-
Cisco Traffic Anomaly Detector Module Configuration Guide (Software Version 6.1 and 6.1-XG)
-
Index
-
Preface
-
Product Overview
-
Configuring the Detector Module on the Supervisor Engine
-
Initializing the Detector Module
-
Configuring the Detector
-
Configuring Zones
-
Configuring Zone Filters
-
Configuring Policy Templates and Policies
-
Learning the Zone Traffic Characteristics
-
Detecting Zone Traffic Anomalies
-
Using Interactive Detect Mode
-
Using Attack Reports
-
Using Detector Module Diagnostic Tools
-
Performing Maintenance Tasks
-
Table Of Contents
Configuring Policy Templates and Policies
Understanding Policy Templates
Understanding the Different Policy Template Types
Configuring Policy Template Parameters
Configuring the Maximum Number of Services
Configuring the Minimum Threshold
Configuring Policy Template States
Configuring All Policy Template Parameters Simultaneously
Understanding and Managing the Policy Services
Understanding the Packet Types that the Detector module Monitors
Understanding the Traffic Characteristics that the Detector Module Monitors
Configuring the Policy Threshold
Setting the Threshold as Fixed
Configuring a Threshold Multiplier
Multiplying a Threshold by a Factor
Configuring Specific IP Thresholds
Configuring the Policy Timeout
Configuring the Detection Time Parameter for PPH Policies
Configuring the Policy Interactive Status
Backing Up the Policy Configuration
Configuring Policy Templates and Policies
This chapter describes the Cisco Traffic Anomaly Detector (Detector module) zone policies, policy structure, and policy templates, and it describes how to configure the zone policy and the policy template parameters.
This chapter refers to the Cisco Guard (Guard), the companion product of the Detector module. The Guard is a Distributed Denial of Service (DDoS) attack detection and mitigation device that cleans the zone traffic as the traffic flows through it, dropping the attack traffic and injecting the legitimate traffic back into the network. When the Detector module determines that the zone is under attack, it can activate the Guard attack mitigation services. The Detector module can also synchronize zone configurations with the Guard. For more information about the Guard, see the Cisco Anomaly Guard Module Configuration Guide or the Cisco Guard Configuration Guide.
This chapter contains the following sections:
•
Understanding Policy Templates
•
Understanding the Policy Path
•
Configuring Policy Parameters
•
Backing Up the Policy Configuration
Understanding Zone Policies
The zone policies enable the Detector module to perform a statistical analysis of the zone traffic flow. Depending on the type of policy, a policy monitors traffic for one of the following traffic characteristics:
•
Traffic rate—Rate of traffic measured in packets per second or packets per hour. Policies that monitor traffic in packets per hour (PPH policies) are used to monitor zone traffic for low rate zombie attacks that can last for hours or days.
•
Connections—Number of concurrent connections.
•
Packet ratio—Ratio of one packet type to another.
The zone policies are configured to take action against a particular traffic flow if the flow exceeds the policy thresholds, indicating malicious or abnormal traffic. When a flow exceeds the policy thresholds, the policies configure a set of filters (dynamic filters) dynamically to record the event in its syslog or activate a Guard that you have defined in the remote Guard lists. When activated, the Guard protects the zone by mitigating the attack.
Every zone configuration contains a set of policies. When you create a new zone using a predefined zone template, the Detector module configures the new zone with policies associated with the template. When you create a new zone by copying an existing zone, the Detector module configures the new zone with the policies of the existing zone.
To create zone-specific policies and tune their thresholds to recognize normal zone traffic, the Detector module learns the zone traffic in a two-phase learning process (see the "Understanding the Learning Process" section). The Detector module uses predefined policy templates to construct the policies and then learns the policy thresholds as determined by the zone traffic. The Detector module uses each policy template to create policies that the Detector module requires to protect the zone against a specific Distributed Denial of Service (DDoS) threat. After the Detector module creates and tunes the zone policies, you can add and delete policies or change policy parameters.
Policies have cross dependencies and priorities. If two different policies define the same traffic flow, the Detector module analyzes the flow using the policy that is more specific. For example, policies that relate to TCP services exclude the HTTP services that are handled by the HTTP-related policies.
Understanding Policy Templates
A policy template is a collection of policy construction rules that the Detector module uses during the policy construction phase to create the zone policies. The name of the policy template is derived from the characteristics that are common to all the policies that it creates and can be a protocol (such as DNS), an application (such as HTTP), or the objective (such as ip_scan). For example, the policy template tcp_connections produces policies that relate to a connection, such as the number of concurrent connections. When you create a new zone, the Detector module includes a set of policy templates in the zone configuration.
This section contains the following topics:
•
Understanding the Different Policy Template Types
•
Configuring Policy Template Parameters
Understanding the Different Policy Template Types
Table 7-1 describes the Detector module policy templates. The Detector module includes these policy templates when you create a new zone using the DETECTOR_DEFAULT zone template.
The Detector module includes additional policy templates for zones that were created from zone templates that are designed for specific types of attacks or specific services. Table 7-2 details the policy templates that the Detector module adds to a zone configuration based on a specific zone template.
Table 7-2 Additional Policy Templates
DETECTOR_WORM
worm_tcp—Constructs a group of policies that identify TCP worms. Worm TCP policies manage worm attacks in which one or more source IP addresses create many nonestablished connections on the same port to many destination IP addresses. This policy template is designed primarily for zones in which the IP address definition is a subnet.
The Detector module adds services to policies that are created from this policy template during the threshold tuning phase of the learning process instead of during the policy construction phase. The policy template parameters, max_services and min_threshold, do not apply to this policy template. See the "Understanding Worm Policies" section for more information.
