配置ISE 2.0 TrustSec SXP监听器和发言人
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
简介
本文档介绍如何配置思科身份服务引擎(ISE) 2.0版在侦听器和扬声器模式下支持TrustSec SGT交换协议(SXP)的功能并对其进行故障排除。
先决条件
要求
Cisco 建议您了解以下主题:
- Cisco Catalyst交换机配置
- 身份服务引擎(ISE)和TrustSec服务
使用的组件
本文档中的信息基于以下软件版本:
- 配备软件IOS-XE 3.7.2及更高版本的Cisco Catalyst 3850交换机
- 思科ISE版本2.0及更高版本
配置
网络图
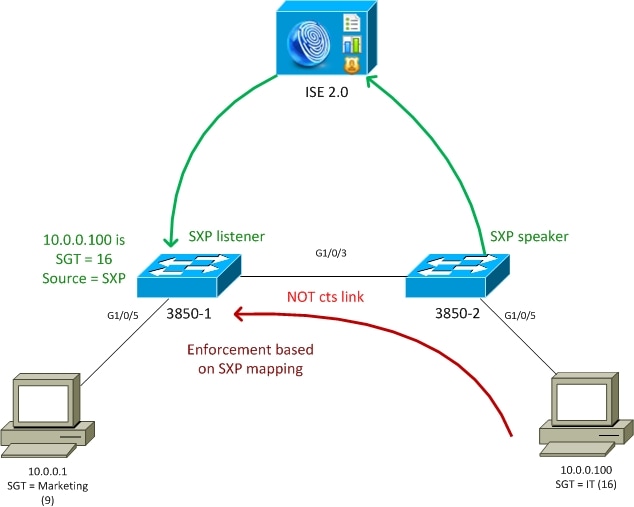
流量传输
- 3850-2是10.0.0.100的802.1x身份验证器- ISE返回安全组标记(SGT) 16 (IT)以成功进行身份验证
- 3850-2交换机了解请求方ip地址(ip设备跟踪)并使用SXP协议将映射信息(IP-SGT)发送到ISE
- 3850-1是10.0.0.1的802.1x身份验证器- ISE返回SGT标记9 (营销)以成功进行身份验证
- 3850-1从ISE接收SXP映射信息(10.0.0.100是SGT 16),然后从ISE下载策略
- 从10.0.0.100发送到10.0.0.1的流量由3850-2(未下载特定策略)转发到3850-1,即执行器命中策略IT (16) ->营销(9)
请注意,交换机之间的链路不是cts链路,因此交换机上的所有远程映射都是通过SXP协议安装的。
注意:并非所有交换机都有允许根据收到的SXP映射通过从ISE接收的策略进行编程的硬件。有关验证信息,请始终参阅最新的TrustSec兼容性列表或联系思科系统公司。
配置
有关基本TrustSec配置的详细信息,请参阅参考一节中的文章。
交换机3850-1
交换机通过SGT分配终止802.1x会话,同时作为面向ISE的SXP发言人。
aaa authentication dot1x default group ISE_mgarcarz
aaa authorization network default group ISE_mgarcarz
aaa authorization network ISE_mgarcarz group ISE_mgarcarz
aaa accounting dot1x default start-stop group ISE_mgarcarz
aaa accounting update newinfo
radius server ISE_mgarcarz
address ipv4 10.48.17.235 auth-port 1645 acct-port 1646
pac key cisco
aaa group server radius ISE_mgarcarz
