-
Cisco MDS 9000 Family Configuration Guide, Release 1.0(3a)
-
Index
-
Preface
-
Product Overview
-
Before You Begin
-
Initial Configuration
-
Configuring High Availability
-
Software Images
-
Managing Modules
-
Managing System Hardware
-
Configuring and Managing VSANs
-
Configuring Interfaces
-
Configuring Trunking
-
Configuring PortChannels
-
Configuring and Managing Zones
-
Managing FLOGI, Name Server, and RSCN Databases
-
Configuring System Security and AAA Services
-
Configuring Fibre Channel Routing Services and Protocols
-
Configuring IP Services
-
Configuring Call Home
-
Configuring Domain Parameters
-
Configuring Traffic Management
-
Configuring System Message Logging
-
Discovering SCSI Targets
-
Monitoring Network Traffic Using SPAN
-
Advanced Features and Concepts
-
Configuring Fabric Configuration Servers
-
Monitoring System Processes and Logs
-
Table Of Contents
Starting a Switch in the Cisco MDS 9000 Family
Preparing to Configure the Switch
Configuring Out-of-Band Management
In-Band Management Configuration
Assigning SNMP Switch Contact Information
Setting the Daylight Saving Time Adjustment
Configuring the Management Port
Formatting Flash Disks and File Systems
Working with Configuration Files
Guidelines for Creating and Using Configuration Files
Downloading Configuration Files to the Switch
From an External Flash (slot0:)
To an External CompactFlash Disk
Backing up the Current Configuration
Rolling Back to a Previous Configuration
Configuring Line Console Settings
Initial Configuration
This chapter describes how to initially configure switches so they can be accessed by other devices. This chapter includes the following sections:
•
Starting a Switch in the Cisco MDS 9000 Family
•
Configuring the Management Port
•
Formatting Flash Disks and File Systems
•
Working with Configuration Files
•
Configuring Line Console Settings
Starting a Switch in the Cisco MDS 9000 Family
The following procedure is a review of the tasks you should have completed during hardware installation, including starting up the switch. These tasks must be completed before you can configure the switch.
Step 1
Check that the switch is set for the correct AC (or DC) power voltages.
Refer to either the Cisco MDS 9200 Series Hardware Installation Guide or the Cisco MDS 9500 Series Hardware Installation Guide for correct power voltages.
Step 2
Connect the power cord(s) to the switch.
Step 3
Connect the console port to the switch.
Note
The console port is an asynchronous (async) serial port; any device connected to this port must be capable of asynchronous transmission.
Before connecting the console port, check the terminal documentation to determine the baud rate. The baud rate of the terminal must match the default baud rate (9600 baud) of the console port. Set up the terminal as follows (see the "Configuring Line Console Settings" section):
•
9600 baud
•
8 data bits
•
1 stop bit
•
No parity
Step 4
Power on the switch. The switch boots automatically.
Initial Setup Routine
The first time that you access a switch in the Cisco MDS 9000 Family, it runs a setup program that prompts you for the IP address and other configuration information necessary for the switch to communicate over the supervisor module Ethernet interface. This information is also required if you plan to configure and manage the switch.
Note
The IP address must first be set up in CLI when the switch is powered up for the first time so the Cisco MDS 9000 Fabric Manager can reach the switch.
Preparing to Configure the Switch
Before you configure a switch in the Cisco MDS 9000 Family for the first time, you need the following information:
•
Administrator password—You have the option to create a new login account or overwrite a preexisting account password.
•
SNMPv3 user name and authentication password.
•
SNMP community string.
•
Switch name—This is your switch prompt.
•
IP address for the switch's management interface—The management interface can be an out-of-band Ethernet interface or an in-band Fibre Channel interface.
•
Subnet mask for the switch's management interface.
•
The following IP addresses:
–
Destination prefix, destination prefix subnet mask, and next hop IP address, if you want to enable IP routing. Also, provide the IP address of the default network.
–
Otherwise, provide an IP address of the default gateway.
•
DNS IP address (optional).
•
Default domain name (optional).
•
SSH service on the switch—if you wish to enable this service, then select the type of SSH key (dsa/rsa/rsa1) and number of key bits (768 to 2048).
•
NTP server IP address (optional).
Note
Be sure to configure the IP routing, the IP default network address, and the IP default gateway address to enable SNMP access. If IP routing is enabled, the switch uses the IP route and the default network IP address. If IP routing is disabled, the switch uses the default gateway IP address.
Default Login
All Cisco MDS 9000 family switches have the network administrator as a default user (admin) and a default password (admin). You can change the default password, if required, during the initial setup process. You cannot change the default user at any time.
During the initial setup process, you have the option to configure one additional user in the network administrator role. See the "Role-Based Authorization" section for information of default roles and permissions.
If you change the administrator password during the initial setup process and subsequently forget this new password, you have the option to recover this password (see the "Recovering Administrator Password" section).
Setup Options
The setup scenario differs based on the subnet to which you are adding the new switch. You must configure a switch in the Cisco MDS 9000 Family with an IP address to enable management connections from outside of the switch.
Note
Some concepts like out-of-band management and in-band management are briefly explained here. These concepts are explained in more detail in subsequent chapters.
