-
Cisco IOS Voice Command Reference
-
About Cisco IOS Software Documentation
-
Using Cisco IOS Software
-
New and Modified Commands
-
Commands: A
-
Commands: B
-
Commands: cache --> call fallback jitter-probe num-packets
-
Commands: call fallback jitter-probe precedence --> ces connect
-
Commands: ces initial-delay --> codec preference
-
Commands: comfort-noise --> customer-id
-
Commands: default (MGCP profile) through direct-inward-dial
-
Commands: E
-
Commands: F
-
Commands: G
-
Commands: H
-
Commands: I
-
Commands: K
-
Commands: L
-
Commands: M
-
Commands: N
-
Commands: O
-
Commands: P through Q
-
Commands: R
-
Commands: SCCP through sgcp tse payload
-
Commands: show aal2 profile through show controllers timeslots
-
Commands: show controllers voice through show mgcp
-
Commands: show mgcp connection through show ss7 sm session
-
Commands: show ss7 sm set through shutdown (voice-port)
-
Commands: signal through suppress
-
Commands: T
-
Commands: U
-
Commands: V through W
-
Commands: Z
-
Table Of Contents
Cisco IOS Voice Commands:
L
This chapter contains commands to configure and maintain Cisco IOS voice applications. The commands are presented in alphabetical order. Some commands required for configuring voice may be found in other Cisco IOS command references. Use the command reference master index or search online to find these commands.
For detailed information on how to configure these applications and features, refer to the Cisco IOS Voice Configuration Guide.
limit-dn (cm-fallback)
To set a limit of directory numbers on each Cisco IP phone when the Survivable Remote Site (SRS) Telephony feature is enabled, use the limit-dn command in call-manager-fallback configuration mode. To reset to the default, use the no form of this command.
limit-dn [7910 | 7940 | 7960] max-lines
no limit-dn [7910 | 7940 | 7960]
Syntax Description
7960
Cisco IP Phone 7960.
7940
Cisco IP Phone 7940.
7910
Cisco IP Phone 7910.
max-lines
Maximum number of directory numbers. Range is from 1 to 34. Default is 34.
Defaults
34 directory numbers
Command Modes
Call-manager-fallback configuration
Command History
Usage Guidelines
This command rations the maximum number of directory numbers for each Cisco IP phone type, when the SRS Telephony features is enabled. In the CallManager environment the network supports large numbers of Cisco IP phones; but when CallManager falls back to STS Telephony, the specified routers have limits to the directory numbers. Therefore this configuration allows you to ration the directory numbers accordingly.
Note
You must configure this command during the initial SRS Telephony router configuration, before any IP phone actually registers to the SRS Telephony router. You can modify the number of lines at a later time.
The range of the maximum lines setting is from 1 to 34. The default maximum directory number is set to 34. If there is any active phone with last line number greater than this limit, warning information is displayed for phone reset.
Examples
The following example sets a directory number limit of 2 for the Cisco IP phone 7910:
Router(config-cm-fallback)# limit-dn 7910 2Related Commands
call-manager-fallback
SRS Telephony feature support and enters call-manager-fallback configuration mode.
link (RLM)
To enable a Redundant Link Manager (RLM) link, use the link command in RLM configuration mode. To disable this function, use the no form of this command.
link {hostname name | address ip-address} source loopback-source weight factor
no link {hostname name | address ip-address} source loopback-source weight factor
Syntax Description
Defaults
Disabled
Command Modes
RLM configuration
Command History
Usage Guidelines
This command is a preference-weighted multiple entries command. Within the same server, the link preference is specified in weighting.
Examples
The following example specifies the RLM group (network access server), device name, and link addresses and their weighting preferences:
rlm group 1server r1-serverlink address 10.1.4.1 source Loopback1 weight 4link address 10.1.4.2 source Loopback2 weight 3load (telephony-service)
To associate a phone firmware file with a type of Cisco IP phone, use the load command in telephony-service configuration mode. To disassociate a phone firmware file with a type of Cisco IP phones, use the no form of this command.
load phone-type firmware-file
no load phone-type firmware-file
Syntax Description
Defaults
No default behavior or values
Command Modes
Telephony-service configuration
Command History
Usage Guidelines
This command updates the Cisco IOS Telephony Service (ITS) configuration file for the specified type of IP phone to add the name of the correct firmware file that it should load. This filename also provides the version number for the phone firmware that is in the file. Later, whenever a phone is started or rebooted the phone reads the configuration file to determine the name of the firmware file that it should load and then looks for that firmware file on the TFTP server.
