- Preface
- Product Overview
- Configuring the Router for the First Time
- Configuring a Supervisor Engine 720
- Configuring a Route Switch Processor 720
- Configuring NSF with SSO Supervisor Engine Redundancy
- ISSU and eFSU on Cisco 7600 Series Routers
- Configuring RPR and RPR+ Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring a Supervisor Engine 32
- Configuring LAN Ports for Layer 2 Switching
- Configuring Flex Links
- Configuring EtherChannels
- Configuring VTP
- Configuring VLANs
- Configuring Private VLANs
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling
- Configuring L2TPv3
- Configuring STP and MST
- Configuring Optional STP Features
- Configuring Layer 3 Interfaces
- Configuring GTP-SLB IPV6 Support
- IP Subscriber Awareness over Ethernet
- Configuring UDE and UDLR
- Configuring Multiprotocol Label Switching on the PFC
- Configuring IPv4 Multicast VPN Support
- Configuring Multicast VPN Extranet Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast PFC3 and DFC3 Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping for IPv6 Multicast Traffic
- Configuring IGMP Snooping for IPv4 Multicast Traffic
- Configuring PIM Snooping
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VRF aware 6RD Tunnels
- Configuring VLAN ACLs
- Private Hosts (Using PACLs)
- Configuring IPv6 PACL
- IPv6 First-Hop Security Features
- Configuring Online Diagnostics
- Configuring Denial of Service Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection
- Configuring Traffic Storm Control
- Unknown Unicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC QoS Statistics Data Export
- Configuring MPLS QoS on the PFC
- Configuring LSM MLDP based MVPN Support
- Configuring IEEE 802.1X Port-Based Authentication
- Configuring IEEE 802.1ad
- Configuring Port Security
- Configuring UDLD
- Configuring NetFlow and NDE
- Configuring Local SPAN, RSPAN, and ERSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Web Cache Services Using WCCP
- Using the Top N Utility
- Using the Layer 2 Traceroute Utility
- Configuring Bidirectional Forwarding and Detection over Switched Virtual Interface
- Configuring Call Home
- Configuring IPv6 Policy Based Routing
- Using the Mini Protocol Analyzer
- Configuring Resilient Ethernet Protocol
- Configuring Synchronous Ethernet
- Configuring Link State Tracking
- Configuring BGP PIC Edge and Core for IP and MPLS
- Configuring VRF aware IPv6 tunnels over IPv4 transport
- ISIS IPv4 Loop Free Alternate Fast Reroute (LFA FRR)
- Multicast Service Reflection
- Y.1731 Performance Monitoring
- Online Diagnostic Tests
- Acronyms
- Cisco IOS Release 15S Software Images
- Index
Cisco 7600 Series Router Software Configuration Guide, Cisco IOS Release 15S
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- July 28, 2014
Chapter: Configuring IEEE 802.1ad
- Prerequisites for IEEE 802.1ad
- Restrictions for IEEE 802.1ad
- Information About IEEE 802.1ad
- How to Configure IEEE 802.1ad
- Configuring a Switchport
- Configuring a Layer 2 Protocol Forward
- Configuring a Switchport for Translating QinQ to 802.1ad
- Configuring a Switchport (L2PT)
- Configuring a Customer-Facing UNI-C Port with EVC
- Configuring a Customer-Facing UNI-C Port and Switchport on NNI with EVC
- Configuring a Customer-Facing UNI-S Port with EVC
- Configuring a Layer 3 Termination
- Displaying a Dot1ad Configuration
- Troubleshooting Dot1ad
Configuring IEEE 802.1ad
Provider networks handle traffic from a large number of customers. It is important that one customer’s traffic is isolated from the other customer’s traffic. IEEE 802.1ad implements standard protocols for double tagging of data. The data traffic coming from the customer side are double tagged in the provider network where the inner tag is the customer-tag (C-tag) and the outer tag is the provider-tag (S-tag). The control packets are tunneled by changing the destination MAC address in the provider network.
Cisco 7600 series routers already support VLAN double tagging through a feature called QinQ. 802.1ad is the standardized version of QinQ. It also extends the support for Layer 2 Protocol Tunneling Protocol (L2PT). By offering transparent Layer 2 connectivity, the service provider does not get involved in the customer’s Layer 3 network. This makes provisioning and maintenance simple, and reduces the operational cost.
