使用重叠方案配置ASA VPN
下载选项
非歧视性语言
此产品的文档集力求使用非歧视性语言。在本文档集中,非歧视性语言是指不隐含针对年龄、残障、性别、种族身份、族群身份、性取向、社会经济地位和交叉性的歧视的语言。由于产品软件的用户界面中使用的硬编码语言、基于 RFP 文档使用的语言或引用的第三方产品使用的语言,文档中可能无法确保完全使用非歧视性语言。 深入了解思科如何使用包容性语言。
关于此翻译
思科采用人工翻译与机器翻译相结合的方式将此文档翻译成不同语言,希望全球的用户都能通过各自的语言得到支持性的内容。 请注意:即使是最好的机器翻译,其准确度也不及专业翻译人员的水平。 Cisco Systems, Inc. 对于翻译的准确性不承担任何责任,并建议您总是参考英文原始文档(已提供链接)。
目录
简介
本文档介绍用于在重叠场景中转换通过两个自适应安全设备(ASA)之间的LAN到LAN(L2L)IPsec隧道传输的VPN流量以及互联网流量的端口地址转换(PAT)的步骤。
先决条件
要求
在继续本配置示例之前,请确保您已在接口上对 Cisco 自适应安全设备进行了 IP 地址配置并具备基本的连接。
使用的组件
本文档中的信息基于以下软件版本:
-
思科自适应安全设备软件8.3版及更高版本。
本文档中的信息都是基于特定实验室环境中的设备编写的。本文档中使用的所有设备最初均采用原始(默认)配置。如果您的网络处于活动状态,请确保您了解所有命令的潜在影响。
背景信息
每台设备后面都有一个受保护的专用网络。在重叠情况下,由于流量发送到同一子网的IP地址,因此数据包永远不会离开本地子网,所以不会通过VPN进行通信。这可以通过网络地址转换(NAT)来完成,如以下各节所述。
两个VPN终端上的转换
当VPN保护网络重叠时,可以在两个终端上修改配置;NAT可用于在转至远程转换的子网时将本地网络转换为不同的子网。
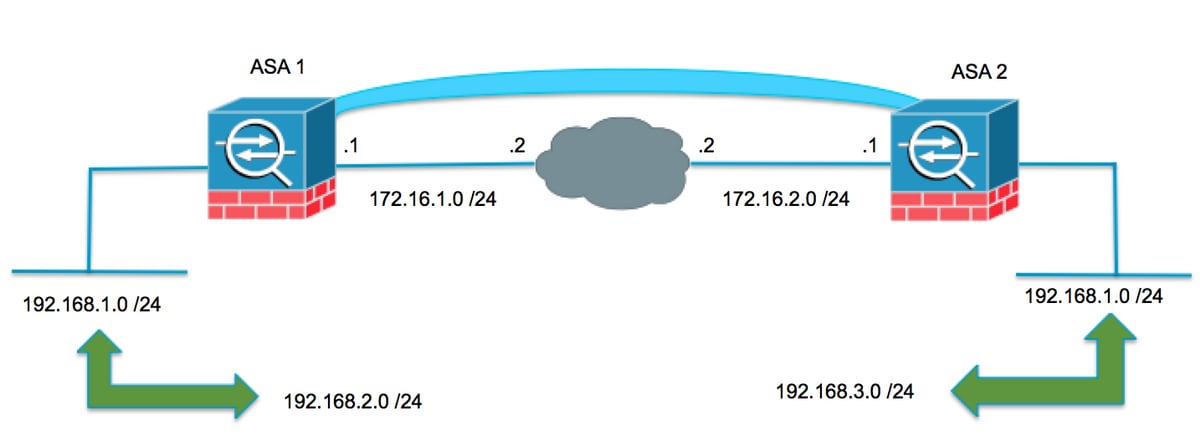
ASA 1
为正在使用的子网创建必要的对象
object network LOCAL subnet 192.168.1.0 255.255.255.0 object network XLATED-LOCAL subnet 192.168.2.0 255.255.255.0 object network XLATED-REMOTE subnet 192.168.3.0 255.255.255.0
配置NAT语句
创建手动语句,以便仅在转到远程子网时(也转换了)将本地网络转换为不同的子网
nat (inside,outside) source static LOCAL XLATED-LOCAL destination static XLATED-REMOTE XLATED-REMOTE
使用转换后的子网配置加密ACL
access-list VPN-TRAFFIC extended permit ip object XLATED-LOCAL object XLATED-REMOTE Rele
相关加密配置
crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 crypto ipsec ikev1 transform-set AES256-SHA esp-aes-256 esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map MYMAP 10 match address VPN-TRAFFIC crypto map MYMAP 10 set peer 172.16.2.1 crypto map MYMAP 10 set ikev1 transform-set AES256-SHA crypto map MYMAP interface outside tunnel-group 172.16.2.1 type ipsec-l2l tunnel-group 172.16.2.1 ipsec-attributes ikev1 pre-shared-key secure_PSK
ASA 2
为正在使用的子网创建必要的对象
object network LOCAL subnet 192.168.1.0 255.255.255.0 object network XLATED-LOCAL subnet 192.168.3.0 255.255.255.0 object network XLATED-REMOTE subnet 192.168.2.0 255.255.255.0
配置NAT语句
创建手动语句,以便仅在转到远程子网时(也转换了)将本地网络转换为不同的子网
nat (inside,outside) source static LOCAL XLATED-LOCAL destination static XLATED-REMOTE XLATED-REMOTE
使用转换后的子网配置加密ACL
access-list VPN-TRAFFIC extended permit ip object XLATED-LOCAL object XLATED-REMOTE Rele
相关加密配置
crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 crypto ipsec ikev1 transform-set AES256-SHA esp-aes-256 esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map MYMAP 10 match address VPN-TRAFFIC crypto map MYMAP 10 set peer 172.16.1.1 crypto map MYMAP 10 set ikev1 transform-set AES256-SHA crypto map MYMAP interface outside tunnel-group 172.16.1.1 type ipsec-l2l tunnel-group 172.16.1.1 ipsec-attributes ikev1 pre-shared-key secure_PSK
验证
使用本部分可确认配置能否正常运行。
ASA 1