If you create a zone from a GUARD_ zone template, you can configure the parameters of additional policy templates that can be synchronized to a Guard. The Detector module uses the policy templates described in Table 7-3 and replaces the policy templates http, tcp_connections, and tcp_outgoing with the policy templates http_ns, tcp_connections_ns, and tcp_outgoing_ns policies. The http_ns, tcp_connections_ns, and tcp_outgoing_ns policy templates do not create policies with actions that require the Guard to apply the strong protection level to the traffic flow.
Table 7-3 details the Detector module policy templates for GUARD_TCP_NO_PROXY.
To view a list of all policy templates, use the policy-template command in zone configuration mode and press Tab twice.
Configuring Policy Template Parameters
During the learning process, each active policy template produces a group of policies based on the policy definitions and the zone traffic characteristics. The Detector module ranks the services (protocol and port numbers) that the policy template monitors by the level of traffic volume. The Detector module then selects the services that have the highest traffic volume and that have exceeded the defined minimum threshold, and it creates a policy for each service. Some of the policy templates create an additional policy to handle all traffic flows for which a specific policy was not added with a service of any.
You can configure the following policy template parameters:
•
Maximum Number of Services—Defines the maximum number of services that the Detector module picks up for the policy template to create specific policies.
•
Minimum Threshold—Defines the minimum threshold that must be exceeded for the Detector module to rank the service.
•
Policy Template State—Defines whether or not the Detector module produces policies from the policy template.
The policy template parameters maximum number of services and minimum threshold do not affect the worm_tcp policy template.
To configure the policy template parameters, enter the policy template configuration mode by entering the following command in zone configuration mode:
policy-template policy-template-name
The policy-template-name argument specifies the name of the policy template. See Table 7-1 for more information.
After executing the command, the Detector module enters the policy template configuration mode.
The following example shows how to enter http policy template configuration mode:
user@DETECTOR-conf-zone-scannet# policy-template httpuser@DETECTOR-conf-zone-scannet-policy_template-http#To display the parameters of a specific policy template, use the show command in policy template configuration mode.
This section contains the following topics:
•
Configuring the Maximum Number of Services
•
Configuring the Minimum Threshold
•
Configuring Policy Template States
•
Configuring All Policy Template Parameters Simultaneously
Configuring the Maximum Number of Services
The maximum number of services parameter defines the maximum number of services (protocol numbers or port numbers) for which the policy template selects and creates policies. The Detector module ranks the services by the level of traffic volume for each service. The Detector module then selects the services that have the highest traffic volume and that have exceeded the defined minimum threshold (as defined by the min-threshold parameter), and it creates policies for each service. The Detector module may add an additional policy with a service of any to handle all other traffic flows with the characteristics of the policy template.
Note
The higher the maximum number of services means that the zone requires more Detector module memory.
You can only define the maximum number of services parameter for policy templates that detect services: tcp_services, tcp_services_ns, udp_services, and other protocols. You cannot configure it for policy templates that monitor a specific service, such as dns_tcp, which monitors service 53, or for policy templates that relate to a specific traffic characteristic, such as fragments.
The Detector module measures the traffic rate of the service based on the policy traffic characteristics. The traffic characteristic can be the source IP addresses or the destination IP addresses. A policy that monitors the service any measures the rate of source IP addresses on all services that are not handled by a specific policy.
By limiting the service number, you can configure the Detector module policies to your preferred traffic flow requirements.
To configure the maximum number of services, use the following command in policy template configuration mode:
max-services max-services
The max-services argument is an integer greater than 1 that defines the maximum number of services that the Detector module selects. We recommend that you do not exceed the maximum of 10 services.
The following example shows how to configure the maximum number of services that the Detector module monitors to 5:
user@DETECTOR-conf-zone-scannet-policy_template-tcp_services# max-services 5Configuring the Minimum Threshold
The minimum threshold parameter defines the minimum traffic volume for a service. When the threshold is exceeded, the Detector module constructs policies that relate to the service traffic according to the particular traffic flow that exceeded the threshold. By setting the threshold, you can adapt the anomaly detection operation to the traffic volume of the zone services.
You cannot configure the minimum threshold parameter for the following policy templates: dns_udp, fragments, ip_scan, port_scan, tcp_connections, tcp_not_auth, tcp_outgoing, and tcp_ratio. These templates are essential for proper zone protection and always construct a policy
To configure the minimum threshold, use the following command in policy template configuration mode:
min-threshold min-threshold
The threshold argument is a real number (a floating point number with two decimal places), equal to or greater than 0, that defines the minimum threshold rate in packets per second (pps). When measuring concurrent connections and the SYN/FIN ratio, the threshold is an integer that defines the total number of connections.
The following example shows how to configure the minimum threshold of the policy template http:
user@DETECTOR-conf-zone-scannet-policy_template-http# min-threshold 12.3Configuring Policy Template States
The policy template state parameter defines whether the policy template is enabled or disabled. The Detector module is unable to use a disabled policy template during the policy construction phase to produce policies.
CautionDisabling a policy template may seriously compromise zone anomaly detection. If you disable a policy template, the Detector module cannot detect the zone traffic to which the policy template relates. For example, disabling the dns_udp policy template prevents the Detector module from creating zone policies that manage DNS (UDP) attacks.
To disable a policy template, use the disable command in policy template configuration mode.
To enable a policy template, use the enable command in policy template configuration mode.
The following example shows how to disable the policy template http:
user@DETECTOR-conf-zone-scannet-policy_template-http# disableConfiguring All Policy Template Parameters Simultaneously
You can configure all policy template operational parameters with a single command by entering the following command in zone configuration mode:
policy-template policy-template-name max-services min-threshold {disabled | enabled}
Table 7-4 provides the arguments and keywords for the policy-template command.
Table 7-4 Arguments and Keywords for the policy-template Command
policy-template-name
Policy template name. See Table 7-5 for more information.
max-services
Maximum number of services for which the Detector module selects and constructs policies from the specific policy template.
To prevent the Detector module from changing the current value, enter a value of -1.