Cisco IP phones update themselves with new phone firmware whenever they are initially started up or reloaded.
A separate load command is needed for each type of phone. The Cisco IP Phone 7960 and Cisco IP Phone 7940 have the same phone firmware and share the 7960-7940 keyword.
When specifying the phone firmware filename in this command, do not use any file extension. For example, if the firmware file for Cisco IP Phone Expansion Module 7914s is named W05473955.bin, you enter load 7914 W05473955.
Following the load command, you use the tftp-server command to enable TFTP access to the file by Cisco IP phones. Note that the tftp-server command requires that you use the file extension as part of the filename.
Examples
The following example identifies the Cisco IP phone firmware file that is used by Cisco IP Phone 7960 and Cisco IP Phone 7910, and then defines the ITS router Flash memory as the location of the phone firmware file:
Router(config)# telephony-serviceRouter(config-telephony-service)# load 7960-7940 P00303020209Router(config-telephony-service)# load 7910 P00403020209Router(config-telephony-service)# exitRouter(config)# tftp-server flash:P00303020209.binRouter(config)# tftp-server flash:P00403020209.binRelated Commands
telephony-service
Enables Cisco IOS Telephony Service and enters telephony-service configuration mode.
tftp-server
Enables TFTP access to firmware files on the TFTP server.
load-balance
To configure load balancing, use the load-balance command in gatekeeper configuration mode. To disable load balancing, use the no form of this command.
load-balance [endpoints max-endpoints] [calls max-calls] [cpu max-%cpu]
[memory max-%mem-used]no load-balance [endpoints max-endpoints] [calls max-calls] [cpu max-%cpu]
[memory max-%mem-used]Syntax Description
Defaults
Load balancing is performed by the gatekeeper.
Command Modes
Gatekeeper configuration
Command History
12.1(2)XM
This command was introduced.
12.2(2)T
This command was integrated into Cisco IOS Release 12.2(2)T.
12.2(2)XB1
This command was implemented on the Cisco AS5850.
Usage Guidelines
Load balancing occurs when one gatekeeper reaches the default or the configured load level. Upon reaching the load-level threshold, the gatekeeper begins sending alternate gatekeeper information in Registration, Admission, and Status (RAS) messages, and the gateways then attempt to migrate from the loaded gatekeeper to its least busy alternate. The move is permanent; endpoints are not actively moved back to the original gatekeeper if it stabilizes. However, they may return to that gatekeeper if the new gatekeeper reaches a load threshold and transfers them again. The gatekeepers share the load, but they may not have equal shares. The process of load balancing allows for more effective zone management.
Examples
The following example configures load balancing:
load-balance endpoints 200 calls 100 cpu 75 memory 80Related Commands
local
To define the local domain, including the IP address and port that the border element (BE) should use for interacting with remote BEs, use the local command in Annex G configuration mode. To reset to the default, use the no form of this command.
local ip ip-address [port local-port]
no local ip
Syntax Description
ip ip-address
IP address of the local border element.
port local-port
(Optional) Port number of the local border element, which is used for exchanging Annex G messages. Default is 2099.
Defaults
Port number: 2099
Command Modes
Annex G configuration
Command History
Usage Guidelines
The local IP address can be a virtual Hot Standby Routing Protocol (HSRP) address for high reliability and availability. You can configure multiple gatekeepers and BEs identically and use HSRP to designate a primary BE and other standby BEs. If the primary BE is down, a standby BE operates in its place.
Examples
The following example sets the IP address and port that the BE should use. (Note that this example uses a nonstandard port number. If you do not want to use a nonstandard port number, use the default value of 2099.)
Router(config)# call-router h323-annexg be20Router(config-annexg)# local ip 121.90.10.80 port 2010Related Commands
call-router
Enables the Annex G border element configuration commands.
show call-router status
Displays the Annex G BE status.
loopback (controller)
To set the loopback method for testing a T1 or E1 interface, use the loopback command in controller configuration mode. To reset to the default, use the no form of this command.
loopback {diagnostic | local {payload | line} | remote {v54 channel-group channel-number | iboc | esf {payload | line}}}
no loopback
Syntax Description
Defaults
No loopback is configured.
Command Modes
Controller configuration
Command History
Usage Guidelines
You can use a loopback test on lines to detect and distinguish equipment malfunctions caused either by the line and channel service unit/digital service unit (CSU/DSU) or by the interface. If correct data transmission is not possible when an interface is in loopback mode, the interface is the source of the problem.
