Cisco Secure Firewall ASA Virtual (ASAv) Data Sheet
Available Languages
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Today, organizations rely on a mixture of physical and virtual control points to meet their network security needs. They need the flexibility to deploy different physical and virtual firewalls across a wide range of environments while still maintaining consistent policy across branch offices, corporate data centers, and all points between. From data center consolidation to office relocations, mergers and acquisitions, as well as seasonal peaks in demand on your applications, Cisco’s virtual firewall portfolio helps businesses simplify security management with the convenience of unified policy and the flexibility to deploy everywhere.
Cisco® Secure Firewall ASA Virtual (formerly ASAv) gives you the flexibility to choose the performance you need for your organization. Secure Firewall ASA Virtual is the virtualized option of our popular Secure Firewall ASA solution and offers security in traditional physical data centers and private and public clouds. Its scalable VPN capability provides secure access to your organization’s resources—and protects workloads against increasingly complex threats with world-class security controls.
Secure Firewall ASA Virtual is a firewall with powerful VPN capabilities. It supports site-to-site VPN, remote- access VPN, and clientless VPN functionalities. Consistent policy simplifies management across your virtual and physical Secure Firewall ASA solutions. Cisco Smart Software Licensing makes it easy to deploy, manage, and track virtual instances of the appliance running in your private cloud or in a public cloud.
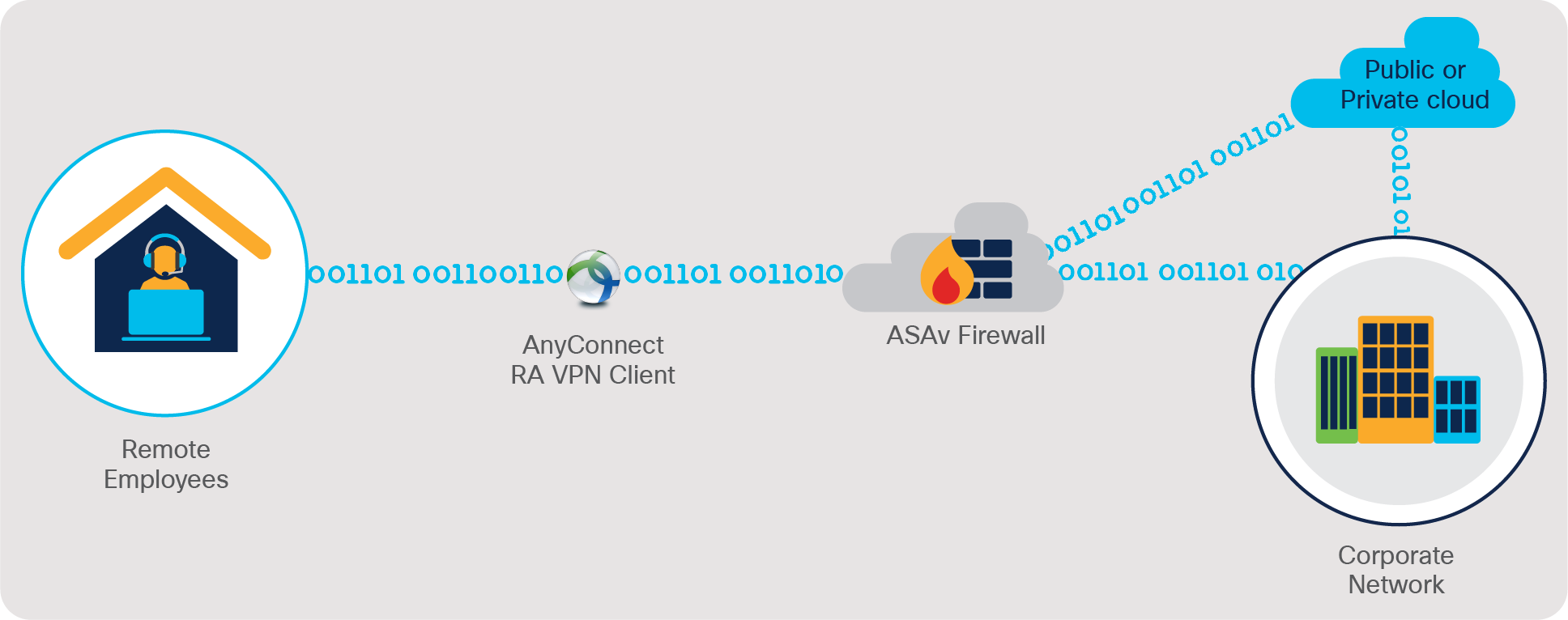
Cisco Secure Firewall ASA Virtual deployed into the public or private cloud
VPN head-end
Cisco AnyConnect® client empowers employees to work from home (or anywhere) on any device at any time, securely. Give any user highly secure access to your enterprise network and provide visibility and control to your IT and security teams to identify who and which devices are accessing the infrastructure. Alleviate strain on your IT and security teams as they support offsite workers and personal devices. Secure Firewall ASA Virtual supports site-to-site VPN for connecting your data centers.
