Catalyst交换机中的动态ARP检测(DAI)和IP源保护(IPSG)故障排除
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍动态ARP检测(DAI)和IP源保护(IPSG)如何工作,以及如何在Catalyst 9K交换机中验证它们。
DHCP监听及相关功能
在介绍DAI和IPSG之前,您需要简要讨论DHCP监听,这是DAI和IPSG的前提条件。
动态主机配置协议(DHCP)是一种客户端/服务器协议,可自动为Internet协议(IP)主机提供IP地址和其它相关配置信息(如子网掩码和默认网关)。RFC 2131和2132将DHCP定义为基于Bootstrap协议(BOOTP)的Internet工程任务组(IETF)标准,BOOTP是DHCP共享许多实施详细信息的协议。DHCP允许主机从DHCP服务器获取所需的TCP/IP配置信息。
DHCP监听是一种安全功能,作用类似于不可信主机和可信DHCP服务器之间的防火墙。DHCP监听功能执行以下活动:
- 验证从不可信源收到的DHCP消息并过滤出无效消息。
- 对来自受信任和不受信任来源的DHCP流量进行速率限制。
- 建立并维护DHCP监听绑定数据库,其中包含有关使用租用IP地址的不受信任主机的信息。
- 使用DHCP监听绑定数据库验证来自不受信任主机的后续请求。
DAI是一项安全功能,用于验证网络中的地址解析协议(ARP)数据包。DAI允许网络管理员拦截、记录并丢弃具有无效MAC地址到IP地址绑定的ARP数据包。此功能可保护网络免受某些“中间人”攻击。
IPSG是一项安全功能,通过根据DHCP监听绑定数据库和手动配置的IP源绑定过滤流量,限制非路由第2层接口上的IP流量。如果主机尝试使用其邻居的IP地址,您可以使用IPSG来防止流量攻击。
没有DHCP监听的场景

1.在此图中,您可以看到多个客户端希望从连接到核心交换机的DHCP服务器接收IP地址。
2.但是,有一个恶意/欺诈DHCP服务器连接到一个接入层交换机,可以接收DHCP,发现并发送DHCP提供的速度比实际DHCP服务器更快。
3.攻击者可以设置提议消息中的网关地址,使其可以接收来自客户端的所有流量,从而影响通信的机密性。
4.这被称为“中间人”。
使用DHCP监听的场景

1.通过在接入交换机中启用DHCP监听,将交换机配置为监听DHCP流量并停止在不可信端口上收到的任何恶意DHCP数据包。
2.一旦在交换机中启用DHCP监听,所有接口都会自动变为不可信。
3.使连接到终端设备的端口不受信任,并将连接到正版DHCP服务器的端口配置为受信任。
4.不受信任的接口将阻止DHCP提供消息。DHCP提供消息仅在受信任端口上允许。
5.您可以限制终端主机每秒可以向不受信任的接口发送的DHCP发现数据包的数量。这是一种安全机制,可以保护DHCP服务器免于异常大量的传入DHCP发现,从而可以在短时间内耗尽地址池。
本节介绍如何在交换网络中配置DHCP监听:
拓扑:

接入交换机的接口Gi1/0/1-4连接到DHCP客户端。您可以启用这些客户端从正版DHCP服务器接收IP地址,并通过利用DHCP监听功能保护它们免受恶意DHCP服务器的攻击。
请参阅以下步骤了解如何实现此目的:
步骤1.在接入交换机的VLAN下全局启用DHCP监听:
ip dhcp snooping
ip dhcp snooping vlan 10,20,30
步骤2.在接收来自正版DHCP服务器的DHCP提供的接入交换机的所有接口上配置DHCP监听信任。此类接口的数量取决于DHCP服务器的网络设计和位置。这些是指向正版DHCP服务器的接口。
接入层交换机:
interface TenGigabitEthernet1/0/2
switchport mode trunk
ip dhcp snooping trust
步骤3.全局配置DHCP监听后,交换机中的所有端口都会自动变为不可信(手动信任的那些端口除外,如前所示)。 但是,您可以配置终端主机每秒可发送到不受信任接口的DHCP发现数据包数量。
这是一种安全机制,可保护DHCP服务器免受异常大量的传入DHCP发现的影响,从而可在短时间内耗尽地址池。
interface range Gi1/0/1-5
ip dhcp snooping limit rate 10
验证:
Access_SW#show ip dhcp snooping
Switch DHCP snooping is enabled
Switch DHCP gleaning is disabled
DHCP snooping is configured on following VLANs:
10,20,30
DHCP snooping is operational on following VLANs:
10,20,30
DHCP snooping is configured on the following L3 Interfaces:
Insertion of option 82 is disabled
circuit-id default format: vlan-mod-port
