在ASA和FTD之間配置基於路由的站點到站點VPN
下載選項
無偏見用語
本產品的文件集力求使用無偏見用語。針對本文件集的目的,無偏見係定義為未根據年齡、身心障礙、性別、種族身分、民族身分、性別傾向、社會經濟地位及交織性表示歧視的用語。由於本產品軟體使用者介面中硬式編碼的語言、根據 RFP 文件使用的語言,或引用第三方產品的語言,因此本文件中可能會出現例外狀況。深入瞭解思科如何使用包容性用語。
關於此翻譯
思科已使用電腦和人工技術翻譯本文件,讓全世界的使用者能夠以自己的語言理解支援內容。請注意,即使是最佳機器翻譯,也不如專業譯者翻譯的內容準確。Cisco Systems, Inc. 對這些翻譯的準確度概不負責,並建議一律查看原始英文文件(提供連結)。
簡介
本檔案介紹如何透過將動態路由BGP作為重疊的FMC,在ASA和FTD之間設定路由型站點到站點VPN通道。
必要條件
需求
思科建議您瞭解以下主題:
- 對IPsec站點到站點VPN的基本瞭解
- Firepower威脅防禦託管(FTD)和自適應安全裝置(ASA)上的邊界網關協定(BGP)配置
- 使用Firepower管理中心(FMC)的經驗
採用元件
- Cisco ASAv版本9.20(2)2
- Cisco FMC版本7.4.1
- Cisco FTD版本7.4.1
本文中的資訊是根據特定實驗室環境內的裝置所建立。文中使用到的所有裝置皆從已清除(預設)的組態來啟動。如果您的網路運作中,請確保您瞭解任何指令可能造成的影響。
背景資訊
基於路由的VPN允許確定要加密或通過VPN隧道傳送的相關流量,並且使用流量路由而不是策略/訪問清單(如基於策略或基於加密對映的VPN中)。加密域設定為允許任何進入IPsec隧道的流量。IPsec本地和遠端流量選擇器設定為0.0.0.0/0.0.0.0。路由到IPsec隧道的所有流量都會被加密,與源/目標子網無關。
本檔案將重點介紹將動態路由BGP作為重疊的靜態虛擬通道介面(SVTI)組態。
設定
本節介紹ASA和FTD上通過SVTI IPSec隧道啟用BGP鄰近所需的配置。
網路圖表
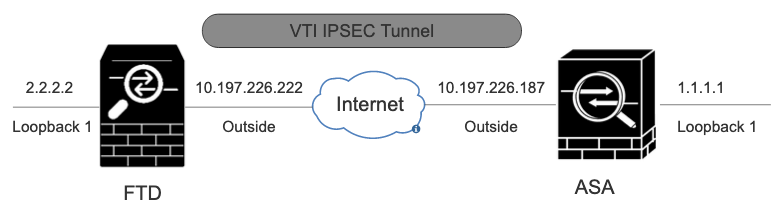 網路圖表
網路圖表
組態
使用FMC在FTD上配置IPSec VPN
步驟1。導覽至Devices > VPN > Site To Site。
步驟2.按一下+Site to Site VPN。
 站點到站點VPN
站點到站點VPN
步驟3.提供Topology Name,然後選擇VPN的類Route Based (VTI)型。選擇IKE Version。
在本演示中:
- 拓撲名稱:ASAv-VTI