License portability across clouds
Deploy Secure Firewall ASA Virtual everywhere—from your data center to your branch office, to a public cloud— with the portability of one license across public or private clouds (VMware, KVM and Hyper-V, OpenStack, Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), Oracle Cloud Infrastructure (OCI) and government clouds). Expand, contract, and relocate workloads over time spanning private and public cloud infrastructures with one license.
Low-touch deployment
Rapidly deploy additional Secure Firewall ASA Virtual appliances to support unplanned or seasonal surges on your applications or VPN. Add more bandwidth or protection for remote offices by spinning up a new virtual machine. Choose from higher-performance model options if you need more protection.
Cisco Smart Software Licensing makes it easier to buy, deploy, track, and renew Cisco licenses. You will enjoy:
● Simpler purchase and activation of the virtual appliance
● Easier license management and reporting of virtual appliances due to license pooling
● Automatic license activation when the virtual appliance is provisioned
Customers, select partners, and Cisco can view product entitlements and services in the Cisco Smart Software Manager. Configuration and activation are done with a single token. Secure Firewall ASA Virtual will self- register with a Cisco server in the cloud, eliminating the need to register products with Product Activation Keys (PAKs). Instead of using PAKs or license files, Smart Software Licensing establishes a pool of software licenses or entitlements that can be used across your organization. When a virtual appliance is instantiated on a customer’s premises, an entitlement is subtracted from the pool. When a virtual appliance is decommissioned, or when it is deinstantiated within the Smart Software Manager, an entitlement is added to the pool.
With the Smart Software Manager, you can manage license deployments throughout your organization easily and quickly. You can also manage multiple products from Cisco that support Smart Software Licensing.
Secure Firewall ASA Virtual uses Smart Software Licensing exclusively. Older forms of licensing are not supported.
Any Secure Firewall ASA Virtual license can be used on any supported ASAv vCPU/memory configuration. This allows customers to run on a wide variety of VM resource footprints. This also increases the number of supported AWS, Azure, GCP and OCI instance types. When configuring the Secure Firewall ASA Virtual VM, the maximum supported number of vCPUs is 16 and the maximum supported memory is 128GB RAM.