Prerequisites for IEEE 802.1ad
Restrictions for IEEE 802.1ad
Follow these restrictions and guidelines when you configure 802.1ad:
- The l2protocol forward command is available only on the main interface of switchports and L3 ports. The command is not available on the subinterfaces. All the subinterfaces on a port inherit the behavior from the main interface. The l2protocol forward command is also available on EVC service instance.
- The l2protocol peer and l2protocol drop commands are not supported.
- The l2protocol forward command on a main interface and on EVCs supports only cdp, dtp, vtp, stp, and dot1x.
- You cannot configure Dot1ad if custom ethertype is configured on port.
- 802.1ad is supported on the following port types:
|
|
|
|
|
|---|---|---|---|
Information About IEEE 802.1ad
To configure IEEE 802.1ad support, you should understand the following concepts:
How Provider Bridges Work
Provider bridges pass the network traffic of many customers, and each customer's traffic flow must be isolated from one another. For the Layer 2 protocols within customer domains to function properly, geographically separated customer sites must appear to be connected through a LAN, and the provider network must be transparent.
The IEEE has reserved 33 Layer 2 MAC addresses for customer devices operating Layer 2 protocols. If a provider bridge uses these standard MAC addresses for its Layer 2 protocols, the customers' and service provider's Layer 2 traffic will be mixed together. Provider bridges solve this traffic-mixing issue by providing Layer 2 protocol data unit (PDU) tunneling for customers using a provider bridge (S-bridge) component and a provider edge bridge (C-bridge) component. Figure 53-1 shows the topology.
Figure 53-1 Layer 2 PDU Tunneling
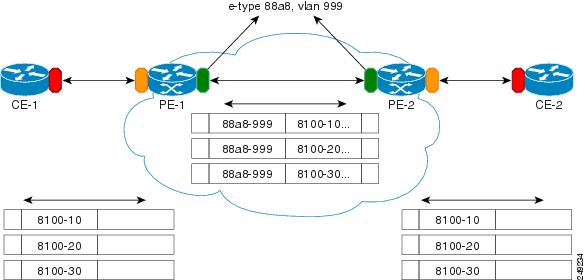
S-Bridge Component
The S-bridge component is capable of inserting or removing a service provider VLAN (S-VLAN) for all traffic on a particular port. IEEE 802.1ad adds a new tag called a Service tag (S-tag) to all the ingress frames from a customer to the service provider.
The VLAN in the S-tag is used for forwarding the traffic in the service provider network. Different customers use different S-VLANs, which results in each customer's traffic being isolated. In the S-tag, provider bridges use an Ethertype value that is different from the standard 802.1Q Ethertype value, and do not understand the standard Ethertype. This difference makes customer traffic tagged with the standard Ethertype appear as untagged in the provider network so customer traffic is tunneled in the port VLAN of the provider port. The 802.1ad service provider user network interfaces (S-UNIs) and network to network interfaces (NNIs) implement the S-bridge component.
For example, a VLAN tag has a VLAN ID of 1, the C-tag Ethertype value is 8100 0001, the S-tag Ethertype value is 88A8 0001, and the class of service (CoS) is zero.
------------------------------------------------------- -----------------------------------------------
0x8100 | Priority bits | CFI | C-VLAN-ID 0x88A8 | Priority bits | 0 | S-VLAN-ID
------------------------------------------------------- -----------------------------------------------
C-Bridge Component
All the C-VLANs entering on a UNI port in an S-bridge component are provided the same service (marked with the same S-VLAN). Although, C-VLAN components are not supported, a customer may want to tag a particular C-VLAN packet separately to differentiate between services. Provider bridges allow C-VLAN packet tagging with a provider edge bridge, called the C-bridge component of the provider bridge. C-bridge components are C-VLAN aware and can insert or remove a C-VLAN 802.1Q tag. The C-bridge UNI port is capable of identifying the customer 802.1Q tag and inserting or removing an S-tag on the packet on a per service instance or C-VLAN basis. A C-VLAN tagged service instance allows service instance selection and identification by C-VLAN. The 802.1ad customer user network interfaces (C-UNIs) implement the C-component.
