XDR Buyer’s Guide
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Navigating the Extended Detection and Response market like a pro
Understanding Extended Detection and Response (XDR)
Why does the world need another security approach?
In today’s hybrid, multi-vendor, multi-vector landscape, complexity is the biggest challenge. Security teams must protect an ever-expanding ecosystem, running operations across dozens of tools with inconsistent integration. IoT and hybrid work have led to an expanded attack surface. Phishing, malware, and ransomware are doubling and even tripling year over year. At the same time, organizations are more hyper-connected than ever before. A security breach to one group can impact suppliers, partners, customers, and even whole sectors of the economy.
This new normal requires a new approach — the ability to protect the integrity of every aspect of the organization to withstand unpredictable threats or changes and emerge stronger.
What is the solution?
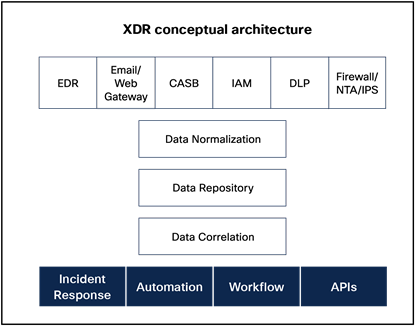
With threats becoming increasingly sophisticated, the old detection and response model, built upon self-contained point security solutions, doesn’t go far enough. This is where XDR comes in. XDR is a unified security incident detection and response tool that automatically collects and correlates telemetry from multiple security tools, applies analytics to detect malicious activity, then responds to and remediates threats. Effective XDR solutions are comprehensive, correlating data across all vectors — networks, cloud and SaaS applications, the web, endpoints, email, and cloud workloads — enabling visibility and context across your environment into even the most advanced threats.
Why XDR?
1. Allows teams to detect the most sophisticated threats with event correlation and multi-vendor detections across network, cloud, endpoint, email, and more.
2. Reduces alert fatigue by prioritizing threats based on impact, so teams know what to do first.
3. Elevates productivity with task automation and guided remediations to make more efficient use of SOC resources.
4. Allows organizations to enhance ROI by leveraging and corelating telemetry across the existing security stack, regardless of vendor or vector.
5 Key Elements of XDR Done Right
1. Provides prioritized and actionable telemetry, everywhere you need it
Can you efficiently sift through the sea of alerts to triage threats?
Breadth of visibility and depth of insight are foundational to XDR. Many sophisticated threats don’t just attack the endpoint, or the network alone – they attack across a variety of vectors, including email, endpoint, network, identity management, sandboxing and firewall. That’s why you need an XDR solution that correlates a broad range of telemetry and quality of data that can provide a holistic and complete view of what is happening across your environment.
But it’s not just about gathering insights — incident management is equally important. For XDR to have the impact it promises, these insights must be prioritized. An XDR solution that offers risk-based prioritization — ranking incidents by greatest material risk to your organization — will allow you to act on what truly matters, faster. It should also offer recommendations for next steps, so that you can make informed decisions on the best course of action.
| Key Functions and Capabilities |
Related Product Areas |
|
●
Efficacy and accuracy to minimize noise from false positives
●
Aggregate and correlate alerts across the environment
|
Endpoint Detection and Response (EDR) |
|
●
Continuous real-time network monitoring
|
Network Detection and Response (NDR) |
|
●
Advanced analytics that generate prioritized alerts with context when unknown malware and other sophisticated network attacks are detected
|
Extended Detection and Response (XDR) |
|
●
Continuous real-time email threat monitoring and automatic remediation prioritization
|
Email security |
Questions to ask vendors:
● How does your solution provide me with visibility across all my environments and deployed solutions (endpoints, devices, network)?
● How does your solution deliver insights? Does your solution provide prioritized telemetry?
● How does your solution prioritize threats based on impact and risk to my organization?
● What type of threat intelligence is feeding your detection? Where does that intelligence come from?
● How do you validate the data sources you use in your solution?
● How does this product handle sophisticated threats such as Wizard Spider, Volt Typhoon, and BlackTech?
2. Enables unified detection, regardless of vector or vendor
Does your XDR solution enable your existing security stack to work together as one coordinated unit, increasing your ROI?