Table 1. Specifications for 9.20 and later- ESXi/KVM/OpenStack
| Feature |
|
|||||
| License Type |
100M (ASAv5) |
1G (ASAv10) |
2G (ASAv30) |
10G (ASAv50) |
20G (ASAv100) |
ASAv-U 9.22+ KVM and ESXi |
| Stateful inspection throughput (maximum)[1] |
100 Mbps |
1 Gbps |
2 Gbps |
10 Gbps |
20 Gbps |
90 Gbps |
| Stateful inspection throughput (multiprotocol)[2] |
100 Mbps |
1 Gbps |
2 Gbps |
10 Gbps |
20 Gbps |
60 Gbps |
| IPsec VPN throughput (AES 450B UDP test)[3] |
100 Mbps |
1 Gbps |
2 Gbps |
6 Gbps |
12 Gbps |
30 Gbps |
| Connections per second |
12,500 |
40,000 |
160,000 |
270,000 |
600,000 |
1,000,000 |
| Concurrent sessions |
50,000 |
100,000 |
500,000 |
2,000,000 |
4,000,000 |
8,000,000 |
| VLANs |
25 |
50 |
200 |
1024 |
1024 |
1024 |
| Bridge groups |
12 |
25 |
100 |
250 |
250 |
250 |
| IPsec VPN peers |
50 |
250 |
750 |
10,000 |
20,000 |
30,000 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
750 |
10,000 |
20,000 |
30,000 |
| Virtual CPU core allocation[4] |
1 |
1 |
4 |
8 |
16 |
16+ |
| Memory allocation4 |
2GB |
2GB |
8GB |
16GB |
32GB |
32+GB |
| Disk storage[5] |
8GB |
8GB |
8GB |
8GB |
8GB |
8GB |
Note: This data is from testing on the Cisco Unified Computing Systems (Cisco UCS®) C series M5 server with the Intel® Xeon® Gold 6254 processors running SR-IOV on Intel X520/X710. Stated virtual CPU core allocation assumes dedicated physical cores with Hyper Threading disabled. Each performance number above was obtained while running only the associated test. For ASAv Unlimited – data is from testing on Cisco UCS M7 with Intel® Xeon® Platinum 8558P processors and SR-IOV on Intel E810.
Table 2. Specifications for 9.20 and later- AWS
| AWS Performance |
|||||
| License Type |
100M (ASAv5) |
1G (ASAv10) |
2G (ASAv30) |
10G (ASAv50) |
20G (ASAv100) |
| AWS Instance Type |
c5n.large |
c5n.large |
c5n.xlarge |
c5n.2xlarge |
c5n.4xlarge |
| Stateful inspection throughput (maximum)6 |
100 Mbps |
1 Gbps |
2 Gbps |
10 Gbps |
20 Gbps |
| Stateful inspection throughput (multiprotocol)7 |
100 Mbps |
1 Gbps |
2 Gbps |
4.5 Gbps |
7 Gbps |
| IPsec VPN throughput (AES 450B UDP test)8 |
100 Mbps |
1 Gbps |
2 Gbps |
4.5 Gbps |
8 Gbps |
| Connections per second |
12,500 |
60,000 |
80,000 |
120,000 |
200,000 |
| Concurrent sessions |
50,000 |
100,000 |
500,000 |
2,000,000 |
4,000,000 |
| IPsec VPN peers |
50 |
250 |
750 |
10,000 |
20,000 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
750 |
10,000 |
20,000 |
Table 3. Specifications for 9.20 and later- Azure
| Azure Performance* |
|||||
| License Type |
100M (ASAv5) |
1G (ASAv10) |
2G (ASAv30) |
10G (ASAv50) |
20G (ASAv100) |
| Azure VM Type |
D3_v2 |
D3_v2 |
D3_v2 |
D4_v2 |
D5_v2 |
| Stateful inspection throughput (maximum)6 |
100 Mbps |
1 Gbps |
2 Gbps |
5.5 Gbps |
11 Gbps |
| Stateful inspection throughput (multiprotocol)7 |
100 Mbps |
1 Gbps |
2 Gbps |
4.6 Gbps |
6 Gbps |