ASA1(config)# sh cry isa sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 172.16.2.1
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAsASA1(config)# show crypto ipsec sa
interface: outside
Crypto map tag: MYMAP, seq num: 10, local addr: 172.16.1.1
access-list VPN-TRAFFIC extended permit ip 192.168.2.0 255.255.255.0 192.168.3.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
current_peer: 172.16.2.1
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 9, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.16.1.1/0, remote crypto endpt.: 172.16.2.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: F90C149A
current inbound spi : 6CE656C7
inbound esp sas:
spi: 0x6CE656C7 (1827034823)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 16384, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/28768)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x000003FF
outbound esp sas:
spi: 0xF90C149A (4178318490)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 16384, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/28768)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
ASA 2
ASA2(config)# show crypto isa sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 172.16.1.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAsASA2(config)# show crypto ipsec sa
interface: outside
Crypto map tag: MYMAP, seq num: 10, local addr: 172.16.2.1
access-list VPN-TRAFFIC extended permit ip 192.168.3.0 255.255.255.0 192.168.2.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.3.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer: 172.16.1.1
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 9, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.16.2.1/0, remote crypto endpt.: 172.16.1.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 6CE656C7
current inbound spi : F90C149A
inbound esp sas:
spi: 0xF90C149A (4178318490)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 12288, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (4373999/28684)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x000003FF
outbound esp sas:
spi: 0x6CE656C7 (1827034823)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 12288, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (4373999/28683)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
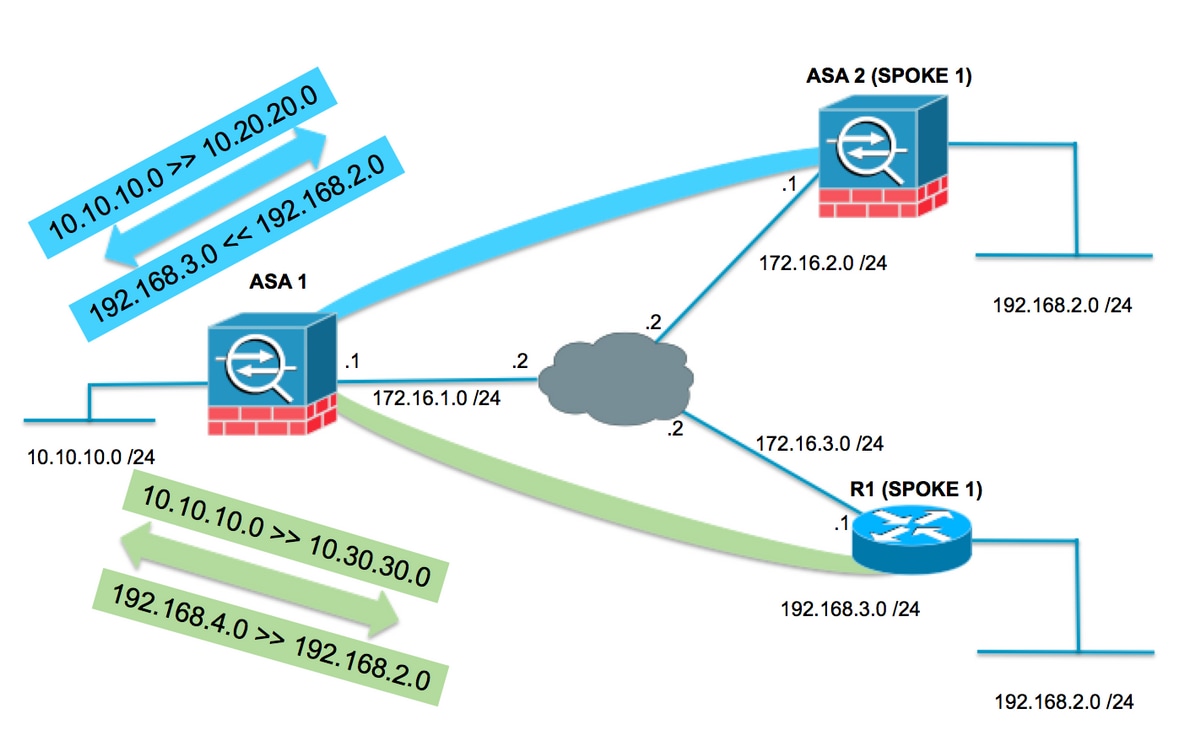
具有重叠分支的中心辐射型拓扑
在以下拓扑中,两个分支具有需要通过通往集线器的IPsec隧道保护的相同子网。为了便于分支上的管理,NAT配置只对集线器执行以解决重叠问题。
ASA1
为正在使用的子网创建必要的对象
object network LOCAL subnet 10.10.10.0 255.255.255.0 object network SPOKES-NETWORK subnet 192.168.2.0 255.255.255.0 object network LOCAL-XLATE-TO-SPOKE1 subnet 10.20.20.0 255.255.255.0 object network LOCAL-XLATE-TO-SPOKE2 subnet 10.30.30.0 255.255.255.0 object network REMOTE-XLATE-SPOKE1 subnet 192.168.3.0 255.255.255.0 object network REMOTE-XLATE-SPOKE2 subnet 192.168.4.0 255.255.255.0