Examples
The following example sets the diagnostic loopback method on controller T1 0/0:
controller t1 0/0loopback diagnosticThe following example sets the payload loopback method on controller E1 0/0:
controller e1 0/0loopback local payloadloop-detect
To enable loop detection for T1, use the loop-detect command in controller configuration mode. To cancel loop detection, use the no form of this command.
loop-detect
no loop-detect
Syntax Description
This command has no arguments or keywords.
Defaults
Loop detection is disabled.
Command Modes
Controller configuration
Command History
Usage Guidelines
This command applies to Voice over Frame Relay and Voice over ATM on the Cisco MC3810 multiservice concentrator.
Examples
The following example configures loop detection for controller T1 0:
controller t1 0loop-detectRelated Commands
loopback (interface)
Diagnoses equipment malfunctions between an interface and a device.
loss-plan
To specify the analog-to-digital gain offset for an analog Foreign Exchange Office (FXO) or Foreign Exchange Station (FXS) voice port, use the loss-plan command in voice-port configuration mode. To reset to the default, use the no form of this command.
loss-plan {plan1 | plan2 | plan3 | plan4 | plan5 | plan6 | plan7 | plan8 | plan9}
no loss-plan
Syntax Description
Defaults
FXO: A-D gain = 0 dB, D-A gain = 0 dB (loss plan 1)
FXS: A-D gain = -3 dB, D-A gain = -3 dB (loss plan 1)Command Modes
Voice-port configuration
Command History
Usage Guidelines
This command sets the analog signal level difference (offset) between the analog voice port and the digital signal processor (DSP). Each loss plan specifies a level offset in both directions—from the analog voice port to the DSP (A-D) and from the DSP to the analog voice port (D-A).
Use this command to obtain the required levels of analog voice signals to and from the DSP.
This command is supported only on Cisco MC3810 multiservice concentrators, on FXO and FXS analog voice ports.
Examples
The following example configures FXO voice port 1/6 for a -3 dB offset from the voice port to the DSP and for a 0 dB offset from the DSP to the voice port:
voice-port 1/6loss-plan plan3The following example configures FXS voice port 1/1 for a 0 dB offset from the voice port to the DSP and for a -7 dB offset from the DSP to the voice port:
voice-port 1/1loss-plan plan6Related Commands
lrq forward-queries
To enable a gatekeeper to forward location request (LRQ) messages that contain E.164 addresses that match zone prefixes controlled by remote gatekeepers, use the lrq forward-queries command in gatekeeper configuration mode. To disable this function, use the no form of this command.
lrq forward-queries [add-ttl]
no lrq forward-queries
Syntax Description
add-ttl
Adds a hop count field to the LRQ if one is not present by filling in the time-to-live (TTL) field as if the LRQ is freshly originated from a Cisco gatekeeper. Maximum value is 10. Default 6.
Defaults
Disabled
Command Modes
Gatekeeper configuration
Command History
12.0(3)T
This command was introduced on the following platforms: Cisco 2500 series, Cisco 3600 series, and Cisco MC3810.
12.3(2)T
The add-ttl keyword was added.
Usage Guidelines
LRQ forwarding is dependent on a Cisco nonstandard field that first appeared in Cisco IOS Release 12.0(3)T. This means that any LRQ message received from a non-Cisco gatekeeper or any gatekeeper running a Cisco IOS software image prior to Cisco IOS Release 12.0(3)T is not forwarded.
The routing of E.164-addressed calls is dependent on the configuration of zone prefix tables (for example, area code definitions) on each gatekeeper. Each gatekeeper is configured with a list of prefixes controlled by itself and by other remote gatekeepers. Calls are routed to the zone that manages the matching prefix. Thus, in the absence of a directory service for such prefix tables, you, the network administrator, may have to define extensive lists of prefixes on all the gatekeepers in your administrative domain.
To simplify this task, you can select one of your gatekeepers as the "directory" gatekeeper and configure that gatekeeper with the complete list of prefixes and the lrq forward-queries command. You can then simply configure all the other gatekeepers with their own prefixes and the wildcard prefix "*" for your directory gatekeeper.
This command affects only the forwarding of LRQ messages for E.164 addresses. LRQ messages for H.323-ID addresses are never forwarded.
Examples
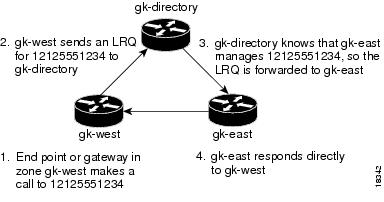
The following example selects one gatekeeper as the directory gatekeeper. See Figure 4.