•
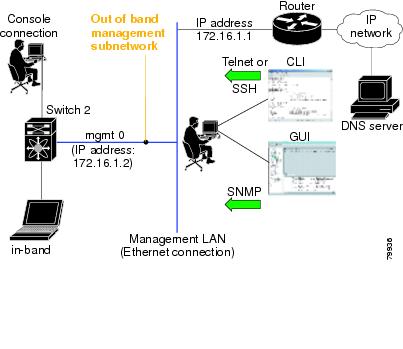
Out-of-band management—This feature provides a connection to the network through a supervisor module front panel Ethernet port (see Figure 3-1).
•
In-band management—This feature provides IP over Fibre Channel (IPFC) to manage the switches. The in-band management feature is transparent to the network management system (NMS). Instead of conventional Ethernet physical media, switches in the Cisco MDS 9000 Family use IPFC as the transport mechanism (see Figure 3-1 and "Configuring IP Services").
Figure 3-1 Management Access to Switches
Assigning Setup Information
This section describes how to initially configure the switch for both out-of-band and in-band management.
Note
Type Ctrl-c at any prompt to skip the remaining configuration options and proceed with what is configured until that point.
Tip
If you do not wish to answer a previously-configured question, or if you wish to skip answers to any questions press Enter. If a default answer is not available (for example switch name), the switch uses what is previously configured and skips to the next question.
Configuring Out-of-Band Management
Note
If you wish to configure both in-band and out-of-band configuration together, enter Yes in both Step 11 and Step 12 in the following procedure.
To configure the switch for first time out-of-band access, follow these steps:
Step 1
Power on the switch. Switches in the Cisco MDS 9000 Family boot automatically.
Step 2
Enter yes to enter the setup mode.
This setup utility will guide you through the basic configuration ofthe system. Setup configures only enough connectivity for managementof the system.Press Enter incase you want to skip any dialog. Use ctrl-c at anytimeto skip away remaining dialogs.Would you like to enter the basic configuration dialog (yes/no): yesThe setup utility guides you through the basic configuration process. Type Ctrl-c at any prompt, to end the configuration process.
Step 3
Enter the new password for the administrator (admin is the default):
Enter the password for admin: adminStep 4
Enter yes (no is the default), to create additional accounts.
Create another login account (yes/no) [n]: yesWhile configuring your initial setup, you can create an additional user account (in the network-admin role) besides the administrator's account. See the "Role-Based Authorization" section for information of default roles and permissions.
a.
Enter the user login ID.
Enter the user login ID: user_nameb.
Enter the user password.
Enter the password for user_name: user-passwordStep 5
Enter yes (yes is the default), if you wish to create an SNMPv3 account.
Configure SNMPv3 Management parameters (yes/no) [y]: yesa.
Enter the user name (admin is the default).
SNMPv3 user name [admin]: adminb.
Enter the SNMPv3 password (minimum of 8 characters).
SNMPv3 user authentication password : admin_pass
Note
If this password contains less than eight characters, you must enter a new password. The same password is also used for the SNMPv3 privacy.
By default if the admin password is at least 8 characters, then the SNMP authentication password will be same as admin password (at least 8 characters). If the admin password is less than 8 characters, then you need to provide a new password for SNMP.
The admin password can have a minimum of 1 character, but the SNMP authentication password must have a minimum of 8 characters.Step 6
Enter yes (no is the default) to configure read-only or read-write SNMP community string.
Configure read-only SNMP community string (yes/no) [n]: yesa.
Enter the SNMP community string.
SNMP community string: snmp_communityStep 7
Enter a name for the switch.
Note
The switch name is limited to 32 alphanumeric characters.
Enter the switch name: switch_nameStep 8
Enter yes (yes is the default) to configure out-of-band management.
Continue with Out-of-band (mgmt0) management configuration? [yes/no]: yesa.
Enter the mgmt0 IP address.
Mgmt0 IP address: ip_addressb.
Enter the mgmt0 subnet mask.
Mgmt0 IP netmask: subnet_maskStep 9
Enter no (no is the default) at the in-band management configuration prompt.
Continue with in-band (VSAN1) management configuration? (yes/no) [no]: noStep 10
Enter yes (yes is the default) to enable IP routing and default-gateway capabilities.
Enable the ip routing capabilities? (yes/no) [y]: yesa.
Enter yes (yes is the default) to configure a static route (recommended).
Configure static route: (yes/no) [y]: yesa.
Enter the destination prefix.
Destination prefix: dest_prefixb.
Type the destination prefix mask.
Destination prefix mask: dest_maskc.
Type the next hop ip address.
Next hop ip address: next_hop_address
Note
Be sure to configure the IP routing, the IP default network address, and the IP default gateway address to enable SNMP access. If IP routing is enabled, the switch uses the IP route and the default network IP address. If IP routing is disabled, the switch uses the default gateway IP address.
b.
Enter yes (yes is the default) to configure the default-network (recommended).
Configure the default-network: (yes/no) [y]: yesa.
Enter the default-network IP address.
Note
The default network address is the destination prefix provided in Step 10 a above.
Default network IP address: dest_prefixc.
Enter yes (yes is the default) to configure the default-gateway (recommended).
Configure the default-gateway: (yes/no) [y]: yesa.
Enter the default-gateway IP address.
IP address of the default-gateway: default_gatewayStep 11
Enter yes (yes is the default) to configure the DNS IP address.