See the "Configuring the Maximum Number of Services" section for more information.
min-threshold
Minimum threshold that must be exceeded for the Detector module to rank the service.
To prevent the Detector module from changing the current value, enter a value of -1.
See the "Configuring the Minimum Threshold" section for more information.
disabled
Disables the policy template from producing policies. See the "Configuring Policy Template States" section for more information.
enabled
Enables the policy template. See the "Configuring Policy Template States" section for more information.
The following example shows how to set the parameters of the tcp_services policy template. The maximum number of services is set to 3, the policy state is set to enabled, and the minimum threshold is unchanged (-1).
user@DETECTOR-conf-zone-scannet# policy-template tcp_services 3 -1 enabledUnderstanding the Policy Path
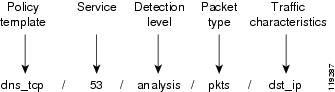
The name of the policy is composed of sections that describe the traffic characteristic that it measures. For example, the policy http/80/analysis/syns/src_ip measures traffic flows of HTTP SYN packets destined to port 80 that were authenticated by the Detector module analysis detection level functions and aggregated according to source IP addresses.
Figure 7-1 provides an example of a zone policy name.
Figure 7-1 Policy Name
Table 7-5 describes the policy name sections.
Table 7-5 Policy Name Sections
Policy template
Policy template that was used to construct the policy. Each policy template deals with the characteristics that the Detector module requires to detect a specific DDoS threat. See the "Understanding Policy Templates" section for more information.
Service
Port number or protocol number in the traffic flow that the policy monitors.
Detection level
Detection level that the Detector module applies to the traffic flow. Detection levels have a static configuration and cannot be configured manually.
Packet types
Packet types that the Detector module monitors.
Traffic characteristics
Traffic characteristics that the Detector module uses to aggregate the policy.
The first four sections of the policy name (policy template, service, detection level, and packet type) define the type of traffic that is analyzed. The last section of the policy path (traffic characteristics) defines how to analyze the flow.
This section contains the following topics:
•
Understanding and Managing the Policy Services
•
Understanding the Packet Types that the Detector module Monitors
•
Understanding the Traffic Characteristics that the Detector Module Monitors
Understanding and Managing the Policy Services
The service section defines the zone application port or protocol to which each policy relates. Policies have cross dependencies and priorities. If two different policies define the same traffic flow, the Detector module analyzes the flow using the policy that is more specific. The service any relates to all traffic that does not specifically match other services created from the same policy template.
We recommend that you define specific policies for the zone main services to obtain anomaly detection that is most suited to your individual needs.
CautionDo not add the same service (port number) to more than one policy because it may decrease the Detector module performance.
When you add or delete a service from the zone policies, the Detector module marks the zone policies as untuned. If you enabled zone anomaly detection and the learning process, the Detector module cannot detect anomalies in the zone traffic until you perform one of the following actions:
•
Perform the threshold tuning phase of the learning process and accept the results (see the "Activating the Threshold Tuning Phase" section).
•
Mark the zone policies tuned (see the "Marking the Policies as Tuned" section).
This section contains the following topics:
Adding a Service
You can add services to all policies that were created from a specific policy template. The new service is an addition to the services that were discovered during the policy construction phase and is defined with default values. You can define the threshold manually, but we recommend that you run the threshold tuning phase of the learning process to tune the policies to the zone traffic. See the "Activating the Threshold Tuning Phase" section for more information.
You can add a new service to policies that were created from the following policy templates:
•
tcp_services, udp_services, tcp_services_ns, or worm_tcp
The service designates a port number.
•
other_protocols
The service designates a protocol number.
Note
If you activate the policy construction phase after adding a service, new services might override the manually added service.
Unless you enable the policy construction phase, you may need to add a service manually in the following situations:
•
A new application or service was added to the zone network.
•
The policy construction phase was activated for a short period, so it does not reflect all the network services (for instance, if there are known applications or services that are active only once a week or during the night).
To add a service, use one of the following commands:
•
add-service service-num—From policy template configuration mode
•
policy-template policy-template-name add-service service-num— From zone configuration mode
Table 7-6 provides the arguments for the add-service command.
Table 7-6 Arguments for the add-service Command
service-num
Protocol or port number.
policy-template-name
Policy template name. See Table 7-1 for more information.
The following example shows how to add a service to all the policies that were created from the policy template tcp_services:
user@DETECTOR-conf-zone-scannet-policy_template-tcp_services#add-service 25Deleting a Service
You can delete a specific service for any policy template. The Detector module will delete the service from all policies that were created from the specific policy template.
To delete a service, use one of the following commands:
•
remove-service service-num—Use this command from policy template configuration mode
•
policy-template policy-template-name remove-service service-num—Use this command from zone configuration mode
Table 7-7 provides the arguments for the remove-service command.
Table 7-7 Arguments for the remove-service Command
service-num
Protocol or port number to remove.
policy-template-name
Policy template name. See Table 7-1 for more information.
CautionIf you delete a service, the Detector module policies cannot monitor the traffic of that service, which may compromise zone anomaly detection.
You can remove services from the following policy templates:
•
tcp_services, udp_services, or tcp_services_ns
The service is a port number.
•
other_protocols
The service is a protocol number.
If you do not activate the policy construction phase of the learning process, you may need to remove a service manually in the following situations:
•
An application or service was removed from the network.
•
An application or service that you do not want to enable (because it is uncommon for the network environment) but was identified during the policy construction phase.
Note
If you activate the policy construction phase after removing a service, the same service might be added again.
The following example shows how to delete a service from all policies that were created from the policy template tcp_services:
user@DETECTOR-conf-zone-scannet-policy_template-tcp_services#remove-service 25Understanding the Packet Types that the Detector module Monitors
The Detector module monitors packet characteristics, which can be one of the following:
•
Packet type (for example, TCP-SYN packets)
•
Packet analysis (for example, authenticated packets, which are packets that the Detector module has verified their connection by performing a TCP handshake)
•
Packet direction (for example, incoming connections)
Table 7-8 describes the packet types that the Detector module monitors.
