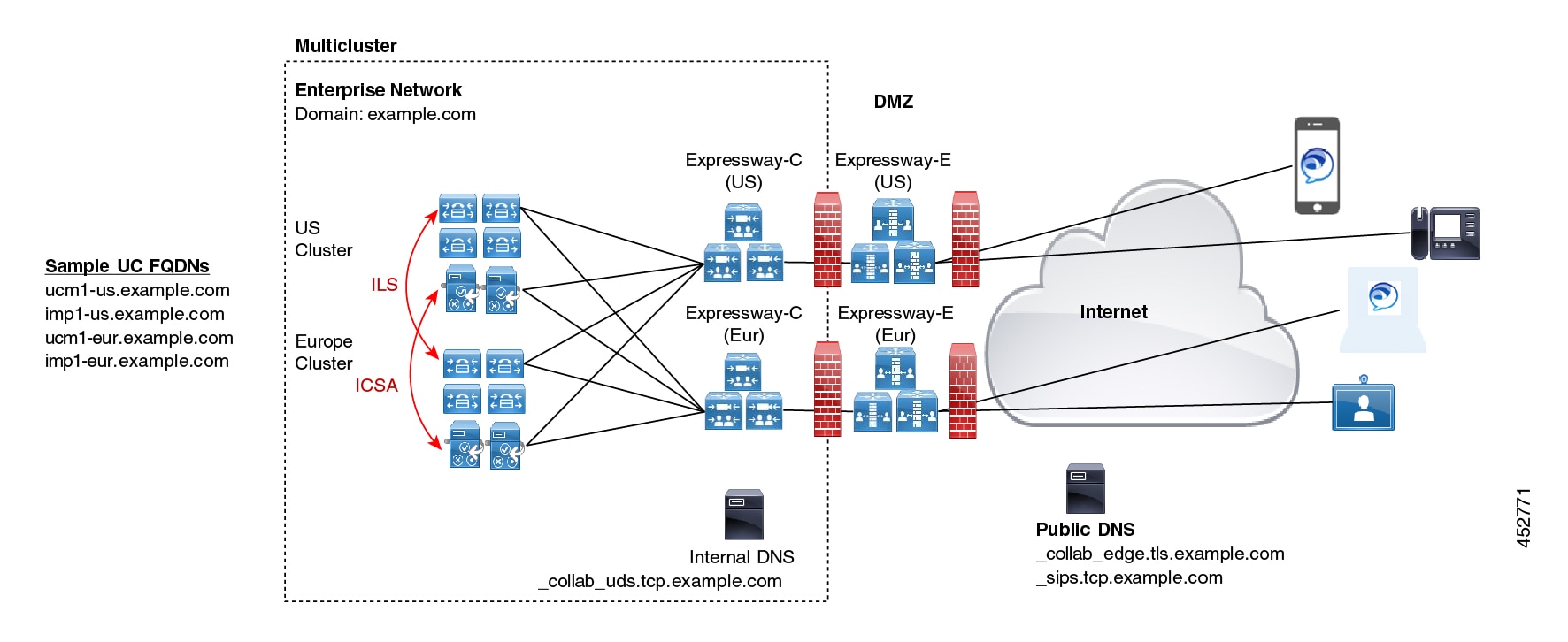
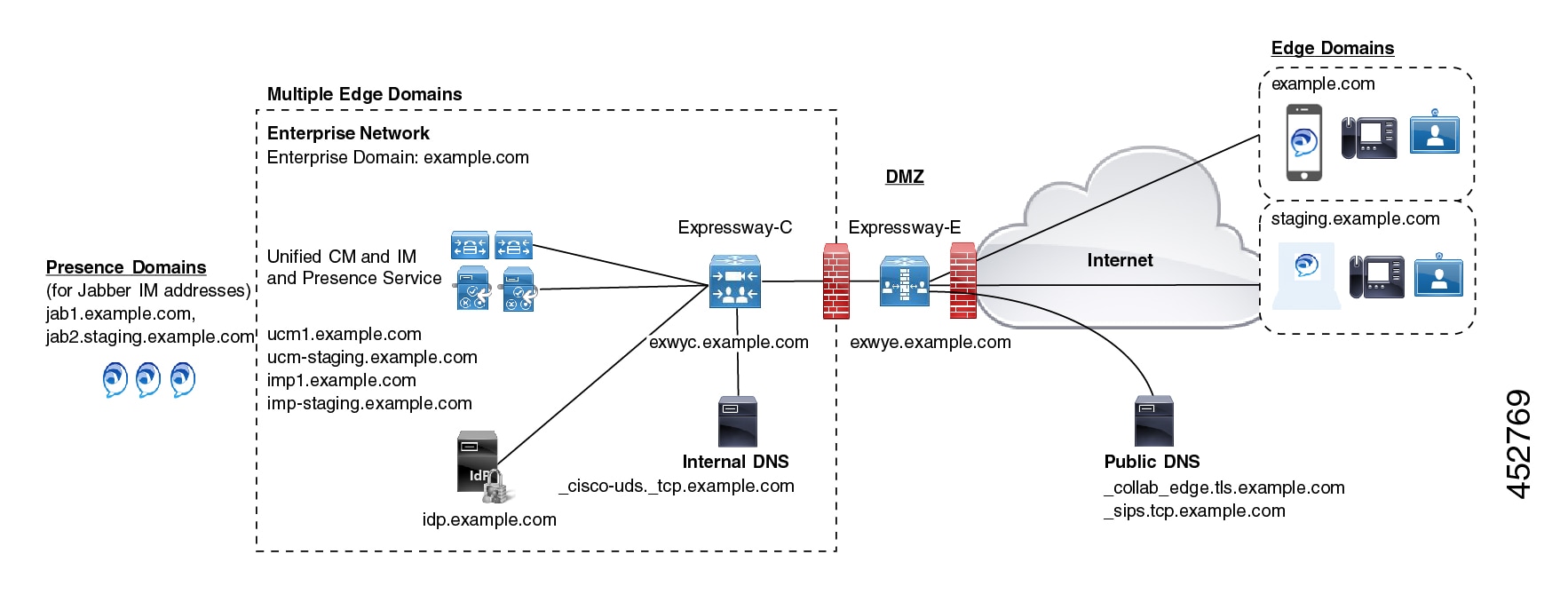
Deployment Partitions
A deployment is an abstract boundary that is used to enclose a domain and one or more Unified Communications service providers (such as Unified CM, Cisco Unity Connection, and IM and Presence Service nodes). The purpose of multiple deployments is to partition the Unified Communications services available to Mobile and Remote Access (MRA) users. So different subsets of MRA users can access different sets of services over the same Expressway pair.
We recommend that you do not exceed ten deployments.
Deployments and their associated domains and services are configured on the Expressway-C.
One primary deployment (called "Default deployment" unless you rename it) automatically encloses all domains and services until you create and populate additional deployments. This primary deployment cannot be deleted, even if it is renamed or has no members.
To partition the services that you provide through Mobile and Remote Access, create as many deployments as you need. Associate a different domain with each one, and then associate the required Unified Communications resources with each deployment.
You cannot associate one domain with more than one deployment. Similarly, each Unified Communications node may only be associated with one deployment.
