- Index
- Preface
- Cisco Analog Telephone Adaptor Overview
- Installing the Cisco ATA
- Configuring the Cisco ATA for MGCP
- Cisco ATA-Supported MGCP Services
- Parameters and Defaults
- Configuring and Debugging Fax Services
- Upgrading the Cisco ATA Signaling Image
- Troubleshooting
- Voice Configuration Menu Codes
- Cisco ATA Specifications
- MGCP Call Flows
- Recommended Cisco ATA Tone Parameter Values by Country
- Glossary
Cisco ATA 186 and Cisco ATA 188 Analog Telephone Adaptor Administrator's Guide for MGCP (version 3.0)
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- November 2, 2007
Chapter: Configuring the Cisco ATA for MGCP
- Default Boot Load Behavior
- Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation
- Steps Needed to Configure the Cisco ATA
- Configuring the Cisco ATA Using a TFTP Server
Configuring the Cisco ATA for MGCP
This section describes how to configure the Cisco ATA to operate with the MGCP signaling image and how the Cisco ATA obtains the latest signaling image.
You can configure the Cisco ATA for use with MGCP with any of the following methods:
•![]() By using a TFTP server—This is the Cisco-recommended method for deploying a large number of Cisco ATAs. This method allows you to set up a unique Cisco ATA configuration file or a configuration file that is common to all Cisco ATAs. The Cisco ATA can automatically download its latest configuration file from the TFTP server when the Cisco ATA powers up, is refreshed or reset, or when the specified TFTP query interval expires.
By using a TFTP server—This is the Cisco-recommended method for deploying a large number of Cisco ATAs. This method allows you to set up a unique Cisco ATA configuration file or a configuration file that is common to all Cisco ATAs. The Cisco ATA can automatically download its latest configuration file from the TFTP server when the Cisco ATA powers up, is refreshed or reset, or when the specified TFTP query interval expires.
•![]() By using manual configuration:
By using manual configuration:
–![]() Voice configuration menu—This is the method you must use if the process of establishing IP connectivity for the Cisco ATA requires changing the default network configuration settings. These settings are CDP, VLAN, and DHCP. You also can use the voice configuration menu to review all IP connectivity settings. The voice configuration menu can also be used when Web access is not available.
Voice configuration menu—This is the method you must use if the process of establishing IP connectivity for the Cisco ATA requires changing the default network configuration settings. These settings are CDP, VLAN, and DHCP. You also can use the voice configuration menu to review all IP connectivity settings. The voice configuration menu can also be used when Web access is not available.
–![]() Web-based configuration—This method is convenient if you plan to deploy a small number of Cisco ATAs in your network. To use this method, the Cisco ATA must first obtain IP connectivity, either through the use of a DHCP server or by using the voice configuration menu to statically configure IP addresses.
Web-based configuration—This method is convenient if you plan to deploy a small number of Cisco ATAs in your network. To use this method, the Cisco ATA must first obtain IP connectivity, either through the use of a DHCP server or by using the voice configuration menu to statically configure IP addresses.
This section contains the following topics:
•![]() Default Boot Load Behavior—This section describes the process that the Cisco ATA follows by default when it boots up. It is very important to understand this process because, if your network environment is not set up to follow this default behavior, you need to make the applicable configuration changes. For example, by default, the Cisco ATA attempts to contact a DHCP server for the necessary IP addresses to achieve network connectivity. However, if your network does not use a DHCP server, you must manually configure various IP settings as described in this section.
Default Boot Load Behavior—This section describes the process that the Cisco ATA follows by default when it boots up. It is very important to understand this process because, if your network environment is not set up to follow this default behavior, you need to make the applicable configuration changes. For example, by default, the Cisco ATA attempts to contact a DHCP server for the necessary IP addresses to achieve network connectivity. However, if your network does not use a DHCP server, you must manually configure various IP settings as described in this section.
•![]() Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation—This section includes a table of the parameters you can configure for VLAN and CDP settings.
Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation—This section includes a table of the parameters you can configure for VLAN and CDP settings.
•![]() Steps Needed to Configure the Cisco ATA—This section provides tables that summarize the general configuration steps you must follow to configure the Cisco ATA.
Steps Needed to Configure the Cisco ATA—This section provides tables that summarize the general configuration steps you must follow to configure the Cisco ATA.
•![]() Configuring the Cisco ATA Using a TFTP Server—This section describes procedures for configuring the Cisco ATA by using a TFTP server, which is the recommended configuration method for the deployment of a large number of Cisco ATAs.
Configuring the Cisco ATA Using a TFTP Server—This section describes procedures for configuring the Cisco ATA by using a TFTP server, which is the recommended configuration method for the deployment of a large number of Cisco ATAs.
•![]() Voice Configuration Menu—This section includes information on how to obtain basic network connectivity for the Cisco ATA and how to perform a factory reset if necessary.
Voice Configuration Menu—This section includes information on how to obtain basic network connectivity for the Cisco ATA and how to perform a factory reset if necessary.
•![]() Cisco ATA Web Configuration Page—This section shows the Cisco ATA Web configuration page and contains a procedure for how to configure Cisco ATA parameters using this interface.
Cisco ATA Web Configuration Page—This section shows the Cisco ATA Web configuration page and contains a procedure for how to configure Cisco ATA parameters using this interface.
•![]() Refreshing or Resetting the Cisco ATA—This section gives the procedure (via the Web configuration page) for refreshing or resetting the Cisco ATA so that your most recent configuration changes take effect immediately.
Refreshing or Resetting the Cisco ATA—This section gives the procedure (via the Web configuration page) for refreshing or resetting the Cisco ATA so that your most recent configuration changes take effect immediately.
•![]() Obtaining Cisco ATA Configuration File After Failed Attempt—This section gives the formula for how soon the Cisco ATA attempts to fetch its configuration file from the TFTP server after a failed attempt.
Obtaining Cisco ATA Configuration File After Failed Attempt—This section gives the formula for how soon the Cisco ATA attempts to fetch its configuration file from the TFTP server after a failed attempt.
•![]() Upgrading the MGCP Signaling Image—This section provides references to the various means of upgrading your Cisco ATA signaling image.
Upgrading the MGCP Signaling Image—This section provides references to the various means of upgrading your Cisco ATA signaling image.