Understanding the Traffic Characteristics that the Detector Module Monitors
Traffic characteristics define how to analyze the traffic flow and what characteristics were used to aggregate the policies. Different policies can analyze the same traffic flow but measure the rate based on different characteristics, as shown in this example:
/53/analysis/pkts/dst_ip and /53/analysis/pkts/src_ip
Table 7-9 describes the traffic characteristics that the Detector module monitors.
Table 7-9 Traffic Characteristics
dst_ip
Traffic destined to a zone IP address.
dst_ip_ratio
Ratio of SYN and FIN flagged packets destined to a specific IP address.
dst_port
Traffic destined to a specific zone port.
dst_port_ratio
Ratio of SYN and FIN flagged packets destined to a specific port.
global
Summation of all traffic flow as defined by the other policy sections.
protocol
Traffic destined to the zone aggregated based on the protocol.
scanners
Histogram of the number of source IP addresses that scan zone destination IP addresses on a specific destination port. See the "Understanding Worm Policies" section for more information.
src_ip
Traffic destined to the zone aggregated according to the source IP address.
src_ip_many_dst_ips
Traffic from a single IP address that probes a large number of zone IP addresses on the same port. This key is used for IP scanning.
src_ip_many_ports
Traffic from a single IP address that probes a large number of ports on a zone destination IP address. This key is used for port scanning.
Configuring Policy Parameters
After completing the learning process, you can display specific policy parameters (policy state, policy threshold, policy timeout, policy action, and policy interactive state) to determine if the policy parameters suit the zone traffic. You can configure the policy parameters of a single policy or a group of policies to adapt to zone traffic requirements.
To display the configuration of the policy parameters, use the following command in policy configuration mode:
show
To display the current parameter configuration of a specific policy, use the show command in policy configuration mode. To enter policy configuration mode, use the following command in zone configuration mode:
policy policy-path
The policy-path argument specifies the policy path sections. The path can be a partial path that includes only part of the policy sections. See the "Understanding Zone Policies" section for more information.
Note
To move up one level in the policy path hierarchy, enter policy .. at the policy path prompt.
The following example shows how to enter the /53/analysis/syns/global policy configuration mode:
user@DETECTOR-conf-zone-scannet# policy /53/analysis/syns/global user@DETECTOR-conf-zone-scannet-policy-//53/analysis/syns/global#You can change the policy action, timeout, threshold, and learning parameters at every section of the policy path. However, more policies are affected if you change these parameters at the higher-level policy sections (such as the policy template or service sections). If you configure these parameters at a high-level policy path hierarchy, these parameters change in all the subpolicy paths. You can use an asterisk (*) as a wildcard character in each policy path section. If you do not specify a policy path section, the Detector module relates to the unspecified section as a wildcard (*). For example, the tcp_services//analysis//global policy uses a wildcard for the service and the packet type.
You can also set the detection time parameter for the policies that monitor zone traffic for low traffic rate zombie attacks. These policies, known as PPH policies, monitor traffic rates in packets per hour (rather than packets per second) and have _pph appended to the packet type in their path name as the following example shows:
user@GUARD-conf-zone-scannet-policy-/tcp_services/any/strong/reqs_pph/src_ip#
Note
Only zone configurations that you create using the 6.1 or 6.1-XG software release will contain PPH policies. Zones that you created using a previous software version will not contain PPH policies.
Note
PPH policies by default are set to the disabled state when you create a new zone because they may increase the amount of memory used by the zone and also affect Detector module performance. To enable the zone PPH polices, you must change the policy states to active (see the "Changing the Policy State")
This section contains the following topics:
•
Configuring the Policy Threshold
•
Configuring the Policy Timeout
•
Configuring the Policy Action
•
Configuring the Detection Time Parameter for PPH Policies
•
Configuring the Policy Interactive Status
Changing the Policy State
The zone policies have three possible states:
•
Active—The policy monitors the traffic and performs an action once the threshold is exceeded.
•
Inactive—The policy monitors the traffic and obtains the threshold, but it takes no action when a threshold is exceeded. You can inactivate a policy to avoid reactivating the threshold-tuning phase of the learning process.
•
Disabled—The policy does not monitor the traffic flow, so no threshold is obtained.
Note
We recommend that you activate the threshold tuning phase of the learning process to ensure that the Detector module monitors the correct thresholds for the other policies.
CautionWhen you disable a policy, the active zone policies assume responsibility for the traffic that would normally be monitored by the disabled policy. To adjust the thresholds of the active policies, we recommend that you activate the threshold tuning phase before you activate zone anomaly detection.
To change the policy state, use the following command in policy configuration mode:
state {active | disabled | inactive}
The following example shows how to set the policy state:
user@DETECTOR-conf-zone-scannet-policy-//53/analysis/syns# state disabledThe following example shows how to set the state of all global policies:
user@DETECTOR-conf-zone-scannet-policy-/*/*/*/global# state inactive
CautionIf you deactivate or disable a policy, the zone policies may not assume their role, compromising the zone anomaly detection function.
If you activate the policy construction phase after disabling a zone policy, all zone policies are reconfigured according to the current traffic flow and the policy may be reactivated.
Configuring the Policy Threshold
The policy threshold defines the threshold traffic rate for a specific policy and is adjusted by the threshold tuning phase. When this threshold is exceeded, the policy performs the action that is defined by the policy action.
The threshold is measured in packets per second except for policies that are constructed from the following policy templates:
•
num_soruces—The threshold is measured in the number of IP addresses or ports.
•
tcp_connections—The threshold is measured in the number of connections.
•
tcp_ratio—The threshold is measured as the ratio number.
