- Preparing for Broadband Access Aggregation
- Understanding Broadband Access Aggregation
- Providing Protocol Support for Broadband Access Aggregation of PPP over ATM Sessions
- Upstream PPPoX Connection Speed Transfer at LAC
- Providing Session Limit Support
- Monitoring PPPoE Sessions with SNMP
- PPP over Ethernet Client
- PPPoE over VLAN Enhancements Configuration Limit Removal and ATM Support
- Providing Protocol Support for Broadband Access Aggregation of PPPoE Sessions
- PPPoE Client DDR Idle-Timer
- Enabling PPPoE Relay Discovery and Service Selection Functionality
- Establishing PPPoE Session Limits per NAS Port
- Offering PPPoE Clients a Selection of Services During Call Setup
- Providing Connectivity Using ATM Routed Bridge Encapsulation over PVCs
- RBE Client Side Encapsulation with QoS
- Routed Bridge Encapsulation with ATM Virtual Circuit Bundles
- Configuring Cisco Subscriber Service Switch Policies
- Subscriber Profile Support
- Controlling Subscriber Bandwidth
- Configuring the Physical Subscriber Line for RADIUS Access and Accounting
- 1-Port ADSL WAN Interface Card
- 1-Port ADSL WAN Interface for the Cisco IAD2420 Series
- 1-Port ADSL WAN Interface Card for Cisco 2600 Series and Cisco 3600 Series Routers
- ADSL Support in IPv6
- ATM Mode for Two-Wire or Four-Wire SHDSL
- 1-Port G.SHDSL WAN Interface Card for Cisco 2600 Series and Cisco 3600 Series Routers
- G.SHDSL Symmetric DSL Support for Cisco IAD2420 Series IAD
- Monitoring and Retraining on Reception of Loss of Margin Messages
- Virtual Auxiliary Port Feature and Configuration of DSL Settings
Broadband Access Aggregation and DSL Configuration Guide, Cisco IOS Release 15MT
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- December 3, 2012
Chapter: Establishing PPPoE Session Limits per NAS Port
- Finding Feature Information
- Prerequisites for Establishing PPPoE Session Limits per NAS Port
- Restrictions for Establishing PPPoE Session Limits per NAS Port
- Information About Establishing PPPoE Session Limits per NAS Port
- How to Establish PPPoE Session Limits per NAS Port
- Configuration Examples for Establishing PPPoE Session Limits per NAS Port
- Where to Go Next
- Additional References
- Feature Information for Establishing PPPoE Session Limits per NAS Port
Establishing PPPoE Session Limits per NAS Port
The PPPoE Session Limits per NAS Port feature enables you to limit the number of PPP over Ethernet (PPPoE) sessions on a specific permanent virtual circuit (PVC) or VLAN configured on an L2TP access concentrator (LAC). The network access server (NAS) port is either an ATM PVC or a configured VLAN ID. PPPoE per-NAS-port session limits are maintained in a RADIUS server customer profile database and are downloaded during Subscriber Service Switch (SSS) preauthorization.
- Finding Feature Information
- Prerequisites for Establishing PPPoE Session Limits per NAS Port
- Restrictions for Establishing PPPoE Session Limits per NAS Port
- Information About Establishing PPPoE Session Limits per NAS Port
- How to Establish PPPoE Session Limits per NAS Port
- Configuration Examples for Establishing PPPoE Session Limits per NAS Port
- Where to Go Next
- Additional References
- Feature Information for Establishing PPPoE Session Limits per NAS Port
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for Establishing PPPoE Session Limits per NAS Port
You must understand the concepts described in the "Preparing for Broadband Access Aggregation" module.
Both the LAC and the L2TP Network Server (LNS) must be running a Cisco IOS image that supports the PPPoE Session Limit Per NAS Port feature.
Protocol support for broadband access aggregation must be established using the procedures in the "Providing Protocol Support for Broadband Access Aggregation of PPPoE Sessions" module.
Restrictions for Establishing PPPoE Session Limits per NAS Port
Do not configure the PPPoE per-NAS-port session limit to zero.
PPPoE Session Limit per NAS Port does not support TACACS+.
PPPoE Session Limit per NAS Port applies only to PVCs and VLANs.
Information About Establishing PPPoE Session Limits per NAS Port
- How PPPoE per-NAS-Port Session Limits Work
- Relationship Between the Per-NAS-Port Session Limit and Other Types of Session Limits
- Benefits of PPPoE Session Limits per NAS Port
How PPPoE per-NAS-Port Session Limits Work
The PPPoE Session Limits Per NAS Port feature limits the number of PPPoE sessions on a specific PVC or VLAN configured on an LAC. The NAS port is either an ATM PVC or a configured VLAN ID.