remote-id: 00fc.ba9e.3980 (MAC)
Option 82 on untrusted port is not allowed
Verification of hwaddr field is enabled
Verification of giaddr field is enabled
DHCP snooping trust/rate is configured on the following Interfaces:
Interface Trusted Allow option Rate limit (pps)
----------------------- ------- ------------ ----------------
GigabitEthernet1/0/1 no no 10
Custom circuit-ids:
GigabitEthernet1/0/2 no no 10
Custom circuit-ids:
GigabitEthernet1/0/3 no no 10
Custom circuit-ids:
GigabitEthernet1/0/4 no no 10
Custom circuit-ids:
GigabitEthernet1/0/5 no no 10
Custom circuit-ids:
TenGigabitEthernet1/0/2 yes yes unlimited
Custom circuit-ids:

注意:如果您查看此输出,您会看到输出中提到连接到恶意DHCP服务器的Gi1/0/5为show ip dhcp snooping不可信。
因此,DHCP监听将对这些端口执行所有检查。
例如,这将导致此端口(Gi1/0/5)上的所有传入DHCP提供被丢弃。
以下是DHCP监听绑定表,显示Gi1/0/1、Gi1/0/2、Gi1/0/3上3个客户端的IP地址、MAC地址和接口:
Access_SW#show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
00:FC:BA:9E:39:82 10.10.10.2 62488 dhcp-snooping 10 GigabitEthernet1/0/1
00:FC:BA:9E:39:A6 10.10.20.2 62492 dhcp-snooping 20 GigabitEthernet1/0/2
00:FC:BA:9E:39:89 10.10.30.3 62492 dhcp-snooping 30 GigabitEthernet1/0/3
Total number of bindings: 3
出于演示目的ip dhcp snooping trust,配置会从接入交换机的Te1/0/2下移除。请查看交换机中生成的日志:
Access_SW#sh cdp neigh
Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge
S - Switch, H - Host, I - IGMP, r - Repeater, P - Phone,
D - Remote, C - CVTA, M - Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
Dist_SW Ten 1/0/2 175 R S I C9300-48U Ten 1/1/3
Total cdp entries displayed : 1
Access_SW#show run int Te1/0/2
Building configuration...
Current configuration : 64 bytes
!
interface TenGigabitEthernet1/0/2
switchport mode trunk
*Apr 4 01:12:47.149: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca65
*Apr 4 01:14:07.161: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca65
*Apr 4 01:29:30.634: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca56
*Apr 4 01:30:03.286: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: f87a.41a8.ca46
- 如您所见,接入交换机正在丢弃Te1/0/2上的传入DHCP提供数据包,因为它不再受信任。
- 日志中的MAC地址属于VLAN 10、20和30的SVI,因为它们是从DHCP服务器向这些客户端发送这些提议的地址。
ARP 毒化
ARP通过将IP地址映射到MAC地址来提供第2层广播域内的IP通信。它是一种简单的协议,但很容易受到称为ARP毒化的攻击。