server name ISE_mgarcarz
interface GigabitEthernet1/0/3
switchport mode trunk
interface GigabitEthernet1/0/5
description mgarcarz
switchport access vlan 100
switchport mode access
ip flow monitor F_MON input
ip flow monitor F_MON output
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
mab
dot1x pae authenticator
cts authorization list ISE_mgarcarz
cts role-based enforcement
cts role-based enforcement vlan-list 1-4094
cts sxp enable
cts sxp default password cisco
cts sxp connection peer 10.48.17.235 password default mode local listener hold-time 0
交换机3850-2
交换机通过SGT分配终止802.1x会话,同时作为SXP侦听程序从ISE获取映射。
aaa authentication dot1x default group ISE_mgarcarz
aaa authorization network default group ISE_mgarcarz
aaa authorization network ISE_mgarcarz group ISE_mgarcarz
aaa accounting dot1x default start-stop group ISE_mgarcarz
aaa accounting update newinfo
radius server ISE_mgarcarz
address ipv4 10.48.17.235 auth-port 1645 acct-port 1646
pac key cisco
aaa group server radius ISE_mgarcarz
server name ISE_mgarcarz
interface GigabitEthernet1/0/3
switchport mode trunk
interface GigabitEthernet1/0/5
description mgarcarz
switchport access vlan 100
switchport mode access
authentication order dot1x mab
authentication priority dot1x mab
authentication port-control auto