•
worm_tcp—The threshold is measured as the maximum number of zone destination IP addresses that a source IP may scan.
You can configure the policy threshold in the following ways:
•
Set the threshold—You can set the value of the policy threshold. See the "Setting the Policy Threshold" section.
•
Multiply the threshold—The Detector module multiplies the current policy thresholds by a factor. The new value may change in subsequent threshold tuning phases if you do not set it as fixed. See the "Multiplying a Threshold by a Factor" section.
•
Configure specific IP thresholds—The Detector module sets thresholds for specific IP source addresses within the zone address range. See the "Configuring Specific IP Thresholds" section.
The policy threshold may change if you perform additional threshold tuning phases. You can modify how a threshold may change in subsequent threshold tuning phases in the following ways:
•
Set the threshold as fixed—The Detector module will not change the value of the policy threshold, proxy-threshold, and threshold-list in subsequent threshold tuning phases. See the "Setting the Threshold as Fixed" section.
•
Set a fixed multiplier for the policy threshold—The Detector module calculates the policy threshold in subsequent threshold tuning phases based on the current policy threshold, the learned threshold, and the fixed multiplier. See the "Configuring a Threshold Multiplier" section.
This section contains the following topics:
•
Setting the Threshold as Fixed
•
Configuring a Threshold Multiplier
•
Multiplying a Threshold by a Factor
•
Configuring Specific IP Thresholds
Setting the Policy Threshold
To configure the policy threshold, use the following command in policy configuration mode:
threshold threshold
The threshold argument is a positive number that specifies the policy threshold.
The following example shows how to set the threshold value of the policy /53/analysis/syns/global to 300:
user@DETECTOR-conf-zone-scannet-policy-//53/analysis/syns/ global# threshold 300Setting the Threshold as Fixed
You can set a policy threshold, proxy-threshold, and threshold-list as fixed. The Detector module ignores new thresholds in the threshold tuning phase of the learning process and maintains the current thresholds. Setting a threshold as fixed enables you to configure the thresholds of a policy but continue learning the thresholds of other policies.
To set a policy threshold as fixed, use the following command in policy configuration mode:
learning-params fixed-threshold
The following example shows how to set the threshold of the policy /53/analysis/syns/global as fixed:
user@DETECTOR-conf-zone-scannet-policy-//53/analysis/syns/global# learning-params fixed-thresholdYou can set the threshold of several policies as fixed in a single command by entering the command in zone configuration mode. To set a policy threshold as fixed while in zone configuration mode, use the following command:
policy policy-path learning-params fixed-threshold
The policy-path argument specifies the policy path. The path can be a partial path that includes only part of the policy sections. See the "Understanding Zone Policies" section for more information.
The following example shows how to set the thresholds of all policies that were created from the policy template as fixed:
user@DETECTOR-conf-zone-scannet# policy learning-params fixed-thresholdTo display the policy learning parameters, use the show learning-params command in policy configuration mode, or use the show policies policy-path learning-params command in zone configuration mode.
Configuring a Threshold Multiplier
You can set a multiplier for a policy threshold. The Detector module calculates a new policy threshold by multiplying the learned threshold by the specified multiplier before accepting the results of subsequent threshold tuning phases. The Detector module accepts the results of the threshold tuning phase using the configured threshold selection method. See the "Configuring the Threshold Selection Method" section.
To set a multiplier for the policy threshold, use the following command in zone configuration mode:
policy policy-path learning-params threshold-multiplier threshold-multiplier
Table 7-10 provides the arguments and keywords for the policy learning-params threshold-multiplier command.
Table 7-10 Arguments and Keywords for the policy learning-params threshold-multiplier Command
policy-path
Policy path for which to multiply the thresholds. The path can be a partial path that includes only part of the policy sections. See the "Understanding Zone Policies" section for more information.
learning-params
Configures the learning parameters.
threshold-multiplier threshold-multiplier
Multiplies the policy threshold. The threshold-multiplier is a real positive number (a floating point number with two decimal places) by which the policy threshold is multiplied. Enter a number less than 1 to decrease the policy threshold.
To set a multiplier for the policy threshold in policy configuration mode, use the learning-params threshold-multiplier threshold-multiplier command.
The following example shows how to configure a threshold multiplier so that the Detector module decreases the thresholds of policies that were created from the policy template by half in subsequent threshold tuning phases:
user@DETECTOR-conf-zone-scannet# policy learning-params threshold-multiplier 0.5To display the policy learning parameters, use the show learning-params command in policy configuration mode, or use the show policies policy-path learning-params command in zone configuration mode.
Multiplying a Threshold by a Factor
You can multiply the thresholds of a policy or a group of policies by a factor, which enables you to increase or decrease the threshold of a policy or a group of policies if the traffic volume does not represent the zone traffic. You can enable the Detector module to multiply the policy thresholds, the proxy thresholds, and the thresholds that were defined by the policy threshold-list command.
To multiply policy thresholds by a factor, use the following command in zone configuration mode:
policy policy-path thresh-mult threshold-multiply-factor
Table 7-11 provides the arguments and keywords for the policy thresh-mult command.
Table 7-11 Arguments and Keywords for the policy thresh-mult Command
policy-path
Policy template name. See Table 7-1 for more information.
thresh-mult threshold-multiply-factor
Specifies a real positive number (a floating point number with 4 decimal places) by which to multiply the threshold. Enter a number less than 1 to decrease the policy threshold.
The following example shows how to decrease the thresholds of policies that were created from the policy template by half:
user@DETECTOR-conf-zone-scannet# policy */*/*/*/src_ip thresh-mult 0.5
Note
The Detector module may change the threshold value in subsequent threshold tuning phases. To prevent the Detector module from changing the threshold value, set the threshold value as fixed. See the "Setting the Threshold as Fixed" section.