The PPPoE per-NAS-port session limit is maintained in a RADIUS server customer profile database. This customer profile database is connected to an LAC and is separate from the RADIUS server that the LAC and LNS use for the authentication and authorization of incoming users. See below for a sample network topology. When the customer profile database receives a preauthorization request from the LAC, it sends the PPPoE per-NAS-port session limit to the LAC.
The LAC sends a preauthorization request to the customer profile database when the LAC is configured for SSS preauthorization. When the LAC receives the PPPoE per-NAS-port session limit from the customer profile database, the LAC compares the PPPoE per-NAS-port session limit with the number of sessions currently on the NAS port. The LAC then decides whether to accept or reject the current call, depending upon the configured PPPoE per NAS port-session-limit and the number of calls currently on the NAS port. PPPoE Session Limit per NAS Port Sample Topology
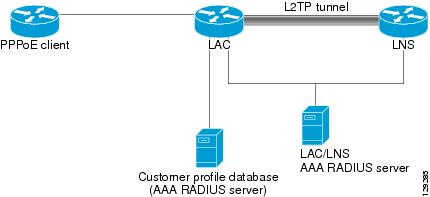
The customer profile database consists of a user profile for each user that is connected to the LAC. Each user profile contains the NAS-IP-Address (attribute 4) and the NAS-Port-ID (attribute 5.) When the LAC is configured for SSS preauthorization, it queries the customer profile database using the username. When a match is found in the customer profile database, the customer profile database sends the PPPoE per-NAS-port session limit in the user profile. The PPPoE per-NAS-port session limit is defined in the username as a Cisco attribute-value (AV) pair.
Relationship Between the Per-NAS-Port Session Limit and Other Types of Session Limits
You can configure types of session limits other than per-NAS-sort sessions on the LAC, including session limit per VC, per VLAN, per MAC, and a global session limit for the LAC. When PPPoE session limits for a NAS port are enabled (that is, when you have enabled SSS preauthorization on the LAC), local configurations for session limits per VC and per VLAN are overwritten by the PPPoE per-NAS-port session limit downloaded from the customer profile database. Configured session limits per VC and per VLAN serve as backups in case of a download failure of the PPPoE per-NAS-port session limit. Global session limits and per-MAC session limits, if configured on the router, will take effect as other means of limiting PPPoE sessions.
Benefits of PPPoE Session Limits per NAS Port
PPPoE session limits per NAS port provides flexibility and simplifies router configuration by allowing you to download the per-VC and per-VLAN session limits from a RADIUS server in addition to being able to configure them on the router.
How to Establish PPPoE Session Limits per NAS Port
- Enabling Subscriber Service Switch Preauthorization
- Configuring the RADIUS User Profile for PPPoE Session Limits per NAS Port
- Verifying PPPoE Session Limit per NAS Port
Enabling Subscriber Service Switch Preauthorization
When SSS preauthorization is enabled on an LAC, local configurations for session limit per VC and per VLAN are overwritten by the per-NAS-port session limit downloaded from the server. Perform this task to enable SSS preauthorization:
1.
enable
2.
configure
terminal
3.
subscriber
access
pppoe
pre-authorize
nas-port-id
[aaa-method-list]
4.
exit
DETAILED STEPS
Configuring the RADIUS User Profile for PPPoE Session Limits per NAS Port
Perform the following steps to enable per-NAS-port PPPoE session limits in a RADIUS user profile for the customer profile database. Refer to the Cisco IOS Security Configuration Guide for information about creating a RADIUS user profile.
1. User-Name = nas-port:ip-address:slot/subslot/port/vpi.vci
2. User-Name = nas-port:ip-address:slot/subslot/port/vlan-id
3. User-Name = nas-port:ip-address:slot/subslot/port/vlan-id
4. Password = "cisco"
5. cisco-avpair = "pppoe:session-limit-session-limit-per-NAS-port"
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | User-Name = nas-port:ip-address:slot/subslot/port/vpi.vci |
Configures the NAS port username for a PPPoE over ATM NAS port user.
|
| Step 2 | User-Name = nas-port:ip-address:slot/subslot/port/vlan-id |
Configures the NAS port username for a PPPoE over ATM NAS port user.
|
| Step 3 |
User-Name = nas-port:ip-address:slot/subslot/port/vlan-id Example: |
Configures the NAS port username for a PPPoE over VLAN NAS port user.
|
| Step 4 |
Password = "cisco" Example: |
Sets the fixed password. |
| Step 5 | cisco-avpair = "pppoe:session-limit-session-limit-per-NAS-port" |
Adds the PPPoE session limit per NAS port cisco AVpair to the user profile.
|
Verifying PPPoE Session Limit per NAS Port
Perform this task to verify per-NAS-port session limit performance.
