Introduzione
In questo documento viene descritta la configurazione per configurare un tunnel da sito a sito IPv6 basato su routing tra due router Cisco con protocollo IKEv2 (Internet Key Exchange versione 2).
Prerequisiti
Requisiti
Cisco raccomanda la conoscenza dei seguenti argomenti:
- Conoscenze fondamentali della configurazione CLI di Cisco IOS®/Cisco IOS® XE
- Conoscenze base dei protocolli ISAKMP (Internet Security Association and Key Management Protocol) e IPsec
- Informazioni sull'indirizzamento e il routing IPv6
Componenti usati
Le informazioni fornite in questo documento si basano sulle seguenti versioni software:
- Cisco IOS XE con 17.03.04a come router locale
- Cisco IOS con versione 17.03.04a come router remoto
Le informazioni discusse in questo documento fanno riferimento a dispositivi usati in uno specifico ambiente di emulazione. Su tutti i dispositivi menzionati nel documento la configurazione è stata ripristinata ai valori predefiniti. Se la rete è operativa, valutare attentamente eventuali conseguenze derivanti dall'uso dei comandi.
Configurazione
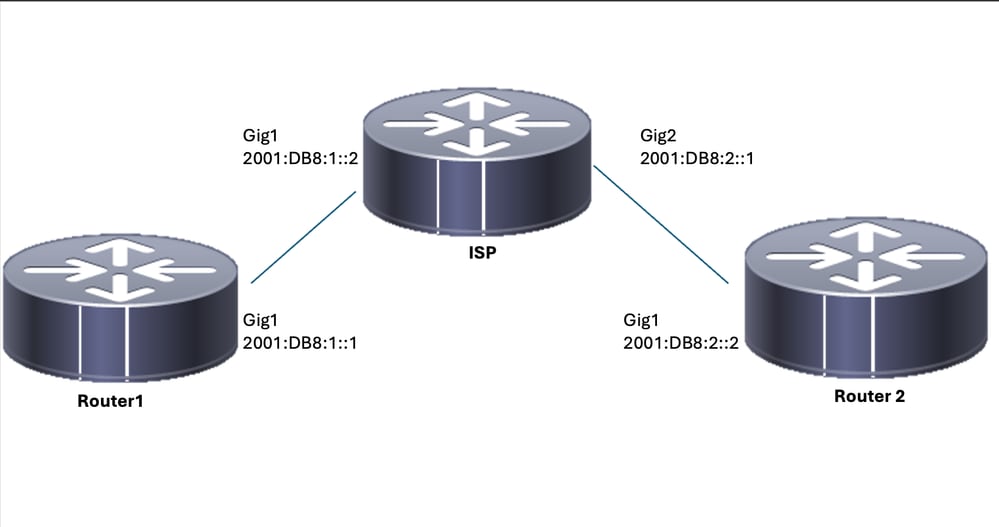
Esempio di rete
Configurazioni router locale
Passaggio 1. Abilitare il routing unicast IPv6.
ipv6 unicast-routing
Passo 2: configurare le interfacce del router.
interface GigabitEthernet1
ipv6 address 2001:DB8:1::1/64
no shutdown
interface GigabitEthernet2
ipv6 address FC00::1/64
no shutdown
Passaggio 3. Impostare la route predefinita IPv6.
ipv6 route ::/0 GigabitEthernet1
Passaggio 4. Configurare La Proposta Ikev2.
crypto ikev2 proposal IKEv2-PROP
encryption aes-cbc-128
integrity sha1
group 14
Passaggio 5. Configurare I Criteri Ikev2.
crypto ikev2 policy IKEv2-POLI
proposal IKEv2-PROP
Passaggio 6. Configurare il keyring con una chiave già condivisa.
crypto ikev2 keyring IPV6_KEY
peer Remote_IPV6
address 2001:DB8:2::2/64
pre-shared-key cisco123
Passaggio 7. Configurare il profilo Ikev2.
crypto ikev2 profile IKEV2-PROF
match identity remote address 2001:DB8:2::2/64
authentication remote pre-share
authentication local pre-share
keyring local IPV6_KEY
Passaggio 8. Configurare il criterio Fase 2.
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac
mode tunnel
Passaggio 9. Configurare il profilo IPSec.
crypto ipsec profile IPSEC-PROF
set transform-set ESP-AES-SHA
set ikev2-profile IKEV2-PROF
Passaggio 10. Configurare l'interfaccia del tunnel.
interface Tunnel1
ipv6 address 2001:DB8:3::1/64
tunnel source GigabitEthernet1
tunnel mode ipsec ipv6
tunnel destination 2001:DB8:2::2
tunnel protection ipsec profile IPSEC-PROF
end
Passaggio 11. Configurare le route per il traffico interessante.
ipv6 route FC00::/64 2012::1
Configurazione finale router locale
ipv6 unicast-routing
!
interface GigabitEthernet1
ipv6 address 2001:DB8:1::1/64
no shutdown
!
interface GigabitEthernet2
ipv6 address FC00::1/64
no shutdown
!
ipv6 route ::/0 GigabitEthernet1
!
crypto ikev2 proposal IKEv2-PROP
encryption aes-cbc-128
integrity sha1
group 14
!
crypto ikev2 policy IKEv2-POLI
proposal IKEv2-PROP
!
crypto ikev2 keyring IPV6_KEY
peer Remote_IPV6
address 2001:DB8:2::2/64
pre-shared-key cisco123
!
crypto ikev2 profile IKEV2-PROF
match identity remote address 2001:DB8:2::2/64
authentication remote pre-share
authentication local pre-share
keyring local IPV6_KEY
!