- IKE版本:IKEv2
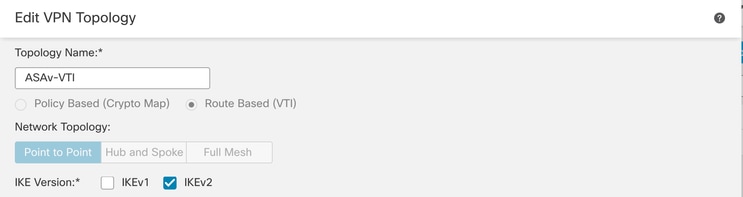 VPN拓撲
VPN拓撲
步驟4.選Device擇需要配置隧道的位置。您可以新增新的虛擬通道介面(按一下該圖+標),或從現有清單中選擇一個虛擬通道介面。
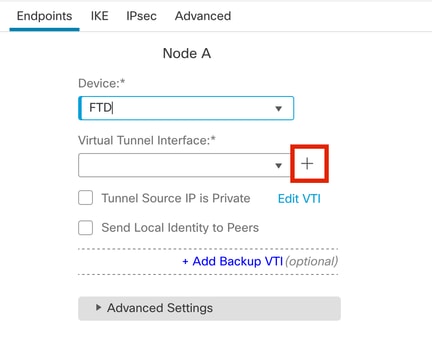 終端節點A
終端節點A
步驟5.定義引數New Virtual Tunnel Interface。按一下Ok。
在本演示中:
- 名稱:ASA-VTI
- 說明(可選):含Extranet ASA的VTI通道
- 安全區域:VTI區域
- 通道ID:1
- IP 位址:169.254.2.1/24
- 通道來源:GigabitEthernet0/1(外部)
- IPsec通道模式:IPv4
 虛擬通道介面
虛擬通道介面
步驟6.OK按一下彈出視窗,提示已建立新VTI。
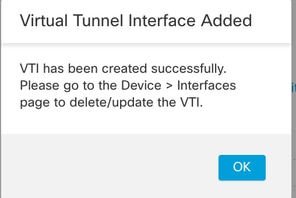 已新增虛擬通道介面
已新增虛擬通道介面
步驟7.選擇新建立的VTI或下面的VTIVirtual Tunnel Interface。提供節點B(對等裝置)的資訊。
在本演示中:
- 裝置:Extranet
- 裝置名稱:ASAv-Peer
- 終端IP地址:10.197.226.187
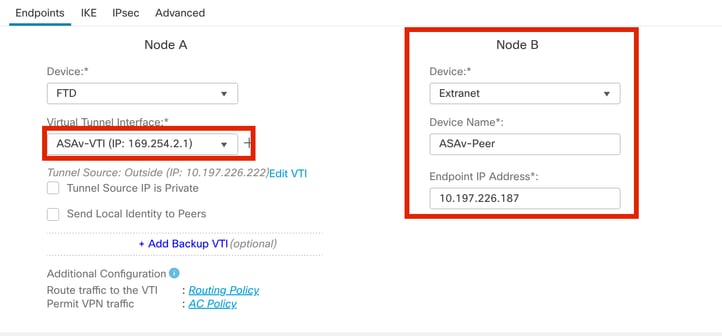 終端節點B
終端節點B
步驟8.導覽至IKE 索引標籤。按一下  .您可以選擇使用預定義
.您可以選擇使用預定義Policy,或按一下選+項卡旁的Policy按鈕以建立新選項。
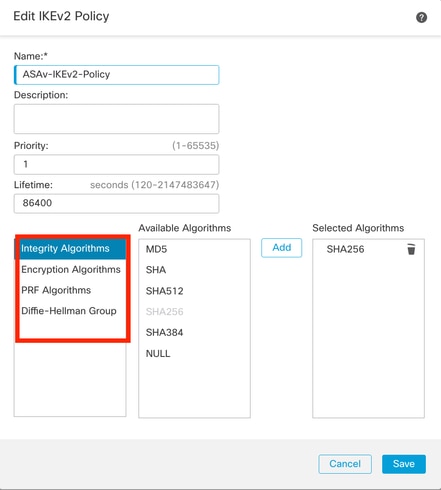
步驟9.(可選,如果建立新的IKEv2策略。) 為策Name略提供一個,並選Algorithms擇要在策略中使用的。按一下Save。
在本演示中:
- 名稱:ASAv-IKEv2-policy
- 完整性演算法:SHA-256
- 加密演算法:AES-256
- PRF演算法:SHA-256
- Diffie-Hellman組:14
 IKEv2-Policy
IKEv2-Policy
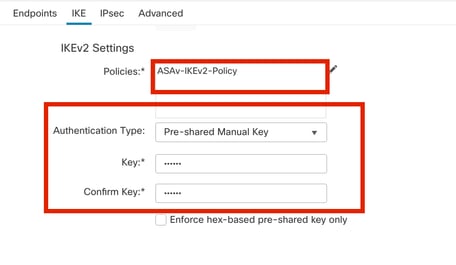
步驟10.選擇新建立的Policy,或現Policy有的。選擇Authentication Type。如果使用預共用手動金鑰,請在和框中輸Key入Confirm Key 金鑰。
在本演示中:
- 策略:ASAv-IKEv2-Policy
- 身份驗證型別:預共用手動金鑰
 驗證
驗證