Example
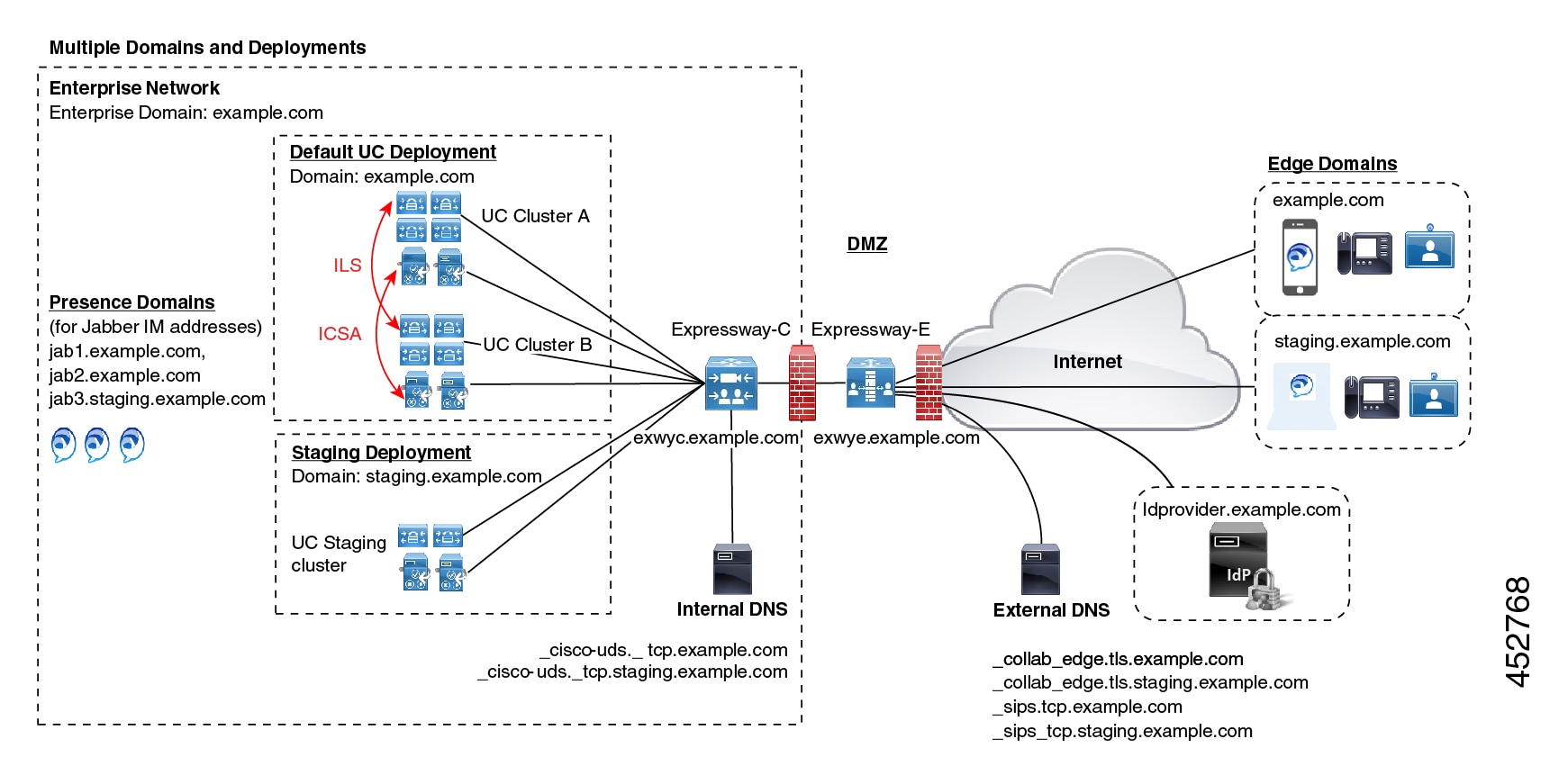
Consider an implementation of two sets of Unified Communications infrastructure to provide a live MRA environment and a staging environment, respectively. This implementation might also require an isolated environment for sensitive communications, as a third set.