ARP毒化是攻击者向网络发送虚假ARP应答数据包的一种攻击。
恶意用户可以通过毒化连接到子网的系统的ARP缓存并拦截流向子网中其他主机的流量,攻击连接到第2层网络的主机、交换机和路由器
这是典型的中间人攻击。
预防机制
动态ARP检测(DAI)
动态 ARP 检测是一项安全功能,用于验证网络中的 ARP 数据包。它拦截、记录并丢弃具有 IP 到 MAC 地址的无效绑定的 ARP 数据包。使用此功能可以防止网络受到某些中间人攻击。
动态 ARP 检测可确保仅转发有效 ARP 请求和响应。交换机可执行以下活动:
- 拦截不受信任端口上的所有 ARP 请求和响应
- 在更新本地ARP缓存之前或转发数据包到适当的目标之前,验证每个拦截的数据包都具有有效的IP到MAC地址绑定
- 丢弃无效的 ARP 数据包
动态 ARP 检测可根据受信任数据库(DHCP 监听绑定数据库)中存储的 IP 到 MAC 地址的有效绑定来确定 ARP 数据包的有效性。
如果已在 VLAN 和交换机上启用 DHCP 监听,则此数据库可通过 DHCP 监听来构建。如果在受信任接口上收到 ARP 数据包,交换机将在不做任何检查的情况下转发数据包。
在不受信任接口上,交换机仅转发有效数据包。
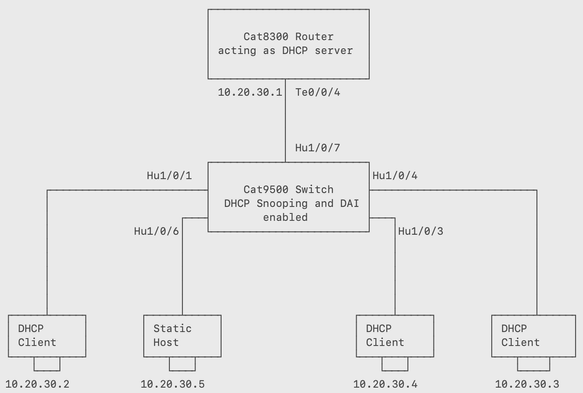
此映像演示连接到四台主机的Cat9500交换机,其中3台主机是DHCP客户端,1台主机具有静态IP地址(10.20.30.5)。 DHCP服务器是配置有DHCP池的Cat8300系列路由器。
上述拓扑用于演示DAI如何检测接口上的无效ARP请求并保护网络免受恶意攻击者的攻击。
配置:
步骤1.在交换机中全局配置DHCP监听和DAI。
F241.24.02-9500-1#sh run | i dhcp
ip dhcp snooping vlan 10
no ip dhcp snooping information option
ip dhcp snooping
F241.24.02-9500-1#sh run | i ip arp
ip arp inspection vlan 10
步骤2.将连接到DHCP服务器的接口Hu1/0/7配置为可信端口。这将允许DHCP提供进入接口并随后到达DHCP客户端。
F241.24.02-9500-1#sh run int Hu1/0/7
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/7
switchport access vlan 10
ip dhcp snooping trust
end
步骤3.将连接到DHCP客户端的端口配置为允许VLAN 10的接入端口。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
end
步骤4.检验DHCP客户端是否已从Cat9500交换机的DHCP监听绑定表中收到来自DHCP服务器的IP地址。
F241.24.02-9500-1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 85046 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 85065 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 85085 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
您还可以检查DHCP服务器中的绑定。
DHCP_Server#show ip dhcp binding
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
10.20.30.2 0063.6973.636f.2d37. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
3837.322e.3564.3162.
2e37.6633.662d.4875.
312f.302f.31
10.20.30.3 0063.6973.636f.2d35. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
6337.312e.3064.6364.
2e65.6530.632d.5465.
312f.302f.35
10.20.30.4 0063.6973.636f.2d32. Apr 08 2024 07:05 AM Automatic Active TenGigabitEthernet0/0/4
6334.662e.3532.3031.
2e61.6163.632d.5465.
312f.302f.35
步骤 5:将连接到Hu1/0/6的主机的IP地址从10.20.30.5更改为10.20.30.2,并尝试从该主机ping其它DHCP客户端。
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.....
