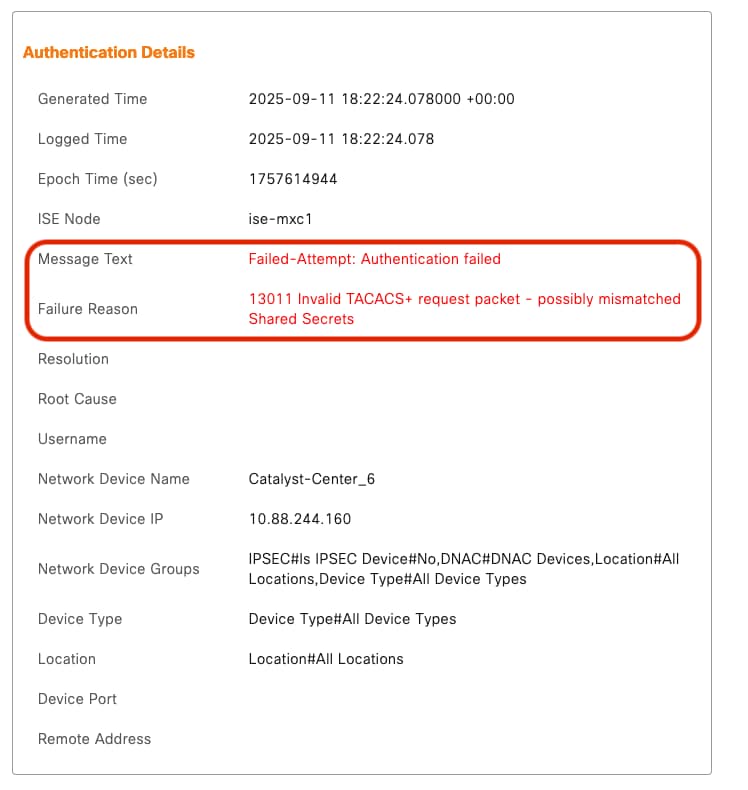
2. Shared Secret Mismatch
-
Symptom: Authentication packets fail between Catalyst Center and Cisco ISE.
-
Possible Cause: The Shared Secret configured in ISE's Network Resourcedoes not match the one configured in Catalyst Center > External Authentication page.
How to Verify:
Example:
 Shared Secret Mismatch
Shared Secret Mismatch























 Feedback
Feedback