Note ![]() The term Cisco ATA is used throughout this manual to refer to both the Cisco ATA 186 and the Cisco ATA 188, unless differences between the Cisco ATA 186 and Cisco ATA 188 are explicitly stated.
The term Cisco ATA is used throughout this manual to refer to both the Cisco ATA 186 and the Cisco ATA 188, unless differences between the Cisco ATA 186 and Cisco ATA 188 are explicitly stated.
Default Boot Load Behavior
Before configuring the Cisco ATA, you need to know how the default Cisco ATA boot load process works. Once you understand this process, you will be able to configure the Cisco ATA by following the instructions provided in this section and in the sections that follow.
All Cisco ATAs are shipped with a bootload signaling-protocol image. However, because this image is not a fully functional signaling image, the image must be upgraded. The image is designed to be automatically upgraded by a properly configured TFTP server. To configure the Cisco ATA to automatically upgrade to the latest signaling image, see the "Upgrading the Signaling Image from a TFTP Server" section.
In addition, the Cisco ATA obtains its configuration file during the bootload process.
The following list summarizes the default Cisco ATA behavior during its boot-up process:
1. ![]() The Cisco ATA uses the Cisco Discovery Protocol (CDP) to discover which VLAN to enter. If the Cisco ATA receives a VLAN ID response from the network switch, the Cisco ATA enters that VLAN and adds 802.1Q VLAN tags to its IP packets. If the Cisco ATA does not receive a response with a VLAN ID from the network switch, then the Cisco ATA assumes it is not operating in a VLAN environment and does not perform VLAN tagging on its packets.
The Cisco ATA uses the Cisco Discovery Protocol (CDP) to discover which VLAN to enter. If the Cisco ATA receives a VLAN ID response from the network switch, the Cisco ATA enters that VLAN and adds 802.1Q VLAN tags to its IP packets. If the Cisco ATA does not receive a response with a VLAN ID from the network switch, then the Cisco ATA assumes it is not operating in a VLAN environment and does not perform VLAN tagging on its packets.

Note ![]() If your network environment is not set up to handle this default behavior, make the necessary configuration changes by referring to the "Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation" section.
If your network environment is not set up to handle this default behavior, make the necessary configuration changes by referring to the "Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation" section.
2. ![]() The Cisco ATA contacts the DHCP server to request its own IP address.
The Cisco ATA contacts the DHCP server to request its own IP address.