Security teams today are dealing with an extraordinary level of complexity both in the security environment and an ecosystem of global supply chains, attackers, and defenders. As threats become more sophisticated, ensuring consistent detection across the environment has never been more critical. XDR solutions can help by aggregating, correlating, and prioritizing detections based on severity and potential impact. But in order to do this, your security stack needs to work in unison. By selecting an XDR solution that is open, extensible, and cloud-first, you’ll benefit from unified detection and event correlation across your environment. Each tool in your security stack has unique detection elements that become more powerful when brought together.
An effective XDR should encompass all six telemetry sources, including endpoint, network, firewall, email, identity, and DNS, to provide a comprehensive view of potential threats. Your XDR solution should easily integrate with your entire security stack with native backend to frontend integration, so coverage stays consistent even as vendors make portfolio changes. Finally, to optimize the threat detection capabilities of your security stack, it is worth exploring XDR solutions that can provide valuable local context and deliver accurate threat intelligence verdicts on which you can rely. All of which extends the value and improves the return on your security investments.
| Key Functions and Capabilities |
Related Product Areas |
|
●
Detect and block abnormal endpoint running program behavior, including exploit-based memory injection attacks
●
Determine Indicators of Compromise (IoCs) with MITRE ATT&CK mapping
●
Monitor file reputation to detect and isolate threats at the point of entry
●
Identify OS vulnerabilities in your environment, enabling administrators to prioritize remediation based on risk and reduce your attack surface
|
EDR, Vulnerability Management |
|
●
Use advanced analytics to quickly detect unknown malware, insider threats such as data exfiltration and policy violations, and other sophisticated attacks
●
Detect network attacks in real-time with high-fidelity alerts
|
XDR, NDR |
|
●
Detect and block unwanted email with reputation filtering
●
Identify and protect against deception–based email attacks such as social engineering, impostors
|
Email security |
Questions to ask vendors:
● How many of my existing investments can your XDR platform leverage?
● Is your XDR platform compatible with my solutions, regardless of vendor?
● Do your solutions have out-of-the-box integrations with one another?
● How are your detection technologies better than others that are on the market?
● What kind of threats does your solution help detect? Does it map alerts to the MITRE ATT&CK framework?
3. Supports fast, accurate threat response
Once identified, how fast can you confidently respond to threats?
Unifying insights from the network, endpoint, and email (to name a few) provides a more accurate understanding of what has happened, how it progressed, and what steps need to be taken in order to remediate the threat. Ideally, you should be able to view threat impact and scope from one location, taking actions with just a click or two. Effective XDR requires native response and remediation capabilities, such as isolating a host or deleting a malicious email out of all inboxes. XDR should also make it easy to create custom response actions with opportunities to automate so that teams can evolve their security as time goes on.
| Key Functions and Capabilities |
Related Product Areas |
|
●
Quickly respond to endpoint threats once compromised
|
EDR |
|
●
Identify and isolate the root cause of a network issue or incident within seconds
|
XDR, NDR |
|
●
Block malicious websites quickly with real-time click time analysis
|
Email security |
Questions to ask vendors:
● What response actions does the product provide?
● Can remediation be performed on the endpoint using an XDR solution in one location and scaled to others?
● How does the product integrate with existing security tools that enable response?
● How does your solution accelerate remediation?
● From threat alert to remediation, what’s the response time (ex: for a phishing attack)?
4. Offers a single investigative viewpoint for a streamlined user experience
Is your threat detection, response, and remediation managed from a single interface?
When evaluating XDR solutions, it’s important to take the security analyst experience into account. SecOps teams have enough to manage — there’s no need to slow them down with dozens of tools and a plethora of consoles. That’s why we recommend XDR solutions that are designed to help analysts detect and respond to threats more quickly and effectively by providing a unified view of security data across multiple security tools and data sources. This can help streamline workflows and reduce the time and effort required to investigate and remediate security incidents. XDR solutions should provide a full lifecycle dashboard covering every threat vector and access point. It should facilitate threat hunting through models such as MITRE ATT&CK that will make hypothesis-driven threat hunting accessible for those new to the process — and make it easier to anticipate what’s next. Another factor to consider is the impact of design on the analyst experience. It should elevate productivity and improve decision making times associated with the key functions of detection, investigation, and response. This in turn should enable less experienced analysts to perform advanced SecOps tasks by providing better context for alerts, along with progressive disclosure to provide only as much detail as is needed to quickly determine the scope and severity of a potential threat. And it should provide recommended and guided remediation so analysts at any level can confidently contain the threat.