To display the policy learning parameters, use the show learning-params command in policy configuration mode, or use the show policies policy-path learning-params command in zone configuration mode.
Configuring Specific IP Thresholds
You can avoid false attack detections by the Detector module when traffic increases on a known high traffic source or destination IP address by configuring a policy with a threshold for traffic that is associated with that IP address.
You should consider configuring a specific IP threshold if one of the following situations occurs:
•
When there is known high-volume traffic from a source IP address, you can configure a threshold to apply to traffic that originates from the specific source IP address.
•
When there is a nonhomogeneous zone (a zone that consists of more than a single IP address) and there is known high-volume traffic flowing to part of the zone only, you can configure a threshold to apply to traffic that targets the specific destination IP address within the zone.
You can configure a specific IP threshold only for policies with traffic characteristics of destination IP (dest_ip).
To configure a specific IP threshold, use one of the following commands:
•
policy policy-path threshold-list ip threshold [ip threshold ...]—Use this command from zone configuration mode
•
threshold-list ip threshold [ip threshold ...]—Use this command from policy configuration mode
Table 7-12 provides the arguments for the threshold-list command.
Table 7-12 Arguments for the policy threshold-list Command
policy-path
Policy template name. See Table 7-1 for more information.
ip
Specific IP address.
threshold
Threshold traffic rate in packets per second, except for policies that measure concurrent connections and SYN-by-FIN ratio where the threshold is the number of connections.
You can add a maximum of 10 specific IP thresholds for each policy. You can enter all specific IP thresholds in a single command.
The Detector module might change the policy thresholds in subsequent threshold tuning phases if the threshold selection method is set to new-thresholds. See the "Configuring the Threshold Selection Method" section for more information.
The following example shows how to set specific IP thresholds for IP addresses 10.10.10.2 and 10.10.15.2 for the policy http/80/analysis/syns/src_ip:
user@DETECTOR-conf-zone-scannet-policy-/http/80/analysis/syns/src_ip#threshold-list 10.10.10.2 500 10.10.15.2 500Configuring the Policy Timeout
The timeout parameter defines the minimum time for dynamic filters that are produced by the policy to apply their action.
To configure the policy timeout, use the following command in policy configuration mode:
timeout {forever | timeout}
Table 7-13 provides the arguments and keywords for the timeout command.
The following example shows how to set the timeout of the policy http/80/analysis/syns/src_ip to 100 seconds:
user@DETECTOR-conf-zone-scannet-policy-/http/80/analysis/syns/src_ip#timeout 100To change the timeout of a group of policies simultaneously, use the policy set-timeout command in zone configuration mode.
The following example shows how to set the timeout of all policies that were produced from the HTTP policy template and measure source IP addresses to 100:
user@DETECTOR-conf-zone-scannet#policy http/*/*/*/src_ip set-timeout 100Configuring the Policy Action
The action parameter defines the type of action that the policy takes once its threshold is exceeded.
To configure the policy action, use the following command in policy configuration mode:
action policy-action
Table 7-14 describes the policy actions.
Table 7-14 Policy Actions
notify
Notifies you when its threshold is exceeded.
remote-activate
Activates remote Guards when its threshold is exceeded. The remote Guards are defined in the remote Guard lists. See the "Activating Remote Guards to Protect a Zone" section for more information.
The following example shows how to set the action of the policy http/80/analysis/syns/src_ip:
user@DETECTOR-conf-zone-scannet-policy-/http/80/analysis/syns/src_ip#action remote-activateTo change the action of a group of policies simultaneously, use the policy set-action command in zone configuration mode.
The following example shows how to set the action of all policies:
user@DETECTOR-conf-zone-scannet# policy / set-action remote-activateset action of / to remote-activate:4 policy actions set.Configuring the Detection Time Parameter for PPH Policies
PPH policies monitor zone traffic for low rate zombie attacks and measure traffic rate in packets per hour rather than packets per second (see the "Understanding Zone Policies" section). The detection time parameter defines the time period (in hours) over which the policy counts the packets to determine the traffic rate.
You may want to increase the detection time when you need a longer sampling period in which to discern malicious traffic from legitimate traffic. For example, it is possible for a legitimate user and an attacker to send the same number of packets during a one hour time period. Over a two hour time period, however, the legitimate user may stop sending traffic, resulting in a lower traffic rate, while the traffic rate of the persistent attacker will remain high.
The policy path of a PPH policy contains a packet type identifier with _pph appended to it (for example, syns_pph). For more information on policy paths, see the "Understanding the Policy Path" section.
To configure the detection time parameter, use one of the following commands:
•
policy policy-path detection-time detection-time-int—Use this command in the zone configuration mode
•
detection-time detection-time-int—Use this command in the policy configuration mode
The detection-time-int argument specifies the detection time in hours. Enter a value from 1 to 48. The default is 1.
The following example shows how to set the detection time of the policy tcps_services/any/strong/reqs_pph/src_ip to 8 hours:
user@DETECTOR-conf-zone-scannet-policy-/tcp_services/any/strong/reqs_pph/src_ip# detection-time 8Configuring the Policy Interactive Status
The interactive status parameter defines the interactive status that the pending dynamic filters, which are created by the zone policy, will assume. The interactive status applies only to zones if you enable zone anomaly detection, and the zone is in interactive detect mode. See Chapter 10 "Using Interactive Detect Mode," for more information.
To modify the status of the pending dynamic filters that a policy produces after you have set the interactive status of a recommendation to always-accept or always-ignore, use the interactive-status command.
For example, if you have defined the status of a recommendation to always-accept, the recommendation and the pending dynamic filters of the recommendation are no longer displayed. To ignore the recommendation or the pending dynamic filters that the recommendation produces, change the policy interactive status to interactive or always-accept.
To configure the policy interactive status, use the following command in policy configuration mode:
interactive-status {always-accept | always-ignore | interactive}
Table 7-15 provides the keywords for the interactive-status command.