Figure 4 Example Scenario with Directory Gatekeeper and Two Remote Gatekeepers
Configuration on gk-directory
On the directory gatekeeper called gk-directory, identify all the prefixes for all the gatekeepers in your administrative domain:
zone local gk-directory cisco.com zone remote gk-west cisco.com 172.16.1.1zone remote gk-east cisco.com 172.16.2.1zone prefix gk-west 1408.......zone prefix gk-west 1415.......zone prefix gk-west 1213.......zone prefix gk-west 1650.......zone prefix gk-east 1212.......zone prefix gk-east 1617.......lrq forward-queriesConfiguration on gk-west
On the gatekeeper called gk-west, configure all the locally managed prefixes for that gatekeeper:
zone local gk-west cisco.comzone remote gk-directory cisco.com 172.16.2.3zone prefix gk-west 1408.......zone prefix gk-west 1415.......zone prefix gk-west 1213.......zone prefix gk-west 1650.......zone prefix gk-directory *Configuration on gk-east
On the gatekeeper called gk-east, configure all the locally managed prefixes for that gatekeeper:
zone local gk-east cisco.comzone remote gk-directory cisco.com 172.16.2.3zone prefix gk-east 1212.......zone prefix gk-east 1617.......zone prefix gk-directory *When an endpoint or gateway in zone gk-west makes a call to 12125551234, gk-west sends an LRQ message for that E.164 address to gk-directory, which forwards the message to gk-east. Gatekeeper gk-east responds directly to gk-west.
The following example configures an LRQ message with a fresh TTL value, adding a new hop count field:
Router(config-gk)# lrq forward-queries add-ttlRelated Commands
lrq reject-unknown-prefix
Enables the gatekeeper to reject all LRQ messages for zone prefixes that are not configured.
lrq lrj immediate-advance
To enable the Cisco IOS gatekeeper to immediately send a sequential location request (LRQ) message to the next zone after it receives a location reject (LRJ) message from a gatekeeper in the current zone, use the lrq lrj immediate-advance command in gatekeeper configuration mode. To disable this function, use the no form of this command.
lrq lrj immediate-advance
no lrq lrj immediate-advance
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Gatekeeper configuration
Command History
12.2(4)T
This command was introduced. This command does not support the Cisco AS5300, Cisco AS5350, and Cisco AS5400 series in this release.
Usage Guidelines
In a network in which LRQ messages are forwarded through multiple gatekeepers along a single path, a single LRQ message sent from a gatekeeper could solicit multiple LRJ and location confirmation (LCF) responses. If an LRJ response is received first, a potentially unnecessary LRQ message could be sent to the next zone, increasing traffic.
To avoid this problem, perform the following:
•
Configure the zone prefix to send sequential LRQ messages rather than to use the blast option, using the zone prefix command.
•
Configure the sequential timer on each gatekeeper along the path, using the timer lrq seq delay command.
Examples
The following example enables the gatekeeper to immediately send a sequential LRQ message to the next zone after it receives an LRJ message from a gatekeeper in the current zone.
lrq lrj immediate-advanceRelated Commands
lrq reject-resource-low
To configure a gatekeeper to notify a sending gatekeeper on receipt of a location request (LRQ) message that no terminating endpoints are available, use the lrq reject-resource-low command in gatekeeper configuration mode. To disable this function, use the no form of this command.
lrq reject-resource-low
no lrq reject-resource-low
Syntax Description
This command has no arguments or keywords.
Defaults
Disabled
Command Modes
Gatekeeper configuration
Command History
Examples
The following example causes the gatekeeper to notify the sending gatekeeper on receipt of an LRQ message that no terminating endpoints are available:
Router(config)# gatekeeperRouter(config-gk)# lrq reject-resource-lowlrq reject-unknown-circuit
To enable the gatekeeper to reject a location request (LRQ) message that contains an unknown destination circuit, use the lrq reject-unknown-circuit command in gatekeeper configuration mode. To disable the rejection, use the no form of this command.
lrq reject-unknown-circuit
no lrq reject-unknown-circuit
Syntax Description
This command has no keywords or arguments.
Defaults
Disabled
Command Modes
Gatekeeper configuration
Command History
Usage Guidelines
The gatekeeper checks the destination circuit field in each LRQ message. If the field contains a circuit unknown to the gatekeeper and this command is entered, the gatekeeper rejects the LRQ request. If this command is disabled, the gatekeeper tries to resolve the alias without considering the circuit.