Configure the DNS IP address? (yes/no) [y]: yesa.
Enter the DNS IP address.
DNS IP address: name_serverStep 12
Enter yes (default is no) to configure the default domain name.
Configure the default domain name? (yes/no) [n]: yesa.
Enter the default domain name.
Default domain name: domain_nameStep 13
Enter yes (yes is the default), to enable Telnet service.
Enable the telnet service? (yes/no) [y]: yesStep 14
Enter yes (no is the default) to enable the SSH service.
Enabled SSH service? (yes/no) [n]: yesStep 15
Enter the SSH key type (see Generating an SSH Host Key Pair) you would like to generate.
Type the SSH key you would like to generate (dsa/rsa/rsa1)? dsaStep 16
Enter the number of key bits within the specified range.
Enter the number of key bits? (512 to 2048): 768Step 17
Enter yes (no is the default) to configure the NTP server.
Configure NTP server? (yes/no) [n]: yesa.
Enter the NTP server IP address.
NTP server IP address: ntp_server_IP_addressStep 18
Enter shut (shut is the default) to configure the default switchport interface to the shut state.
Configure default switchport interface state (shut/noshut) [shut]: shutStep 19
Enter on (on is the default) to configure the switchport trunk mode.
Configure default switchport trunk mode (on/off/auto) [on]: onStep 20
Enter permit (deny is the default) to permit a default zone policy.
Configure default zone policy (permit/deny) [deny]: permitPermits traffic to flow to all members of the default zone.
Step 21
Review and edit the configuration that you have just entered.
Step 22
Enter no (no is the default) if you are satisfied with the configuration.
The following configuration will be applied:username admin password admin_pass role network-adminusername user_name password user_pass role network-adminsnmp-server user admin network-admin auth md5 admin_pass priv admin_passsnmp-server community snmp_community roswitchname switchinterface mgmt0ip address ip_address subnet_maskno shutdownip routingip route dest_prefix dest_mask dest_addressip default-network dest_prefixip default-gateway default_gatewayip name-server name_serverip domain-name domain_nametelnet server enablessh key dsa 768 forcessh server enablentp server ntp_serversystem default switchport shutdownsystem default switchport trunk mode onno zone default-zone permit vsan 1-4093Would you like to edit the configuration? (yes/no): noStep 23
Enter yes (yes is default) to use and save this configuration:
Use this configuration and save it? (yes/no):yes
CautionIf you do not save the configuration at this point, none of your changes will be updated the next time the switch is rebooted. Ensure to type yes in order to save the new configuration. This will ensure that the kickstart and system boot images are also automatically configured (see "Software Images").
In-Band Management Configuration
The in-band management logical interface is VSAN 1. This management interface uses the Fibre Channel infrastructure to transport IP traffic. An interface for VSAN 1 is created on every switch in the fabric. Each switch should have it's VSAN 1 interface configured with an IP address in the same subnetwork. A default route, pointing to the switch that provides access to the IP network should be configured on every switch in the Fibre Channel fabric (see "Configuring and Managing VSANs").
Note
If you wish to configure both in-band and out-of-band configuration together, enter Yes in both Step 11 and Step 12 in the following procedure.
To configure a switch for first time in-band access, follow these steps:
Step 1
Power on the switch. Switches in the Cisco MDS 9000 Family boot automatically.
Step 2
Enter yes to enter the setup mode.
---- Basic System Configuration Dialog ----This setup utility will guide you through the basic configuration ofthe system. Setup configures only enough connectivity for managementof the system.Press Enter incase you want to skip any dialog. Use ctrl-c at anytimeto skip away remaining dialogs.Would you like to enter the basic configuration dialog (yes/no): yesThe setup utility guides you through the basic configuration process. Type Ctrl-c from any prompt, to abort the configuration process.
Step 3
Enter the new password for the administrator.
Enter the password for admin: adminStep 4
Enter no (no is the default), if you do not wish to create other additional accounts.
Create another login account (yes/no) [no]: noStep 5
Enter yes (yes is the default), if you wish to create a SNMPv3 account.
Configure SNMPv3 Management parameters (yes/no) [y]: yesa.
Enter the user name.
SNMPv3 user name [admin]: user_nameBy default, the SNMP user name is admin.
b.
Enter the SNMPv3 password (minimum of 8 characters).
SNMPv3 user authentication password [admin_pass]: admin_pass
Note
If this password contains less than eight characters, you must enter a new password. The same password is also used for the SNMPv3 privacy.
By default if the admin password is at least 8 characters, then the SNMP authentication password will be same as admin password (at least 8 characters). If the admin password is less than 8 characters, then you need to provide a new password for SNMP.
The admin password can have a minimum of 1 character, but the SNMP authentication password must have a minimum of 8 characters.Step 6
Configure read-only or read-write SNMP community string.
a.
Enter no (no is the default) to avoid configuring read-only SNMP community string.
Configure read-only SNMP community string (yes/no) [n]: nob.
Enter no (no is the default) to configure read-only SNMP community string.
Configure read-only SNMP community string (yes/no) [n]: yesc.
Enter the SNMP community string.
SNMP community string: snmp_communityStep 7
Enter a name for the switch.
Note
The switch name is limited to 32 alphanumeric characters.
Enter the switch name: switch_nameStep 8
Enter no (yes is the default) at the configuration prompt to configure out-of-band management.