在Cat9500交换机上可以看到以下无效ARP日志:
F241.24.02-9500-1#
*Apr 7 09:29:24.520: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:23 UTC Sun Apr 7 2024])
*Apr 7 09:29:26.520: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:25 UTC Sun Apr 7 2024])
*Apr 7 09:29:28.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:27 UTC Sun Apr 7 2024])
*Apr 7 09:29:30.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:29 UTC Sun Apr 7 2024])
*Apr 7 09:29:32.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.3/09:29:31 UTC Sun Apr 7 2024])
F241.24.02-9500-1#
*Apr 7 09:29:47.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:46 UTC Sun Apr 7 2024])
*Apr 7 09:29:49.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:48 UTC Sun Apr 7 2024])
*Apr 7 09:29:51.521: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:50 UTC Sun Apr 7 2024])
*Apr 7 09:29:53.522: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:52 UTC Sun Apr 7 2024])
*Apr 7 09:29:55.523: %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Req) on Hu1/0/6, vlan 10.([7035.0956.7ee4/10.20.30.2/0000.0000.0000/10.20.30.4/09:29:54 UTC Sun Apr 7 2024])
- 如您所见,当您尝试从Static_Host ping 10.20.30.3和10.20.30.4时,您做不到。
即使Static_Host试图欺骗合法DHCP客户端的IP地址,它也无法这样做,因为到达Hu1/0/6的任何ARP数据包都将由交换机进行检查,并与DHCP监听绑定表中显示的数据进行比较。 - 来自Cat9500交换机的后续日志确认从Static_Host发送到DHCP客户端的ARP请求被丢弃。
- Cat9500交换机通过引用DHCP监听绑定数据库实现这一点。
- 当ARP请求进入Hu1/0/6且源MAC-IP与DHCP监听绑定数据库中存在的值不匹配时,交换机将丢弃ARP请求。
步骤6.验证:
F241.24.02-9500-1#show ip arp inspection
Source Mac Validation : Disabled
Destination Mac Validation : Disabled
IP Address Validation : Disabled
Vlan Configuration Operation ACL Match Static ACL
---- ------------- --------- --------- ----------
10 Enabled Active DAI No
Vlan ACL Logging DHCP Logging Probe Logging
---- ----------- ------------ -------------
10 Deny Deny Off
Vlan Forwarded Dropped DHCP Drops ACL Drops
---- --------- ------- ---------- ---------
10 9 39 39 0
Vlan DHCP Permits ACL Permits Probe Permits Source MAC Failures
---- ------------ ----------- ------------- -------------------
10 6 3 0 0
Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data
---- ----------------- ---------------------- ---------------------
10 0 0 0
在此输出中,您可以看到Cat9500交换机中VLAN 10中的DAI丢弃和允许的数据包数量。

注意:一个非常重要的情况可能是网络中分配有静态IP地址(例如10.20.30.5)的合法主机?
虽然主机没有尝试伪装任何内容,但它仍然会与网络隔离,因为其MAC-IP绑定数据不存在于DHCP监听绑定数据库中。
这是因为静态主机从未使用DHCP接收IP地址,因为它是静态分配的。
我们提供一些解决方法,可以实施为具有静态IP地址的合法主机提供连接。
第 1 项.
使用ip arp inspection trust配置连接到主机的接口。
F241.24.02-9500-1#sh run int HundredGigE 1/0/6
Building configuration...
Current configuration : 110 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
switchport mode access
ip arp inspection trust
end
Static_Host#ping 10.20.30.4
*Apr 7 18:44:45.299 JST: %SYS-5-CONFIG_I: Configured from console by admin on vty0 (192.168.1.5)
F241.24.02-9300-STACK#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
第 2 项.
使用ARP Access-List允许静态主机:
F241.24.02-9500-1#sh run | s arp access-list
arp access-list DAI
permit ip host 10.20.30.5 mac host 7035.0956.7ee4
F241.24.02-9500-1#sh run | i ip arp ins
ip arp inspection filter DAI vlan 10
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
选项 3.
配置静态主机的绑定表条目。
F241.24.02-9500-1#sh run | i binding
ip source binding 7035.0956.7EE4 vlan 10 10.20.30.5 interface Hu1/0/6
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 80640 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 80659 dhcp-snooping 10 HundredGigE1/0/4
70:35:09:56:7E:E4 10.20.30.5 infinite static 10 HundredGigE1/0/6
2C:4F:52:01:AA:CC 10.20.30.4 80679 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 4
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 1/1/1 ms
DAI提供的其他选项:
F241.24.02-9500-1(config)#ip arp inspection validate ?