MAC Addresses for Layer 2 Protocols
Customers' Layer 2 PDUs received by a provider bridge are not forwarded, so Layer 2 protocols running in customer sites do not know the complete network topology. By using a different set of addresses for the Layer 2 protocols running in provider bridges, IEEE 802.1ad causes customers' Layer 2 PDUs entering the provider bridge to appear as unknown multicast traffic and forwards it on customer ports (on the same S-VLAN). Customers' Layer 2 protocols can then run transparently.
Table 53-1 shows the Layer 2 MAC addresses reserved for the C-VLAN component.
Table 53-2 shows the Layer 2 MAC addresses reserved for an S-VLAN component. These addresses are a subset of the C-VLAN component addresses, and the C-bridge does not forward the provider's bridge protocol data units (BPDUs) to a customer network.
Guidelines for Handling BPDU
UNI-C Ports
The guidelines pertaining to UNI-C ports are:
- VLAN-aware L2 protocols can be peered, tunneled, or dropped.
- Port L2 protocols can either be peered or dropped. They cannot be tunneled.
Table 53-3 shows the Layer 2 PDU destination MAC addresses for customer-facing C-bridge UNI ports, and how frames are processed.
UNI-S Ports
The guidelines pertaining to UNI-S ports are:
- Packets with C-Bridge addresses (00 - 0F) that are not part of S-Bridge addresses (01 - 0A) are treated as data packet (tunneled).
- VLAN-aware L2 protocols cannot be peered because the port is not C-VLAN aware. They can only be tunneled or dropped.
- Port L2 protocols can be peered, tunneled, or dropped.
Table 53-4 shows the Layer 2 PDU destination MAC addresses for customer-facing S-bridge UNI ports, and how frames are processed.
|
|
|
|
|
|---|---|---|---|
NNI Ports
The Dot1add NNI ports behave in the same way as the customer facing S-bridge ports, with the following exceptions:
- On NNI ports, frames received with DA 01-80-C2-00-00-08 contain STP BPDU. The frames are received and transmitted. On S-UNI ports, any such frames that are received are dropped, and none are sent. Starting with Cisco IOS Release 15.4(3)S, on NNI ports, frames received with DA 01-80-C2-00-00-08 include PVST BPDU.
- On NNI ports, frames received with DA 01-80-C2-00-00-02 include CDP Pagp, VTP, DTP, and UDLD protocols.
- Starting with Cisco IOS Release 15.4(3)S, on NNI ports, frames received with DA 01-80-C2-00-00-03 include LLDP protocol.
7600 Action Table
Table 53-5 lists the actions performed on a packet when the packet is received with a specified destination MAC address.
|
|
|
|
|
|
|---|---|---|---|---|
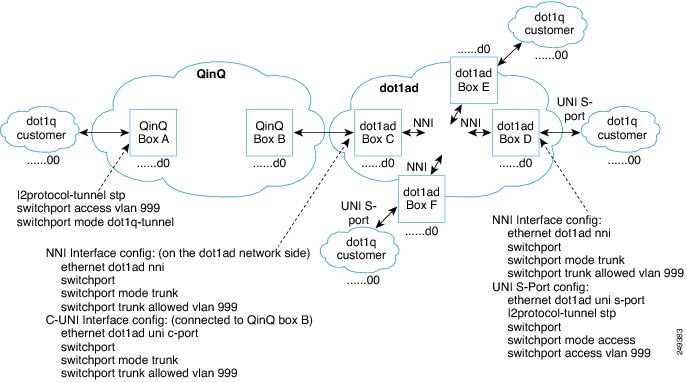
Interoperability of QinQ and Dot1ad
The interoperability of QinQ and Dot1ad network enables the exchange of data frames between the networks. The 802.1Q network outer tag VLANs are mapped to the provider S-VLANs of the 802.1ad network.
Figure 53-2 illustrates the interoperability of a Dot1ad network and a QinQ network.
Figure 53-2 Interoperability of Dot1ad Network and a QinQ Network
How to Configure IEEE 802.1ad
This section contains the information about following procedures:
- Configuring a Switchport
- Configuring a Layer 2 Protocol Forward
- Configuring a Switchport for Translating QinQ to 802.1ad
- Configuring a Switchport (L2PT)
- Configuring a Customer-Facing UNI-C Port with EVC
- Configuring a Customer-Facing UNI-C Port and Switchport on NNI with EVC
- Configuring a Customer-Facing UNI-S Port with EVC
- Configuring a Layer 3 Termination
- Displaying a Dot1ad Configuration
Configuring a Switchport
A switchport can be configured as a UNI-C port, UNI-S port, or NNI port.
