Cisco UCS Manager PowerTool, Release 1.x User Guide
Available Languages
Table of Contents
Cisco UCS Manager PowerTool User Guide, Release 1.x
Windows PowerShell Requirements
Default UCS List with Multiple UCS
Register/Unregister Cisco UCS Central
Generating Cmdlets From UCS Manager GUI Actions
Blade Power & Temperature Statistics
Managed Object Synchronization
Monitoring UCS Managed Object Transitions
Server Pool Policy Qualifications
Dynamic vNIC connection Policy
Remote Authentication – RADIUS
Remote Authentication – TACACS
Communication Services - Telnet
Communication Services - CIM XML
Communication Services - HTTPS
Generic Managed Object Queries
Generic Managed Object Cmdlets
XtraProperty in Get/Add/Set cmdlets
Configure Scalability Port in UCS 6324 Fabric Interconnect
Compare-UcsManagedObject - Dn Translation
Compare-UcsManagedObject – GetPropertyDiff()
Add Cmdlet –ModifyPresent Flag
Cisco UCS Manager PowerTool User Guide, Release 1.x
Overview
Cisco UCS Manager PowerTool is a PowerShell module which helps automate all aspects of Cisco UCS Manager including server, network, storage and hypervisor management. PowerTool enables easy integration with existing IT management processes and tools.
The PowerTool cmdlets work on the UCS Manager’s Management Information Tree (MIT), performing create, modify or delete actions on the Managed Objects (MO) in the tree. The next chapter provides an overview of the Cisco UCS Management Information Model (MIM) and relation of PowerTool cmdlets with it.
One of the easiest ways to learn UCS configuration through PowerTool is to generate PowerTool cmdlets, for configuration actions performed with the GUI, using the ConvertTo-UcsCmdlet described in “PowerTool Cmdlet Generation” section section.
Management Information Model
All the physical and logical components that comprise a Cisco UCS domain are represented in a hierarchical Management Information Model (MIM), referred to as the Management Information Tree (MIT). Each node in the tree represents a Managed Object (MO), uniquely identified by its Distinguished Name (DN). Figure 1 illustrates the MIM.
Figure 1 Management Information Model

The following illustration shows a sample (partial) MIT for three chassis.
Managed Objects
Managed Objects (MO) are abstractions of Cisco UCS domain resources, such as fabric interconnects, chassis, blades, and rack-mounted servers. Managed Objects represent any physical or logical entity that is configured / managed in the Cisco UCS MIT. For example, physical entities such as Servers, Chassis, I/O cards, Processors and logical entities such as resource pools, user roles, service profiles, and policies are represented as managed objects.

Every managed object is uniquely identified in the tree with its Distinguished Name (Dn) and can be uniquely identified within the context of its parent with its Relative Name (Rn). The Dn identifies the place of the MO in the MIT. A Dn is a concatenation of all the relative names starting from the root to the MO itself. Essentially, Dn = [Rn]/[Rn]/[Rn]/…/[Rn].
In the example below, Dn provides a fully qualified name for adaptor-1 in the model.
The above written Dn is composed of the following Rn:
A Relative Name (Rn) may have the value of one or more of the MO’s properties embedded in it. This allows in differentiating multiple MOs of the same type within the context of the parent. Any properties that form part of the Rn as described earlier are referred to as Naming properties.
For instance, multiple blade MOs reside under a chassis MO. The blade MO contains the blade identifier as part of its Rn (blade-[Id]), thereby uniquely identifying each blade MO in the context of a chassis.
References to Managed Objects
The contents of the managed objects are referred to during the operation of Cisco UCS. Some of the MOs are referred to implicitly (PreLoginBanner during login) or as part of deployment of another MO (The Service Profile MO may refer to a template or a VNIC refers to a number of VLAN MOs).
The different types of references can be classified as shown below:
Figure 3 References to Managed Objects

A singleton MO type is found at most once in the entire MIT and is typically referred to implicitly.