mab
dot1x pae authenticator
cts authorization list ISE_mgarcarz
cts role-based enforcement
cts role-based enforcement vlan-list 1-4094
cts sxp enable
cts sxp default password cisco
cts sxp connection peer 10.48.17.235 password default mode local speaker hold-time 0
ISE
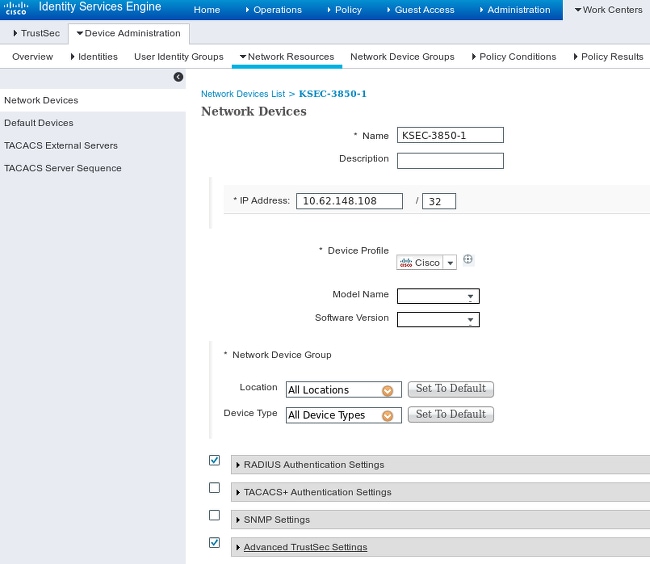
步骤1.网络接入设备
导航到工作中心(Work Centers) >设备管理(Device Administration) >网络资源(Network Resources),使用共享密钥cisco和TrustSec密码Krakow123添加两台交换机。
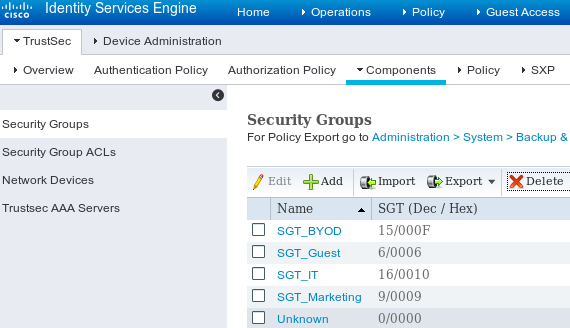
第二步:安全组
要添加面向IT和市场营销的SGT,请导航到工作中心> TrustSec >组件>安全组。
步骤3.安全组ACL
要添加安全组ACL,请导航到工作中心> TrustSec >组件>安全组ACL。
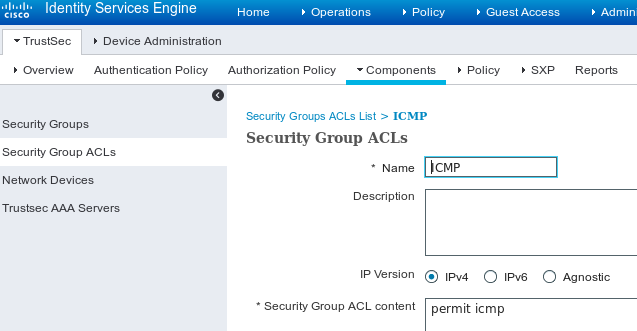
仅允许ICMP流量。
第四步:TrustSec策略
要添加控制从IT到营销的流量的策略,请导航到工作中心> TrustSec >组件>出口策略>矩阵。
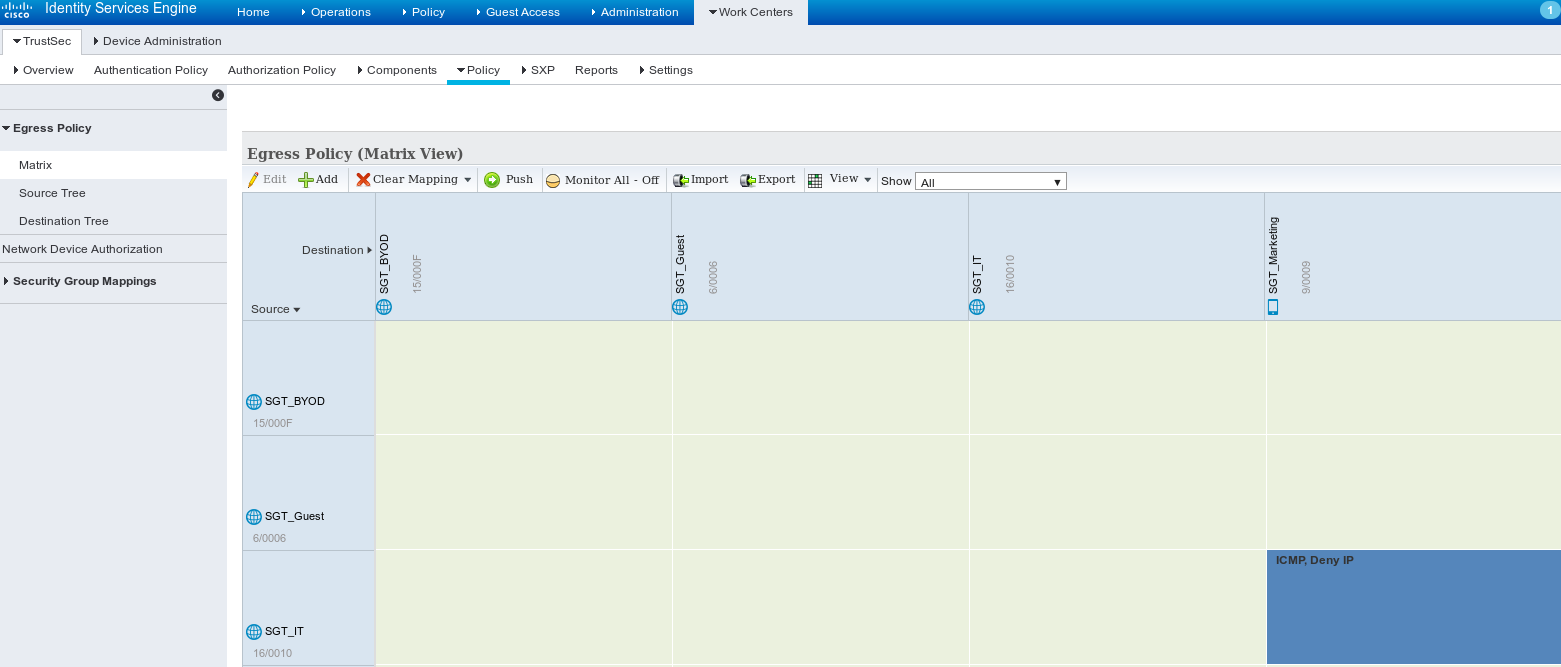
设置默认条目catch all规则以拒绝所有流量。
第五步:SXP设备
要为相应交换机配置SXP侦听器和扬声器,请导航到工作中心> TrustSec > SXP设备。
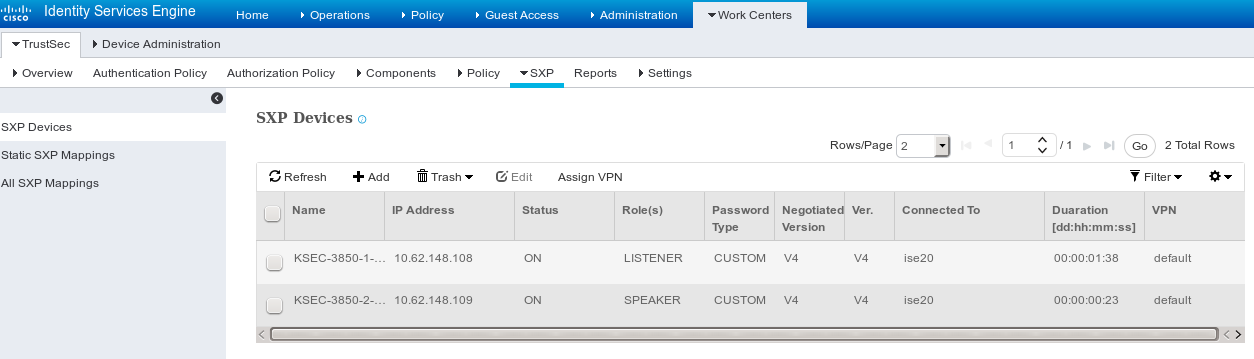
使用口令cisco(或为交换机上的sxp配置的任何其它口令)。
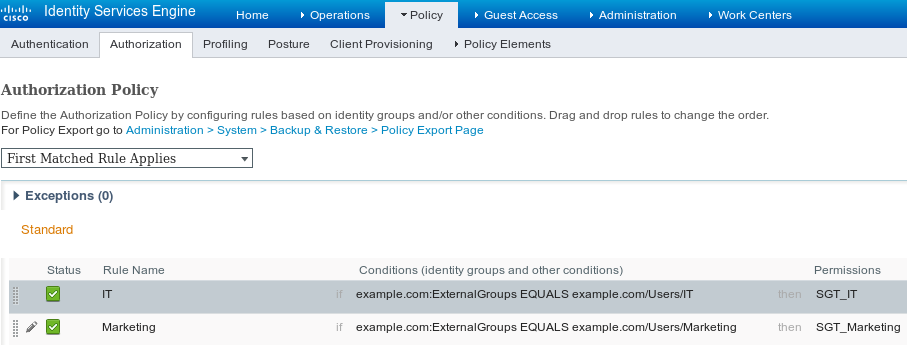
第六步:授权策略
确保授权策略返回每个用户的正确SGT标记,导航到策略>授权。
验证
步骤1:交换机加入CTS的ISE
从每台交换机提供TrustSec凭证(在ISE/第1步中配置)以获取PAC。
KSEC-3850-2#cts credentials id KSEC-3850-2 password Krakow123
CTS device ID and password have been inserted in the local keystore. Please make sure that the same ID and password are configured in the server database.