1.
enable
2.
debug
aaa
authorization
3.
debug
radius
[brief | hex]
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
| Step 2 |
debug
aaa
authorization
Example: Router# debug aaa authorization |
Displays information about AAA authorization. |
| Step 3 |
debug
radius
[brief | hex] Example: Router(config)# debug radius |
Displays information about RADIUS. |
Configuration Examples for Establishing PPPoE Session Limits per NAS Port
- Configuring the LAC for per-NAS-Port Session Limits for PPPoE over ATM Example
- Configuring the LAC for per-NAS-Port Session Limits for PPPoE over VLAN Example
- Configuring the User Profile for PPPoE Session Limits per NAS Port Example
Configuring the LAC for per-NAS-Port Session Limits for PPPoE over ATM Example
 Note | Effective with Cisco IOS Release 12.2(28)SB, the pppoe limit per-mac, pppoe limit per-vc, and pppoe limit per-vlan commands are replaced by the sessions per-mac limit, sessions per-vc limit, and sessions per-vlan limit commands, respectively, in bba-group configuration mode. See the sessions per-mac limit, sessions per-vc limit, and sessions per-vlan limit commands for more information. |
The following example shows how to configure per-NAS-port session limits for PPPoE over ATM on the LAC:
! username lac password 0 lab username lns password 0 lab aaa new-model ! aaa authentication ppp default group radius local aaa authentication ppp mlist-nasport group radius aaa authorization network mlist-nasport group radius aaa session-id common ip subnet-zero ! no ip domain lookup ip host abrick 209.165.200.225 ! ip cef subscriber access pppoe pre-authorize nas-port-id mlist-nasport vpdn enable ! vpdn-group l2tp-initiator request-dialin protocol l2tp domain example.com initiate-to ip 10.1.1.2 local name lac ! vpdn-group pppoe-terminate accept-dialin protocol pppoe virtual-template 1 pppoe limit per-mac 10 pppoe limit per-vc 10 pppoe limit per-vlan 10 ! vc-class atm pppoe protocol pppoe ubr 155000 encapsulation aal5snap ! interface ATM2/0 no ip address no ip mroute-cache no atm ilmi-keepalive ! interface ATM2/0.1 point-to-point class-int pppoe pvc 1/100 encapsulation aal5snap ! ! interface FastEthernet4/0 ip address 10.1.1.1 255.255.255.0 no ip mroute-cache duplex full ! interface FastEthernet6/0 ip address 10.165.200.225 255.255.255.0 no ip mroute-cache duplex full ! interface Virtual-Template1 ip unnumbered Loopback0 no peer default ip address ppp authentication chap mlist-nasport ! ip default-gateway 10.3.0.1 ip classless ip route 0.0.0.0 0.0.0.0 10.3.0.1 ! ! ip radius source-interface FastEthernet6/0 ! radius-server host 10.1.1.2 auth-port 1645 acct-port 1646 radius-server key cisco radius-server authorization permit missing Service-Type !
Configuring the LAC for per-NAS-Port Session Limits for PPPoE over VLAN Example
 Note | Effective with Cisco IOS Release 12.2(28)SB, the pppoe limit per-mac, pppoe limit per-vc, and pppoe limit per-vlan commands are replaced by the sessions per-mac limit, sessions per-vc limit, and sessions per-vlan limit commands, respectively, in bba-group configuration mode. See the sessions per-mac limit, sessions per-vc limit, and sessions per-vlan limit commands for more information. |
The following example shows how to configure per-NAS-port session limits for PPPoE over VLAN on the LAC:
! username lac password 0 lab username lns password 0 lab aaa new-model ! ! aaa authentication ppp default group radius local aaa authentication ppp mlist-nasport group radius aaa authorization network mlist-nasport group radius aaa session-id common ip subnet-zero ! ! no ip domain lookup ip host abrick 192.0.2.0 ! ip cef subscriber access pppoe pre-authorize nas-port-id mlist-nasport vpdn enable ! vpdn-group l2tp_initiator request-dialin protocol l2tp domain example.com initiate-to ip 10.1.1.2 local name lac ! vpdn-group pppoe-terminate accept-dialin protocol pppoe virtual-template 1 pppoe limit per-mac 10 pppoe limit per-vc 10 pppoe limit per-vlan 10 ! vc-class atm pppoe protocol pppoe ubr 155000 encapsulation aal5snap ! interface ATM2/0 no ip address no ip mroute-cache shutdown no atm ilmi-keepalive ! interface FastEthernet4/0 ip address 10.1.1.1 255.255.255.0 no ip mroute-cache duplex full ! interface FastEthernet6/0 ip address 224.0.0.0 255.255.255.0 no ip mroute-cache duplex full ! interface Virtual-Template1 ip unnumbered Loopback0 no peer default ip address ppp authentication chap mlist-nasport ! ip default-gateway 224.0.0.0 ip classless ip route 0.0.0.0 0.0.0.0 224.0.0.0 ! ! ip radius source-interface FastEthernet6/0 ! ! ! radius-server host 10.1.1.2 auth-port 1645 acct-port 1646 radius-server key cisco radius-server authorization permit missing Service-Type !