| IPsec VPN throughput (AES 450B UDP test)8 |
100 Mbps |
1 Gbps |
2 Gbps |
4 Gbps |
8 Gbps |
| Connections per second |
4,000 |
4,000 |
4,000 |
8,000 |
14,000 |
| Concurrent sessions |
50,000 |
100,000 |
500,000 |
2,000,000 |
4,000,000 |
| IPsec VPN peers |
50 |
250 |
750 |
10,000 |
20,000 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
750 |
10,000 |
20,000 |
Table 4. Specifications for 9.20 and later- GCP
| GCP Performance |
|||||
| License Type |
100M (ASAv5) |
1G (ASAv10) |
2G (ASAv30) |
10G (ASAv50) |
20G (ASAv100) |
| GCP Machine Type |
c2-standard-4 |
c2-standard-4 |
c2-standard-4 |
c2-standard-8 |
c2-standard-16 |
| Stateful inspection throughput (maximum)6 |
100 Mbps |
1 Gbps |
2 Gbps |
7.6 Gbps |
16 Gbps |
| Stateful inspection throughput (multiprotocol)7 |
100 Mbps |
1 Gbps |
2 Gbps |
6 Gbps |
10 Gbps |
| IPsec VPN throughput (AES 450B UDP test)8 |
100 Mbps |
1 Gbps |
2 Gbps |
5 Gbps |
9.5 Gbps |
| Connections per second |
12,500 |
48,000 |
48,000 |
82,000 |
160,000 |
| Concurrent sessions |
50,000 |
100,000 |
500,000 |
2,000,000 |
4,000,000 |
| IPsec VPN peers |
50 |
250 |
750 |
10,000 |
20,000 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
750 |
10,000 |
20,000 |
Table 5. Specifications for 9.20 and later- OCI
| OCI Performance* |
|||||
| License Type |
100M (ASAv5) |
1G (ASAv10) |
2G (ASAv30) |
10G (ASAv50) |
20G (ASAv100) |
| OCI Shape Type |
VM.Standard3.4 |
VM.Standard3.4 |
VM.Standard3.4 |
VM.Standard3.8 |
VM.Standard3.8 |
| Stateful inspection throughput (maximum)[6] |
100 Mbps |
1 Gbps |
2 Gbps |
8 Gbps |
8 Gbps |
| Stateful inspection throughput (multiprotocol)[7] |
100 Mbps |
1 Gbps |
2 Gbps |
8 Gbps |
8 Gbps |
| IPsec VPN throughput (AES 450B UDP test)[8] |
100 Mbps |
1 Gbps |
2 Gbps |
7.5 Gbps |
7.5 Gbps |
| Connections per second |
12,500 |
120,000 |
250,000 |
450,000 |
450,000 |
| Concurrent sessions |
50,000 |
100,000 |
500,000 |
2,000,000 |
4,000,000 |
| IPsec VPN peers |
50 |
250 |
750 |
10,000 |
20,000 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
750 |
10,000 |
20,000 |
Table 6. ASAc on Catalyst 9300 App Hosting performance numbers
| ASAc on Catalyst 9K Performance* |
||||
| License Type |
100M (ASAc5) |
1G (ASAc10) |
1G (ASAc10) |
1G (ASAc10) |
| Catalyst Switch Model and ASAc vCPU/Mem |
9300 1vCPU/2GB |
9300 2vCPU/2GB |
9300X 2vCPU/4GB |
9300X 4vCPU/8GB |
| Stateful inspection throughput (maximum)6 |
100 Mbps |
1 Gbps |
1 Gbps |
1 Gbps |
| Throughput: FW (450B) |
100 Mbps |
500 Mbps |
700 Mbps
|
900 Mbps
|
| IPsec VPN throughput (AES 450B UDP test)8 |
100 Mbps |
250 Mbps |
450 Mbps |
600 Mbps |
| Connections per second |
1400 |
6000 |
8000 |
8000 |
| Concurrent sessions |
50,000 |
100,000 |
100,000 |
100,000 |
| IPsec VPN peers |
50 |
250 |
250 |
250 |
Table 7. Standalone ASAc on K8s and Docker
| Standalone ASAc |
||
| License Type |
100M (ASAc5) |
1G (ASAc10) |
| ASAc vCPU/Mem |