Continue with Out-of-band (mgmt0) management configuration? [yes/no]: noStep 9
Enter yes (no is the default) at the in-band management configuration prompt.
Continue with in-band (VSAN1) management configuration? (yes/no) [no]: yesa.
Enter the VSAN 1 IP address.
VSAN1 IP address: ip_addressb.
Enter the subnet mask.
VSAN1 IP net mask: subnet_maskStep 10
Enter yes (yes is the default) to enable the default-gateway capabilities.
Enable ip routing capabilities? (yes/no) [y]: yesa.
Enter no (yes is the default) to configure a static route.
Configure static route: (yes/no) [y]: nob.
Enter yes (yes is the default) to configure the default network.
Configure the default-network: (yes/no) [y]: noc.
Enter yes (yes is the default) to configure the default gateway.
Configure the default-gateway: (yes/no) [y]: yesa.
Enter the default-gateway IP address.
IP address of the default-gateway: default_gatewayStep 11
Enter No (yes is the default) to configure the DNS IP address.
Configure the DNS IP address? (yes/no) [y]: noStep 12
Enter no (no is the default) to skip the default domain name configuration.
Configure the default domain name? (yes/no) [n]: noStep 13
Enter no (yes is the default), to disable Telnet service.
Enable the telnet service? (yes/no) [y]: noStep 14
Enter yes (no is the default) to enable the SSH service.
Enabled SSH service? (yes/no) [n]: yesStep 15
Enter the SSH key type (see Generating an SSH Host Key Pair) you would like to generate.
Type the SSH key you would like to generate (dsa/rsa/rsa1)? rsaStep 16
Enter the number of key bits within the specified range.
Enter the number of key bits? (512 to 1024): 1024Step 17
Enter no (no is the default) to configure the NTP server.
Configure NTP server? (yes/no) [n]: noStep 18
Enter noshut (shut is the default) to configure the default switchport interface to the up state.
Configure default switchport interface state (shut/noshut) [shut]: noshutStep 19
Enter auto (on is the default) to configure the switchport trunk mode automatically.
Configure default switchport trunk mode (on/off/auto) [on]: autoStep 20
Enter deny (deny is the default) to deny a default zone policy.
Configure default zone policy (permit/deny) [deny]: denyStep 21
Review and edit the configuration that you have just entered.
Step 22
Enter no (no is the default) if you are satisfied with the configuration.
The following configuration will be applied:username admin password admin_pass role network-adminsnmp-server user snmp_user network-admin auth md5 snmp_pass priv snmp_passsnmp-server community snmp_community rwswitchname switchinterface vsan1ip address ip_address subnet_maskno shutdownip default-gateway default_gatewayno telnet server enablessh key rsa 1024 forcessh server enableno system default switchport shutdownsystem default switchport trunk mode autono zone default-zone deny vsan 1-4093Would you like to edit the configuration? (yes/no): noStep 23
Enter yes (yes is default) to use and save this configuration.
Use this configuration and save it? (yes/no):yes
CautionIf you do not save the configuration at this point, none of your changes will be updated the next time the switch is rebooted. Ensure to type yes in order to save the new configuration. This will ensure that the kickstart and system boot images are also automatically configured (see "Software Images").
Using the setup Command
If you wish to make changes to the initial configuration at a later time, you can issue the setup command in EXEC mode.
switch# setup---- Basic System Configuration Dialog ----This setup utility will guide you through the basic configuration ofthe system. Setup configures only enough connectivity for managementof the system.*Note: setup always assumes a predefined defaults irrespectiveof the current system configuration when invoked from CLI.Press Enter incase you want to skip any dialog. Use ctrl-c at anytimeto skip away remaining dialogs.Would you like to enter the basic configuration dialog (yes/no): yesThe setup utility guides you through the basic configuration process.
Assigning a Switch Name
Each switch in the fabric requires a unique name. You can assign names to easily identify the switch by its physical location, its SAN association, or the organization to which it is deployed. The assigned name is displayed in the command-line prompt.
Note
The switch name is limited to 32 alphanumeric characters.
This guide refers to a switch in the Cisco MDS 9000 Family as switch, and uses the switch# prompt.
To change the name of the switch, follow these steps:
Assigning SNMP Switch Contact Information
Use the snmp-server command to set the contact information, switch location, and switch name. They are each limited to 32 characters (without spaces). Use the no form of the command to remove the system contact information. For more information on other snmp-server commands see the "SNMP Security" section
To configure contact information, follow these steps:
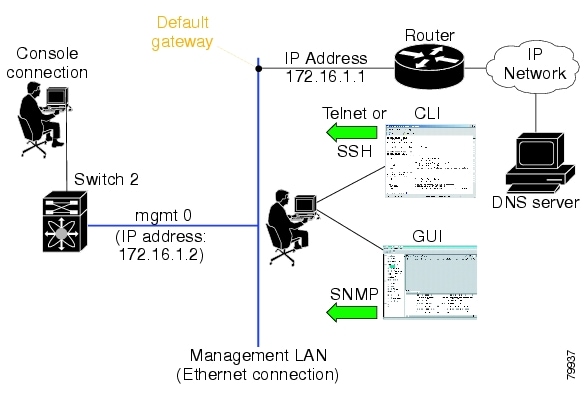
Accessing the Switch
After initial configuration, you can access the switch in one of three ways (see Figure 3-2):
•
In-band IP (IPFC) access—You can use Telnet or SSH to access a switch in the Cisco MDS 9000 Family or use SNMP to connect to a Cisco MDS 9000 Fabric Manager GUI.