确保已下载PAC。
KSEC-3850-2#show cts pacs
AID: 65D55BAF222BBC73362A7810A04A005B
PAC-Info:
PAC-type = Cisco Trustsec
AID: 65D55BAF222BBC73362A7810A04A005B
I-ID: KSEC-3850-2
A-ID-Info: Identity Services Engine
Credential Lifetime: 20:42:37 UTC Nov 13 2015
PAC-Opaque: 000200B8000300010004001065D55BAF222BBC73362A7810A04A005B0006009C00030100B26D8DDC125B6595067D64F917DA624C0000001355CB2E1C00093A800E567155E0DE76419D2F3B97D890F34F109C4C42F586B29050CEC7B441E0CA60FC6684D4F6E8263FA2623A6E450927815A140CD3B9D68988E95D8C1E65544E222E187C647B9F7F3F230F6DB4F80F3C201ACD623B309077E27688EDF7704740A1CD3F18CE8485788054C19909083ED303BB49A6975AC0395D41E1227B
Refresh timer is set for 12w4d
并刷新环境策略。
KSEC-3850-2#show cts environment-data
CTS Environment Data
====================
Current state = COMPLETE
Last status = Successful
Local Device SGT:
SGT tag = 0-00:Unknown
Server List Info:
Installed list: CTSServerList1-0001, 1 server(s):
*Server: 10.48.17.235, port 1812, A-ID 65D55BAF222BBC73362A7810A04A005B
Status = ALIVE
auto-test = FALSE, keywrap-enable = FALSE, idle-time = 60 mins, deadtime = 20 secs
Multicast Group SGT Table:
Security Group Name Table:
0-00:Unknown
6-00:SGT_Guest
9-00:SGT_Marketing
15-00:SGT_BYOD
16-00:SGT_IT
255-00:SGT_Quarantine
Environment Data Lifetime = 86400 secs
Last update time = 20:47:04 UTC Sat Aug 15 2015
Env-data expires in 0:08:09:13 (dd:hr:mm:sec)
Env-data refreshes in 0:08:09:13 (dd:hr:mm:sec)
Cache data applied = NONE
State Machine is running
对3850-1重复相同的过程
第2步:802.1x会话
在IT用户通过身份验证后,将分配正确的标记。
KSEC-3850-2#show authentication sessions interface g1/0/5 details
Interface: GigabitEthernet1/0/5
IIF-ID: 0x107E700000000C4
MAC Address: 0050.b611.ed31
IPv6 Address: Unknown
IPv4 Address: 10.0.0.100
User-Name: cisco
Status: Authorized
Domain: DATA
Oper host mode: single-host
Oper control dir: both
Session timeout: N/A
Common Session ID: 0A3E946D00000FF214D18E36
Acct Session ID: 0x00000FDC
Handle: 0xA4000020
Current Policy: POLICY_Gi1/0/5
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
SGT Value: 16
Method status list:
Method State
dot1x Authc Success
映射安装在本地SGT-IP表中。
KSEC-3850-2#show cts role-based sgt-map all
Active IPv4-SGT Bindings Information
IP Address SGT Source
============================================
10.0.0.100 16 LOCAL
第三步:SXP扬声器
3850-2将映射发送到cts sxp的ISE和交换机调试。
KSEC-3850-2(config)#do show debug
CTS:
CTS SXP message debugging is on
*Aug 16 12:48:30.173: CTS-SXP-MSG:trp_send_msg <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.173: CTS-SXP-MSG:trp_socket_write fd<1>, cdbp->ph_sock_pending<1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.226: CTS-SXP-MSG:trp_process_read_sock <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.226: CTS-SXP-MSG:trp_process_read_sock socket_recv result:-1 errno:11; <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.226: CTS-SXP-MSG:trp_process_read_sock socket_conn is accepted; <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.226: CTS-SXP-MSG:trp_socket_write fd<1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.226: CTS-SXP-MSG:trp_socket_write freeing tx_msgq_entry, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.227: CTS-SXP-MSG:after socket_send, wlen=28, slen=0, tot_len=28, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.227: CTS-SXP-MSG:trp_socket_write freeing tx_buf, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.227: CTS-SXP-MSG:trp_socket_read <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.227: CTS-SXP-MSG:trp_socket_read readlen = -1; errno = 11, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.278: CTS-SXP-MSG:trp_process_read_sock <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.278: CTS-SXP-MSG:trp_socket_read <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.278: CTS-SXP-MSG:RCVD peer 10.48.17.235 readlen:32, datalen:0 remain:4096 bufp =
*Aug 16 12:48:30.278: CTS-SXP-MSG:sxp_handle_rx_msg_v2 <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:imu_sxp_conn_cr <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:wrt_sxp_opcode_info_v4 cdbp 0x3D541160
*Aug 16 12:48:30.279: CTS-SXP-MSG:trp_send_msg <1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:trp_socket_write fd<1>, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:trp_socket_write freeing tx_msgq_entry, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:after socket_send, wlen=28, slen=0, tot_len=28, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.279: CTS-SXP-MSG:trp_socket_write freeing tx_buf, <10.48.17.235, 10.62.148.109>
*Aug 16 12:48:30.280: CTS-SXP-MSG:trp_socket_read readlen = 32; errno = 11, <10.48.17.235, 10.62.148.109>
ISE报告(sxp_appserver/sxp.log)
2015-08-16 14:44:07,029 INFO [nioEventLoopGroup-2-3] opendaylight.sxp.core.behavior.Strategy:473 - [ISE:10.48.17.235][10.48.17.235:21121/10.62.148.109:64999][O|Lv4/Sv4 192.168.77.2] PURGEALL processing
2015-08-16 14:44:07,029 WARN [nioEventLoopGroup-2-3] opendaylight.sxp.core.handler.MessageDecoder:173 - [ISE:10.48.17.235][10.48.17.235:21121/10.62.148.109:64999] Channel inactivation
2015-08-16 14:44:07,029 INFO [pool-3-thread-1] sxp.util.database.spi.MasterDatabaseProvider:721 - SXP_PERF:BINDINGS_PER_SXP_UPDATE_MESSAGE(CHUNK)=1, onlyChanged=true
2015-08-16 14:44:07,030 INFO [pool-3-thread-1] sxp.util.database.spi.MasterDatabaseProvider:725 - SXP_PERF:NUM_OF_CHUNKS=1, onlyChanged=true
2015-08-16 14:44:07,030 INFO [pool-3-thread-9] opendaylight.sxp.core.service.UpdateExportTask:93 - SXP_PERF:SEND_UPDATE_BUFFER_SIZE=16
2015-08-16 14:44:07,030 INFO [pool-3-thread-9] opendaylight.sxp.core.service.UpdateExportTask:119 - SENT_UPDATE to [ISE:10.48.17.235][10.48.17.235:57719/10.62.148.108:64999][O|Sv4]
2015-08-16 14:44:07,030 INFO [pool-3-thread-9] opendaylight.sxp.core.service.UpdateExportTask:140 - SENT_UPDATE SUCCESSFUL to [ISE:10.48.17.235][10.48.17.235:57719/10.62.148.108:64999][O|Sv4]:false
2015-08-16 14:44:07,030 INFO [pool-3-thread-1] opendaylight.sxp.core.service.BindingDispatcher:198 - SXP_PERF:MDB_PARTITON_AND_SXP_DISPATCH:DURATION=1 milliseconds, NUM_CONNECTIONS=1