步驟11.定位至標籤IPsec 卡。按一下  可以選擇使用預定義的IKEv2 IPsec建議或建立一個新的IKEv2 IPsec建議。按一下選
可以選擇使用預定義的IKEv2 IPsec建議或建立一個新的IKEv2 IPsec建議。按一下選+項卡旁邊的按IKEv2 IPsec Proposal 鈕。
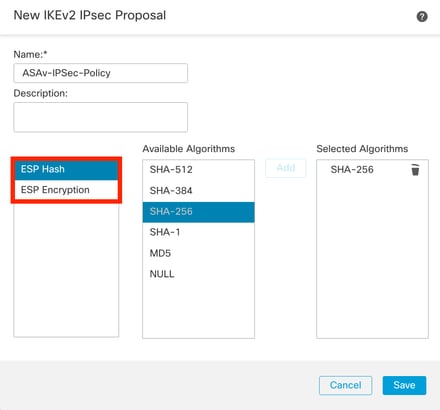
步驟12.(可選,如果建立新的IKEv2 IPsec提議。) 為建議Name輸入一個,並選Algorithms擇要在建議中使用的項。按一下Save。
在本演示中:
- 名稱:ASAv-IPSec-Policy
- ESP雜湊:SHA-256
- ESP加密:AES-256
 IKEv2-IPsec-Proposal
IKEv2-IPsec-Proposal
步驟13.從可用建議清單Proposal中Proposal選擇新建立的建議或現有建議。按一下OK。
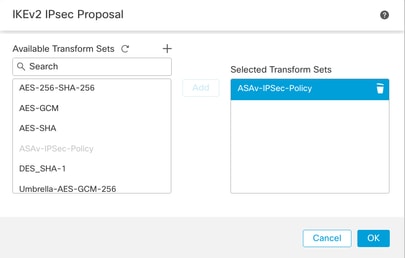 轉換集
轉換集
步驟14。(可選)選擇設置Perfect Forward Secrecy。配置IPsecLifetime Duration and Lifetime Size。
在本演示中:
- 完全向前保密:模陣列14
- 生存期持續時間:28800(預設)
- 生存期大小:4608000(預設)
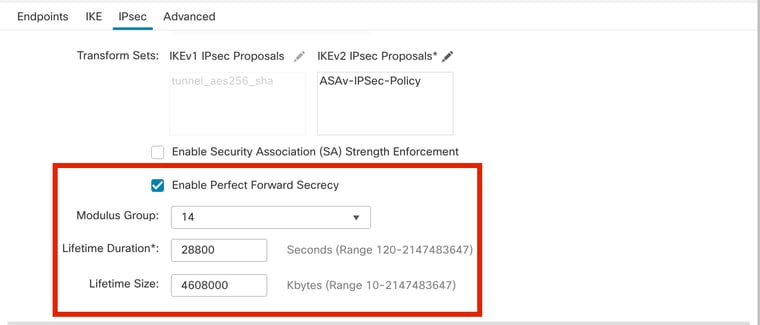 PFS配置
PFS配置
步驟15.檢查配置的設定。按一下Save,如下圖所示。
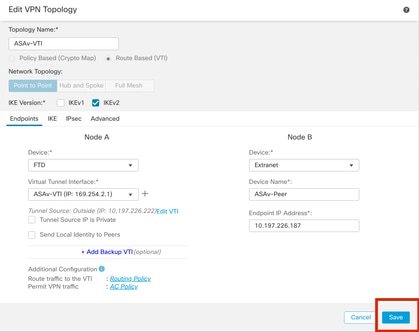 儲存配置
儲存配置
使用FMC設定FTD上的回送介面
導航至Devices > Device Management。編輯需要配置環回的裝置。
步驟1。轉到Interfaces > Add Interfaces > Loopback Interface。
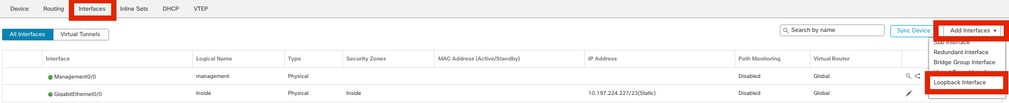 導航到環回介面
導航到環回介面
步驟2.輸入名稱"loopback",提供環回ID "1"並啟用介面。
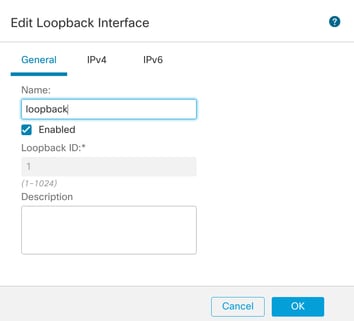 啟用環回介面
啟用環回介面
步驟3.配置介面的IP地址,按一下OK。
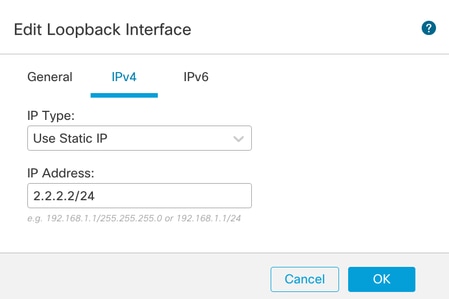 為環回介面提供IP地址
為環回介面提供IP地址
在ASA上配置IPSec VPN
!--- Configure IKEv2 Policy ---!