•
Out-of-band (10/100BASE-T Ethernet) access—You can use Telnet or SSH to access a switch in the Cisco MDS 9000 Family or use SNMP to connect to a Cisco MDS 9000 Fabric Manager GUI.
Note
To use the Cisco Fabric Manager, refer to the Cisco MDS 9000 Family Fabric Manager User Guide.
•
Serial console access—You can use a serial port connection to access the CLI.
Figure 3-2 Switch Access Options
Where Do You Go Next?
After reviewing the default configuration, you can change it or perform other configuration or management tasks. The initial setup can only be performed at the CLI. However, you can continue to configure other software features, or access the switch after initial configuration by using either the CLI or the Element Manager and Fabric Manager GUIs.
To use the Cisco MDS 9000 Fabric Manager, refer to the Cisco MDS 9000 Family Fabric Manager User Guide.
Verifying the Module Status
Before you begin configuring the switch, you need to ensure that the modules in the chassis are functioning as designed. To verify the status of a module at any time, issue the show module command in EXEC mode. A sample output of the show module command follows:
switch# show moduleMod Ports Module-Type Model Status--- ----- ------------------------------- ------------------ ------------3 16 1/2 Gbps FC Module DS-X9016 ok5 0 Supervisor/Fabric-1 DS-X9530-SF1-K9 active *9 16 1/2 Gbps FC Module DS-X9016 okMod Sw Hw World-Wide-Name(s) (WWN)--- ----------- ------ --------------------------------------------------3 1.0(1.22) 0.0 20:81:00:05:30:00:12:5e to 20:90:00:05:30:00:12:5e5 1.0(1.22) 0.0 --9 1.0(1.22) 0.0 22:01:00:05:30:00:12:5e to 22:10:00:05:30:00:12:5eMod MAC-Address(es) Serial-Num--- -------------------------------------- ----------3 00-05-30-00-76-26 to 00-05-30-00-76-2a5 00-05-30-00-53-ae to 00-05-30-00-53-b29 00-05-30-00-64-b6 to 00-05-30-00-64-ba* this terminal sessionIf the status is OK or active, you can continue with your configuration (see "Managing Modules").
Configuring Time
Switches in the Cisco MDS 9000 Family use Coordinated Universal Time (UTC), which is the same as Greenwich Mean Time (GMT). To change the default time on the switch, issue the clock command from EXEC mode.
switch# clock set <HH:MM:SS> <DD> <Month in words> <YYYY>For example:
switch# clock set 12:07:50 23 September 2002Mon Sep 23 12:07:50 UTC 2002HH represents hours in military format (15 for 3 p.m.), MM is minutes (58), SS is seconds (09), DD is the date (02), Month is the month in words (August), and YYYY is the year (2002).
Note
The clock command changes are saved across system resets.
Configuring the Time Zone
You can specify a time zone for the switch to display the time.
To specify the local time without the daylight savings feature, follow these steps:
Setting the Daylight Saving Time Adjustment
Following U.S. standards, you can have the switch advance the clock one hour at 2:00 a.m. on the first Sunday in April and move back the clock one hour at 2:00 a.m. on the last Sunday in October. You can also explicitly specify the start and end dates and times and whether or not the time adjustment recurs every year.
To enable the daylight saving time clock adjustment according to the U.S. rules, follow these steps:
NTP Configuration
A Network Time Protocol (NTP) server provides a precise time source (radio clock or atomic clock) to synchronize the system clocks of network devices. NTP is transported over User Datagram Protocol UDP/IP. All NTP communications use UTC. An NTP server receives its time from a reference time source, such as a radio clock or atomic clock, attached to the time. NTP distributes this time across the network.
In a large enterprise network, having one time standard for all network devices is critical for management reporting and event logging functions when trying to correlate interacting events logged across multiple devices. Many enterprise customers with extremely mission-critical networks maintain their own stratum-1 NTP source.
Time synchronization happens when several frames are exchanged between clients and servers. The switches in client mode know the address of one or more NTP servers. The servers act as the time source and receive client synchronization requests.
By configuring an IP address as a peer, the switch will obtain and provide time as required. The peer is capable of providing time on its own and is capable of having a server configured. If both these instances point to different time servers, your NTP service will be more reliable. Thus, even if the active server link is lost, you can still maintain the right time due to the presence of the peer.
Tip
If an active server fails, a configured peer helps in providing the NTP time. Provide a direct NTP server association and configure a peer to ensure backup support if the active server fails.
If you only configure a peer, the most accurate peer takes on the role of the NTP server and the other peer(s) act as a peer(s). Both machines end at the right time if they have the right time source or if they point to the right NTP source.
To configure NTP in a server association, follow these steps:
NTP Configuration Guidelines
The following guidelines apply to all NTP configurations:
•
You should have a peer association with another switch only when you are sure that your clock is reliable (which means that you are a client of a reliable NTP server).
•
Though a peer configured alone, will be the most accurate peer taking on the role of a server, the configured peer should be used more as a back-up support. If more than one server is present, you can have several switches point to one server, and the remaining to the another server, and then configure peer association between these two sets. This forces the clock more reliable.
