Cisco Prime Network Control System Appliance
| Series | Cisco Prime Network Control System Series Appliances |
|---|---|
| Overview | Product Overview |
| Status | Available Order |
| Release Date | 18-APR-2011 |
| Product ID | |
- US/Canada 800-553-2447
- Worldwide Support Phone Numbers
- All Tools
 Feedback
Feedback
-
Key Information
Customers Also Viewed
Saved Content
-
You can now save documents for easier access and future use. Saved documents for this product will be listed here, or visit the My Saved Content page to view and manage all saved content from across Cisco.com.
Log in to see your Saved Content.
Recent Security Notices
- 10-Jan-2024
- 16-Aug-2023
- 16-Aug-2023
- 05-Apr-2023
- 05-Apr-2023
Document Categories
-
Data Sheets and Product Information
At-a-Glance
- Cisco Prime for IT At-a-Glance (PDF - 466 KB)
Data Sheets
End-of-Life and End-of-Sale Notices
-
Security Notices
Security Advisories, Responses and Notices
Most Recent
- Cisco Evolved Programmable Network Manager and Cisco Prime Infrastructure Vulnerabilities
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Stored Cross-Site Scripting Vulnerability
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Cross-Site Scripting Vulnerabilities
- Cisco Prime Infrastructure and Cisco Evolved Programmable Network Manager Vulnerabilities
- Cisco Evolved Programmable Network Manager, Cisco Identity Services Engine, and Cisco Prime Infrastructure Command Injection Vulnerabilities
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Stored Cross-Site Scripting Vulnerability
- Cisco Prime Infrastructure Reflected Cross-Site Scripting Vulnerability
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Cross-Site Scripting Vulnerability
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Vulnerabilities
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Stored Cross-Site Scripting Vulnerability
- Cisco Prime Infrastructure and Cisco Evolved Programmable Network Manager Information Disclosure Vulnerability
- Cisco Prime Infrastructure and Cisco Evolved Programmable Network Manager Command Injection Vulnerability
- Cisco ADE-OS Local File Inclusion Vulnerability
- Cisco Prime Infrastructure and Cisco Evolved Programmable Network Manager SQL Injection Vulnerability
- Cisco Prime Infrastructure and Evolved Programmable Network Manager Remote Code Execution Vulnerability
-
Release and Compatibility
Release Notes
-
- Cisco Prime NCS (WAN) 1.1.1 Release Notes
- Release Notes for Cisco Prime Network Control System (WAN) 1.1
- Release Notes for Cisco Prime Network Control System, Release 1.1.1.24
- Release Notes for Cisco Prime Network Control System, Release 1.1.0.58
- Release Notes for Cisco Prime Network Control System, Release 1.0.2.29
- Release Notes for Cisco Prime Network Control System, Release 1.0.0.96
- Test 3D PDF Publish (PDF - 25 MB)
Cisco Prime Network Control System Appliance
Reference
Command References
-
- Cisco Prime Network Control System Command Reference, Release 1.0
Cisco Prime Network Control System Appliance
Documentation Roadmaps
- Cisco Prime Network Control System (WAN) 1.1 Documentation Overview
Cisco Prime Network Control System Appliance
Licensing Information
- Open Source Used In Cisco Prime Network Control System (WAN) 1.1 (PDF - 7 MB)
Cisco Prime Network Control System Appliance
Install and Upgrade
Install and Upgrade Guides
-
- Cisco Prime Network Control System (WAN) 1.1 Quick Start Guide
- Cisco Prime Network Control System Appliance Getting Started Guide
Cisco Prime Network Control System Appliance
Configuration
Configuration Guides
-
- Cisco Prime Network Control System Configuration Guide, Release 1.0
Cisco Prime Network Control System Appliance
Maintain and Operate
End-User Guides
-
- Cisco Prime Network Control System (WAN) 1.1 User Guide
Cisco Prime Network Control System Appliance
Literature
White Papers
Log in to see available downloads.
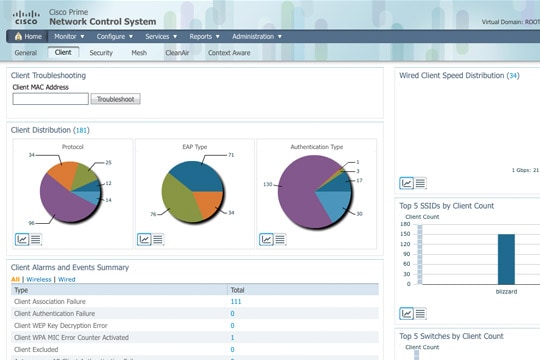
 Feedback
Feedback