UNI-C Port
A UNI-C port can be configured as either a trunk port or an access port. Perform the following tasks to configure a UNI-C port as an access port for 802.1ad.
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
DETAILED STEPS
|
|
|
|
|---|---|---|
Configures a dot1ad NNI port or UNI port. In this example, it is a UNI-C port. |
||
Sets the VLAN when an interface is in access mode. In this example, the VLAN is set to 1000. |
||
Perform the following tasks to configure a UNI-C port as a trunk port for 802.1ad.
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
DETAILED STEPS
UNI-S Port
On a UNI-S port, all the customer VLANs that enter are provided with the same service. The port allows only access configuration. In this mode, the customer’s port is configured as a trunk port. Therefore, the traffic entering the UNI-S port is tagged traffic.
Perform the following tasks to configure a UNI-S port as an access port for 802.1ad.
SUMMARY STEPS
5.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
6.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
DETAILED STEPS
|
|
|
|
|---|---|---|
Configures a dot1ad NNI port or UNI port. In this example, it is a UNI-S port. |
||
Sets the VLAN when an interface is in access mode. In this example, the VLAN is set to 999. |
||
NNI Port
NNI port allows only trunk configuration. On an NNI port, the frames received on all the allowed VLANs are bridged to the respective internal VLANs.
Perform the following tasks to configure an NNI port as a trunk port for 802.1ad.
SUMMARY STEPS
5.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
6.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
DETAILED STEPS
Examples
The following example shows how to configure a UNI-C port as an access port. In this example, all the frames that are received are bridged to one internal VLAN 1000. The transmitted frames do not have the access VLAN Dot1q tag.
The following example shows how to configure a UNI-C port as a trunk port. In this example, all the frames that are received on all allowed VLANs (1000 and 2000) are bridged to the respective internal VLANs. The transmitted frames have the respective internal VLAN Dot1q tag.
Router(config-if)# switchport access vlan 1000, 2000
The following example shows how to configure a UNI-S port. In this example, all the frames that are received are bridged to one internal VLAN (999). The transmitted frames do not have the access VLAN Dot1q tag.
The following example shows how to configure an NNI port. Only trunk configuration is allowed on an NNI port. In this example, all the frames that are received on all the allowed VLANs (999) are bridged to the respective internal VLANs. The transmitted frames have the respective internal VLAN Dot1q tag.
Router(config-if)# switchport trunk allowed vlan 999
The following example shows how to configure Dot1ad on an SVI:
Router(config-if)# switchport trunk allowed vlan 999
Router(config)# interface vlan 999
Router(config-if)# ip address 1.2.3.4 255.255.0.0
Configuring a Layer 2 Protocol Forward
Perform the following tasks to configure the Layer 2 protocol forward:
SUMMARY STEPS
4.![]() switchport access vlan vlan-id
switchport access vlan vlan-id
5.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
DETAILED STEPS
Examples
The following example shows how to configure a Layer 2 protocol forward:
Configuring a Switchport for Translating QinQ to 802.1ad
Translating a QinQ port to 802.1ad involves configuring the port connecting to QinQ port and NNI port.
Perform the following tasks to configure a port connecting to the QinQ port.
SUMMARY STEPS
4.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
DETAILED STEPS
|
|
|
|
|---|---|---|
Sets the list of allowed VLANs that transmit traffic from this interface in tagged format when in trunking mode. |
||
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
DETAILED STEPS
Examples
The following example shows how to translate a QinQ port to 802.1ad. In this example, the peer router to gig1/1 multiplexes various customer VLANs into VLAN 1000.
Router(config-if)# switchport trunk allowed vlan 1000
Configuring a Switchport (L2PT)
Configuring the switchport for L2PT is required to tunnel the STP packets from a customer on the dot1ad network to a customer on the QinQ network.
Perform the following tasks to configure the port connecting to the customer.
