-
Cisco Traffic Anomaly Detector Module Configuration Guide (Software Version 6.1 and 6.1-XG)
-
Index
-
Preface
-
Product Overview
-
Configuring the Detector Module on the Supervisor Engine
-
Initializing the Detector Module
-
Configuring the Detector
-
Configuring Zones
-
Configuring Zone Filters
-
Configuring Policy Templates and Policies
-
Learning the Zone Traffic Characteristics
-
Detecting Zone Traffic Anomalies
-
Using Interactive Detect Mode
-
Using Attack Reports
-
Using Detector Module Diagnostic Tools
-
Performing Maintenance Tasks
-
Table Of Contents
Understanding the Detector Module
Understanding Nonspoofed Attacks
Understanding Zones, Zone Policies, and the Learning Process
Understanding the Zone Policies
Understanding the Learning Process
Understanding the Anomaly Detection Process
Understanding the Different Anomaly Detection Modes
Understanding the Detect and Learn Function
Understanding the 1-Gbps and 2-Gbps Bandwidth Options
Product Overview
This chapter provides a general overview of the Cisco Traffic Anomaly Detector Module (Detector module) including its major components and how they work together to help protect network elements by detecting malicious attack traffic.
The chapter contains the following sections:
•
Understanding the Detector Module
•
Understanding Zones, Zone Policies, and the Learning Process
•
Understanding the Anomaly Detection Process
•
Understanding the 1-Gbps and 2-Gbps Bandwidth Options
Understanding the Detector Module
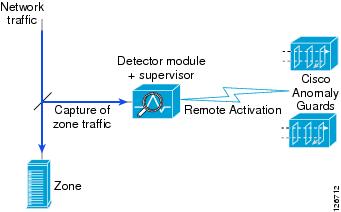
The Detector module monitors a copy of the network traffic, continuously looking for indications of a Distributed Denial of Service (DDoS) attack against a network element, or zone, such as a server, firewall interface, or router interface.
You can install the Detector module in one of the following Cisco products:
•
Catalyst 6500 series switch
•
Cisco 7600 series router
Using port mirroring or a fiber optic link splitter, you configure the switch or router to capture the traffic sent to the zone and pass a copy of it to the Detector module.
The Detector module can operate as an independent DDoS detection and alarm component; however, it works optimally with the Cisco Guard (Guard), the companion product of the Detector module.
Note
The Guard is a DDoS attack detection and mitigation device that cleans the zone traffic as the traffic flows through it, dropping the attack traffic and injecting the legitimate traffic back into the network. When the Detector module determines that the zone is under attack, it can activate the Guard attack mitigation services. The Detector module can also synchronize zone configurations with the Guard. For more information about the Guard, see the Cisco Anomaly Guard Module Configuration Guide or the Cisco Guard Configuration Guide.
The Detector module uses a set of zone policies to analyze a copy of all inbound zone traffic. The zone policies enable the Detector module to identify traffic anomalies that indicate an attack on the zone. When the Detector module identifies a traffic anomaly, it can issue a syslog message to notify you of the attack or it can activate a Guard to mitigate the attack.
The Detector module allows you to do the following tasks:
•
Traffic learning—Learns the characteristics (services and traffic rates) of normal zone traffic using an algorithm-based process. During the learning process, the Detector module modifies the default zone traffic policies and policy thresholds to match the characteristics of normal zone traffic. The traffic policies and thresholds define the reference points that the Detector module uses to determine when the zone traffic is normal or abnormal (indicating and attack on the zone).
•
Traffic anomaly detection—Detects anomalies in zone traffic based on normal traffic characteristics.
Figure 1-1 shows a sample network application in which the Detector module receives a copy of the network traffic for analysis.
Figure 1-1 Cisco Traffic Anomaly Detector Module Operation
Understanding DDoS Attacks
DDoS attacks deny legitimate users access to a specific computer or network resource. These attacks are launched by individuals who send malicious requests to targets that degrade service, disrupt network services on computer servers and network devices, and saturate network links with unnecessary traffic.
This section contains the following topics:
•
Understanding Spoofed Attacks
•
Understanding Nonspoofed Attacks
Understanding Spoofed Attacks
A spoofed attack is a type of DDoS attack in which the packets contain an IP address in the header that is not the actual IP address of the originating device. The source IP addresses of the spoofed packets can be random or have specific, focused addresses. Spoofed attacks saturate the target site links and the target site server resources. It is easy for a computer hacker to generate high volume spoofed attacks even from a single device.
Understanding Nonspoofed Attacks
Nonspoofed attacks (or client attacks) are mostly TCP-based with real TCP connections that can overwhelm the application level on the server rather than the network link or operating system.
Client attacks from a large number of clients (or zombies) may overwhelm the server application even without any of the individual clients creating an anomaly. The zombie programs try to imitate legitimate browsers that access the target site.
Understanding Zones, Zone Policies, and the Learning Process
This section describes what a Detector module zone represents, how zone policies detect traffic anomalies, and how the Detector module learns the zone traffic characteristics.
These sections contain the following topics:
•
Understanding the Zone Policies
•
Understanding the Learning Process
Understanding Zones
A zone that the Detector module monitors for traffic anomalies can be one of the following elements:
•
A network server, client, or router
•
A network link, subnet, or an entire network
•
An individual Internet user or a company
•
An Internet Service Provider (ISP)
•
Any combination of these elements
When you create a new zone, you assign a name to it and configure the zone with network addresses. The Detector module configures the zone with a default set of policies and policy thresholds to detect anomalies in the zone traffic.