The following example shows how to configure the interactive status of policy dns_tcp/53/analysis/pkts/src_ip to always-accept:
user@DETECTOR-conf-zone-scannet-policy-/dns_tcp/53/analysis/pkts/ src_ip# interactive-status always-acceptUnderstanding Worm Policies
Internet worms are automated, self-propagating, intrusive agents that make copies of themselves and facilitate their distribution. Worms attack a vulnerable host, infect it, and then use it as a base to attack other vulnerable targets. They search for other targets by using a form of network inspection, typically a scan, and propagate to the next target. A scanning worm locates vulnerable hosts by generating a list of addresses to probe and then contacting the hosts. Code Red worm, Sasser worm, Blaster worm, and the Slammer worm are all examples of high-profile worms that spread in this manner.
The Detector module enables you to detect TCP worm attacks by identifying worms through abnormal traffic patterns that indicate that the zone network is being scanned. The Detector module assumes that even if no TCP worm attack is in progress, there may be some scanners in the network. It identifies a scanner as a source IP address that is the initiator of nonestablished connections (an incoming SYN packet for which no SYN/ACK reply packet was identified) to many zone destination IP addresses on a specific port.
To analyze the zone traffic, the Detector module uses a table that holds frequency data, which is known as a histogram, of network scanners. The Detector module first learns the zone network when no attack is in progress, and then it creates a histogram of concurrent scanners. The histogram describes the number of scanners that concurrently scan specific numbers of zone destination IP addresses. The Detector module then measures how many scanners access more than a specific number of zone destination IP addresses.
The Detector module uses two types of thresholds to analyze worm traffic characteristics:
•
Scanning threshold—Defines the maximum number of zone IP addresses that a single source IP address may scan. This threshold is defined by the policy threshold.
•
Histogram threshold—Defines the maximum number of source IP addresses that can scan more than the specified numbers of zone IP addresses.
The Detector module identifies a worm attack when there is a deviation from the histogram that it has learned when no attack was in progress (that is, when the number of source IP addresses that concurrently scan more than the defined zone destination IP addresses is exceeded). See the "Identifying Worm Attacks" section for more information.
Worm policies differ from other policies as follows:
•
The Detector module learns new services for worm policies during the threshold tuning phase, rather than during the policy construction phase, so you may see new services (ports) added to worm policies during the threshold tuning phase.
•
The service any relates to ports for which the Detector module does not have specific policies. For example, if the Detector module has policies for worm_tcp/80 and worm_tcp/50, the policy worm_tcp/any monitors all traffic that is not destined to ports 50 or 80. Unlike other policies, the any service does not aggregate the traffic to all unspecified ports. When the Detector module monitors the zone traffic, it holds a separate, internal histogram for each port that is scanned. It compares this histogram with the histogram of the any service.
This section contains the following topics:
Configuring Worm Policies
The worm_tcp policy template is available in the DETECTOR_WORM zone template only.
The policies that manage TCP worms are constructed from the worm_tcp policy template, the non_estb_conns packet type, and the scanner's traffic characteristics.
You can configure the histogram and change the scanning thresholds by entering the following command in policy configuration mode:
histogram num-dst-ips num-src-ips [num-dst-ips num-src-ips...]
Table 7-16 provides the arguments for the histogram command.
You can enter all the histogram thresholds in a single command.
The following example shows how to set the histogram thresholds for all frequencies:
user@DETECTOR-conf-zone-scannet- worm_tcp/445/analysis/non_estb_conns/scanners#histogram 5 99 20 80 50 8 100 1To display the current histogram settings, use the show policies command.
You can set the maximum number of zone IP addresses that a single source IP address may scan (scanning threshold). To set this number, use the threshold command. See the "Configuring the Policy Threshold" section for more information.
To specify the histogram thresholds for a specific port, use the add-service command to add a service for the specific port number to all policies that were created from the worm_tcp policy template. See the "Adding a Service" section for more information.
Identifying Worm Attacks
The Detector module uses two types of thresholds to analyze worm traffic characteristics: a scanning threshold and a histogram threshold. See the "Understanding Worm Policies" section for more information.
When a histogram threshold is exceeded, the Detector module produces a dynamic filter with an unspecified source IP address (*). This dynamic filter indicates that a worm attack is in progress. The dynamic filter policy threshold specifies which histogram threshold was exceeded. The Detector module defines a new, internal scanning threshold that is equal to the dynamic filter policy threshold.
The source IP addresses that scan the zone destination IP addresses are those of worm-infected hosts. As long as the zone is under attack, each worm-infected host that scans more zone destination IP addresses than the maximum defined by the new, internal scanning threshold causes the production of a dynamic filter. The Detector module acts on these attacking flows as defined by the dynamic filter action.
For example, if the policy threshold (the scanning threshold) is 300, and the policy scanner's histogram for port 445 is as shown in Table 7-17, then if the Detector module identifies a scanner that scans 350 zone destination IP addresses, it produces a dynamic filter indicating that a mass scanner was detected. However, this scanner does not yet imply that a worm attack is in progress.
Table 7-17 Sample Histogram
Number of source IP addressesNumber of Destination IP addresses
When the Detector module identifies six concurrent source IP addresses that scan more than 50 zone destination IP addresses on port 445, it produces a dynamic filter from the worm_tcp policy with an unspecified source IP address (*) that indicates that the Detector module has identified a worm attack on port 445. The dynamic filter policy threshold, 50, specifies the new internal scanning threshold and causes the Detector module to lower the threshold definition of a scanner, so that the Detector module produces additional dynamic filters for each source IP address that scans more than the new scanning threshold (50).
Monitoring Policies
You can monitor the policies to see how well they are suited to the zone traffic volume and services.