Non-Singleton MO type may be instantiated one or more times in the MIT. In many cases, when an MO refers to another, the reference is made by name. Depending on the type of the referenced MO, the resolution may be hierarchical. For instance, a service profile template is defined under an org. Since an org may contain sub-orgs, a sub org may have a service profile template defined with the same name. Now, when a service profile instance refers to a service profile template (by name), the name is looked up hierarchically from the org of the service profile instance up until the root org. The first match is used. If no match is found, the name “default” is looked up in the similar way and the first such match is used.
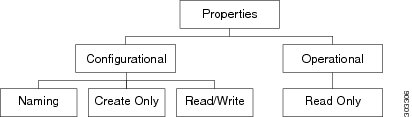
Properties of Managed Objects
Properties of Managed Objects may be classified as Configuration or Operational.
Configuration properties may be classified as:
- Naming properties: Form part of the Rn. Needs to be specified only during MO creation and cannot be modified later.
- Create-Only properties: May be specified only during MO creation and cannot be modified later. If the property is not specified, a default value is assumed.
- Read / Write properties: May be specified during MO creation and can also be modified subsequently.
Operational properties indicate the current status of the MO / system and are hence read-only.
Figure 4 Properties of Managed Objects
The table below lists the examples of the various property types.
Methods
Methods are Cisco UCS XML APIs used to manage and monitor the system. There are methods supported for:
- Authentication
- AaaLogin
- AaaRefresh
- AaaLogout
- Configuration
- ConfigConfMo(s)
- LsClone
- LsInstantiate*
- FaultAckFaults
- Query
- ConfigResolveDn(s)
- ConfigResolveClass(es)
- ConfigResolveChildren
- Event Monitor
- EventSubscribe
The class query methods (ConfigResolveClass(es), ConfigResolveChildren) allow a filter to be specified so that a specific set of MOs are matched and returned by the method.
- Property Filters:
- Composite Filters (Acts on sub-filters)
PowerTool Mapping
All but about 30 of the PowerTool cmdlets are generated from the MO specification. A convenient noun is used in place of the type (ServiceProfile instead of LsServer etc.). Get, Add, Set, Remove cmdlets or a subset is generated for the various MO types. All cmdlets support the Xml parameter, which dumps the Xml request and response on the screen.
Add Cmdlet —Uses the ConfigConfMo(s) method with MO status “created” along with the specified property values. If the ModifyPresent parameter is specified, status “created, modified” is specified instead. If the Force parameter is specified, there will be no prompt for confirmation.
Get Cmdlet —Use the ConfigResolveClass method to retrieve MOs. If any property parameters are specified, they are used to generate “eq” filters. If multiple property parameters are specified, the multiple “eq” filters are combined with a “and” filter.
Set Cmdlet —Uses the ConfigConfMo(s) method with MO status “modified” along with the specified property values. If the Force parameter is specified, there will be no prompt for confirmation.
Remove Cmdlet —Uses the ConfigConfMo(s) method with MO status “deleted”. If the Force parameter is specified, there will be no prompt for confirmation.
The table below lists the properties that can be specified for a given Verb:
The table below lists the types that can come down the pipeline for corresponding cmdlets:
The table below lists the methods invoked to generate the required XML requests:
Add-Ucs1 |
|
Get-UcsCmdletMeta is useful cmdlet to explore the MO types, the corresponding nouns, supported Verbs, properties of the MOs, the details of properties including the type (Naming, Read/Write etc.) and the version of UCS Manager the property was introduced in etc.
System Requirements
Before installing Cisco UCS Manager PowerTool, ensure that the system meets the following requirements:
Installation
Before installing Cisco UCS Manager PowerTool, you must do the following:
- Close any instances of PowerShell running with the PowerTool module loaded.
- Uninstall all versions of Cisco UCS Power Tool that are older than Cisco UCS Manager PowerTool, Release 0.9.1.0.