•
If you only have one server, it's better for all the switches have a client association with that server.
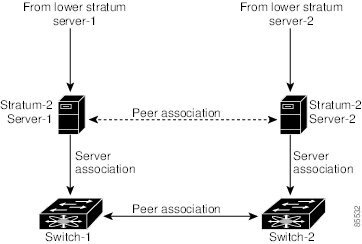
If the network is configured robustly, even a server down time will not affect well-configured switches in the network. Figure 3-3 displays a network with two NTP stratum 2 servers and two switches.
Figure 3-3 NTP Peer and Server Association
In this configuration, the switches were configured as explained below:
•
Stratum 2 Server 1
–
IP address -10.10.10.10
–
Stratum-2 Server-2
–
IP address -10.10.10.9
•
Switch 1
–
Switch ip address -10.10.10.1
•
NTP Configuration
–
NTP server 10.10.10.10
–
NTP peer 10.10.10.2
•
Switch 2
–
Switch ip address -10.10.10.2
–
NTP Configuration
–
NTP server 10.10.10.9
–
NTP peer 10.10.10.1
Configuring the Management Port
The management port on the switch allows multiple simultaneous Telnet or SNMP sessions.
You can remotely configure the switch through the management port, but first you must configure some IP parameters (IP address, subnet mask) so that the switch is reachable. You can manually configure the management port interface from the CLI.
Note
Before you begin to configure the management port interface manually, obtain the switch's IP address and IP subnet mask. Also make sure the console cable is connected to the console port.
To obtain remote management access using Telnet (CLI) or SNMP (GUI), follow these steps:
In some cases, a switch interface might be administratively shut down. You can check the status of an interface at any time by using the show interface command.
The management port (mgmt0) is autosensing and operates as full duplex mode and 100 Mbps speed. The speed and mode cannot be configured.
Note
You need to explicitly configure a default gateway to connect to the switch and send IP packets or add a route for each subnet.
Configuring Default Gateways
The supervisor module sends IP packets with unresolved destination IP addresses to the default gateway (see Figure 3-4).
Figure 3-4 Default Gateway
To configure the IP address of the default gateway, follow these steps:
Step 1
Enters configuration mode.
Step 2
Configures the 172.16.1.1 IP address.
Disabling a Telnet Server
The Telnet server is enabled by default on all switches in the Cisco MDS 9000 Family. If you require a secure SSH connection, you need to disable the default Telnet connection and then enable the SSH connection (see the "Enabling SSH Service" section).
Note
For information on connecting a terminal to the supervisor module console port, refer to the Cisco MDS 9200 Series Hardware Installation Guide or the Cisco MDS 9500 Series Hardware Installation Guide.
Make sure the terminal is connected to the switch and that the switch and terminal are on. To allow Telnet connections to the switch, follow these steps:
About Flash Devices
Every switch in the Cisco MDS 9000 Family contains one internal bootflash: that resides in the supervisor or switching module. Cisco MDS 9500 Series directors contain an additional external CompactFlash called slot0: (see Figure 3-5 and Figure 3-6).
Figure 3-5 Flash Devices in the Cisco MDS 9000 Supervisor Module
Figure 3-6 External CompactFlash in the Cisco MDS 9000 Supervisor Module
The external CompactFlash, an optional device for MDS 9500 series Directors, can be used for storing software images, logs and core dumps.
Formatting Flash Disks and File Systems
By formatting a flash disk or a file system, you are essentially clearing out the contents of the disk or the file system and restoring it to its factory-shipped state.
Initializing bootflash:
When a switch is shipped, the init system command is already performed and you do not need to issue it again. Initializing the switch resets the entire internal disk and erases all data in the bootflash: partition. The internal disk is composed of several file systems with bootflash: being one of them. All files in bootflash: are erased and you must download the system and kickstart images again. If you issue an init system command at any time, you don't have to format the bootflash: again since bootflash: is automatically formatted.
Note
The init system command also installs a new loader from the existing (running) kickstart image. You can access this command from the switch(boot)# prompt (see "Software Images").
If bootflash: is found corrupted during a boot sequence, you will see the following message:
ERROR:bootflash: has unrecoverable error; please do "format bootflash:"Use the format bootflash: command to only format the bootflash: filesystem. You can access the format bootflash: command from either the switch# or the switch(boot)# prompts.
If you issue the format bootflash: command, you need to download the kickstart and system images again.
Formatting Slot0:
Be sure to format an external CompactFlash device before using it to save files or images.
You can verify if the external CompactFlash device is formatted by inserting it into slot0: and issuing the dir slot0: command.
•
If the external CompactFlash device is already formatted, you can see file system usage information (along with any existing files).
•
If the external CompactFlash device is unformatted (corrupted), you will see the following message:
Device unavailableIn this case, you need to format the CompactFlash device using the format slot0: command.
Note
The slot0: file system cannot be accessed from the standby the loader> prompt or the switch(boot) prompt, if the disk is inserted after booting the switch.
Working with Configuration Files
This section describes how to work with configuration files and has the following topics:
•
Guidelines for Creating and Using Configuration Files
•
Downloading Configuration Files to the Switch
Guidelines for Creating and Using Configuration Files
Configuration files can contain some or all of the commands needed to configure one or more switches. For example, you might want to download the same configuration file to several switches that have the same hardware configuration so that they have identical module and port configurations.