Configuring the User Profile for PPPoE Session Limits per NAS Port Example
The following example shows how to configure the user profile for PPPoE session limits per NAS port. In this example, the user has a PVC with a VPI of 1 and a VCI of 100 on ATM interface 4/0/0 of the LAC with an IP address of 10.10.10.10:
Username=nas_port:10.10.10.10:4/0/0/1.100 Password = "password1" cisco-avpair= "pppoe:session-limit=<session limit per NAS-port>"
Where to Go Next
If you want to use service tags to enable a PPPoE server to offer PPPoE clients a selection of services during call setup, refer to the "Offering PPPoE Clients a Selection of Services During Call Setup" module.
If you want to enable an L2TP access concentrator to relay active discovery and service selection functionality for PPPoE over an L2TP control channel to an LNS or tunnel switch, refer to the "Enabling PPPoE Relay Discovery and Service Selection Functionality" module.
If you want to configure the transfer upstream of the PPPoX session speed value, refer to the "Configuring Upstream Connections Speed Transfer" module.
If you want to use the Simple Network Management Protocol (SNMP) to monitor PPPoE sessions, refer to the "Monitoring PPPoE Sessions with SNMP" module.
If you want to identify a physical subscribe line for RADIUS communication with a RADIUS server, refer to the "Identifying a Physical Subscriber Line for RADIUS Access and Accounting" module.
If you want to configure a Cisco Subscriber Service Switch, refer to the "Configuring Cisco Subscriber Service Switch Policies" module.
Additional References
Related Documents
|
Related Topic |
Document Title |
|---|---|
|
Broadband access commands: complete command syntax, command mode, command history, defaults, usage guidelines, and examples |
"Wide-Area Networking Commands" chapter in the Cisco IOS Wide-Area Networking Command Reference |
|
Broadband access aggregation concepts |
" Understanding Broadband Access Aggregation" |
|
Task for preparing for broadband access aggregation |
"Preparing for Broadband Access Aggregation" |
|
Broadband access aggregation support |
"Providing Protocol Support for Broadband Access Aggregation of PPPoE Sessions" |
Standards
|
Standard |
Title |
|---|---|
|
No new or modified standards are supported by this feature, and support for existing standards has not been modified by this feature. |
-- |
MIBs
|
MIB |
MIBs Link |
|---|---|
|
No new or modified MIBs are supported by this feature, and support for existing MIBs has not been modified by this feature. |
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
RFCs
|
RFC |
Title |
|---|---|
|
RFC 2516 |
A Method for Transmitting PPP over Ethernet (PPPoE) |
|
RFC 2684 |
Multiprotocol Encapsulation over ATM Adaptation Layer 5 |
Technical Assistance
|
Description |
Link |
|---|---|
|
The Cisco Support website provides extensive online resources, including documentation and tools for troubleshooting and resolving technical issues with Cisco products and technologies. To receive security and technical information about your products, you can subscribe to various services, such as the Product Alert Tool (accessed from Field Notices), the Cisco Technical Services Newsletter, and Really Simple Syndication (RSS) Feeds. Access to most tools on the Cisco Support website requires a Cisco.com user ID and password. |
Feature Information for Establishing PPPoE Session Limits per NAS Port
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to . An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
PPPoE Session Limit per NAS Port |
12.2(31)SRC 12.2(15)B 12.3(4)T |
The PPPoE Session Limit per NAS Port feature enables you to limit the number of PPP over Ethernet (PPPoE) sessions on a specific permanent virtual circuit (PVC) or VLAN configured on an L2TP access concentrator (LAC). In Cisco IOS Release 12.2(15)B, this feature was introduced. In Cisco IOS Release 12.3(4)T, this feature was integrated into the T train. |
 Feedback
Feedback