Note ![]() If your network environment does not contain a DHCP server, you need to statically configure various IP addresses so that the Cisco ATA can obtain network connectivity. For a list of parameters that you must configure to obtain network connectivity, see Table 3-6. For instructions on how to use the voice configuration menu, which you must use to perform this configuration, see the "Voice Configuration Menu" section.
If your network environment does not contain a DHCP server, you need to statically configure various IP addresses so that the Cisco ATA can obtain network connectivity. For a list of parameters that you must configure to obtain network connectivity, see Table 3-6. For instructions on how to use the voice configuration menu, which you must use to perform this configuration, see the "Voice Configuration Menu" section.
3. ![]() Also from the DHCP server, the Cisco ATA requests the IP address of the TFTP server.
Also from the DHCP server, the Cisco ATA requests the IP address of the TFTP server.
4. ![]() The Cisco ATA contacts the TFTP server and downloads the Cisco ATA release software that contains the correct signaling image for the Cisco ATA to function properly.
The Cisco ATA contacts the TFTP server and downloads the Cisco ATA release software that contains the correct signaling image for the Cisco ATA to function properly.

Note ![]() If you are not using a TFTP server, you need to manually upgrade the Cisco ATA to the correct signaling image. For information on this procedure, see the "Upgrading the Signaling Image Manually" section.
If you are not using a TFTP server, you need to manually upgrade the Cisco ATA to the correct signaling image. For information on this procedure, see the "Upgrading the Signaling Image Manually" section.
5. ![]() The Cisco ATA looks for a Cisco ATA-specific configuration file (designated by the MAC address of the Cisco ATA and named ata<macaddress> with a possible file extension) on the TFTP server and downloads this file if it exists. For information about configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
The Cisco ATA looks for a Cisco ATA-specific configuration file (designated by the MAC address of the Cisco ATA and named ata<macaddress> with a possible file extension) on the TFTP server and downloads this file if it exists. For information about configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
6. ![]() If the Cisco ATA does not find an ata<macaddress> configuration file, it looks for an atadefault.cfg configuration file and downloads this file if it exists. This file can contain default values for the Cisco ATA to use.
If the Cisco ATA does not find an ata<macaddress> configuration file, it looks for an atadefault.cfg configuration file and downloads this file if it exists. This file can contain default values for the Cisco ATA to use.

Note ![]() When the Cisco ATA is downloading its DHCP configuration, the function button on the top panel blinks.
When the Cisco ATA is downloading its DHCP configuration, the function button on the top panel blinks.
Specifying a Preconfigured VLAN ID or Disabling VLAN IP Encapsulation
If you want the Cisco ATA to use a preconfigured VLAN ID instead of using the Cisco Discovery Protocol to locate a VLAN, or if you want to disable VLAN IP encapsulation, refer to Table 3-1 for a reference to the parameters and bits you may need to configure. Use the voice configuration menu to configure these parameters. (See the "Voice Configuration Menu" section for instructions on using this menu.) Also, refer to Table 3-2 for a matrix that indicates which VLAN-related parameters and bits to configure depending on your network environment.

Note ![]() Bits are numbered from right to left, starting with bit 0.
Bits are numbered from right to left, starting with bit 0.
N/A indicates that the variable is not applicable to the feature and the setting of this varaible does not affect the feature.
Example
The following procedure shows you how to configure the OpFlags and VLANSetting parameters to allow the Cisco ATA to use a user-specified VLAN ID. In this example, the voice VLAN ID is 115 (in decimal format).
Step 1 ![]() Set bits 4-6 of the OpFlags parameter to 1, 0, and 1, respectively. This setting translates to the following bitmap:
Set bits 4-6 of the OpFlags parameter to 1, 0, and 1, respectively. This setting translates to the following bitmap:
xxxx xxxx xxxx xxxx xxxx xxxx x101 xxxx
The remaining bits of the OpFlags parameter, using all default values, make up the following bitmap representation:
0000 0000 0000 0000 0000 0000 0xxx 0010
Therefore, the resulting value of the OpFlags parameter becomes the following bitmap representation:
0000 0000 0000 0000 0000 0000 0101 0010
In hexadecimal format, this value is 0x00000052.
Step 2 ![]() Set bits 18-29 of the VLANSetting parameter to to voice VLAN ID 115. This setting translates to the following bitmap
Set bits 18-29 of the VLANSetting parameter to to voice VLAN ID 115. This setting translates to the following bitmap
xx00 0001 1100 11xx xxxx xxxx xxxx xxxx
where 000001110011 is the binary representation of the demical value 115.
The remaining bits of the VLANSetting parameter, using all default values, make up the following representation:
00xx xxxx xxxx xx00 0000 0000 0010 1011
Therefore, the resulting value of the VLANSetting parameter becomes the following bitmap representation:
0000 0001 1100 1100 0000 0000 0010 1011
In hexadecimal format, this value is 0x01cc002b.