Certain commands must be followed by a blank line in the configuration file. Without these blank lines, the commands might disconnect your Telnet session. Before disconnecting a session, the switch prompts you for confirmation. The blank line acts as a carriage return, which indicates a negative response to the prompt retaining the Telnet session.
Include a blank line after the following command in a configuration file:
interface mgmt0 disableViewing Configuration Files
To view the running configuration file, use the show running-config command:
switch# show running-configBuilding Configuration ...interface port-channel 98interface fc1/1interface fc1/2interface mgmt0ip address 172.22.95.112 255.255.255.0no shutdownvsan databasevsan 2clock summer-time Pacific 1 Sun Apr 02:00 5 Sun Oct 02:00 60switchname switch112To view the startup configuration file, use the show startup-config command:
switch# show startup-configinterface port-channel 98interface fc1/1channel-group 98 forceno shutdowninterface mgmt0ip address 172.22.95.112 255.255.255.0boot system system-237; ep-41boot kickstart boot-237 ep-41ip domain-name cisco.comDownloading Configuration Files to the Switch
You can configure a switch in the Cisco MDS 9000 Family by using configuration files you create or download from another switch. In addition, you can store configuration files on a bootflash device on the supervisor module and you can configure the switch using a configuration stored on an external CompactFlash disk.
Before you begin downloading a configuration file using a remote server, do the following:
•
Ensure the switch has a route to the remote server. The switch and the remote server must be in the same subnetwork if you do not have a router or default gateway to route traffic between subnets. Check connectivity to the remote server using the ping command.
•
Ensure the configuration file to be downloaded is in the correct directory on the remote server.
•
Ensure that the permissions on the file are set correctly. Permissions on the file should be world-read.
Note
See the "Copying Files" section.
From a Remote Server
To configure a switch in the Cisco MDS 9000 Family using a configuration file downloaded from a remote server using TFTP, FTP, SCP, or SFTP, follow these steps:
Step 1
Log into the switch through the console port or through a Telnet session.
Step 2
Configure the switch using the configuration file downloaded from the remote server using the
copy <scheme> :// <server address> system: running-config command.The scheme is TFTP, FTP, SCP, or SFTP.
Step 3
Specify the IP address or host name of the remote server and the name of the file to download.
The configuration file downloads and the commands are executed as the file is parsed line by line.
Use the following command to download a configuration file from a remote server to the running configuration.
switch# copy <scheme>://<url> system:running-configUse the following command to download a configuration file from a remote server to the startup configuration.
switch# copy <scheme>://<url> nvram:startup-configFrom an External Flash (slot0:)
Note
The physical media must be inserted into slot0: after you login to the switch.
To configure a switch in the Cisco MDS 9000 Family using a configuration file stored on an external CompactFlash disk, follow these steps:
Step 1
Log into the switch through the console port or through a Telnet session.
Step 2
Locate the configuration file using the cd and dir commands. (See the "Copying Files" section.)
Step 3
Configure the switch using the configuration file stored on the external CompactFlash disk using the copy <source file> system:running-config command.
The commands are executed as the file is parsed line by line.
Use the following command to download a configuration file from an external CompactFlash to the running configuration.
switch copy slot0:dns-config.cfg system:running-configUse the following command to download a configuration file from an external CompactFlash to the startup configuration.
switch copy slot0:dns-config.cfg nvram:startup-configTo a Remote Server
To save a configuration file to a remote server like TFTP, FTP, SCP, or SFTP, follow these steps:
Step 1
Log into the switch through the console port or through a Telnet session.
Step 2
Save the configuration using the copy system: running-config <scheme> :// <url> command.
Scheme can be TFTP, FTP, SCP, or SFTP.
Step 3
Specify the IP address or host name of the remote server and the name of the file to download.
The configuration file is saved to the remote server.
Use the following command to save a running configuration file to a remote server:
switch# copy system:running-config <scheme>://<url>Use the following command to save a startup configuration file to a remote server
switch# copy nvram:startup-config <scheme>://<url>To an External CompactFlash Disk
To save a configuration file on an external CompactFlash disk, follow these steps:
Step 1
Log into the switch through the console port or through a Telnet session.
Step 2
Locate the configuration file using the cd and dir commands. (See the "Copying Files" section.)
Step 3
Save the configuration file using the copy system:running-config <source file> command.
The configuration file is saved to the CompactFlash disk.
Use the following command to save a running configuration file to an external CompactFlash disk.
switch# copy system:running-config slot0:dns-config.cfgUse the following command to save a startup configuration file to an external CompactFlash disk.
switch# copy system:startup-config slot0:dns-config.cfgSaving the Configuration
After you have created a configuration, you save the configuration using the following copy command:
switch# copy system:running-config nvram:startup-configThe copy running-config startup-config command is an alias to the previous command and is used frequently throughout this guide.
Copying Files
The syntax for the copy command follows and is explained in Table 3-1.
switch# copy <scheme>://<username@><server>/<file name> <scheme>://<username@><server>/<file name>
Table 3-1 copy Command Syntax
bootflash
active-sup
standby-supUser-specified
slot0
—
User-specified
volatile
—
User-specified
nvram
—
startup-config or snapshot-config
system
—
running-config
tftp1
IP address or DNS name
User-specified
ftp
scp (secure copy)
sftp
core
—
Process identifier number
1 When downloading and uploading files, a TFTP limitation restricts a TFTP client to a 32 MB file size and some TFTP servers to a 16 MB file size.