2015-08-16 14:44:07,031 INFO [pool-3-thread-1] sxp.util.database.spi.MasterDatabaseProvider:725 - SXP_PERF:NUM_OF_CHUNKS=0, onlyChanged=true
2015-08-16 14:44:12,534 INFO [nioEventLoopGroup-2-4] opendaylight.sxp.core.behavior.Strategy:232 - [ISE:10.48.17.235][10.48.17.235:64999/10.62.148.109:1035][X|Lv4/Sv4 192.168.77.2] received Message Open
2015-08-16 14:44:12,535 INFO [nioEventLoopGroup-2-4] opendaylight.sxp.core.behavior.Strategy:358 - [ISE:10.48.17.235][10.48.17.235:64999/10.62.148.109:1035][O|Lv4/Sv4 192.168.77.2] Sent RESP 0 0 0 32 0 0 0 2 | 0 0 0 4 0 0 0 2 80 6 6 3 0 2 0 1 0 80 7 4 0 120 0 180
2015-08-16 14:44:12,585 INFO [nioEventLoopGroup-2-4] opendaylight.sxp.core.behavior.Strategy:451 - [ISE:10.48.17.235][10.48.17.235:64999/10.62.148.109:1035][O|Lv4/Sv4 192.168.77.2] received Message Update
2015-08-16 14:44:12,586 INFO [pool-3-thread-2] opendaylight.sxp.core.service.SimpleBindingHandler:663 - PERF_SXP_PROCESS_UPDATE from [ISE:10.48.17.235][10.48.17.235:64999/10.62.148.109:1035][O|Lv4/Sv4 192.168.77.2]
2015-08-16 14:44:12,586 INFO [pool-3-thread-2] opendaylight.sxp.core.service.SimpleBindingHandler:666 - PERF_SXP_PROCESS_UPDATE_DONE from [ISE:10.48.17.235][10.48.17.235:64999/10.62.148.109:1035][O|Lv4/Sv4 192.168.77.2]
2015-08-16 14:44:12,586 INFO [pool-3-thread-1] sxp.util.database.spi.MasterDatabaseProvider:721 - SXP_PERF:BINDINGS_PER_SXP_UPDATE_MESSAGE(CHUNK)=1, onlyChanged=true
2015-08-16 14:44:12,587 INFO [pool-3-thread-1] sxp.util.database.spi.MasterDatabaseProvider:725 - SXP_PERF:NUM_OF_CHUNKS=1, onlyChanged=true
2015-08-16 14:44:12,587 INFO [pool-3-thread-11] opendaylight.sxp.core.service.UpdateExportTask:93 - SXP_PERF:SEND_UPDATE_BUFFER_SIZE=32
2015-08-16 14:44:12,587 INFO [pool-3-thread-11] opendaylight.sxp.core.service.UpdateExportTask:119 - SENT_UPDATE to [ISE:10.48.17.235][10.48.17.235:57719/10.62.148.108:64999][O|Sv4]
2015-08-16 14:44:12,587 INFO [pool-3-thread-11] opendaylight.sxp.core.service.UpdateExportTask:140 - SENT_UPDATE SUCCESSFUL to [ISE:10.48.17.235][10.48.17.235:57719/10.62.148.108:64999][O|Sv4]:false
2015-08-16 14:44:12,587 INFO [pool-3-thread-1] opendaylight.sxp.core.service.BindingDispatcher:198 - SXP_PERF:MDB_PARTITON_AND_SXP_DISPATCH:DURATION=1 milliseconds, NUM_CONNECTIONS=1
并通过GUI显示所有映射(包括从3850-2接收的10.0.0.100映射),如此图中所示。
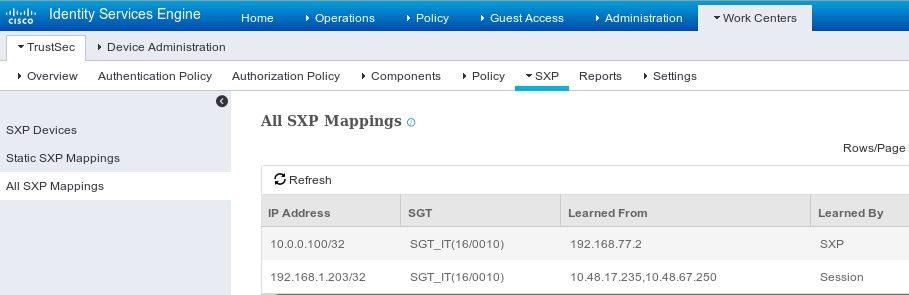
192.168.77.2是3850-2上SXP连接的标识符(定义的最高ip地址)。
KSEC-3850-2#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 unassigned YES unset down down
Vlan1 unassigned YES NVRAM administratively down down
Vlan100 10.0.0.2 YES manual up up
Vlan480 10.62.148.109 YES NVRAM up up
Vlan613 unassigned YES NVRAM administratively down down
Vlan666 192.168.66.2 YES NVRAM down down
Vlan777 192.168.77.2 YES NVRAM down down
第四步:SXP侦听程序
然后,ISE将该映射重新发送到3850-1,进行交换机调试。
