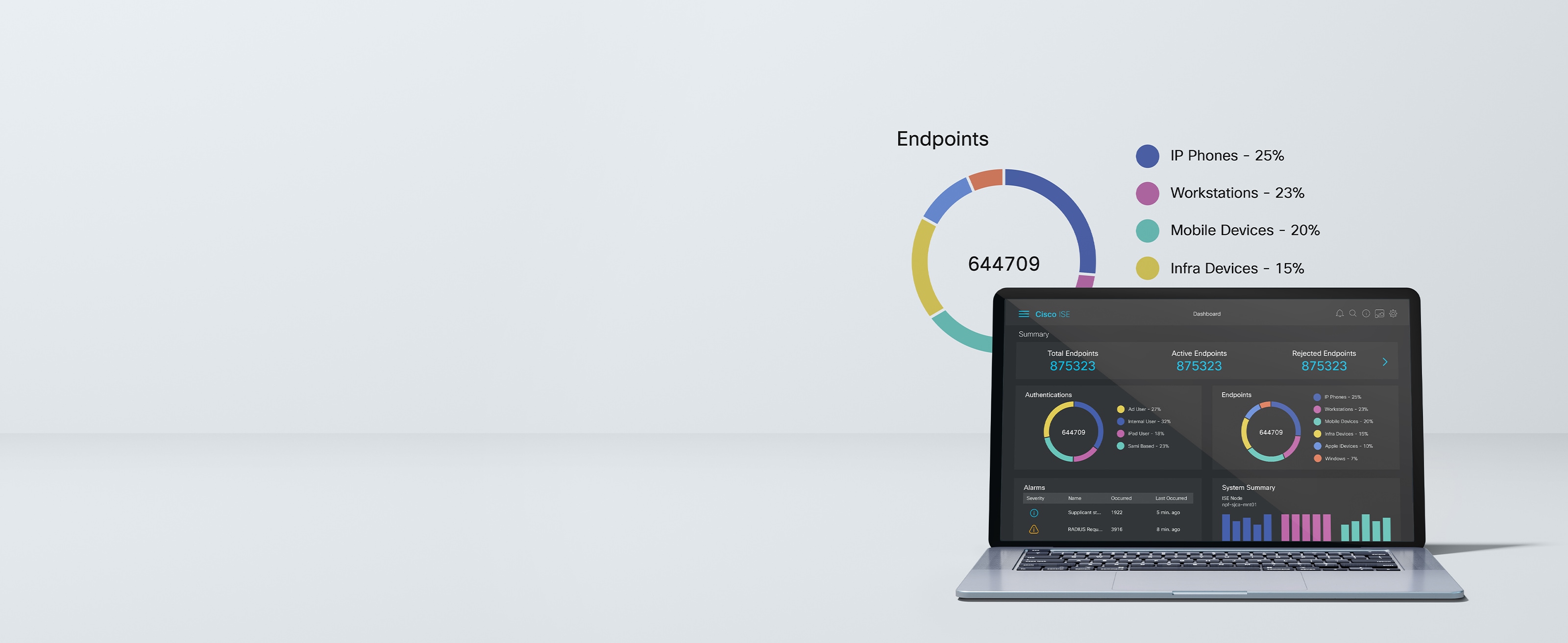
In zero-trust architecture, ISE is the policy decision point. It gathers intel from the stack to authenticate users and endpoints, automatically containing threats.
Harness the power of resilience
Resilience begins with secure connections. ISE helps ensure that only trusted users and their devices can access resources across your self-managed network.
Visibility better than 20/20
Knowing who's connecting to your network, what devices they're on, and what connection they're using is key. ISE uses key intel to automatically identify, classify, and profile devices.
Think outside the box
Switching from infrastructure in a box to infrastructure as code (IaC) helps preserve business integrity, while aligning access and policy to your strategy and objectives.
Make a stand
Verify your device posture with ISE 3.x and see how easily it complies with your security policy. ISE works to protect your network, data, and resources from hostile attacks.
Get more for your investment
Cisco Secure Choice Enterprise Agreement
Instant savings
Buy only what you need, with one flexible, easy-to-manage agreement.
Cisco Capital
Flexible payment options
Make the most of your budget, with no upfront costs and payments spread over time.