Note ![]() If you are using the voice configuration menu to set the parameters, you must convert hexadecimal values to decimal values. For example, the OpFlags setting of 0x00000052 is equivalent to 82 in decimal format, and the VLANSetting of 0x01cc002b is equivalent to 30146603 in decimal format.
If you are using the voice configuration menu to set the parameters, you must convert hexadecimal values to decimal values. For example, the OpFlags setting of 0x00000052 is equivalent to 82 in decimal format, and the VLANSetting of 0x01cc002b is equivalent to 30146603 in decimal format.
Steps Needed to Configure the Cisco ATA
This section contains the following topics:
•![]() Basic Configuration Steps in a TFTP Server Environment
Basic Configuration Steps in a TFTP Server Environment
•![]() Basic Configuration Steps in a Non-TFTP Server Environment
Basic Configuration Steps in a Non-TFTP Server Environment
Basic Configuration Steps in a TFTP Server Environment
Table 3-3 shows the basic steps for configuring the Cisco ATA and making it operational in a typical MGCP environment, which includes a TFTP server.
|
|
|
|---|---|
1. |
|
2. a. b. Make sure to use an include command in the unique configuration file to pull in values from the common configuration file. c. d. |
|
3. |
|
4. |
|
5. |
|
6. |
Configuring the Cisco ATA to Obtain its Configuration File from the TFTP Server |
7. |
|
8. |
Basic Configuration Steps in a Non-TFTP Server Environment
Table 3-4 shows the basic steps for configuring the Cisco ATA without using the TFTP server method.
|
|
|
|---|---|
1. a. b. c. 
Note |
|
2. |
|
3. |
|
4. |
Configuring the Cisco ATA Using a TFTP Server
The TFTP method of configuration is useful when you have many Cisco ATA because you can use a TFTP server for remote, batch configuration of Cisco ATAs. A TFTP server can host one unique configuration file for each Cisco ATA.
This section contains the following topics:
•![]() Setting Up the TFTP Server with Cisco ATA Software
Setting Up the TFTP Server with Cisco ATA Software
•![]() Configurable Features and Related Parameters
Configurable Features and Related Parameters
•![]() Creating Unique and Common Cisco ATA Configuration Files
Creating Unique and Common Cisco ATA Configuration Files
•![]() atadefault.cfg Configuration File
atadefault.cfg Configuration File
•![]() Configuring the Cisco ATA to Obtain its Configuration File from the TFTP Server
Configuring the Cisco ATA to Obtain its Configuration File from the TFTP Server
Setting Up the TFTP Server with Cisco ATA Software
This section provides the procedure for the Cisco ATA administrator to obtain the correct Cisco ATA software and set up the TFTP server with this software.
Procedure
Step 1 ![]() If you are a registered CCO user. go to the following URL: http://www.cisco.com/cgi-bin/tablebuild.pl/ata186
If you are a registered CCO user. go to the following URL: http://www.cisco.com/cgi-bin/tablebuild.pl/ata186
Step 2 ![]() Download the zip file that contains the software for the applicable release and signaling image you are using. The contents of each file are described next to the file name. Save the zip file onto a floppy disc.
Download the zip file that contains the software for the applicable release and signaling image you are using. The contents of each file are described next to the file name. Save the zip file onto a floppy disc.

Note ![]() The file that contains the protocol signaling image has an extension of .zup.
The file that contains the protocol signaling image has an extension of .zup.
Step 3 ![]() Extract the signaling files onto the TFTP server. This should be the same TFTP server that will contain the binary Cisco ATA configuration file that you create (either ata<macaddress> with a possible file extension or atadefault.cfg). For information about possible configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
Extract the signaling files onto the TFTP server. This should be the same TFTP server that will contain the binary Cisco ATA configuration file that you create (either ata<macaddress> with a possible file extension or atadefault.cfg). For information about possible configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
Configurable Features and Related Parameters
For a list of all required MGCP parameters, see the "Required Parameters" section. These parameters must be properly configured for the Cisco ATA to work.
For descriptions of important Cisco ATA MGCP services that you can configure, and references to their configuration parameters, see the "Important Basic MGCP Services" section and the "Additional MGCP Services" section.
Table 4-1 lists, in alphabetical order, various features that you can configure for the Cisco ATA. Table 4-1 also includes links to the related parameter that allows you to configure each of these features. Each link takes you to a detailed description of the parameter that includes its default values.
For an example of how to configure parameters for the TFTP Server configuration method, see the "Creating Unique and Common Cisco ATA Configuration Files" section.
Creating Unique and Common Cisco ATA Configuration Files
If you have many Cisco ATAs to configure, a good approach is to create two configuration files:
•![]() One file that will contain only parameter values unique to a specific Cisco ATA.
One file that will contain only parameter values unique to a specific Cisco ATA.
•![]() One file for parameters that will be configured with values common to a group of Cisco ATAs. If this file is updated, all Cisco ATA devices in this common group can obtain the new configuration data in a batch-mode environment.
One file for parameters that will be configured with values common to a group of Cisco ATAs. If this file is updated, all Cisco ATA devices in this common group can obtain the new configuration data in a batch-mode environment.
The following procedure demonstrates the steps needed to create these configuration files.