•
This example shows how to copy a file from the active supervisor module's (sup-1 in slot 5) bootflash to the standby supervisor module's (sup-2 in slot 6) bootflash.
switch# copy bootflash:system_imgage bootflash://sup-2/system_image
Note
Do not copy a file from an external source directly to the standby supervisor. Copy the external source to the active supervisor, and then copy the saved file to the standby supervisor.
•
This example shows how to overwrite the contents of an existing configuration in NVRAM.
switch# copy nvram:snapshot-config nvram:startup-config Warning: this command is going to overwrite your current startup-config. Do you wish to continue? {y/n} [y] y•
This example shows how to create a running configuration copy in bootflash.
switch# copy system:running-config bootflash:my-config•
This example shows how to copy a system image file from the TFTP server to bootflash.
switch# copy tftp://172.16.10.100/system-237.img bootflash:system-237.img•
This example shows how to copy a script file from the SFTP server to volatile.
switch# copy sftp://172.16.10.100/myscript.txt volatile:myscript.txt
Note
Use the show version image command to verify if the downloaded images are valid.
Backing up the Current Configuration
Before installing or migrating to any software configuration, back up the startup configuration.
•
You can create a snapshot of the startup configuration in a predefined location on the switch (binary file).
switch# copy nvram:startup-config nvram:snapshot-config•
This example shows how to backup the startup configuration copy in the bootflash: file system (ASCII file).
switch# copy nvram:startup-config bootflash:my-config•
This example shows how to backup the startup configuration to the TFTP server (ASCII file).
switch# copy nvram:startup-config copy tftp://172.16.10.100/my-config•
This example shows how to backup the running configuration to the bootflash: file system (ASCII file).
switch# copy system:running-config bootflash:my-configRolling Back to a Previous Configuration
All switch configurations reside in the internal bootflash: file system. If your internal bootflash: file system is corrupted, you could potentially lose your configuration. Save and back up your configuration file periodically.
•
This example shows how to roll back to a snapshot copy of a previously saved running configuration (binary file).
switch# copy nvram:snapshot-config nvram:startup-config
Note
You can issue a rollback command only when a snapshot is already created (see the "Each time a copy running-config startup-config command is issued a binary file is created and the ASCII file is updated. A valid binary configuration file reduces the overall boot time significantly. A binary file cannot be uploaded, but its contents can be used to overwrite the existing startup configuration. The write erase command clears the binary file to match the new system image." section). Otherwise, you will receive the No snapshot-config found error message.
•
This example shows how to roll back to a configuration copy that was previously saved in the bootflash: file system (ASCII file).
switch# copy bootflash:my-config nvram:startup-config•
This example shows how to roll back to a configuration copy that was previously saved in a TFTP server (ASCII file).
switch# copy tftp://172.16.10.100/my-config nvram:startup-config
Note
Each time a copy running-config startup-config command is issued a binary file is created and the ASCII file is updated. A valid binary configuration file reduces the overall boot time significantly. A binary file cannot be uploaded, but its contents can be used to overwrite the existing startup configuration. The write erase command clears the binary file to match the new system image.
Deleting Files
To delete files on a Flash device, follow these steps:
Step 1
Deletes files from a directory
Step 2
Verifies the files are deleted.
•
This example shows how to delete a file from the bootflash: directory (assuming you are already in the bootflash: directory):
switch# delete dns_config.cfg•
This example shows how to delete a file from an external CompactFlash (slot0):
switch# delete slot0:dns_config.cfg•
This example deletes the file named test from the Flash card inserted in slot 0.
switch# delete slot0:test Delete slot0:test? [confirm]•
This example deletes the entire my-dir directory and all its contents:
switch# delete bootflash:my-dirConfiguring Line Console Settings
Console ports on Cisco switches are set up for quick and easy access through any standard RS-232 data terminal equipment (DTE) device.
You can perform the configuration specified in this section only if you are connected to the serial console.
Note
If you plan on connecting a modem to the console port of a switch in the Cisco MDS 9000 Family, first refer to the Console Port Issues section of the Modem-Router Connection Guide (www.cisco.com).
Console Port Speed
The default console baud rate is 9600 baud. The valid range is between 110 and 115,200 bps—110, 150, 300, 600, 1200, 2400, 4800, 9600, 19200, 28800, 38400, 57600, 115200. Be sure to specify one of these exact values.
For the purposes of this document, the default console port speed of 9600 baud is assumed.
CautionThe console baud rate automatically reverts to the default rate (9600) after any BIOS upgrade.
To configure console port speed, follow these steps:
If you specify an invalid speed, you will receive the following error message:
switch(config-console)# speed 111Error: 111 is not supported speedSupported speed are 110, 150, 300,2400, 4800, 9600, 19200, 28800, 38400, 57600 (56K), and 115200Device Control Parameters
Be sure to set the values for the device control parameters when setting up the terminal:
•
8 data bits
•
1 stop bit
•
No parity
You can change these parameters to meet the requirements of the terminal or host to which you are attached.
To configure device control parameters, follow these steps:

 Feedback
Feedback