Installation
Step 1![]() Download and launch the installer.
Download and launch the installer.
Step 2![]() (Optional) Select Create Shortcut to add a shortcut on the desktop.
(Optional) Select Create Shortcut to add a shortcut on the desktop.
Getting Started
Step 1![]() Launch Cisco UCS Manager PowerTool from the desktop shortcut.
Launch Cisco UCS Manager PowerTool from the desktop shortcut.
Step 2![]() View all cmdlets, functions, and aliases supported by the Cisco UCS Manager PowerTool.
View all cmdlets, functions, and aliases supported by the Cisco UCS Manager PowerTool.
Step 3![]() Connect to a Cisco UCS domain.
Connect to a Cisco UCS domain.

Note![]() After logging on, by default, the Cisco UCS handle is added to the default Cisco UCS domain list, unless the
After logging on, by default, the Cisco UCS handle is added to the default Cisco UCS domain list, unless the -NotDefault option is specified. Every cmdlet that operates on a Cisco UCS domain takes the –Ucs parameter, where the handle can be specified.
Step 4![]() Connect to a Cisco UCS domain using a proxy.
Connect to a Cisco UCS domain using a proxy.
Step 5![]() Use the following cmdlets:
Use the following cmdlets:
a.![]() Get Cisco UCS domains consolidated status information.
Get Cisco UCS domains consolidated status information.
c.![]() Get list of service profile Instances.
Get list of service profile Instances.
Get-UcsServiceProfile -Ucs $handle –Type instance
Default UCS
If no handle or name is specified, the Cisco UCS domain handle is added to a DefaultUcs domain list unless the –Ucs parameter is specified, the first cmdlet in the pipeline operates on the default Ucs list.
Get UCS’s consolidated status information.
Get the set of all chassis objects.
Get the object pertaining to chassis 1.
Default UCS List with Multiple UCS
PowerTool cmdlets can work with multiple Cisco UCS domains by specifying multiple handles.
Connect to a Cisco UCS domain.
By default, multiple Cisco UCS handles are not allowed in DefaultUcs. This can be overridden using the Set-UcsPowerToolConfiguration cmdlet.
Connect to multiple Cisco UCS domains using the same login credentials.
Credentials to/from File
Credentials can be stored to a file. The stored credentials are encrypted with a specified Key.
Login can be initiated from credentials stored in a file.
Specify proxy while logging in with credentials stored in a file.
Login to an additional system and add the credentials to the file.
SSL Handling
When a user connects to a Cisco UCS server and the server cannot recognize any valid certificates; connection establishment depends on InvalidCertificateAction.InvalidCertificateAction is set to Ignore by default. By default PowerTool is configured to establish the connection without taking into account if the certificate is invalid.
You can override this using the Set-UcsPowerToolConfiguration cmdlet.
Register/Unregister Cisco UCS Central
If you want to have Cisco UCS Central manage a Cisco UCS domain, you need to register that domain. When you register, you need to choose the types of policies and other configurations, such as backups and firmware, that will be managed by Cisco UCS Central and which will be managed by Cisco UCS Manager.
Before you register a Cisco UCS domain with Cisco UCS Central, do the following:
Step 1![]() Configure an NTP server and the correct time zone in both Cisco UCS Manager and Cisco UCS Central to ensure that they are in sync. If the time and date in the Cisco UCS domain and Cisco UCS Central are out of sync, the registration may fail.
Configure an NTP server and the correct time zone in both Cisco UCS Manager and Cisco UCS Central to ensure that they are in sync. If the time and date in the Cisco UCS domain and Cisco UCS Central are out of sync, the registration may fail.