dst-mac Validate destination MAC address
ip Validate IP addresses
src-mac Validate source MAC address
对于src-mac,请根据ARP正文中的发送方MAC地址检查以太网报头中的源MAC地址。此检查针对ARP请求和响应执行。启用时,具有不同MAC地址的数据包将被分类为无效并丢弃
对于dst-mac,请根据ARP正文中的目标MAC地址检查以太网报头中的目标MAC地址。对ARP响应执行此检查。启用时,具有不同MAC地址的数据包将被分类为无效并丢弃。
对于IP,检查ARP正文是否存在无效和意外的IP地址。地址包括0.0.0.0、255.255.255.255和所有IP组播地址。在所有ARP请求和响应中检查发送方IP地址,仅在ARP响应中检查目标IP地址。
您还可以配置ARP速率限制。默认情况下,不可信接口上的ARP流量限制为15 pps:
Switch(config)#interface Gigabitethernet<>
Switch(config-if)#ip arp inspection limit rate 10
IP 源防护
- IPSG是一项安全功能,它通过根据DHCP监听绑定数据库和手动配置的IP源绑定过滤流量来限制非路由第2层接口上的IP流量。
- 如果主机尝试使用其邻居的IP地址,您可以使用IPSG来防止流量攻击。
- 在不可信接口上启用DHCP监听时,可以启用IPSG。在接口上启用IPSG后,交换机将阻止接口上接收的所有IP流量,但DHCP监听允许的DHCP数据包除外。
- 交换机使用硬件中的源IP查找表将IP地址绑定到端口。对于IP和MAC过滤,使用源IP和源MAC查找的组合。允许绑定表中具有源IP地址的IP流量,但拒绝所有其他流量。
- IP 源绑定表中包含由 DHCP 监听识别的绑定或手动配置的绑定(静态 IP 源绑定)。 此表中的条目具有 IP 地址、关联的 MAC 地址和关联的 VLAN 编号。仅当启用IP源保护时,交换机才使用IP源绑定表。
- 您可以使用源IP地址过滤或源IP和MAC地址过滤配置IPSG。
静态主机的IPSG
- 静态主机的IPSG允许IPSG在没有DHCP的情况下工作。静态主机的IPSG依赖IP设备跟踪表条目来安装端口ACL。交换机根据ARP请求或其他IP数据包创建静态条目,以维护给定端口的有效主机列表。
参考:

Cat9500交换机连接到4台主机,其中3台主机是DHCP客户端,1台主机具有静态IP地址。DHCP服务器是配置有DHCP池的Cat8300系列路由器。
您可以使用此拓扑演示IPSG如何检测和阻止来自MAC-IP绑定未出现在DHCP监听绑定数据库中的主机的流量。
配置:
步骤1.在Cat9500交换机中全局配置DHCP监听。
F241.24.02-9500-1#sh run | i dhcp
ip dhcp snooping vlan 10
no ip dhcp snooping information option
ip dhcp snooping
步骤2.将连接到DHCP服务器的接口Te1/0/7配置为可信端口。这允许DHCP提供进入接口并随后到达DHCP客户端。
F241.24.02-9500-1#sh run int Hu1/0/7
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/7
switchport access vlan 10
ip dhcp snooping trust
end
步骤3.将连接到DHCP客户端的端口配置为允许VLAN 10的接入端口。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 61 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 85 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
end
步骤4.检验DHCP客户端是否已从DHCP服务器收到IP地址。
F241.24.02-9500-1#sh ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 85046 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 85065 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 85085 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 64764 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 64783 dhcp-snooping 10 HundredGigE1/0/4
2C:4F:52:01:AA:CC 10.20.30.4 64803 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 3
DHCP_Server#show ip dhcp binding
Bindings from all pools not associated with VRF:
IP address Client-ID/ Lease expiration Type State Interface
Hardware address/
User name
10.20.30.2 0063.6973.636f.2d37. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
3837.322e.3564.3162.
2e37.6633.662d.4875.
312f.302f.31
10.20.30.3 0063.6973.636f.2d35. Apr 08 2024 07:04 AM Automatic Active TenGigabitEthernet0/0/4
6337.312e.3064.6364.
2e65.6530.632d.5465.
312f.302f.35
10.20.30.4 0063.6973.636f.2d32. Apr 08 2024 07:05 AM Automatic Active TenGigabitEthernet0/0/4
6334.662e.3532.3031.
2e61.6163.632d.5465.
312f.302f.35
步骤5.在连接到所有终端主机的接口下配置IPSG(3个DHCP客户端和1个具有静态IP地址的主机)。
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 79 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
ip verify source
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 103 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
ip verify source
end
验证:
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip active 10.20.30.2 10
Hu1/0/3 ip active 10.20.30.4 10
Hu1/0/4 ip active 10.20.30.3 10
Hu1/0/6 ip active deny-all 10
从此输出中,您可以看到Hu1/0/6的IP Address字段设置为deny-all,因为DHCP监听绑定表中没有与此接口对应的MAC-IP绑定。
步骤6.尝试从Static_Host ping IP地址为10.20.30.2、10.20.30.3和10.20.30.4的DHCP客户端。
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
.....