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 14
prf sha256
lifetime seconds 86400
!--- Enable IKEv2 on the outside interface ---!
crypto ikev2 enable outside
!---Configure Tunnel-Group with pre-shared-key---!
tunnel-group 10.197.226.222 type ipsec-l2l
tunnel-group 10.197.226.222 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
!--- Configure IPSec Policy ---!
crypto ipsec ikev2 ipsec-proposal ipsec_proposal_for_FTD
protocol esp encryption aes-256
protocol esp integrity sha-256
!--- Configure IPSec Profile ---!
crypto ipsec profile ipsec_profile_for_FTD
set ikev2 ipsec-proposal FTD-ipsec-proposal
set pfs group14
!--- Configure VTI ---!
interface Tunnel1
nameif FTD-VTI
ip address 169.254.2.2 255.255.255.0
tunnel source interface outside
tunnel destination 10.197.226.222
tunnel mode ipsec ipv4
tunnel protection ipsec profile ipsec_profile_for_FTD
!--- Configure the WAN routes ---!
route outside 0.0.0.0 0.0.0.0 10.197.226.1 1
配置ASA上的環回介面
interface Loopback1
nameif loopback
ip address 1.1.1.1 255.255.255.0
使用FMC在FTD上設定重疊BGP
導航到Devices > Device Management.Edit,導航到配置VTI隧道的裝置,然後導航到Routing > General Settings > BGP。
步驟1.啟用BGP並配置自治系統(AS)編號和路由器ID,如下圖所示。
裝置FTD和ASA上的AS編號必須相同。
路由器ID用於識別參與BGP的每個路由器。
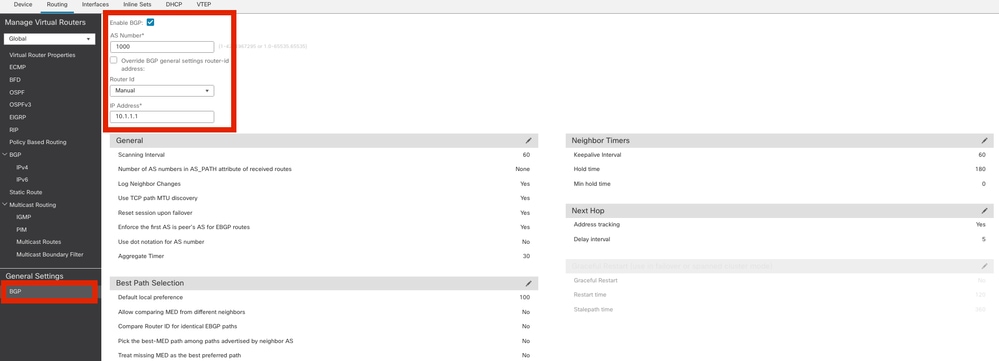 導航到配置BGP
導航到配置BGP
步驟2.導覽至BGP > IPv4,並在FTD上啟用BGP IPv4。
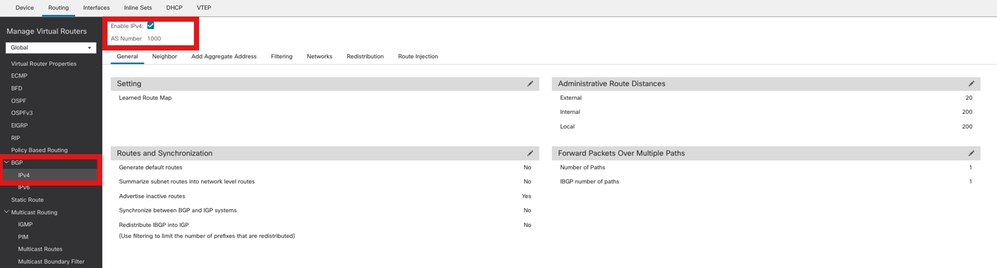 啟用BGP
啟用BGP
步驟3.在Neighbor頁籤下,將ASAv VTI隧道IP地址新增為鄰居並啟用鄰居。
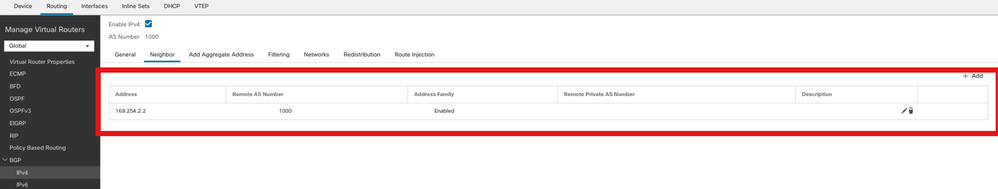 新增BGP鄰居
新增BGP鄰居
步驟4.在Networks下,新增要透過BGP進行廣告且需要通過VTI通道的網路,在本案例中為回送1。
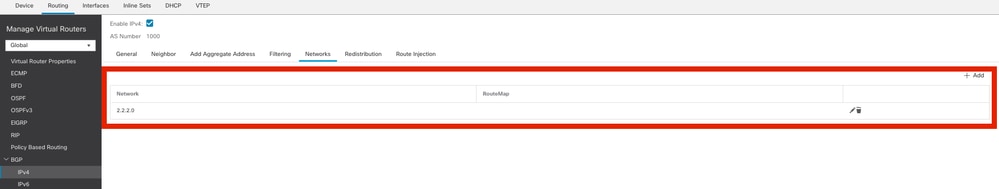 新增BGP網路
新增BGP網路
步驟5.所有其他BGP設定都是可選的,您可以根據您的環境對其進行配置。驗證配置並按一下Save。
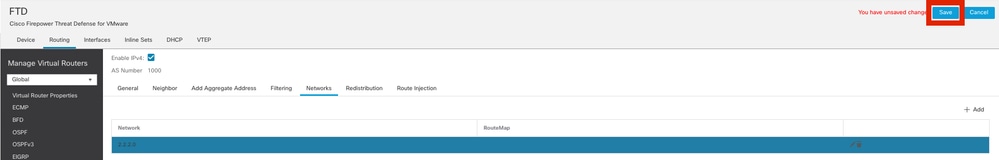 儲存BGP配置
儲存BGP配置
步驟6.部署所有配置。
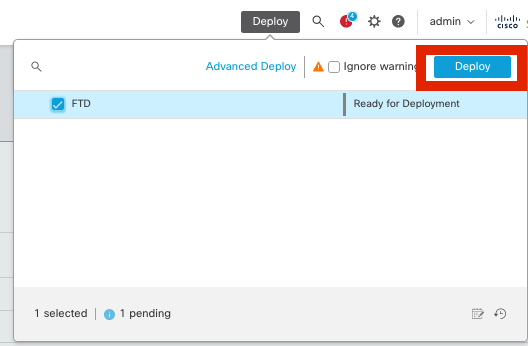 部署
部署
在ASA上配置重疊BGP
router bgp 1000
bgp log-neighbor-changes
bgp router-id 10.1.1.2
address-family ipv4 unicast
neighbor 169.254.2.1 remote-as 1000
neighbor 169.254.2.1 transport path-mtu-discovery disable
neighbor 169.254.2.1 activate
network 1.1.1.0 mask 255.255.255.0
no auto-summary
no synchronization
exit-address-family
驗證
使用本節內容,確認您的組態是否正常運作。
FTD上的輸出
#show crypto ikev2 sa
IKEv2 SAs:
Session-id:20, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status Role
666846307 10.197.226.222/500 10.197.226.187/500 Global/Global READY RESPONDER
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1201 sec
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0xa14edaf6/0x8540d49e
#show crypto ipsec sa
interface: ASAv-VTI
Crypto map tag: __vti-crypto-map-Tunnel1-0-1, seq num: 65280, local addr: 10.197.226.222