Step 2![]() Obtain the hostname or IP address of Cisco UCS Central
Obtain the hostname or IP address of Cisco UCS Central
Step 3![]() Obtain the shared secret that you configured when you deployed Cisco UCS Central
Obtain the shared secret that you configured when you deployed Cisco UCS Central
Examples
The examples in this section show how to execute the cmdlets. This following examples are included in this section:
- PowerTool Cmdlet Generation
- Get UCS Server
- Org
- Faults
- Get Cmdlet -Hierarchy Flag
- Get Cmdlet –LimitScope Flag
- Transaction Support
- VLANs (Creation & Deletion)
- MAC Pools & Blocks
- Server Pools
- UUID Suffix Pools & Blocks
- WWNN Pools & Blocks
- WWPN Pools & Blocks
- IQN Suffix Pools & Blocks
- Port Roles
- Port Channel
- VLANs (Assignment)
- Blade Power & Temperature Statistics
- Configuration Backup
- Import Configuration
- Managed Object Synchronization
- Monitoring UCS Managed Object Transitions
- Tech Support
- Service Profile
- Service Profile Components
- Service Profile Association
- Filters
- iSCSI Boot
- vNIC Template
- vHBA Template
- Boot Policy
- Adapter Policy
- BIOS Policy
- Host Firmware Package
- IPMI Access Profile
- Management Firmware Package
- Power Control Policy
- Server Pool Policy QualificationsDynamic vNIC connection Policy
- Network Control Policy
- Privileges
- User Roles
- Locales
- User Accounts
- Remote Authentication – RADIUS
- Remote Authentication – TACACS
- Remote Authentication – LDAP
- RADIUS Provider
- TACACS Provider
- LDAP Provider
- Authentication Domains
- Communication Services
- Communication Services - Telnet
- Communication Services - CIM XML
- Communication Services - SNMP
- Communication Services – HTTP
- Communication Services - HTTPS
- Generic Managed Object Queries
- Generic Managed Object Cmdlets
- Generic Cmdlet –XmlTag
- XtraProperty in Get/Add/Set cmdlets
- CCO Integration
- Upload Firmware
- Export to XML
- Import from XML
- KVM
- Launch the UCSM GUI
- Configure Scalability Port in UCS 6324 Fabric Interconnect
- UCS Statistics
- Transaction Impact
- Cmdlet Meta Information
- Compare-UcsManagedObject - Dn Translation
- Compare-UcsManagedObject – GetPropertyDiff()
- Add Cmdlet –ModifyPresent Flag
- Capability Catalog Update
- Server Operations
PowerTool Cmdlet Generation
Generate cmdlets for the specified actions in UCS GUI.
Get xml request along with generated cmdlets.
Generate cmdlets for action in the specified GUI log.
Generate cmdlets for the specified xml request.
Generate cmdlets for the specified xml requests in file.
Generate cmdlets for the specified MO
From the version 1.2(1), you can pipe a manage object to the ConvertTo-UcsCmdlet, and get the cmdlets required to create the managed object.
Generating Cmdlets From UCS Manager GUI Actions
You can generate cmdlets for the actions performed on the UCS Manager GUI using the ConvertTo-UcsCmdlet cmdlet.
The Cisco UCS Manager GUI considers a few XML snippets as secure and does not log them. So, the ConvertTo-UcsCmdlet does not find the logs to do the translation.
To log the xml snippets of all the user actions in the GUI, launch the UCSM GUI by using one of the following ways:
- Using Start-UcsGuiSession -LogAllXml cmdlet
- Manually launch the UCS Manager GUI by performing the following steps:
Step 1![]() Save the launch link in.jnlp file format. For example, https://<ip_or_hostname>/ucsm/ucsm.jnlp.
Save the launch link in.jnlp file format. For example, https://<ip_or_hostname>/ucsm/ucsm.jnlp.
Step 2![]() Right-click the file and open the file with Notepad.
Right-click the file and open the file with Notepad.
Step 3![]() Add the following line after the other property definitions:
Add the following line after the other property definitions:
Step 4![]() Save and close the file.
Save and close the file.
Step 5![]() Right-click the file and open with Java™ Web Start Launcher.