创建要转换的手动语句:
- 本地网络10.10.10.0 /24到10.20.20.0 /24(当转到SPOKE1(192.168.2.0 /24)时)。
- SPOKE1网络192.168.2.0 /24到192.168.3.0 /24(当到达10.20.20.0 /24时)。
- 本地网络10.10.10.0 /24到10.30.30.0 /24(当转到SPOKE3(192.168.2.0 /24)时)。
- SPOKE2网络192.168.2.0 /24到192.168.4.0 /24(当到达10.30.30.0 /24时)。
nat (inside,outside) source static LOCAL LOCAL-XLATE-SPOKE1 destination static REMOTE-XLATE-SPOKE1 SPOKES-NETWORK nat (inside,outside) source static LOCAL LOCAL-XLATE-SPOKE2 destination static REMOTE-XLATE-SPOKE2 SPOKES-NETWORK
使用转换后的子网配置加密ACL
access-list VPN-to-SPOKE1 extended permit ip object LOCAL-XLATE-SPOKE1 object SPOKES-NETWORKS access-list VPN-to-SPOKE2 extended permit ip object LOCAL-XLATE-SPOKE2 object SPOKES-NETWORKS
相关加密配置
crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 crypto ipsec ikev1 transform-set AES256-SHA esp-aes-256 esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map MYMAP 10 match address VPN-to-SPOKE1 crypto map MYMAP 10 set peer 172.16.2.1 crypto map MYMAP 10 set ikev1 transform-set AES256-SHA crypto map MYMAP 20 match address VPN-to-SPOKE2 crypto map MYMAP 20 set peer 172.16.3.1 crypto map MYMAP 20 set ikev1 transform-set AES256-SHA crypto map MYMAP interface outside tunnel-group 172.16.2.1 type ipsec-l2l tunnel-group 172.16.2.1 ipsec-attributes ikev1 pre-shared-key secure_PSK tunnel-group 172.16.3.1 type ipsec-l2l tunnel-group 172.16.3.1 ipsec-attributes ikev1 pre-shared-key secure_PSK
ASA2(SPOKE1)
配置通往转换后子网(10.20.20.0 /24)的加密ACL
access-list VPN-TRAFFIC extended permit ip 192.168.2.0 255.255.255.0 10.20.20.0 255.255.255.0
相关加密配置
crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes-256 hash sha group 2 lifetime 86400 crypto ipsec ikev1 transform-set esp-aes-256 esp-sha-hmac crypto ipsec security-association pmtu-aging infinite crypto map MYMAP 10 match address VPN-TRAFFIC crypto map MYMAP 10 set peer 172.16.1.1 crypto map MYMAP 10 set ikev1 transform-set AES256-SHA crypto map MYMAP interface outside tunnel-group 172.16.1.1 type ipsec-l2l tunnel-group 172.16.1.1 ipsec-attributes ikev1 pre-shared-key secure_PSK
R1(SPOKE2)
配置通往转换后子网(10.30.30.0 /24)的加密ACL
ip access-list extended VPN-TRAFFIC permit ip 192.168.2.0 0.0.0.255 10.30.30.0 0.0.0.255
相关加密配置
crypto isakmp policy 1
encr aes 256
authentication pre-share
group 2
crypto isakmp key secure_PSK address 172.16.1.1
crypto ipsec transform-set AES256-SHA esp-aes 256 esp-sha-hmac
mode tunnel
crypto map MYMAP 10 ipsec-isakmp
set peer 172.16.1.1
set transform-set AES256-SHA
match address VPN-TRAFFIC
interface GigabitEthernet0/1
ip address 172.16.3.1 255.255.255.0
duplex auto
speed auto
media-type rj45
crypto map MYMAP验证