F241.24.02-9500-1(config)# ip source binding <mac-address-of-static-host> vlan 10 10.20.30.5 interface Hu1/0/6
F241.24.02-9500-1#show run int Hu1/0/6
*Apr 7 15:13:48.449: %SYS-5-CONFIG_I: Configured from console by console
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip active 10.20.30.2 10
Hu1/0/3 ip active 10.20.30.4 10
Hu1/0/4 ip active 10.20.30.3 10
Hu1/0/6 ip active 10.20.30.5 10
F241.24.02-9500-1#show ip source binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------------- ---- --------------------
78:72:5D:1B:7F:3F 10.20.30.2 62482 dhcp-snooping 10 HundredGigE1/0/1
5C:71:0D:CD:EE:0C 10.20.30.3 62501 dhcp-snooping 10 HundredGigE1/0/4
70:35:09:56:7E:E4 10.20.30.5 infinite static 10 HundredGigE1/0/6
2C:4F:52:01:AA:CC 10.20.30.4 62521 dhcp-snooping 10 HundredGigE1/0/3
Total number of bindings: 4
Verification:
Static_Host#ping 10.20.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
Static_Host#ping 10.20.30.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.20.30.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
IPSG的其他可用选项:
默认情况下,IPSG仅根据IP地址过滤不可信端口上的传入流量。
如果要根据IP和MAC地址执行过滤,请执行以下步骤。
F241.24.02-9500-1#sh run int Hu1/0/1
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/1
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/3
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/3
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/4
Building configuration...
Current configuration : 89 bytes
!
interface HundredGigE1/0/4
switchport access vlan 10
ip verify source mac-check
end
F241.24.02-9500-1#sh run int Hu1/0/6
Building configuration...
Current configuration : 113 bytes
!
interface HundredGigE1/0/6
switchport access vlan 10
switchport mode access
ip verify source mac-check
end
F241.24.02-9500-1#show ip verify source
Interface Filter-type Filter-mode IP-address Mac-address Vlan
--------- ----------- ----------- --------------- ----------------- ----
Hu1/0/1 ip-mac active 10.20.30.2 78:72:5D:1B:7F:3F 10
Hu1/0/3 ip-mac active 10.20.30.4 2C:4F:52:01:AA:CC 10
Hu1/0/4 ip-mac active 10.20.30.3 5C:71:0D:CD:EE:0C 10
Hu1/0/6 ip-mac active deny-all deny-all 10
在此输出中,您可以看到Filter-type为ip-mac。因此,交换机现在根据源IP和MAC地址过滤这些接口上的传入数据包。
DAI和IPSG故障排除提示
- 在排查DAI和IPSG相关问题时,首先要检查的是验证DHCP监听绑定表是否已正确填充。
- 启用这些功能之前,请使用静态IP地址处理终端。如果您不希望这些设备丢失可达性,请配置静态绑定或使用前面提到的方法之一,使交换机信任这些终端。
- 在尚未启用DHCP监听且客户端已经从DHCP服务器接收IP的环境中配置DAI或IPSG时,请首先启用DHCP监听并执行下列两个步骤之一:
- 退回客户端连接的接口,以便其续订租期。
- 等待客户端自动续订租约。这可能需要花费更多的时间,但省去了手动退回所有客户端连接的端口的麻烦。
- 执行上述两个步骤之一将触发新的DORA事务。交换机将嗅探DORA数据包并更新绑定表。如果未执行此操作,并且在配置DHCP监听后立即启用DAI或IPSG,则可能会遇到网络中所有DHCP客户端都失去与网络的连接的问题。
- 在配置DAI或IPSG的环境中排除连接问题时,请确保DHCP监听绑定表未损坏。确保交换机可以访问存储此表的数据结构。
- 在某些情况下,绑定表可能会导出到介质中,该介质在交换机启动后需要一段时间才能初始化,或者由于某种原因导致交换机无法访问。您可能会发现此类场景中的连接问题。
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
05-Aug-2024
|
初始版本 |

 反馈
反馈