SUMMARY STEPS
5.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() no l2 protocol [peer | forward] [ protocol ]
no l2 protocol [peer | forward] [ protocol ]
7.![]() l2protocol-tunnel [cdp | stp | vtp]
l2protocol-tunnel [cdp | stp | vtp]
DETAILED STEPS
|
|
|
|
|---|---|---|
Configures a dot1ad NNI port or UNI port. In this example, it is a UNI S-port. |
||
SUMMARY STEPS
5.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
DETAILED STEPS
|
|
|
|
|---|---|---|
Configures a dot1ad NNI or UNI port. In this example, it is an NNI. |
||
Examples
The following example shows how to tunnel the STP packets from a customer on the Dot1ad network to a customer on a QinQ network:
Router(config-if)# switchport mode access
Configuring a Customer-Facing UNI-C Port with EVC
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
5.![]() service instance id service-type
service instance id service-type
6.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
8.![]() service instance id service-type
service instance id service-type
9.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
DETAILED STEPS
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
5.![]() service instance id service-type
service instance id service-type
6.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
7.![]() rewrite ingress tag pop 1 symmetric
rewrite ingress tag pop 1 symmetric
9.![]() service instance id service-type
service instance id service-type
10.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
DETAILED STEPS
Examples
The following example shows how to configure a customer-facing UNI port. In this example, a dot1q frame coming on VLAN 50 matches service instance 1, and on the ingress port, the rewrite command pushes the 1000 outer-vlan.
Router(config-if)# bridge-domain 1000
Router(config-if)# service instance 2 ethernet
Router(config-if)# encapsulation dot1q 102-4904
Router(config-if)# bridge-domain 500
Router(config-if)# bridge-domain 1000
Router(config-if)# service instance 2ethernet
Router(config-if)# rewrite ingress tag pop 1 symmetric
Router(config-if)# bridge-domain 500
Configuring a Customer-Facing UNI-C Port and Switchport on NNI with EVC
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
5.![]() service instance id service-type
service instance id service-type
6.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
8.![]() service instance id service-type
service instance id service-type
9.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
DETAILED STEPS
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() switchport mode {access | trunk}
switchport mode {access | trunk}
DETAILED STEPS
Examples
The following example shows how to configure a customer-facing UNI-C port and switchport on NNI with EVC:
Router(config-if)# bridge-domain 1000
Router(config-if)# service instance 2 ethernet
Router(config-if)# encapsulation dot1q 102-4904
Router(config-if)# bridge-domain 500
Router(config-if)# switchport
Router(config-if)# ethernet dot1ad uni
Router(config-if)# switchport mode trunk
Router(config-if)# switchport allowed vlan 1000,500
Configuring a Customer-Facing UNI-S Port with EVC
SUMMARY STEPS
4.![]() service instance id service-type
service instance id service-type
DETAILED STEPS
SUMMARY STEPS
4.![]() service instance id service-type
service instance id service-type
5.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
DETAILED STEPS
Examples
The following example shows how to configure an NNI port:
Router(config-if)# bridge-domain 1000
Configuring a Layer 3 Termination
Perform the following tasks to configure a Layer 3 termination.
SUMMARY STEPS
4.![]() ethernet dot1ad {nni | uni {c-port | s-port}}
ethernet dot1ad {nni | uni {c-port | s-port}}
6.![]() encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
encapsulation dot1q vlan -id second-dot1q {any | vlan -id} [native]
DETAILED STEPS
Examples
The following example shows how to configure a Layer 3 termination. Note that Layer 3 is supported only on trunk interfaces.
Router(config-if)# ip address 1.2.3.4 255.255.0.0
The following example shows how to configure a Layer 3 termination on an SVI:
Router(config-if)# bridge-domain 50
Router(config-if)# service instance 2 ethernet
Router(config-if)# bridge-domain 60
Router(config-if)# ip address 2.3.4.5 255.255.0.0
Displaying a Dot1ad Configuration
You can display a Dot1ad configuration using the show ethernet dot1ad command. This command displays the Dot1ad configuration for all interfaces. To display the configuration on a particular interface, use the show ethernet dot1ad interface command.
The following example shows how to display a Dot1ad configuration on all interfaces:
Troubleshooting Dot1ad
The following section describes how to troubleshoot Dot1ad.

Note![]() The show commands in these examples should be run from a line card console.
The show commands in these examples should be run from a line card console.
Run the following command to verify the Dot1ad configuration:
Run the following command to verify the Dot1ad configuration:
Run the following command to verify the L2protocol forwarding:
For switchports, run the following command:
For EVCs, run the following command:
To display the default values, run the following commands:
 Feedback
Feedback