Protected vrf (ivrf): Global
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 10.197.226.187
#pkts encaps: 45, #pkts encrypt: 45, #pkts digest: 45
#pkts decaps: 44, #pkts decrypt: 44, #pkts verify: 44
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed:0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.197.226.222/500, remote crypto endpt.: 10.197.226.187/500
path mtu 1500, ipsec overhead 78(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 8540D49E
current inbound spi : A14EDAF6
inbound esp sas:
spi: 0xA14EDAF6 (2706299638)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv2, VTI, }
slot: 0, conn_id: 49, crypto-map: __vti-crypto-map-Tunnel1-0-1
sa timing: remaining key lifetime (kB/sec): (4331517/27595)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
000001FFF 0xFFFFFFFF
outbound esp sas:
spi: 0x8540D49E (2235618462)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv2, VTI, }
slot: 0, conn_id: 49, crypto-map: __vti-crypto-map-Tunnel1-0-1
sa timing: remaining key lifetime (kB/sec): (4101117/27595)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
#show bgp summary
BGP router identifier 10.1.1.1, local AS number 1000
BGP table version is 5, main routing table version 5
2 network entries using 400 bytes of memory
2 path entries using 160 bytes of memory
2/2 BGP path/bestpath attribute entries using 416 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 976 total bytes of memory
BGP activity 21/19 prefixes, 24/22 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
169.254.2.2 4 1000 22 22 5 0 0 00:19:42 1
#show bgp neighbors
BGP neighbor is 169.254.2.2, vrf single_vf, remote AS 1000, internal link
BGP version 4, remote router ID 10.1.1.2
BGP state = Established, up for 00:19:49
Last read 00:01:04, last write 00:00:38, hold time is 180, keepalive interval is 60 seconds
Neighbor sessions:
1 active, is not multisession capable (disabled)
Neighbor capabilities:
Route refresh: advertised and received(new)
Four-octets ASN Capability: advertised and received
Address family IPv4 Unicast: advertised and received
Multisession Capability:
Message statistics:
InQ depth is 0
OutQ depth is 0
Sent Rcvd
Opens 1 1
Notifications: 0 0
Updates: 2 2
Keepalives: 19 19
Route Refresh: 0 0
Total: 22 22
Default minimum time between advertisement runs is 0 seconds
For address family: IPv4 Unicast
Session: 169.254.2.2
BGP table version 5, neighbor version 5/0
Output queue size : 0
Index 15
15 update-group member
Sent Rcvd