The Detector module can protect multiple zones at the same time if the network address ranges do not overlap.
For more information about zones, see Chapter 5 "Configuring Zones."
Understanding the Zone Policies
The policies associated with the zone configuration enable the Detector module to detect anomalies in the zone traffic. When the traffic flow exceeds a policy threshold, the Detector module identifies the traffic as abnormal or malicious and dynamically configures a set of filters (dynamic filters) to apply the appropriate detection level to the traffic flow according to the severity of the attack.
For more information about zone policies, see Chapter 7 "Configuring Policy Templates and Policies."
Understanding the Learning Process
The learning process enables the Detector module to analyze normal zone traffic and create a set of zone-specific policies and policy thresholds that enable the Detector module to more accurately detect zone traffic anomalies.
You enable the learning process to replace the default set of zone policies or to update the current set of zone policies that may not be configured properly to recognize current normal traffic services and volume. When policy thresholds are set too high compared to the current normal traffic volume, the Detector module might not be able to detect traffic anomalies (attacks). When policy thresholds are set too low, the Detector module may mistake legitimate traffic for attack traffic.
The learning process consists of the following two phases:
•
Policy Construction Phase—Creates the zone policies for the main services that the zone traffic uses. To create zone policies, the Detector module follows the rules established by the policy templates that each zone configuration contains.
•
Threshold Tuning Phase—Tunes the thresholds of the zone policies to values that are appropriate for recognizing the normal traffic rates of the zone services.
For more information about the learning process, see Chapter 8 "Learning the Zone Traffic Characteristics."
Understanding the Anomaly Detection Process
This section describes how the Detector module detects zone traffic anomalies and generates attack reports.
This section contains the following topics:
•
Understanding Traffic Filters
•
Understanding the Different Anomaly Detection Modes
•
Understanding the Detect and Learn Function
Understanding Traffic Filters
The Detector module uses three types of traffic filters to apply the required anomaly detection level to the zone traffic. You can configure these filters to customize the traffic flow and control the DDoS detection operation.
The Detector module uses the following types of traffic filters:
•
Bypass filters—Prevent the Detector module from applying DDoS detection measures to specific traffic flows.
•
Flex-content filters—Count a specified traffic flow and filter according to fields in the IP and TCP headers and content bytes.
•
Dynamic filters—Apply the analysis detection level to the traffic flow. When the Detector module detects an anomaly during the analysis process, the dynamic filters instruct the Detector module to either record the event in the syslog or activate a Guard to protect the zone.
The Detector module coordinates the actions of the zone policies that monitor the zone traffic for anomalies with the zone filters.
For more information about filters, see Chapter 6 "Configuring Zone Filters."
Understanding the Different Anomaly Detection Modes
You can activate the Detector module anomaly detection operation in the following ways:
•
Automatic detection mode—The Detector module automatically activates the dynamic filters that it creates.
•
Interactive detect mode—The Detector module builds a queue of the dynamic filters that it creates and then groups the filters as recommended actions. You review the recommendations and decide whether to accept, ignore, or direct these recommendations to automatic activation. For more information about the interactive detect mode, see Chapter 10 "Using Interactive Detect Mode."
Understanding the Detect and Learn Function
You can activate the threshold tuning phase of the learning process and activate zone anomaly detection simultaneously (the detect and learn function) to enable the Detector module to learn the new zone policy thresholds and at the same time monitor the traffic for anomalies using the current thresholds. When the Detector module detects an attack, it stops the learning process but continues to monitor the traffic for anomalies. This process prevents the Detector module from learning malicious traffic thresholds during an attack.
For more information about the detect and learn function, see the "Enabling the Detect and Learn Function" section.
Understanding Attack Reports
The Detector module provides an attack report for every zone that provides zone status information and details of the attack, starting with the production of the first dynamic filter, and ending with anomaly detection termination.
For more information about the attack reports, see Chapter 11 "Using Attack Reports."
Understanding the 1-Gbps and 2-Gbps Bandwidth Options
The Detector module can operate at two different bandwidth performance levels: 1 Gigabit per second (Gbps) or 2 Gbps. The software image that you load on the Detector module determines the operating bandwidth by controlling the three physical interfaces between the module and the supervisor engine. The installed software image controls the interfaces as follows:
•
6.0 software image—Provides 1-Gbps throughput, allowing data traffic to move between the supervisor engine and the Detector module over a single interface port. A second interface port is used to transport out-of-band management traffic and activate associated Guard devices. The third interface port is not used.
•
6.0-XG software image—Provides 2-Gbps throughput, enabling two of the interface ports for transporting data traffic. The third interface is dedicated to transporting out-of-band management traffic and activating Guard devices. To use the XG software image, the Detector module requires a software license.
Note
You can order the Detector module with either software image installed or you can upgrade a 6.0 software image (1-Gbps operation) to the 6.0-XG software image (2-Gbps operation). If you order a new Detector module with the 6.0-XG software image, Cisco installs the required license with the software image. For information about upgrading to the 6.0-XG software image, see the "Upgrading the Bandwidth Performance from 1 Gbps to 2 Gbps" section).
Table 1-1 shows the correlation between the Detector module physical interfaces and the supervisor ports. The table also shows how the CLI interface designators for data traffic change after installing the software image for 2-Gbps operation.
The following items describe the VLAN interface configuration differences between the 1-Gbps operation and the 2-Gbps operation:
•
1-Gbps operation—Define the data traffic VLAN on port 1 only.
•
2-Gbps operation—Define the data traffic VLAN on port 1 and port 2. You define different VLANs on each port.

 Feedback
Feedback