*Aug 16 05:42:54.199: CTS-SXP-MSG:trp_send_msg <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.199: CTS-SXP-MSG:trp_socket_write fd<1>, cdbp->ph_sock_pending<1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_process_read_sock <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_process_read_sock socket_recv result:-1 errno:11; <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_process_read_sock socket_conn is accepted; <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_socket_write fd<1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_socket_write freeing tx_msgq_entry, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:after socket_send, wlen=32, slen=0, tot_len=32, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.248: CTS-SXP-MSG:trp_socket_write freeing tx_buf, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.249: CTS-SXP-MSG:trp_socket_read <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.249: CTS-SXP-MSG:trp_socket_read readlen = -1; errno = 11, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.300: CTS-SXP-MSG:trp_process_read_sock <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.300: CTS-SXP-MSG:trp_socket_read <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.300: CTS-SXP-MSG:RCVD peer 10.48.17.235 readlen:28, datalen:0 remain:4096 bufp =
*Aug 16 05:42:54.301: CTS-SXP-MSG:sxp_handle_rx_msg_v2 <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.301: CTS-SXP-MSG:imu_sxp_conn_cr ci<1> cdbp->ph_conn_state<2>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.301: CTS-SXP-MSG:trp_socket_read readlen = 28; errno = 11, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.301: CTS-SXP-MSG:trp_process_read_sock <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:trp_socket_read <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:RCVD peer 10.48.17.235 readlen:52, datalen:0 remain:4096 bufp =
*Aug 16 05:42:54.302: CTS-SXP-MSG:sxp_handle_rx_msg_v2 <1>, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:sxp_recv_update_v4 <1> peer ip: 10.48.17.235
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:44, opc_ptr:0x3DFC7308, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:37, opc_ptr:0x3DFC730F, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:32, opc_ptr:0x3DFC7314, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:24, opc_ptr:0x3DFC731C, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:13, opc_ptr:0x3DFC7327, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.302: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:8, opc_ptr:0x3DFC732C, <10.48.17.235, 10.62.148.108>
*Aug 16 05:42:54.303: CTS-SXP-MSG:1. msg type:3, total len:52, payl len:0, opc_ptr:0x3DFC7334, <10.48.17.235, 10.62.148.108>
从ISE捕获的流向3850-1的数据包确认正在发送SXP映射。
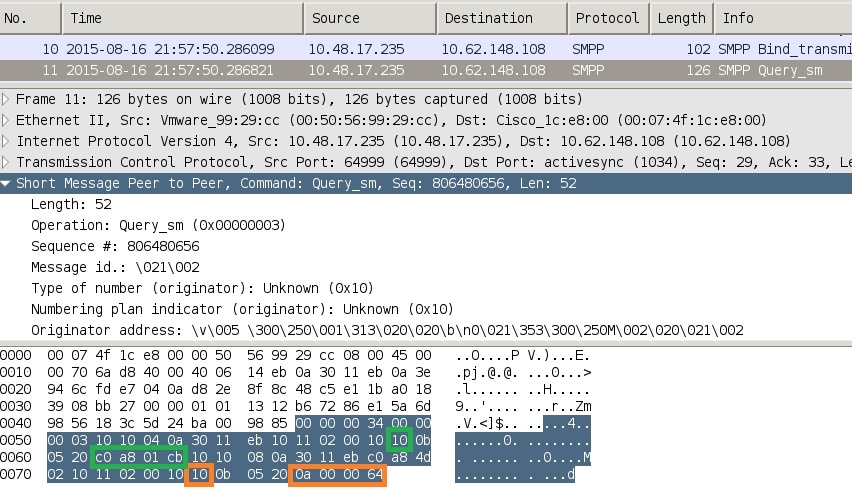
Wireshark使用标准SMPP解码器。要检查负载,请执行以下操作:
“c0 a8 01 cb”(192.168.1.203)为10 (SGT = 16)
“0a 00 00 64” (10.0.0.100)为10 (SGT = 16)
3850-1安装从ISE接收的所有映射。
KSEC-3850-1# show cts sxp sgt-map
SXP Node ID(generated):0xC0A84D01(192.168.77.1)
IP-SGT Mappings as follows:
IPv4,SGT: <10.0.0.100 , 16:SGT_IT>
source : SXP;
Peer IP : 10.48.17.235;
Ins Num : 2;
Status : Active;
Seq Num : 439
Peer Seq: 0A3011EB,C0A84D02,
IPv4,SGT: <192.168.1.203 , 16:SGT_IT>
source : SXP;
Peer IP : 10.48.17.235;
Ins Num : 6;
Status : Active;
Seq Num : 21
Peer Seq: 0A3011EB,
Total number of IP-SGT Mappings: 2