Prefix activity: ---- ----
Prefixes Current: 1 1 (Consumes 80 bytes)
Prefixes Total: 1 1
Implicit Withdraw: 0 0
Explicit Withdraw: 0 0
Used as bestpath: n/a 1
Used as multipath: n/a 0
Outbound Inbound
Local Policy Denied Prefixes: -------- -------
Bestpath from this peer: 1 n/a
Invalid Path: 1 n/a
Total: 2 0
Number of NLRIs in the update sent: max 1, min 0
Address tracking is enabled, the RIB does have a route to 169.254.2.2
Connections established 7; dropped 6
Last reset 00:20:06, due to Peer closed the session of session 1
Transport(tcp) path-mtu-discovery is disabled
Graceful-Restart is disabled
#show route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.197.226.1 to network 0.0.0.0
B 1.1.1.0 255.255.255.0 [200/0] via 169.254.2.2, 00:19:55
ASA上的輸出
#show crypto ikev2 sa
IKEv2 SAs:
Session-id:7, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status Role
442126361 10.197.226.187/500 10.197.226.222/500 Global/Global READY INITIATOR
Encr: AES-CBC, keysize: 256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/1200 sec
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 0.0.0.0/0 - 255.255.255.255/65535
ESP spi in/out: 0x8540d49e/0xa14edaf6
#show crypto ipsec sa
interface: FTD-VTI
Crypto map tag: __vti-crypto-map-Tunnel1-0-1, seq num: 65280, local addr: 10.197.226.187
Protected vrf (ivrf): Global
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer: 10.197.226.222
#pkts encaps: 44 #pkts encrypt: 44, #pkts digest: 44
#pkts decaps: 45, #pkts decrypt: 45, #pkts verify: 45
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed:0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 10.197.226.187/500, remote crypto endpt.: 10.197.226.222/500
path mtu 1500, ipsec overhead 78(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: A14EDAF6
current inbound spi : 8540D49E
inbound esp sas:
spi: 0x8540D49E (2235618462)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv2, VTI, }
slot: 0, conn_id: 9, crypto-map: __vti-crypto-map-Tunnel1-0-1
sa timing: remaining key lifetime (kB/sec): (4147198/27594)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x007FFFFF
outbound esp sas:
spi: 0xA14EDAF6 (2706299638)
SA State: active
transform: esp-aes-256 esp-sha-256-hmac no compression
in use settings ={L2L, Tunnel, PFS Group 14, IKEv2, VTI, }
slot: 0, conn_id: 9, crypto-map: __vti-crypto-map-Tunnel1-0-1
sa timing: remaining key lifetime (kB/sec): (3916798/27594)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
#show bgp summary
BGP router identifier 10.1.1.2, local AS number 1000