ASA 1
ASA1(config)# show crypto isakmp sa
IKEv1 SAs:
Active SA: 2
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 2
1 IKE Peer: 172.16.3.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
2 IKE Peer: 172.16.2.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAsASA1(config)# show crypto ipsec sa
interface: outside
Crypto map tag: MYMAP, seq num: 10, local addr: 172.16.1.1
access-list VPN-to-SPOKE1 extended permit ip 10.20.20.0 255.255.255.0 192.168.2.0 255.255.255.0
local ident (addr/mask/prot/port): (10.20.20.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer: 172.16.2.1
#pkts encaps: 10, #pkts encrypt: 9, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 9, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 9, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.16.1.1/0, remote crypto endpt.: 172.16.2.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 79384296
current inbound spi : 2189BF7A
inbound esp sas:
spi: 0x2189BF7A (562675578)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 12288, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/28618)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x000003FF
outbound esp sas:
spi: 0x79384296 (2033730198)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 12288, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/28618)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
Crypto map tag: MYMAP, seq num: 20, local addr: 172.16.1.1
access-list VPN-to-SPOKE2 extended permit ip 10.30.30.0 255.255.255.0 192.168.2.0 255.255.255.0
local ident (addr/mask/prot/port): (10.30.30.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
current_peer: 172.16.3.1
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 4, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.16.1.1/0, remote crypto endpt.: 172.16.3.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 65FDF4F5
current inbound spi : 05B7155D
inbound esp sas:
spi: 0x05B7155D (95884637)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 8192, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/2883)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x0000001F
outbound esp sas:
spi: 0x65FDF4F5 (1711142133)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 8192, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (3914999/2883)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001 ASA2(SPOKE1)
ASA2(config)# show crypto isakmp sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 172.16.1.1
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
There are no IKEv2 SAsASA2(config)# show crypto ipsec sa
interface: outside
Crypto map tag: MYMAP, seq num: 10, local addr: 172.16.2.1
access-list VPN-TRAFFIC extended permit ip 192.168.2.0 255.255.255.0 10.20.20.0 255.255.255.0