Right-click the file and open with Java™ Web Start Launcher.
After the UCS Manager GUI is launched, from a PowerShell window with the CiscoUCS module loaded, run the ConvertTo-UcsCmdlet cmdlet.
Get UCS Server
From Release 1.4.1, use the new cmdlet Get-UcsServer to get all the servers regardless of the form factor.
Org
Get a list of orgs across Cisco UCS domains, in the Default UCS list.
Get Cmdlet –LimitScope Flag
Get service profile at the root level without descending into org root children.
Get service profile from org Finance without descending into org Finance children.
VLANs (Creation & Deletion)
VLANs in Cisco UCS domains are referred to by name and VLAN definitions can be created under four nodes in the MIT.
Create a VLAN under the Global LAN Cloud.
Create a VLAN under Fabric A LAN Cloud.
Create a VLAN under Fabric B LAN Cloud.
Create a VLAN under the Global Appliance Cloud.
Create a VLAN under the Fabric A Appliance Cloud.
Create a VLAN under the Fabric B Appliance Cloud.
Import a list of VLANs from a csv file and create the VLANs under the LAN cloud. (This example creates the csv file as well.)
MAC Pools & Blocks
Add a MAC Block to the default MAC Pool.
Check for any clashes in MAC Pool assignments across all Cisco UCS domains in default list.
WWPN Pools & Blocks
Add a WWN block to the WWPN pool.
Port Roles
Make Fabric A’s Slot 1 (Fixed Ports Slot) Port 19 a server port.
Unconfigure Fabric A’s Slot 1 (Fixed Ports Slot) Port 19 from being a server port.
Make Fabric A’s Slot 1 (Fixed Ports Slot) Port 15 an appliance port.
Unconfigure Fabric A’s Slot 1 (Fixed Ports Slot) Port 15 from being an appliance port.
Make Fabric A’s Slot 1 (Fixed Ports Slot) Port 16 an uplink port.
Unconfigure Fabric A’s Slot 1 (Fixed Ports Slot) Port 16 from being an uplink port.
Port Channel
Create an Appliance Port Channel on Fabric A with ports 19 & 20.
Add Port Channel to the Appliance VLAN.
VLANs (Assignment)
Configuration Backup
Remove any previously stored backups in UCS.
The PathPattern can be auto-filled, allowing the cmdlet to be used with multiple Cisco UCS domains. Create and download full-state system backup of UCS. This creates a binary file that includes a snapshot of the entire system. You can use the file generated from this backup to restore the system during disaster recovery. This file can restore or rebuild the configuration on the original fabric interconnect, or recreate the configuration on a different fabric interconnect. You cannot use this file for an import.
Create and download logical backup of UCS. This creates an XML file that includes all logical configuration settings such as service profiles, VLANs, VSANs, pools, and policies. You can use the file generated from this backup to import these configuration settings to the original fabric interconnect or to a different fabric interconnect. You cannot use this file for a system restore.
Create and download system backup of UCS. This creates an XML file that includes all system configuration settings such as usernames, roles, and locales. You can use the file generated from this backup to import these configuration settings to the original fabric interconnect or to a different fabric interconnect. You cannot use this file for a system restore.
Create and download config-all backup of UCS. This creates an XML file that includes all system and logical configuration settings. You can use the file generated from this backup to import these configuration settings to the original fabric interconnect or to a different fabric interconnect. You cannot use this file for a system restore. This file does not include passwords for locally authenticated users.
Import Configuration
The import function is available for all configuration, system configuration, and logical configuration files. You can perform an import while the system is up and running.
Import all configuration xml (An XML file that includes all system and logical configuration settings. The current configuration information is replaced with the information in the imported configuration file one object at a time.
Import all configuration xml. The information in the imported configuration file is #compared with the existing configuration information. If there are conflicts, the import operation overwrites the information on the Cisco UCS domain with the information in the import configuration file.