BGP table version is 7, main routing table version 7
2 network entries using 400 bytes of memory
2 path entries using 160 bytes of memory
2/2 BGP path/bestpath attribute entries using 416 bytes of memory
0 BGP route-map cache entries using 0 bytes of memory
0 BGP filter-list cache entries using 0 bytes of memory
BGP using 976 total bytes of memory
BGP activity 5/3 prefixes, 7/5 paths, scan interval 60 secs
Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd
169.254.2.1 4 1000 22 22 7 0 0 00:19:42 1
#show bgp neighbors
BGP neighbor is 169.254.2.1, context single_vf, remote AS 1000, internal link
BGP version 4, remote router ID 10.1.1.1
BGP state = Established, up for 00:19:42
Last read 00:01:04, last write 00:00:38, hold time is 180, keepalive interval is 60 seconds
Neighbor sessions:
1 active, is not multisession capable (disabled)
Neighbor capabilities:
Route refresh: advertised and received(new)
Four-octets ASN Capability: advertised and received
Address family IPv4 Unicast: advertised and received
Multisession Capability:
Message statistics:
InQ depth is 0
OutQ depth is 0
Sent Rcvd
Opens: 1 1
Notifications: 0 0
Updates: 2 2
Keepalives: 19 19
Route Refresh: 0 0
Total: 22 22
Default minimum time between advertisement runs is 0 seconds
For address family: IPv4 Unicast
Session: 169.254.2.1
BGP table version 7, neighbor version 7/0
Output queue size : 0
Index 5
5 update-group member
Sent Rcvd
Prefix activity: ---- ----
Prefixes Current: 1 1 (Consumes 80 bytes)
Prefixes Total: 1 1
Implicit Withdraw: 0 0
Explicit Withdraw: 0 0
Used as bestpath: n/a 1
Used as multipath: n/a 0
Outbound Inbound
Local Policy Denied Prefixes: -------- -------
Bestpath from this peer: 1 n/a
Invalid Path: 1 n/a
Total: 2 0
Number of NLRIs in the update sent: max 1, min 0
Address tracking is enabled, the RIB does have a route to 169.254.2.1
Connections established 5; dropped 4
Last reset 00:20:06, due to Peer closed the session of session 1
Transport(tcp) path-mtu-discovery is disabled
Graceful-Restart is disabled
#show route bgp
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF, BI - BGP InterVRF
Gateway of last resort is 10.197.226.1 to network 0.0.0.0
B 2.2.2.0 255.255.255.0 [200/0] via 169.254.2.1, 00:19:55
疑難排解
本節提供的資訊可用於對組態進行疑難排解。
debug crypto ikev2 platform 255
debug crypto ikev2 protocol 255
debug crypto ipsec 255
debug ip bgp all
- 僅支援IPv4介面,以及IPv4、受保護的網路或VPN負載(不支援IPv6)。
修訂記錄
| 修訂 | 發佈日期 | 意見 |
|---|---|---|
2.0 |
06-Aug-2025
|
格式化。 |
1.0 |
13-Jun-2024
|
初始版本 |
 意見
意見