1vCPU/2GB |
1vCPU/2B |
| Stateful inspection throughput (maximum)6 |
100 Mbps |
1 Gbps |
| Throughput: FW (450B) |
100 Mbps |
500 Mbps |
| IPsec VPN throughput (AES 450B UDP test)8 |
100 Mbps |
250 Mbps |
| Connections per second |
1400 |
6000 |
| Concurrent sessions |
50,000 |
100,000 |
| VLANs |
25 |
50 |
| Bridge groups |
12 |
25 |
| IPsec VPN peers |
50 |
250 |
| Cisco AnyConnect or clientless VPN user sessions |
50 |
250 |
| Virtual CPU core allocation4 |
1 |
1 |
| Memory allocation4 |
2GB |
2GB |
Table 8. Secure Firewall ASA Virtual models and appropriate public cloud instance types
| Standard tier |
100M (ASAv5) |
1G (ASAv10)* |
2G (ASAv30)* |
10G (ASAv50)* |
20G (ASAv100)* |
Comments |
| Appropriate AWS instance types |
c5.large c4.large c3.large m4.large |
c5.large c4.large c3.large m4.large |
c5.xlarge c3.xlarge m4.xlarge c4.xlarge |
c5.2xlarge c4.2xlarge c3.2xlarge m4.2xlarge |
c5.4xlarge c5n.4xlarge |
Smallest supported instance type is large, which supports maximum throughput/limits of 1G entitlement. Auto Scale is supported |
| Recommended Azure VM types |
F4, F4s D3, D3_v2, DS3, DS3_v2 |
F4, F4s D3, D3_v2, DS3, DS3_v2 |
F4, F4s D3, D3_v2, DS3, DS3_v2 |
F8, F8s D8_v3 D4, D4_v2, DS4, DS4_v2 |
F16, F16s
D5, D5_v2, D16_v3, DS5, DS5_v2 (Version 9.15 and above only) |
Smallest supported instance size is F4/F4s, and supports max throughput/limits of 2G entitlement. Auto Scale is supported. Accelerated Networking is supported. |
| Recommended GCP machine types (Version 9.15 and above only) |
c2-standard-4 |
c2-standard-4 |
c2-standard-4 |
c2-standard-8 |
c2-standard-16 |
Smallest supported instance size is c2-standard-4, and supports max throughput/limits of 2G entitlement |
| Recommended OCI shape types (Version 9.15 and above only) |
VM.Standard2.4 |
VM.Standard2.4 |
VM.Standard2.4 |
VM.Standard2.8 |
VM.Standard2.8 |
Smallest supported instance size is VM.standard2.4, and supports max throughput/limits of 2G entitlement |
Table 9. Hypervisor and public cloud constraints
| Feature |
Vmware |
KVM |
Hyper-V |
AWS |
Azure |
GCP |
OCI |
| Hypervisor support |
ESXi 6.0, 6.5, 6.7, 7.0 |
Yes |
Yes |
AWS, AWS Gov Marketplace, AWS China (see VM instances supported in Table 9) |
Azure, Azure Gov Marketplace, Azure China (see VM instances supported in Table 10) |
GCP (see VM instances supported in Table 11) |
OCI (see VM instances supported in Table 12) |
| High availability |
Stateful active/standby |
|
No |
Stateless active/standby |
No |
No |
|
| Modes |
Routed and transparent |
|
Routed only |
Routed only |
Routed only |
Routed only |
|
Table 10. Maximum Cisco AnyConnect user sessions
| RAM (GB) |
Entitlement support |
|||||
| MIN |
MAX |
100M (ASAv5) |
1G (ASAv10)* |
2G (ASAv30)* |
10G (ASAv50)* |
20G (ASAv100)* |
| 2 |
<8 |
50 |
250 |
250 |
250 |
250 |
| 8 |
<16 |
50 |
250 |
750 |
750 |
750 |
| 16 |
<32 |
50 |
250 |
750 |
10K |