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec profile Prof1
set transform-set ESP-AES-SHA
!
crypto ipsec profile IPSEC-PROF
set transform-set ESP-AES-SHA
set ikev2-profile IKEV2-PROF
!
interface Tunnel1
ipv6 address 2001:DB8:3::1/64
tunnel source GigabitEthernet1
tunnel mode ipsec ipv6
tunnel destination 2001:DB8:2::2
tunnel protection ipsec profile IPSEC-PROF
end
!
ipv6 route FC00::/64 2012::1
Configurazione ISP
ipv6 unicast-routing
!
!
interface GigabitEthernet1
description Link to R1
ipv6 address 2001:DB8:1::2/64
!
interface GigabitEthernet2
description Link to R3
ipv6 address 2001:DB8:2::1/64
!
!
!
ipv6 route 2001:DB8:1::/64 GigabitEthernet1
ipv6 route 2001:DB8:2::/64 GigabitEthernet2
!
Configurazione finale router remoto
ipv6 unicast-routing
!
interface GigabitEthernet1
ipv6 address 2001:DB8:2::2/64
no shutdown
!
interface GigabitEthernet2
ipv6 address FC00::2/64
no shutdown
!
ipv6 route ::/0 GigabitEthernet1
!
crypto ikev2 proposal IKEv2-PROP
encryption aes-cbc-128
integrity sha1
group 14
!
crypto ikev2 policy IKEv2-POLI
proposal IKEv2-PROP
!
crypto ikev2 keyring IPV6_KEY
peer Remote_IPV6
address 2001:DB8:1::1/64
pre-shared-key cisco123
!
crypto ikev2 profile IKEV2-PROF
match identity remote address 2001:DB8:1::1/64
authentication remote pre-share
authentication local pre-share
keyring local IPV6_KEY
!
crypto ipsec transform-set ESP-AES-SHA esp-aes esp-sha-hmac
mode tunnel
!
crypto ipsec profile Prof1
set transform-set ESP-AES-SHA
!
crypto ipsec profile IPSEC-PROF
set transform-set ESP-AES-SHA
set ikev2-profile IKEV2-PROF
!
interface Tunnel1
ipv6 address 2001:DB8:3::2/64
tunnel source GigabitEthernet1
tunnel mode ipsec ipv6
tunnel destination 2001:DB8:1::1
tunnel protection ipsec profile IPSEC-PROF
end
!
ipv6 route FC00::/64 2012::1
Verifica
On Router 1
R1#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
IPv6 Crypto IKEv2 SA
Tunnel-id fvrf/ivrf Status
2 none/none READY
Local 2001:DB8:1::1/500
Remote 2001:DB8:2::2/500
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/75989 sec
R1#show crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 2001:DB8:1::1
protected vrf: (none)
local ident (addr/mask/prot/port): (::/0/0/0)
remote ident (addr/mask/prot/port): (::/0/0/0)
current_peer 2001:DB8:2::2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 14, #pkts encrypt: 14, #pkts digest: 14
#pkts decaps: 14, #pkts decrypt: 14, #pkts verify: 14
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2001:DB8:1::1,
remote crypto endpt.: 2001:DB8:2::2
plaintext mtu 1422, path mtu 1500, ipv6 mtu 1500, ipv6 mtu idb GigabitEthernet1
current outbound spi: 0x9DC2A6F6(2646779638)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x18569EF7(408329975)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2104, flow_id: CSR:104, sibling_flags FFFFFFFF80000049, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4608000/1193)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x9DC2A6F6(2646779638)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2103, flow_id: CSR:103, sibling_flags FFFFFFFF80000049, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4608000/1193)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
On Router 2
R2#show crypto ikev2 sa
IPv4 Crypto IKEv2 SA
IPv6 Crypto IKEv2 SA
Tunnel-id fvrf/ivrf Status
1 none/none READY
Local 2001:DB8:2::2/500
Remote 2001:DB8:1::1/500
Encr: AES-CBC, keysize: 256, PRF: SHA256, Hash: SHA256, DH Grp:14, Auth sign: PSK, Auth verify: PSK
Life/Active Time: 86400/19 sec
R2#show cryto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 2001:DB8:2::2
protected vrf: (none)
local ident (addr/mask/prot/port): (::/0/0/0)
remote ident (addr/mask/prot/port): (::/0/0/0)
current_peer 2001:DB8:1::1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 14, #pkts encrypt: 14, #pkts digest: 14
#pkts decaps: 14, #pkts decrypt: 14, #pkts verify: 14
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2001:DB8:2::2,
remote crypto endpt.: 2001:DB8:1::1
plaintext mtu 1422, path mtu 1500, ipv6 mtu 1500, ipv6 mtu idb GigabitEthernet1
current outbound spi: 0xEF1D3BA2(4011670434)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x9829B86D(2552871021)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2006, flow_id: CSR:6, sibling_flags FFFFFFFF80000049, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4608000/3556)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xEF1D3BA2(4011670434)
transform: esp-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 2005, flow_id: CSR:5, sibling_flags FFFFFFFF80000049, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4607998/3556)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Risoluzione dei problemi
Per risolvere i problemi del tunnel, usare i seguenti comandi di debug:
debug crypto ikev2debug crypto ikev2 errordebug crypto ipsecdebug crypto ipsec error

 Feedback
Feedback