Managed Object Synchronization
Sync a set of MOs from SYSA to SYSB.
Sync a set of MOs from SYSA to all systems in the default list.
Monitoring UCS Managed Object Transitions
Watch Cisco UCS domains for all events for 60 seconds.
Watch Cisco UCS domains for any changes in faults for 60 seconds.
Watch UCS for a particular field in MO to attain a success value.
Tech Support
Technical support data for the entire UCSM instance will be created and downloaded to the specified file.
Technical support data for the UCSM management services(excluding fabric interconnects) will be created and downloaded to the specified file.
Technical support data for Chassis id 1 and Cimc id 1 will be created and downloaded to specified file.
Technical support data for Chassis id 1 and Iom id 1 will be created and downloaded to specified file.
Technical support data for RackServer id 1 and RackAdapter id 1 will be created and downloaded to specified file.
Technical support data for FEX id 1 will be created and downloaded to specified file.
Service Profile
Get all service profile instances in UCS.
Get all service profile updating templates in UCS.
Get all service profile initial templates in UCS.
Add a new service profile sp_name from service profile template sp_template
Get power state of a service profile.
Service Profile Components
Create a vNIC with reference to QoS Policy.
Add a VLAN for vNIC, make it Native VLAN.
Service Profile Association
Associate a service profile to a blade.
Associate service profile to a rack.
Associate service profile to a server pool.
Associate a service profile to a server pool along with server pool qualification policy.
Disassociate a service profile.
Filters
#Get all Service Profile Templates.
Get all Service Profiles with Name containing string ‘SJC’.
Get all Service Profiles with Name beginning with string ‘SJC’.
Get all VLANs with Id between 8 and 50.
Get all Roles that have the fault privilege.
Get all Roles that have the fault or operations privilege.
Get all Roles that have the fault and operations privilege.
Get a list of blades/rack units with temperature greater than 45.
Get a list of faults generated between 4/18/2012 9:00 and 4/19/2012 9:30.
Get Service Profiles with Name equals ‘SJC’.
Get all Service Profiles with Name equals ‘SJC/sjc/SjC’ etc.
Get all Service Profiles with Name beginning with string ‘SJC/sjc/SjC’ etc.
Get all Service Profiles with Name except ‘SJC/sjc/SjC’ etc.
iSCSI Boot
Add a static IP þ(not related to iSCSI boot).
Create the required vNIC and add VLAN.
Create iSCSI vNIC and map it to the vNIC created above.
Add iSCSI Initiator Parameters – VLAN and IP address.
Create a specific boot policy.
If installation is required, create a LsbootVirtualMedia.
vNIC Template
Create an Initial vNIC template.
Create an Updating vNIC template.
Add a VLAN to an Initial vNIC template.
Add a VLAN to an Initial vNIC template and make it Native VLAN.
Set MAC Pool, Network Control policy and QoS policy for Initial vNIC template.
vHBA Template
Create an Initial vHBA template.
Create an Updating vHBA template.
Add a VSAN to Updating vHBA template.
Set WWN Pool, QoS policy, Pin Group and Stats policy for Updating vHBA template.
Boot Policy
Create a Boot policy and enable Reboot on boot order change and enforce vNIC/vHBA/iSCSI name.
Adapter Policy
Add a custom Eth Adapter policy, that disables receive checksum offload.
Enable FCP error recovery for Fibre Channel Adapter policy.
Enable TCP timestamp, HBA mode and Boot to target for iSCSI Adapter policy.
BIOS Policy
Create a Bios policy and enable reboot on Bios setting change.
Modify USB system idle power optimizing setting to high-performance.
Enable Virtulization technology.
Enable quite boot for Bios policy.
Host Firmware Package
Create a Host Firmware package and set IgnoreCompCheck to No.
Add a Host Firmware pack item.
Management Firmware Package
Create a Management Firmware package and set IgnoreCompCheck to no.
Add a Management Firmware pack item.