10K |
| 32 |
No max |
50 |
250 |
750 |
10K |
20K |
Table 11. AWS instance support
| Instance |
Attributes |
|
| vCPUs |
Memory (GB) |
|
| C5.large* |
2 |
4 |
| C5.xlarge* |
4 |
8 |
| C5.2xlarge* |
8 |
16 |
| C5.4xlarge** |
16 |
32 |
| C5n.large** |
2 |
5.25 |
| C5n.xlarge** |
4 |
10.5 |
| C5n.2xlarge** |
8 |
21 |
| C5n.4xlarge** |
16 |
42 |
| C4.large |
2 |
3.75 |
| C4.xlarge |
4 |
7.5 |
| C4.2xlarge* |
8 |
15 |
| C3.large |
2 |
3.75 |
| C3.xlarge |
4 |
7.5 |
| C3.2xlarge* |
8 |
15 |
| m4.large |
2 |
8 |
| m4.xlarge |
4 |
16 |
| m4.2xlarge* |
8 |
32 |
Table 12. Azure instance support
| Instance |
Attributes |
|
| vCPUs |
Memory (GB) |
|
| D3, D3_v2, DS3*, DS3_v2* |
4 |
14 |
| D4*, D4_v2*, DS4*, DS4_v2* |
8 |
28 |
| D5, DS5, D5_v2, DS5_v2** |
16 |
56 |
| D8_v3* |
8 |
32 |
| D16_v3** |
16 |
64 |
| F4*, F4s* |
4 |
8 |
| F8*, F8s* |
8 |
16 |
| F16, F16s** |
16 |
32 |
Table 13. GCP instance support*
| Instance |
Attributes |
|
| OCPU’s |
Memory (GB) |
|
| n1-standard-4 |
4 |
15 |
| c2-standard-4 n2-standard-4 |
4 |
16 |
| n2-highmem-4 |
4 |
32 |
| c2-standard-8 n2-standard-8 |
8 |
32 |
| n1-standard-8 |
8 |
30 |
| n1-highcpu-8 |
8 |
7.2 |
| n2-highcpu-8 |
8 |
8 |
| n2-highmem-8 |
8 |
64 |
| c2-standard-16 n2-standard-16 |
16 |
64 |
| n1-standard-16 |
16 |
60 |
| n1-highcpu-16 |
16 |
14.4 |
| n2-highcpu-16 |
16 |
16 |
| n2-highmem-16 |
16 |
128 |
Table 14. OCI instance support*
| Instance |
Attributes |
|
| vCPUs |
Memory (GB) |
|
| VM.Standard2.4 |
4 |
60 |
| VM.Standard2.8 |
8 |
120 |
Table 15. Ordering information: In Cisco Commerce Workspace (CCW) order the base selection (denoted by “K9” in the part number), followed by the desired license type
| Part number |
Description |
| L-ASAV5S-K9= |
Cisco 100 Mbps entitlement (ASAv5) selection(Perpetual License) |
| L-ASA-V-5S-K9= |
Cisco 100 Mbps entitlement (ASAv5) subscription |
| L-ASAV10S-K9= |
Cisco 1 Gbps entitlement (ASAv10) selection(Perpetual License) |
| L-ASA-V-10S-K9= |
Cisco 1 Gbps entitlement (ASAv10) subscription |
| L-ASAV30S-K9= |
Cisco 2 Gbps entitlement (ASAv30) selection(Perpetual License) |
| L-ASA-V-30S-K9= |
Cisco 2 Gbps entitlement (ASAv30) subscription |
| L-ASAV50S-K9= |
Cisco 10 Gbps entitlement (ASAv50) selection(Perpetual License) |
| L-ASA-V-50S-K9= |
Cisco 10 Gbps entitlement (ASAv50) subscription |
| L-ASA-V-100S-K9= |
Cisco 20 Gbps entitlement (ASAv100) subscription* |
Flexible payment solutions to help you achieve your objectives
Cisco Capital makes it easier to get the right technology to achieve your objectives, enable business transformation and help you stay competitive. We can help you reduce the total cost of ownership, conserve capital, and accelerate growth. In more than 100 countries, our flexible payment solutions can help you acquire hardware, software, services and complementary third-party equipment in easy, predictable payments. Learn more.