| Key Functions and Capabilities |
Related Product Areas |
|
● Provides
a
full
lifecycle
dashboard
covering
every
threat
vector
and
access
point
● Delivers
a
unified
toolset
that
extends
across
SecOps,
NetOps,
and
ITOps
● Access
and
manage
data,
analytics,
and
automation
from
one unified
location
|
XDR |
Questions to ask vendors:
● How does your solution help improve the performance of my team in their threat hunting endeavors?
● How does the solution integrate with existing tools in my security stack?
● Can your XDR help me understand the potential impact of a threat, discover the scope of the breach, and take single-click actions from one interface?
● Does your solution provide support for role-based security by restricting all or portions of system/sub-system access to authorized groups and individual users?
● Can you centralize and analyze telemetry from all my existing security tools, regardless of vendor?
● Does your solution streamline incident response workflows to bring down the overall investigation timeline?
5. Provides opportunities to elevate productivity and strengthen security posture
Does your XDR solution increase threat detection and response efficiency, with less overhead, to improve ROI?
An important element of building your organization’s security resilience is automation and orchestration. Your security staff have important tasks to complete. When faced with a security threat, there’s no need for their time to be swallowed up following convoluted, manual, and repetitive workflows. XDR solutions that elevate productivity by automating critical workflows
● such as discovering an alert, correlating it, prioritizing and taking a response action quickly
● will free up your team across the full lifecycle.
An effective XDR solution should reduce the Mean Time to Respond (MTTR) by enabling an investigation that presents clear decisions and actions to allow analysts to respond in an automated and consistent way according to their policy and procedures. This means your SecOps teams can invest their time and energy towards more strategic and proactive tasks, further strengthening your security posture and improving the ROI of your existing security investments.
| Key Functions and Capabilities |
Related Product Areas |
|
●
Automatic endpoint threat hunting, including low prevalence threats
●
Enable administrators to write and scan for custom Indicators of Compromise (IoCs)
|
EDR |
|
●
Predictive network threat remediation enabled by behavioral analytics driven insights
|
XDR, NDR |
|
●
Automatically prioritize email threat remediation
|
Email security |
Questions to ask vendors:
● For third-party integrations, do vendors’ API changes break my automation scripts?
● How does your solution support monitoring to and from cloud-based workloads?
● Will I need to change environment or deploy new technology with the XDR solution?
● Does your XDR solution offer pre-built, out-of- the-box integrations with third-party security technology?
● Does your XDR solution reduce the analyst time needed to investigate and resolve an incident?
● Does your XDR solution inform your policy management to build resilience?
XDR is a crucial component of security resilience
Today, uncertainty is a guarantee. In response, organizations are investing in resilience across every aspect from finance to supply chains. But these will fall short without investment in security resilience — the ability to protect against threats and disruption, and to respond confidently so you can emerge even stronger.
XDR is a crucial component of embracing security resilience. Doing XDR right will increase your security posture by empowering security teams to prioritize threats by impact, detect threats sooner, and accelerate response. Automation and orchestration capabilities facilitate this process, freeing up security teams so they can focus on what matters most.

Security Operations Simplified with Cisco XDR
At Cisco, we have proactively invested in creating the most comprehensive security portfolio on the market, anticipating the security needs of the future, and integrating the components to make effective security simple and accessible for all teams, regardless of vendor or vector. We understand that building an XDR approach is a process, and we want your teams to break out of the vicious cycle of patchwork coverage from an industry supersaturated with point solutions. With Cisco XDR, we aim to create the shortest path from detection to response with the least friction.
Designed by security practitioners for security practitioners, Cisco XDR simplifies SecOps to help analysts remain proactive and resilient against the most sophisticated threats. Our solution is open, extensible, and cloud-first, allowing you to leverage existing security investments to enhance your ROI and gain unified security detection across your entire environment.