Examples
The following example causes the gatekeeper to reject unknown carriers in an LRQ request:
Router(config)# gatekeeperRouter(config-gk)# lrq reject-unknown-circuitRelated Commands
endpoint circuit-id h323id
Assigns a circuit to a non-Cisco endpoint.
show gatekeeper endpoint circuits
Displays the information of all registered endpoints for a gatekeeper.
lrq reject-unknown-prefix
To enable the gatekeeper to reject all location request (LRQ) messages for zone prefixes that are not configured, use the lrq reject-unknown-prefix command in gatekeeper configuration mode. To reenable the gatekeeper to accept and process all incoming LRQ messages, use the no form of this command.
lrq reject-unknown-prefix
no lrq reject-unknown-prefix
Syntax Description
This command has no arguments or keywords.
Defaults
The gatekeeper accepts and processes all incoming LRQ messages.
Command Modes
Gatekeeper configuration
Command History
11.3(6)NA2
This command was introduced on the Cisco 2500 series and Cisco 3600 series.
12.0(3)T
This command was integrated into Cisco IOS Release 12.0(3)T.
Usage Guidelines
Use this command to configure the gatekeeper to reject any incoming LRQ messages for a destination E.164 address that does not match any of the configured zone prefixes.
Whether or not you use this command, the following is true when the E.164 address matches a zone prefix:
•
If the matching zone prefix is local (that is, controlled by this gatekeeper), the LRQ message is serviced.
•
If the matching zone prefix is remote (that is, controlled by some other gatekeeper), the LRQ message is rejected.
If you do not use this command and the target address does not match any known local or remote prefix, the default behavior is to attempt to service the call using one of the local zones. If this default behavior is not suitable for your site, use this command on your router to force the gatekeeper to reject such requests.
Examples
Consider the following gatekeeper configuration:
zone local gk408 cisco.comzone local gk415 cisco.comzone prefix gk408 1408.......zone prefix gk415 1415.......lrq reject-unknown-prefixIn this sample configuration, the gatekeeper is configured to manage two zones. One zone contains gateways with interfaces in the 408 area code, and the second zone contains gateways in the 415 area code. Then using the zone prefix command, the gatekeeper is configured with the appropriate prefixes so that calls to those area codes hop off in the optimal zone.
Now say some other zone has been erroneously configured to route calls to the 212 area code to this gatekeeper. When the LRQ message for a number in the 212 area code arrives at this gatekeeper, the gatekeeper fails to match the area code, and the message is rejected.
If this was your only site that had any gateways in it and you wanted your other sites to route all calls that require gateways to this gatekeeper, you can undo the lrq reject-unknown-prefix command by simply using the no lrq reject-unknown-prefix command.Now when the gatekeeper receives an LRQ message for the address 12125551234, it attempts to find an appropriate gateway in either one of the zones gk408 or gk415 to service the call.
Related Commands
lrq forward-queries
Enables a gatekeeper to forward LRQ messages that contain E.164 addresses that match zone prefixes controlled by remote gatekeepers.
lrq timeout blast window
To configure the timeout window for use when sending multiple location request (LRQ) messages (either sequentially or simultaneously), use the lrq timeout blast window command in gatekeeper configuration mode. To reset to the default, use the no form of this command.
lrq timeout blast window seconds
no lrq timeout blast window
Syntax Description
Defaults
6 seconds
Command Modes
Gatekeeper configuration
Command History
12.1(2)T
This command was introduced on the following platforms: Cisco 2500 series, Cisco 2600 series, Cisco 3600 series, Cisco 7200 series, and Cisco MC3810.
Examples
The following example sets the window to 3 seconds:
lrq timeout blast window 3Related Commands
gatekeeper gw-type-prefix
Sets the gatekeepers responsible for each technology prefix.
zone prefix
Adds a prefix to a gatekeeper's zone list.
lrq timeout seq delay
To configure the delay for use when sending location request (LRQ) messages sequentially, use the lrq timeout seq delay command in gatekeeper configuration mode. To reset to the default, use the no form of this command.
lrq timeout seq delay value
no lrq timeout seq delay
Syntax Description
value
Duration of the delay, in 100-millisecond units.Range is from 1 to 10. The default is 5 (500 ms or 0.5 seconds).
Defaults
Five 100-millisecond units (500 ms or 0.5 seconds)
Command Modes
Gatekeeper configuration
Command History
12.1(2)T
This command was introduced on the following platforms: Cisco 2500 series, Cisco 2600 series, Cisco 3600 series, Cisco 7200 series, and Cisco MC3810.
Examples
The following example sets the window to 300 milliseconds:
lrq timeout seq delay 3Related Commands
gatekeeper gw-type-prefix
Sets the gatekeepers responsible for each technology prefix.
zone prefix
Adds a prefix to a gatekeeper's zone list.

 Feedback
Feedback