Power Control Policy
Create a Power Control policy. Priority is ranked on a scale of 1-10, where 1 indicates the highest priority and 10 indicates lowest priority. The default priority is 5.
Server Pool Policy Qualifications
Create a Server Pool policy qualification.
Create an Adaptor qualification.
Create a Memory qualification policy with memory clock speed of 1067Mhz and 16 memory units.
Create a CPU/Cores qualification policy with Pentium_4 processor architecture
Create a Diskless Storage qualification policy for servers without a local disk (SAN only configuration).
Dynamic vNIC connection Policy
Create a Dynamic vNIC connection policy dy_vnic_conn with 54 dynamic vNICs and protection enabled for failover mode.
Network Control Policy
Create a Network Control policy network_policy with CDP enabled and VIF configured to change the operational state of a vNIC to down when uplink connectivity is lost on the fabric interconnect.
Set Mac security for Network Control policy to allow forged MAC addresses.
Set Mac security for Network Control policy so that after the first packet has been sent to the fabric interconnect, all other packets must use the same MAC address or they will be silently rejected by the fabric interconnect. This enables port security for the associated vNIC.
User Roles
Add a user role “test_role” with admin privileges.
Change privileges for a user role to allow read-and-write access to fabric interconnect infrastructure, network security operations and read access to the rest of the system.
Remote Authentication – RADIUS
Set global configuration for RADIUS authentication.
Create a RADIUS server instance with server key “test1234” and maximum 2 retries.
Remote Authentication – LDAP
RADIUS Provider
Create a RADIUS server instance with server key “test1234” and maximum 2 retries.
Add a RADIUS provider group and set it as the default remote authentication.
LDAP Provider
Add an LDAP provider group and set it as the default remote authentication.
Authentication Domains
Authentication Domains configure simultaneous support for different authentication methods (local, TACACS+, RADIUS, and LDAP/Active Directory) and provider groups.
Configure a TACAS Provider Group with a TACACS Provider.
Create an Authentication Domain and add a reference to the TACACS Provider group.
Now if a user logs in from the console, GUI or XML API with the user name being “ucs-adtacacs\user” the TACACS configuration created above will be used for authentication.
Communication Services
Get UCS Web Session Limits, which define the maximum number of concurrent web sessions (both GUI and xml) permitted access to the system at any one time.
Set Web Session Limit for the user to 30 and an overall session limit of 255.
Communication Services - SNMP
Enable SNMP with community string being “public”, system contact person being “CiscoSystems” and location of the host being “Bangalore”.
Communication Services – HTTP
Set UCS http configuration to enable http and enable http to https redirection.
Communication Services - HTTPS
Create a keyring with a key size of 1024 bits.
Create a certificate request passing the required subject name(hostname of the machine).
Get the certificate for the generated certificate request and have it installed on the client machine. Verify it by running "certmgr.msc"
Set a certificate chain for TP.
Set a TP and certificate for a key ring.
Access UCSM through https should now give no "untrusted connection" message.
Generic Managed Object Queries
Get Managed Object of a specific DN.
Get all Managed Objects of a particular class.
Get DNs of Managed Objects of a particular class.
Get names of all Service Profiles from org-root.
Generic Managed Object Cmdlets
Create a VLAN using parent object.
Create a VLAN using parent object, modify if already existing.
Modify a VLAN using Managed Object.
Generic Cmdlet –XmlTag
The XmlTag parameter enables us to work with unknown Managed Objects.
XtraProperty in Get/Add/Set cmdlets
The XtraProperty parameter ensures that unknown Managed Object properties can also be used in Get/Add/Set cmdlets.
Create a service profile with extra property ExtIPPoolName.
Get all service profiles that have ext-mgmt as ExtIPPoolName.
CCO Integration
Get a List of Images from CCO.
Select 2.0(1x) images and download the images. Get-UcsCcoImage first checks if the image is available locally. If the image exists and md5sum matches, no download is initiated. If not, the image is downloaded.