At Cisco, we take the responsibility of protecting customers’ assets seriously, as we are also customers of our customers. We want to partner with you in your security journey through the Cisco Security Cloud, an open security platform that helps you protect your entire ecosystem, no matter what comes next. Join us and experience the power of comprehensive security.
Ready to build the security operations of tomorrow, today?
Key XDR Elements and Capabilities
Use this table (pages 9-10) for quick reference during conversations with XDR vendors.
| Key Element |
Key Capabilities |
Aligned Cisco Products |
| Provides prioritized and actionable telemetry, everywhere you need it |
● Built-in EDR that can be completely managed, proactive threat hunting
● Integrated risk-based vulnerability management that enables quick vulnerability identification, risk scoring, prioritization, and remediation
|
Secure Endpoint |
|
● Continuous cloud activity analysis
● Advanced analytics including behavioral modeling and machine learning algorithms
● One view across your security infrastructure for unified visibility and aggregated, actionable intelligence
|
Cisco XDR |
|
|
● Advanced outbreak filters with real-time click time analysis
|
Secure Email |
|
| Enables unified detection, regardless of vector or vendor |
● Run-time detection and blocking of abnormal running program behavior
● Ability to make advanced OS queries on the endpoint in real time
● Built-in threat hunting that maps to the MITRE ATT&CK framework
|
Secure Endpoint |
|
● Detect attacks across the cloud in real-time with high-fidelity alerts enriched with context (including user, device, location, timestamp, and application)
● Detect and isolate threats with confirmed detections
● Detect rogue entities with NDR and automate quarantine with endpoints
● Detect internal hosts communicating to an external host
● Provides a complete audit trail of all cloud transactions for more effective forensic investigations
● Integrate with third-party solutions through built-in, pre-packaged, or custom integrations for a connected backend architecture and consistent frontend experience
● Built-in integrations with other technologies across cloud, endpoint, network and applications (including other third-party technologies)
|
Secure Network Analytics and Cisco XDR |
|
|
● Antispam, URL-related protection and control, high-performance virus scanning, outbreak filters, and reputation scanning for domain functionality
● Forged email detection that protects against BEC attacks targeting executives
● Automated malware analysis and sandboxing
|
Secure Email |
|
| Supports fast, accurate threat response |
● Access always-on protection with threat intelligence and insights pooled from dedicated global SOCs for broad customer base
|
All Cisco Security products |
|
● Continual monitoring of all endpoint activity, providing run-time detection and blocking of abnormal behavior
|
Secure Endpoint |
|
|
● Identify and isolate threats in encrypted traffic without compromising privacy and data integrity
● Trigger “response” workflows from one location
● Threat response that aggregates contextual awareness from security product data sources along with global threat intelligence from Talos® and third-party sources via APIs
● Create forensic incident investigation casebooks
|
Cisco XDR |
|
|
● Persistent protection against URL-based threats via real-time analysis of potentially malicious links
● Continuous leveraging of real-time Talos monitoring, analytics, and threat intelligence to identify unknown threats or sudden changes
|
Secure Email |
|
| Offers a single investigative viewpoint for a streamlined user experience |
● Gather and correlate global intelligence in a single view, enabling accelerated threat investigation
● Create custom response actions to reduce response time
● Automate enrichment from multiple data sources, overlayed with threat intelligence
|
Cisco XDR |
| Provides opportunities to elevate productivity and strengthen security posture |
● Automatic identification and threat analysis of low prevalence executables
● Ability to write custom IoCs to scan for post-compromise indicators across the entire endpoint deployment
|
Secure Endpoint |
|
● Behavioral modeling, multilayered machine learning, global threat intelligence
● Automatically classify new device roles as they are added to the network
● Integration with an XDR solution to enable automation across every threat vector and access point
|
Secure Network Analytics & Cisco XDR |
|
|
● Automatically trigger dynamic reputation analysis and provide visibility into where email malware originated, what systems were affected, and what the malware is doing
● Take action on both inbound and outbound email based on remediation insights
|
Secure Email |
|
|
● Automate routine tasks using prebuilt workflows that align to common use cases
● Share playbooks between SecOps teams
● Automated triage and prioritization of alerts from other security solutions
|
Cisco XDR |