KSEC-3850-1# show cts role-based sgt-map all
Active IPv4-SGT Bindings Information
IP Address SGT Source
============================================
10.0.0.100 16 SXP
192.168.1.203 16 SXP
IP-SGT Active Bindings Summary
============================================
Total number of CLI bindings = 1
Total number of SXP bindings = 2
Total number of active bindings = 3
第五步:策略下载和实施
从ISE下载正确的策略。(使用SGT 16的矩阵行)
KSEC-3850-1#show cts role-based permissions
IPv4 Role-based permissions default:
Permit IP-00
IPv4 Role-based permissions from group 16:SGT_IT to group 9:SGT_Marketing:
ICMP-10
Deny IP-00
RBACL Monitor All for Dynamic Policies : FALSE
RBACL Monitor All for Configured Policies : FALSE
允许从10.0.0.100 (SGT IT)到10.0.0.1 (SGT营销)的ICMP流量,计数增加。
KSEC-3850-1#show cts role-based counters from 16
Role-based IPv4 counters
#Hardware counters are not available for specific SGT/DGT
#Use this command without arguments to see hardware counters
From To SW-Denied SW-Permitted
16 9 0 0 11 0
当尝试使用telnet连接失败时,丢弃计数器增加。
KSEC-3850-1#show cts role-based counters from 16
Role-based IPv4 counters
#Hardware counters are not available for specific SGT/DGT
#Use this command without arguments to see hardware counters
From To SW-Denied SW-Permitted
16 9 3 0 11 0
请注意,3850-2上没有特定策略,允许所有流量。
KSEC-3850-2#show cts role-based permissions
IPv4 Role-based permissions default:
Permit IP-00
RBACL Monitor All for Dynamic Policies : FALSE
RBACL Monitor All for Configured Policies : FALSE
在ISE上修改SG ACL后,在3850-1上添加permit tcp和cts刷新策略-然后接受telnet流量。
还可以使用Flexible Netflow(从IOS-XE 3.7.2开始是SGT感知)本地缓存来确认行为。
flow record cts-v4
match ipv4 protocol
match ipv4 source address
match ipv4 destination address
match transport source-port
match transport destination-port
match flow direction
match flow cts source group-tag
match flow cts destination group-tag
collect counter packets long
flow monitor F_MON
record cts-v4
interface GigabitEthernet1/0/3
ip flow monitor F_MON input
ip flow monitor F_MON output
结果显示从3850-2接收的流量。源SGT为0,因为接收的流量没有任何SGT(无cts链路),但目标组标记根据本地映射表自动替换。
KSEC-3850-1#show flow monitor F_MON cache
Cache type: Normal (Platform cache)
Cache size: Unknown
Current entries: 6
Flows added: 1978
Flows aged: 1972
- Active timeout ( 1800 secs) 30
- Inactive timeout ( 15 secs) 1942
IPV4 SRC ADDR IPV4 DST ADDR TRNS SRC PORT TRNS DST PORT FLOW DIRN FLOW CTS SRC GROUP TAG FLOW CTS DST GROUP TAG IP PROT pkts long
=============== =============== ============= ============= ========= ====================== ====================== ======= ====================
150.1.7.1 224.0.0.10 0 0 Output 0 0 88 57
10.62.148.1 224.0.0.13 0 8192 Output 0 0 103 0
7.7.4.1 224.0.0.10 0 0 Output 0 0 88 56
10.0.0.1 10.0.0.100 0 0 Output 0 0 1 1388
150.1.7.105 224.0.0.5 0 0 Output 0 0 89 24
150.1.7.1 224.0.0.5 0 0 Output 0 0 89 24
10.0.0.100 10.0.0.1 0 2048 Input 0 9 1 1388
Netflow本地缓存可用于确认收到的流量。如果该流量被接受或丢弃,则由之前提供的cts计数器确认。
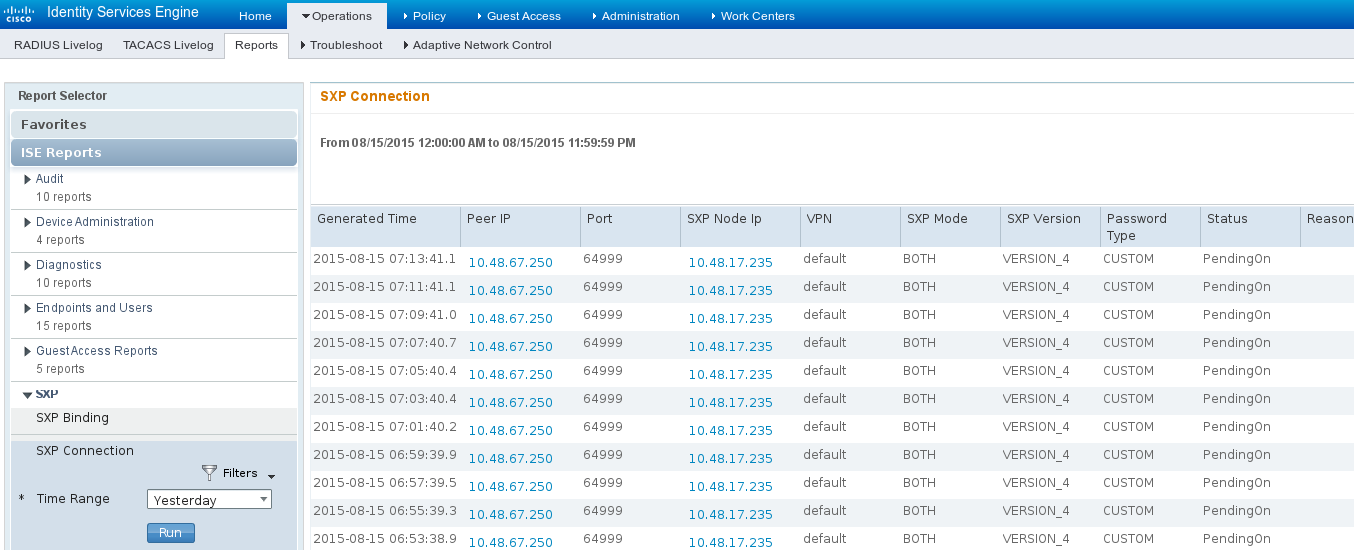
ISE还允许生成SXP绑定和连接报告,如下图所示。
参考
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
01-Dec-2015
|
初始版本 |
 反馈
反馈