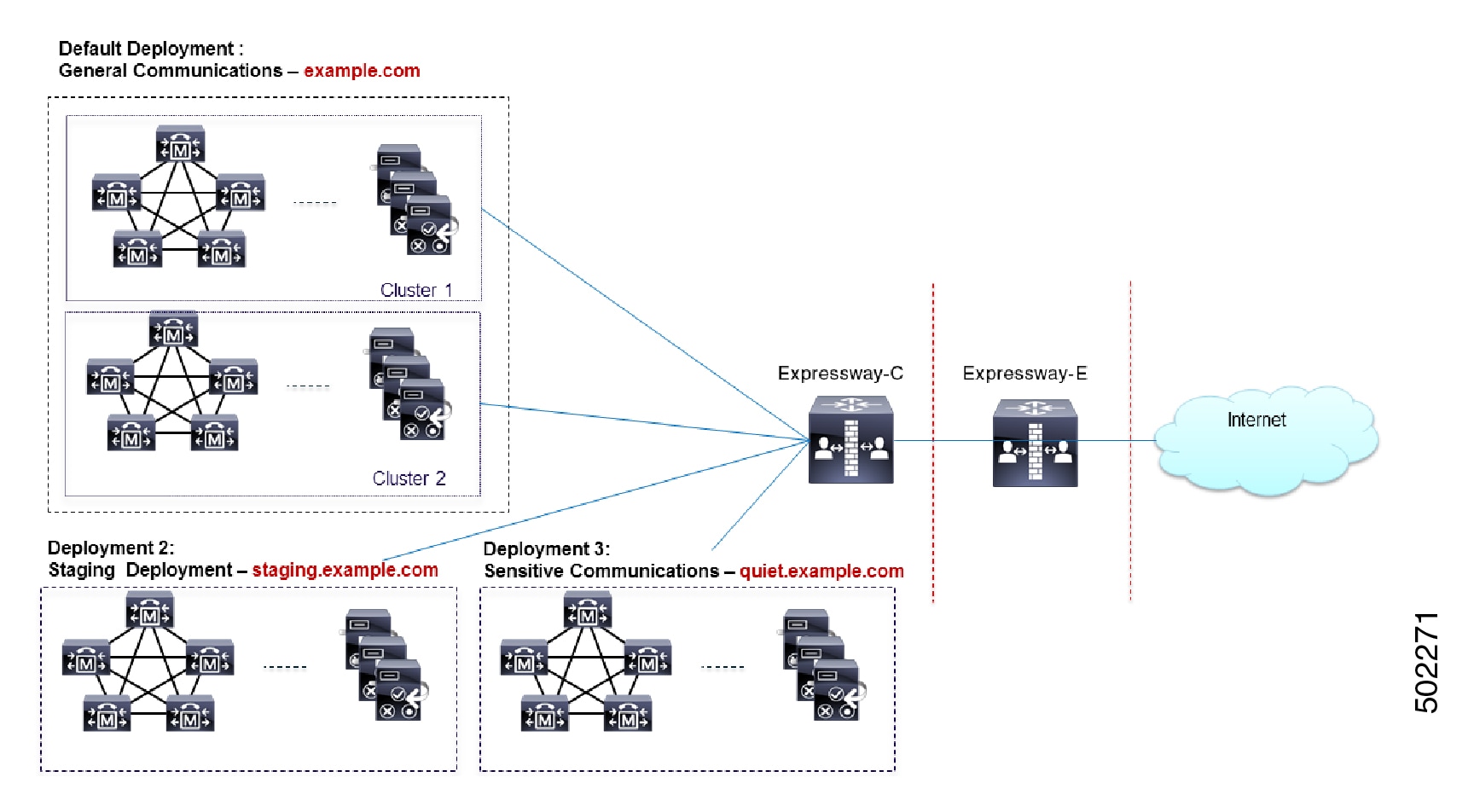
Assign Deployment Partitions for UC Services
 Note |
If you don't create any new deployments, then all internal UC applications belong to a single enterprise-wide Default Deployment. |
Procedure
| Step 1 |
On Expressway-C, create your deployments:
|
| Step 2 |
Assign UC domains to your deployments:
|
| Step 3 |
Assign UC Services to your Deployments:
|
 Feedback
Feedback