Re-running the command should not initiate any downloads, if the previous download was successful.
Export to XML
Export the configuration of a Managed Object.
This cmdlet exports the configuration of the managed object and the entire hierarchy.
KVM
Start a KVM session for service profile and add a customized title for the KVM window.
Launch the UCSM GUI
Connect to UCSM and launch the UCSM GUI.
Some XML transactions are treated as secure and the UCSM GUI does not log them. The LogAllXml flag enables secure logging.
Launch the UCSM GUI using the Get-UcsStatus and Start-UcsGuiSession cmdlets.
UCS Statistics
Get current Ucs statistics for Chassis Id 1 and Slot Id 1.
Configure Scalability Port in UCS 6324 Fabric Interconnect
Configure the breakout port 1/5/1 in UCS 6324 Fabric Interconnect B as a server port
Configure the breakout port 1/5/1 in UCS 6324 Fabric Interconnect B as an FCoE storage port
Configure breakout port 1/5/1 in UCS 6324 Fabric Interconnect B appliance port
Transaction Impact
Get-UcsTransactionImpact cmdlet estimates the impact of a pending transaction. The cmdlet uses the ConfigEstimateImpact method and returns a UcsImpact object. A message that is similar to the message provided by UCS Manager GUI is provided as part of the UcsImpact object.
Add a VLAN for vNIC, make it Native VLAN.
One can now observe that a UcsImpact object was returned, which indicates a config-failure for the service profile that would be created etc.
Cmdlet Meta Information
Get Meta information about all Managed Object mapped cmdlets.
Get Meta information about LsServer mapped cmdlets.
View the hierarchy of the ServiceProfile (LsServer) class.
Get Meta information for the UcsServiceProfile noun.
Compare-UcsManagedObject - Dn Translation
Create a service profile under org A. Assume that orgs A & B are in place already.
Create a translation map with DNs of entities that needs to be translated.
Combine the translation map with Compare-UcsMo to see the changes required.
Combine the translation org with Compare to see the changes required.
Sync a service profile from org A to org B while renaming it.
Compare-UcsManagedObject – GetPropertyDiff()
Use GetPropertyDiff() function on output of Compare- UcsManagedObject to see the difference in properties.
Display all the properties having difference. If $diff is an array of objects, then GetPropertyDiff works on $diff[<index>]
Add Cmdlet –ModifyPresent Flag
The ModifyPresent option ensures that the add-cmdlets modify the MO, if it already exists, instead of returning an error.
Create a csv file with Name, Id pairs.
Import the Name, Vlan pairs from the file and create those vlans.
Edit the csv file to edit the ids or add new vlans. Re-running the same Add-UcsVlan snippet above will result in an error, if existing VLANs created again (with or without changes). Invoking Add-UcsVlanþwith the ModifyPresent option, addresses this by modifying the VLANs instead, if they already exist.
Capability Catalog Update
The capability catalog is a set of tunable parameters, strings, and rules. Cisco UCS uses the catalog to update the display and configurability of components, such as newly qualified DIMMs and disk drives for servers.
To update the capability catalog from a local file source you can use the following cmdlet:
Server Operations
Added the following new simplified cmdlets to perform server operations:
Related Cisco UCS Documentation and Documentation Feedback
For more information, you can access related documents from the following links:
To provide technical feedback on this document, or to report an error or omission, please send your comments to ucs-docfeedback@external.cisco.com. We appreciate your feedback.
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What’s New in Cisco Product Documentation, which also lists all new and revised Cisco technical documentation:
http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html
Subscribe to the What’s New in Cisco Product Documentation as an RSS feed and set content to be delivered directly to your desktop using a reader application. The RSS feeds are a free service. Cisco currently supports RSS Version 2.0.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses used in this document are not intended to be actual addresses. Any examples, command display output, and figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses in illustrative content is unintentional and coincidental.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback