瞭解Nexus VPC環路規避
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本文檔介紹在基於Nexus的第3層網路設計中vPC環路規避可能會影響流量轉發的場景。
必要條件
需求
思科建議您瞭解以下主題:
- Nexus作業系統CLI
- vPC概念
採用元件
本文中的資訊係根據以下軟體和硬體版本:
- 軟體10.4(4)
- 硬體N9K-C9364C-GX
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
在當今的資料中心環境中,Cisco Nexus虛擬埠通道(vPC)技術對於實現冗餘和負載均衡至關重要。vPC允許到兩個獨立的Nexus交換機的連線作為單個邏輯埠通道運行,從而簡化了網路架構,提高了下游裝置的可靠性。但是,某些配置詳細資訊可能會帶來操作複雜性。
本文檔探討了vPC環路規避變得重要的場景,並檢查了它對流量轉發的影響。對於希望在基於Nexus的基礎設施中設計和維護強大、高效的第3層連線,從而幫助防止流量中斷並保持最佳網路效能的網路工程師來說,清楚地瞭解此機制至關重要。
問題
在使用vPC的Cisco Nexus環境中,網路操作員可以觀察到vPC環路規避規則導致的意外流量轉發行為。當流量通過vPC對等鏈路從一個vPC對等裝置傳輸到另一個時,它無法通過兩台交換機上處於活動狀態的任何vPC埠通道退出。因此,依賴此連線路徑的裝置可能會遇到資料包丟失或連線斷開的情況,即使所有物理鏈路似乎都已啟動。
瞭解和記帳vPC環路規避規則對於設計和排除恢復性網路拓撲故障至關重要,因為忽略此行為可能會導致意外服務中斷,並使網路問題更難以診斷。
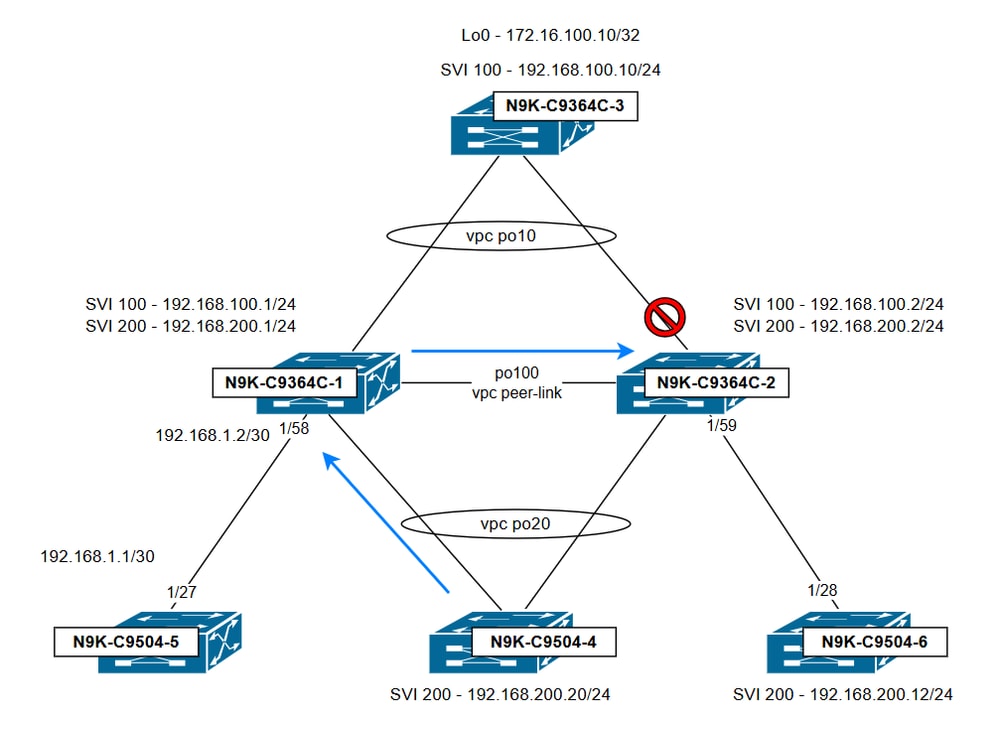
網路圖表
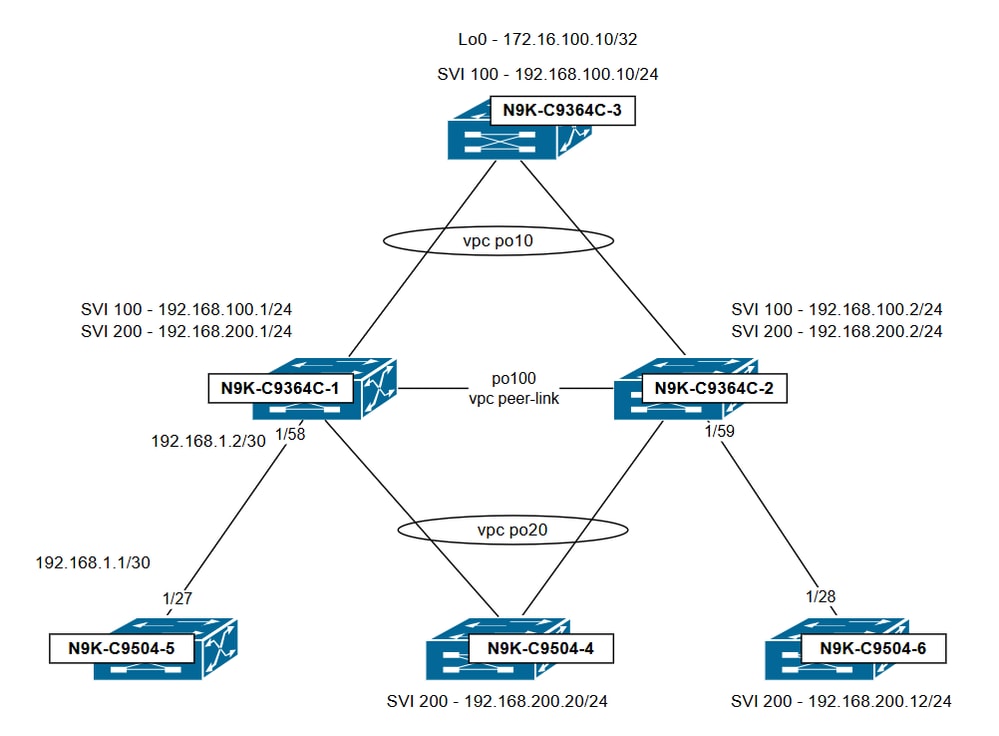
在此拓撲中,vPC域由N9K-C9364C-1和N9K-C9364C-2組成。兩台交換機均配置了VLAN 100和200作為vPC VLAN,並為每個VLAN設定SVI。vPC域負責這些VLAN之間的VLAN間路由。除非另有指定,否則vPC對等交換機之間共用的HSRP虛擬IP(VIP)將用作拓撲中其他交換機預設路由的下一跳。
- N9K-C9364C-1 SVI配置
interface Vlan100
no shut
no ip redirects
ip address 192.168.100.1/24
no ipv6 redirects
hsrp 100
ip 192.168.100.254
interface Vlan200
no shut
no ip redirects
ip address 192.168.200.1/24
no ipv6 redirects
hsrp 200
ip 192.168.200.254
- N9K-C9364C-2 SVI配置
interface Vlan100
no shut
no ip redirects
ip address 192.168.100.2/24
no ipv6 redirects
hsrp 100
ip 192.168.100.254
interface Vlan200
no ip redirects
ip address 192.168.200.2/24
no ipv6 redirects
hsrp 200
ip 192.168.200.254
案例
案例 1:vPC VLAN的SVI在vPC對等體上管理性關閉
a)從vPC到vPC的路由流量受影響
在工作場景中,N9K-C9504-4(VLAN 200)可以成功ping N9K-C9364C-3(VLAN 100)。 Traceroute表示連線路徑通過192.168.200.2,該路徑分配給N9K-C9364C-2。
N9K-C9504-4# ping 192.168.100.10
PING 192.168.100.10 (192.168.100.10): 56 data bytes
64 bytes from 192.168.100.10: icmp_seq=0 ttl=253 time=8.48 ms
64 bytes from 192.168.100.10: icmp_seq=1 ttl=253 time=0.618 ms
64 bytes from 192.168.100.10: icmp_seq=2 ttl=253 time=0.582 ms
64 bytes from 192.168.100.10: icmp_seq=3 ttl=253 time=0.567 ms
64 bytes from 192.168.100.10: icmp_seq=4 ttl=253 time=0.55 ms
--- 192.168.100.10 ping statistics ---
5 packets transmitted, 5 packets received, 0.00% packet loss
round-trip min/avg/max = 0.55/2.159/8.48 ms
N9K-C9504-4#
N9K-C9504-4# traceroute 192.168.100.10
traceroute to 192.168.100.10 (192.168.100.10), 30 hops max, 40 byte packets
1 192.168.200.2 (192.168.200.2) 1.129 ms 0.602 ms 0.724 ms <<<---- SVI 200 on N9K-C9364C-2
2 192.168.100.10 (192.168.100.10) 1.001 ms 0.657 ms 0.588 ms
此時,流量工作方式如下:
- N9K-C9364C-2接收來自192.168.200.20、目的地為192.168.100.10的流量,並將目的MAC地址設定為vPC域中的共用HSRP虛擬MAC(VMAC)。
- 由於HSRP從vPC的資料平面角度以主用 — 主用模式運行,因此N9K-C9364C-2將流量從VLAN 200路由到VLAN 100並通過vPC 10轉發出去。
請考慮以下場景:在N9K-C9364C-2上關閉SVI 200,但在N9K-C9364C-1上保持活動狀態:
N9K-C9364C-1# show ip interface brief
IP Interface Status for VRF "default"(1)
Interface IP Address Interface Status
Vlan100 192.168.100.1 protocol-up/link-up/admin-up
Vlan200 192.168.200.1 protocol-up/link-up/admin-up <<<---- SVI 200 is up
N9K-C9364C-1#
N9K-C9364C-2# show ip interface brief
IP Interface Status for VRF "default"(1)
Interface IP Address Interface Status
Vlan100 192.168.100.2 protocol-up/link-up/admin-up
Vlan200 192.168.200.2 protocol-down/link-down/admin-down <<<---- SVI 200 is down
N9K-C9364C-2#
由於vPC對等體之間SVI的操作狀態不同,在vPC域內檢測到第2類不一致:
N9K-C9364C-1# show vPC
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 100
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : failed
Type-2 inconsistency reason : SVI type-2 configuration incompatible
vPC role : primary
Number of vPCs configured : 2
Peer Gateway : Enabled
Dual-active excluded VLANs : -
Graceful Consistency Check : Enabled
Auto-recovery status : Disabled
Delay-restore status : Timer is off.(timeout = 30s)
Delay-restore SVI status : Timer is off.(timeout = 10s)
Delay-restore Orphan-port status : Timer is off.(timeout = 0s)
Operational Layer3 Peer-router : Disabled
Virtual-peerlink mode : Disabled
vPC Peer-link status
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ -------------------------------------------------
1 Po100 up 1,100,200
vPC status
----------------------------------------------------------------------------
Id Port Status Consistency Reason Active vlans
-- ------------ ------ ----------- ------ ---------------
10 Po10 up success success 1,100,200
20 Po20 up success success 1,100,200
N9K-C9364C-1#
N9K-C9364C-2# show vPC
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 100
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : failed
Type-2 inconsistency reason : SVI type-2 configuration incompatible
vPC role : secondary
Number of vPCs configured : 2
Peer Gateway : Enabled
Dual-active excluded VLANs : -
Graceful Consistency Check : Enabled
Auto-recovery status : Disabled
Delay-restore status : Timer is off.(timeout = 30s)
Delay-restore SVI status : Timer is off.(timeout = 10s)
Operational Layer3 Peer-router : Disabled
Virtual-peerlink mode : Disabled
vPC Peer-link status
---------------------------------------------------------------------
id Port Status Active vlans
-- ---- ------ -------------------------------------------------
1 Po100 up 1,100,200
vPC status
----------------------------------------------------------------------------
Id Port Status Consistency Reason Active vlans
-- ------------ ------ ----------- ------ ---------------
10 Po10 up success success 1,100,200
20 Po20 up success success 1,100,200
N9K-C9364C-2#
在這個階段,從192.168.200.20到192.168.100.10的流量不再成功:
N9K-C9504-4# ping 192.168.100.10
PING 192.168.100.10 (192.168.100.10): 56 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
Request 3 timed out
Request 4 timed out
--- 192.168.100.10 ping statistics ---
5 packets transmitted, 0 packets received, 100.00% packet loss
N9K-C9504-4#
有顏色的ping(具有指定MTU大小的ping)用於追蹤此流量所採用的路徑:
N9K-C9504-4# ping 192.168.100.10 count 100 timeout 0 packet-size 1030
PING 192.168.100.10 (192.168.100.10): 1030 data bytes
Request 0 timed out
Request 1 timed out
---- snip -----
Request 98 timed out
Request 99 timed out
--- 192.168.100.10 ping statistics ---
100 packets transmitted, 0 packets received, 100.00% packet loss
N9K-C9504-4# ^C
N9K-C9504-4#
根據N9K-C9364C-2上的介面計數器,此流量在port-channel 20上接收並轉發到port-channel 100(vPC對等鏈路):
N9K-C9364C-2# show interface port-channel 20 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
port-channel20
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress vPC po20
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 100 <<<----- Egress po100 (vPC peer-link)
N9K-C9364C-2#
出現此行為的原因是SVI 200在N9K-C9364C-2上關閉,從而阻止了VLAN 200的本地流量路由。在此場景中,流量通過vPC對等鏈路橋接到N9K-C9364C-1,以便裝置執行VLAN間路由。
檢視N9K-C9364C-1上的介面計數器,可以確認資料包是通過vPC對等鏈路到達該裝置的,但是,在連線到192.168.100.10的vPC埠通道10上未觀察到傳出資料包。
N9K-C9364C-1# show interface port-channel 20 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
port-channel20
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0 <<<----- Expected egress vPC po10. No packets!!!
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress po100 (vPC peer-link)
60. Tx Packets from 1024 to 1518 bytes: = 0
N9K-C9364C-1#
即使流量通過vPC對等鏈路到達N9K-C9364C-1,它也不會轉發到vPC埠通道10。這是因為此vPC的egress_vsl_drop位設定為1,這發生在對等交換機(在本例中為N9K-C9364C-2)上相同vPC埠通道正常運行時。
N9K-C9364C-1# show system internal eltm info interface Po10 | i i vsl
egress_vsl_drop = 1
N9K-C9364C-1#
N9K-C9364C-1# show system internal vPCm info interface Po10 | i "Peer stat|Inform|vPC sta"
IF Elem Information:
MCECM DB Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
PSS Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
Shared Database Information:
Application database Information:
Lock Information:
N9K-C9364C-1#
說明流量及其丟棄位置的拓撲:
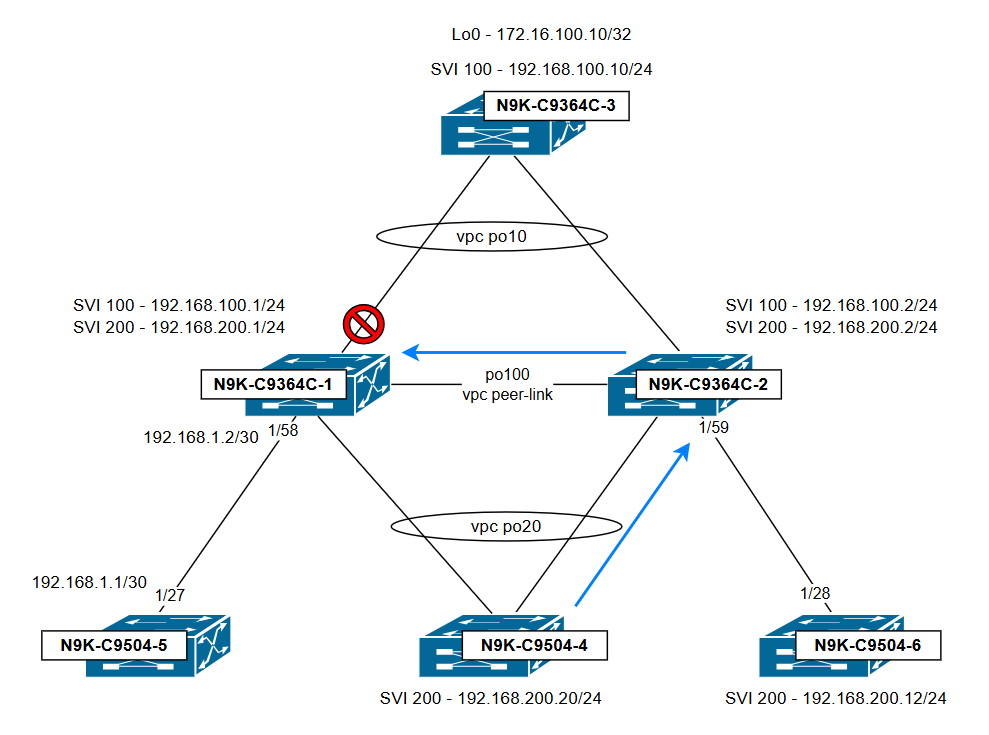
結論:
由於vPC環路規避規則,N9K-C9364C-1丟棄流量:通過vPC對等鏈路接收的流量無法從兩台交換機上處於活動狀態的任何vPC埠通道轉發出去。」要避免此問題,請確保兩台交換機上SVI的管理狀態一致且其配置對稱。
b)從孤立主機到vPC主機的路由流量受影響
考慮在N9K-C9364C-2上關閉SVI 200,但在N9K-C9364C-1上保持活動狀態的相同場景。從N9K-C9504-6(VLAN 200)對N9K-C9364C-3(VLAN 100)執行ping操作不成功。
N9K-C9504-6# ping 192.168.100.10 packet-size 1030 count 100 timeout 0
PING 192.168.100.10 (192.168.100.10): 1030 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
---- snip -----
Request 97 timed out
Request 98 timed out
Request 99 timed out
--- 192.168.100.10 ping statistics ---
100 packets transmitted, 0 packets received, 100.00% packet loss
N9K-C9504-6#
有顏色的ping(具有指定MTU大小的ping)用於追蹤此流量所採用的路徑:
N9K-C9364C-2# show interface eth1/59 counters detailed all | i "1024 to|Eth" ; sh int port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
Ethernet1/59
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress port to N9K-C9504-6
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 100 <<<----- Egress po100 (vPC peer-link)
N9K-C9364C-2#
N9K-C9364C-1# show interface port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0 <<<----- Expected egress vPC po10. No packets!!!
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress po100 (vPC peer-link)
60. Tx Packets from 1024 to 1518 bytes: = 0
N9K-C9364C-1#
即使流量通過vPC對等鏈路到達N9K-C9364C-1,它也不會轉發到vPC埠通道10。這是因為此vPC的egress_vsl_drop位設定為1,這發生在對等交換機(在本例中為N9K-C9364C-2)上相同vPC埠通道正常運行時。
N9K-C9364C-1# show system internal eltm info interface Po10 | i i vsl
egress_vsl_drop = 1
N9K-C9364C-1#
N9K-C9364C-1# show system internal vpcm info interface Po10 | i "Peer stat|Inform|vPC sta"
IF Elem Information:
MCECM DB Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
PSS Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
Shared Database Information:
Application database Information:
Lock Information:
N9K-C9364C-1#
說明流量及其丟棄位置的拓撲:
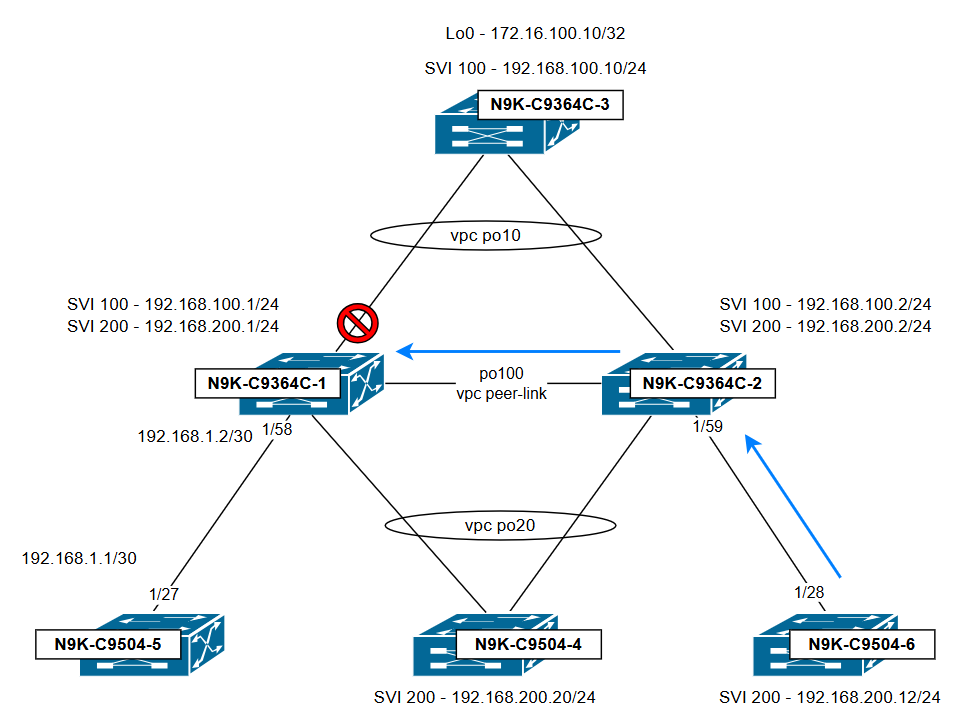
結論:
即使流量來自連線到N9K-C9364C-2的孤立主機,由於vPC環路規避規則,N9K-C9364C-1會丟棄該流量:通過vPC對等鏈路接收的流量無法從兩台交換機上處於活動狀態的任何vPC埠通道轉發出去。對等交換器上的輸入連線埠是vPC還是孤立連線埠不相關;重要的是,流量通過vPC對等鏈路進入,且目的地為兩台交換機上均處於活動狀態的vPC。為避免此問題,請確保兩台交換機上SVI的管理狀態一致且其配置對稱。
場景2:所有vPC和SVI均處於運行狀態 — 指向vPC對等體的下一跳點
在此場景中,vPC域中的所有SVI和vPC埠通道都已啟動。但是,通過第3層介面連線到N9K-C9364C-1的N9K-C9504-5無法ping通N9K-C9364C-3上的Loopback 0。
來自N9K-C9504-5的traceroute表示資料包首先到達192.168.1.2的下一跳,然後繼續到192.168.100.2(與N9K-C9364C-2關聯)。
N9K-C9504-5# traceroute 172.16.100.10
traceroute to 172.16.100.10 (172.16.100.10), 30 hops max, 40 byte packets
1 192.168.1.2 (192.168.1.2) 1.338 ms 0.912 ms 0.707 ms
2 192.168.100.2 (192.168.100.2) 0.948 ms 0.751 ms 0.731 ms
3 * * *
4 * * *
N9K-C9504-5#
從N9K-C9364C-1(此流量的初始躍點)進行的下一跳驗證顯示,可以通過192.168.100.2到達目的地,該目的地對應於N9K-C9364C-2上的SVI 100。
N9K-C9364C-1# show ip route 172.16.100.10
IP Route Table for VRF "default"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%<string>' in via output denotes VRF <string>
172.16.100.0/24, ubest/mbest: 1/0
*via 192.168.100.2, [1/0], 00:05:05, static
N9K-C9364C-1#
有顏色的ping(具有指定MTU大小的ping)用於追蹤此流量所採用的路徑:
N9K-C9364C-1# show interface e1/58 counters detailed all | i "1024 to|Eth" ; sh int port-channel 100 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po"
Ethernet1/58
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress Eth1/58
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 100 <<<----- Egress po100 (vPC peer-link)
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
N9K-C9364C-1#
N9K-C9364C-2# sh int port-channel 100 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po"
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress po100 (vPC peer-link)
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0 <<<----- Egress vPC po10, no packets!!!
N9K-C9364C-2#
即使流量通過vPC對等鏈路到達N9K-C9364C-2,它也不會轉發到vPC埠通道10。這是因為此vPC的egress_vsl_drop位設定為1,這發生在對等交換機(在此情況下,N9K-C9364C-1)上同一vPC埠通道正常運行時。
N9K-C9364C-2# show system internal eltm info interface Po10 | i i vsl
egress_vsl_drop = 1
N9K-C9364C-2# N9K-C9364C-2# show system internal vPCm info interface Po10 | i "Peer stat|Inform|vPC sta"
IF Elem Information:
MCECM DB Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
PSS Information:
vPC state: Up Old Compat Status: Pass
vPC Peer Information:
Peer state: Up <<<------------- vPC 10 up on peer
Shared Database Information:
Application database Information:
Lock Information:
N9K-C9364C-2#
說明流量及其丟棄位置的拓撲:
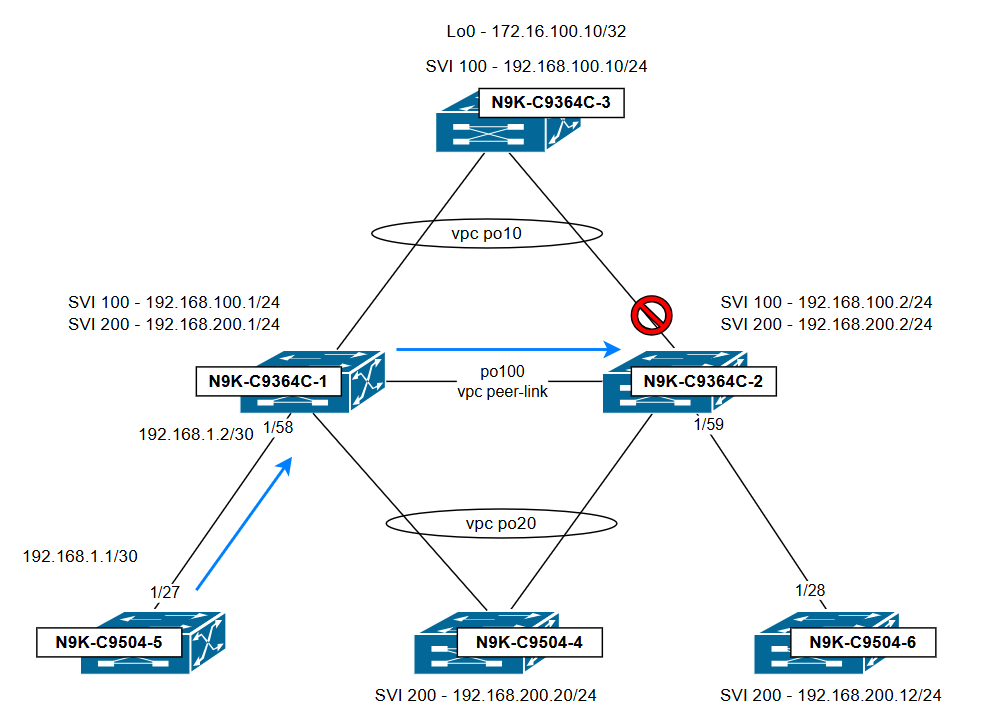
結論:
發現此問題的原因是N9K-C9364C-1使用N9K-C9364C-2作為下一跳,在通過vPC對等鏈路嘗試通過vPC 10退出之前傳送流量。由於vPC環路迴避規則,流量被丟棄:通過vPC對等鏈路接收的流量無法從兩台交換機上處於活動狀態的任何vPC埠通道轉發出去。若要避免此問題,請確保在兩個vPC對等交換機上配置了具有通過vPC埠通道的下一躍點的路由(動態或靜態),以便流量無需通過vPC對等鏈路並通過vPC輸出。
場景3:所有vPC和SVI均啟動 — VPC對等網關功能關閉
在此場景中,所有SVI和vPC埠通道都在vPC域中開啟;但是,vPC對等網關功能已關閉。此時,N9K-C9504-4(VLAN 200)無法ping通N9K-C9364C-3(VLAN 100)。
N9K-C9504-4# ping 192.168.100.10
PING 192.168.100.10 (192.168.100.10): 56 data bytes
Request 0 timed out
Request 1 timed out
Request 2 timed out
Request 3 timed out
Request 4 timed out
--- 192.168.100.10 ping statistics ---
5 packets transmitted, 0 packets received, 100.00% packet loss
N9K-C9504-4#從N9K-C9504-4進行的下一跳驗證顯示,可以通過192.168.200.2到達目的地,該目的地對應於N9K-C9364C-2上的SVI 200,並通過vPC port-channel 20連線。
N9K-C9504-4# show ip route 192.168.100.10
IP Route Table for VRF "default"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%<string>' in via output denotes VRF <string>
0.0.0.0/0, ubest/mbest: 1/0
*via 192.168.200.2, [1/0], 01:22:46, static
N9K-C9504-4#
N9K-C9504-4# show ip arp detail | i 192.168.200.2
192.168.200.2 00:08:05 a478.06de.7edb Vlan200 port-channel20 default
有色ping(具有指定MTU大小的ping)用於追蹤此流量所經過的路徑。此處介面計數器顯示,N9K-C9364C-1通過port-channel 20接收從192.168.200.20到192.168.100.10的流量,並將其傳送到vPC對等鏈路(port-channel100)
N9K-C9364C-1# show interface port-channel 20 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
port-channel20
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress vPC 20
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 100 <<<----- Egress po100 (vPC peer-link)
N9K-C9364C-1#
N9K-C9364C-2通過vPC對等鏈路(port-channel100)接收流量,但不會將其轉發到vPC埠通道10。
N9K-C9364C-2# show int port-channel 20 counters detailed all | i "1024 to|po" ; sh int port-channel 10 counters detailed all | i "1024 to|po" ; sh int port-channel 100 counters detailed all | i "1024 to|po"
port-channel20
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0
port-channel10
52. Rx Packets from 1024 to 1518 bytes: = 0
60. Tx Packets from 1024 to 1518 bytes: = 0 <<<----- Egress vPC po10, no packets!!!
port-channel100
52. Rx Packets from 1024 to 1518 bytes: = 100 <<<----- Ingress po100 (vPC peer-link)
60. Tx Packets from 1024 to 1518 bytes: = 0
N9K-C9364C-2#
即使流量通過vPC對等鏈路到達N9K-C9364C-2,它也不會轉發到vPC埠通道10。這是因為此vPC的egress_vsl_drop位設定為1,這發生在對等交換機上相同vPC埠通道正常運行時(在本例中為N9K-C9364C-1)。
由於對等網關被禁用,N9K-C9364C-1隻能路由發往其本地MAC地址的資料包。因此,發往a478.06de.7edb(來自N9K-C9364C-2的MAC)的資料包由N9K-C9364C-1通過vPC對等鏈路轉發。
N9K-C9364C-1# show mac address-table add a478.06de.7edb
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link,
(T) - True, (F) - False, C - ControlPlane MAC, ~ - vsan
VLAN MAC Address Type age Secure NTFY Ports
---------+-----------------+--------+---------+------+----+------------------
* 100 a478.06de.7edb static - F F vPC Peer-Link(R)
* 200 a478.06de.7edb static - F F vPC Peer-Link(R)
N9K-C9364C-1# 說明流量及其丟棄位置的拓撲:
結論:
如果啟用對等網關,則通過將對等MAC程式設計為網關,本地處理目的地為vPC對等體的MAC地址的路由流量。這可防止vPC對等鏈路在流量路徑中使用,並避免由vPC環路規避規則引起的丟棄。要防止此類問題,請確保在vPC域上啟用vPC對等網關功能。
解決方案概述
- 在vPC VLAN上保持SVI配置一致。
vPC對等交換機之間的非對稱交換虛擬介面(SVI)配置可能會導致嚴重的流量轉發問題,包括流量黑洞。造成這種情況的一個常見但不受支援的做法是通過在一端關閉SVI來測試vPC對等體之間的故障切換。此方法建立Nexus vPC架構不支援的非對稱SVI狀態,從而導致流量黑屏和轉發故障。確保需要路由的所有vPC VLAN上的SVI配置始終一致。
- 在vPC域上啟用對等網關。
對等網關功能是Cisco Nexus vPC部署的關鍵增強功能。在vPC域上啟用時,它允許每個vPC對等交換機接受和處理目的地為vPC對等裝置的虛擬MAC地址的資料包。這意味著,無論最初接收資料包的是哪台交換機,任一vPC對等裝置都可以響應網關繫結的流量。 如果沒有啟用對等網關,某些型別的流量(如傳送到預設網關MAC地址的資料包)在到達一個對等體上時可能會被丟棄,否則將需要穿越對等鏈路並退出vPC成員埠。確保vPC域上配置了vPC對等網關。
相關資訊
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
1.0 |
14-Oct-2025
|
初始版本 |
由思科工程師貢獻
- 弗蘭西尼·瑪麗亞·費爾南德斯·蘇尼加技術諮詢工程師
 意見
意見