This section contains the following topics:
Displaying Policies
You can display the zone policies to verify that they are adapted to the zone traffic characteristics. You might want to view the zone-constructed policies to verify that these policies are customized for the traffic characteristics of the zone. You can configure only policies that appear in this list.
The Detector module displays only current zone policies. If a policy template was disabled during the policy construction phase, the Detector module does not create policies from that policy template, and you do not see these policies when you enter the show policies command.
To display the zone policies, use the following command in zone configuration mode:
show policies policy-path
The policy-path argument specifies a group of policies. You can use an asterisk (*) as a wildcard character in each policy path section. If you do not specify a policy path section, the Detector module considers the unspecified section to be a wildcard (*). For example, the policy tcp_services//analysis//global uses wildcards for the service and the packet type sections.
To display the statistics of all policies, enter an asterisk (*) for the policy path.
See the "Understanding Zone Policies" section for more information about the policy path sections.
The following example shows how to display all the zone policies:
user@DETECTOR-conf-zone-scannet#show policies *The following example shows how to display all policies that monitor DNS-over-TCP synchronization packets on port 53:
user@DETECTOR-conf-zone-scannet#show policies dns_tcp/53/*/syns/*Table 7-18 describes the fields in the show policies command output.
Table 7-18 Field Descriptions of the show policies Command Output
Policy
Policy name. See the "Understanding Zone Policies" section for more information about the policy path sections.
State
Policy state. See the "Changing the Policy State" section for more information.
act = active, inact = inactive, disab= disabled
IStatus
Policy interactive status. See the "Configuring the Policy Interactive Status" section for more information.
a-accept = always-accept, a-ignor = always-ignore,
interac = interactiveThreshold
Policy threshold. When traffic rate exceeds this threshold, the Detector module executes the action associated with the policy. See the "Configuring the Policy Threshold" section for more information.
List
Number of specific IP thresholds defined for the policy. See the "Configuring Specific IP Thresholds" section for more information. Displays H (histogram) for policies that relate to worms. See the "Understanding Worm Policies" section for more information.
Action
Action that the Detector module executes when the traffic exceeds the policy threshold. See the "Configuring the Policy Action" section for more information.
Timeout
Minimum time span that the policy action is valid. The Detector module determines, according to the filter-termination thresholds, whether or not the dynamic filter that was produced by the policy is to be inactivated. See the "Configuring the Policy Timeout" section for more information.
Displaying Policy Statistics
You can display the rate of the traffic flowing through a zone policy or a group of zone policies and you can determine whether the type of services and volume represent the zone traffic. The Detector module displays the traffic flows forwarded to the zone with the highest rates as measured by the policies. The rate is calculated based on traffic samples.
To display the policy statistics, use the following command in zone configuration mode:
show policies policy-path statistics [num-entries]
Table 7-19 provides the arguments for the show policies statistics command output.
Table 7-19 Arguments for the show policies statistics Command
policy-path
Group of policies for which to display statistics.
You can use an asterisk (*) as a wildcard character in each policy path section. If you do not specify a policy path section, the Detector module relates to the unspecified section as a wildcard (*). For example, the policy tcp_services//analysis//global uses wildcards for the service and the packet type sections.
To display the statistics of all policies, enter an asterisk (*) for the policy-path.
See the "Understanding Zone Policies" section for more information about the policy path sections.
num-entries
(Optional) Number of entries to display. Enter a number from 1 to 100. The Detector module displays the policies with the highest values.
The following example shows how to display the statistics of all the zone policies:
user@DETECTOR-conf-zone-scannet#show policies * statisticsThe following example shows how to display the statistics of all policies that monitor DNS-over-TCP synchronization packets on port 53:
user@DETECTOR-conf-zone-scannet#show policies dns_tcp/53/*/syns/*The following example shows how to display the statistics of the zone global traffic:
user@DETECTOR-conf-zone-scannet#show policies */*/*/*/global statisticsTable 7-20 describes the fields in the tables of the show policies statistics command output. The Detector module sorts the output and displays it in four tables: Rates, Rates (pph), Connections, and Ratios. The information in each table is sorted by value, with the highest values appearing at the top of the table. If a table does not contain any information, the Detector module does not display it.
Table 7-20 Field Descriptions of the show policies statistics Command Output Tables
Key
Key that is the traffic characteristic used to aggregate the policies.
For example, in the tcp_services/any/analysis/syns/dst_ip policy, the key is the destination IP address (dst_ip). If the traffic characteristic that was used to aggregate the policies is global, the key displays N/A.
In policies that relate to worms, such as worm_tcp/any/analysis/non_estb_conns/scanners, the key is the the source IP address that scans the zone network addresses, colon, and the destination port that is being scanned, as shown in this example: 192.128.100.3:70.
See Table 7-8 for more information.
Policy
Policy name. See the "Understanding Zone Policies" section for more information.
Rate
Rate of the traffic that flows through the policy and is measured in packets per second (pps). The rate is calculated based on traffic samples.
Rate (pph)
Rate of the traffic as determined by the policies that measure traffic rate in packets per hour (pph).When you enter the command beyond the first hour of an attack, the Detector module displays the average packet per hour rate that occurred over the past two hours.
This field displays only when you enable the PPH policies, which are disabled by default (see the "Changing the Policy State" section).
Connection
Number of concurrent connections. This information is available for tcp_connections policies with a packet type of in_nodata_conns.
Ratio
Ratio between the number of SYN flagged packets and the number of FIN/RST flagged packets. This information is available for syn_by_fin policies only.
Dst IPs
Number of zone destination IP addresses that were scanned. This information is available for worm_tcp policies only.
Backing Up the Policy Configuration
You can back up the current zone policies at any time by using the snapshot threshold-selection cur-thresholds command in zone configuration mode.
The following example shows how to create a snapshot to back up the current policy configuration:
user@DETECTOR-conf-zone-scannet#snapshot threshold-selection cur-thresholds

 Feedback
Feedback