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.20.20.0/255.255.255.0/0/0)
current_peer: 172.16.1.1
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 9, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 172.16.2.1/0, remote crypto endpt.: 172.16.1.1/0
path mtu 1500, ipsec overhead 74(44), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 2189BF7A
current inbound spi : 79384296
inbound esp sas:
spi: 0x79384296 (2033730198)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 8192, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (4373999/28494)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x000003FF
outbound esp sas:
spi: 0x2189BF7A (562675578)
transform: esp-aes-256 esp-sha-hmac no compression
in use settings ={L2L, Tunnel, IKEv1, }
slot: 0, conn_id: 8192, crypto-map: MYMAP
sa timing: remaining key lifetime (kB/sec): (4373999/28494)
IV size: 16 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001R1(SPOKE2)
R31show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 172.16.1.1 172.16.3.1 QM_IDLE 1001 ACTIVE IPv6 Crypto ISAKMP SA
R1#show crypto ipsec sa
interface: GigabitEthernet0/1
Crypto map tag: MYMAP, local addr 172.16.3.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.2.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.30.30.0/255.255.255.0/0/0)
current_peer 172.16.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 10, #pkts encrypt: 10, #pkts digest: 10
#pkts decaps: 10, #pkts decrypt: 10, #pkts verify: 10
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.3.1, remote crypto endpt.: 172.16.1.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/1
current outbound spi: 0x5B7155D(95884637)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x65FDF4F5(1711142133)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80004040, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4188495/2652)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x5B7155D(95884637)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80004040, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4188495/2652)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:故障排除
本部分提供的信息可用于对配置进行故障排除。
清除安全关联
排除故障时,请务必在进行更改后清除现有的 SA。在 PIX 的特权模式下,使用以下命令:
-
clear crypto ipsec sa - 删除活动的 IPsec SA。
-
clear crypto isakmp sa - 删除活动的 IKE SA。
检查NAT配置
-
show nat detail — 显示扩展了对象/对象组的NAT配置
故障排除命令
使用本部分可确认配置能否正常运行。
思科 CLI 分析器(仅适用于注册客户)支持某些 show 命令。要查看对 show 命令输出的分析,请使用思科 CLI 分析器。
注意:使用 debug 命令之前,请参阅有关 debug 命令的重要信息和 IP 安全故障排除 - 了解和使用 debug 命令。
-
debug crypto ipsec - 显示第 2 阶段的 IPsec 协商。
-
debug crypto isakmp - 显示第 1 阶段的 ISAKMP 协商。
相关信息
修订历史记录
| 版本 | 发布日期 | 备注 |
|---|---|---|
1.0 |
25-May-2017
|
初始版本 |
由思科工程师提供
- 古斯塔沃·梅迪纳
 反馈
反馈