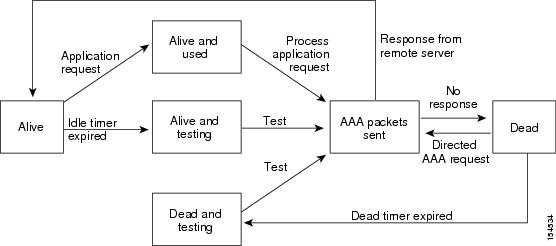
You can monitor the availability of all RADIUS servers without having to configure the test parameters for each server individually.
Any servers for which test parameters are not configured are monitored using the global level parameters.

Note |
Test parameters that are configured for individual servers take precedence over global test parameters.
|
The global configuration parameters include the username and password to use for the servers and an idle timer. The idle
timer specifies the interval in which a RADIUS server receives no requests before the Cisco NX-OS device sends out a test
packet. You can configure this option to test servers periodically, or you can run a one-time only test.

Note |
CFS does not distribute global RADIUS server group configurations.
|

Note |
To protect network security, we recommend that you use a username that is not the same as an existing username in the RADIUS
database.
|

Note |
The default idle timer value is 0 minutes. When the idle time interval is 0 minutes, periodic RADIUS server monitoring is
not performed.
|

 Feedback
Feedback