Note ![]() The parameters used in this section help illustrate the process of creating a unique Cisco ATA configuration file, and do not include all required MGCP parameters in the examples. See "Cisco ATA-Supported MGCP Services," for complete listings and descriptions of required parameters and additional configurable features. Also, refer back to Table 3-3 for all main configuration steps.
The parameters used in this section help illustrate the process of creating a unique Cisco ATA configuration file, and do not include all required MGCP parameters in the examples. See "Cisco ATA-Supported MGCP Services," for complete listings and descriptions of required parameters and additional configurable features. Also, refer back to Table 3-3 for all main configuration steps.
Procedure
Step 1 ![]() Use the mgcp_example.txt file as a template for creating a text file of values that are common to one group of Cisco ATAs. The mgcp_example.txt file is included in the software-release zip file and contains all default values. This file is shown without its annotations in the "Configuration Text File Template" section.
Use the mgcp_example.txt file as a template for creating a text file of values that are common to one group of Cisco ATAs. The mgcp_example.txt file is included in the software-release zip file and contains all default values. This file is shown without its annotations in the "Configuration Text File Template" section.
Copy the mgcp_example.txt file and save it with a meaningful name, such as common.txt.
Step 2 ![]() Configure all common parameters by editing the text file as desired. For example, you might configure the following parameters:
Configure all common parameters by editing the text file as desired. For example, you might configure the following parameters:
UseTftp:1
DHCP:1
TFtpURL:10.10.10.1
The settings in this example indicate that a group of Cisco ATAs is using the TFTP server with an IP address of 10.10.10.1 to obtain their configuration files. These Cisco ATAs will use a DHCP server to obtain their own IP addresses but not to obtain the TFTP server IP address (because the TftpURL parameter has a configured value).
Step 3 ![]() Save your changes.
Save your changes.
Step 4 ![]() Use the mgcp_example.txt file again, this time as a template for creating a text file of values that are specific to one Cisco ATA. For example, you might configure the following parameters:
Use the mgcp_example.txt file again, this time as a template for creating a text file of values that are specific to one Cisco ATA. For example, you might configure the following parameters:
UserID:8530709
GkorProxy:192.168.1.1
Save this file of Cisco ATA-specific parameters as:
ata<macaddress>.txt
where macaddress is the non-dotted hexadecimal version of the MAC address of the Cisco ATA you are configuring. This non-dotted hexadecimal MAC address is labeled on the bottom of most Cisco ATAs next to the word "MAC." The file name must be exactly 15 characters long. (However, if this filename is supplied by the DHCP server, the name can be as long as 31 characters and can be any name with printable ASCII characters.)
If necessary, you can obtain the non-dotted hexadecimal MAC address by using the atapname.exe command. For information on using the atapname.exe command, see the "Using atapname.exe Tool to Obtain MAC Address" section. That section includes an example of a dotted decimal MAC address and its corresponding non-dotted hexadecimal address.

Note ![]() The ata<macaddress>.txt file should contain only those parameters whose values are different from the file of common parameters. Parameter values in the ata<macaddress> configuration file will overwrite any manually configured values (values configured through the web or voice configuration menu) when the Cisco ATA powers up or refreshes.
The ata<macaddress>.txt file should contain only those parameters whose values are different from the file of common parameters. Parameter values in the ata<macaddress> configuration file will overwrite any manually configured values (values configured through the web or voice configuration menu) when the Cisco ATA powers up or refreshes.
Step 5 ![]() On the top line of the ata<macaddress>.txt file, add an include command to include the name of the common-parameters file, and save the file.
On the top line of the ata<macaddress>.txt file, add an include command to include the name of the common-parameters file, and save the file.
include:common.txt
UserID:8530709
GkorProxy:192.168.1.1
Step 6 ![]() Run the cfgfmt.exe tool, which is bundled with the Cisco ATA software, on the ata<macaddress>.txt text file to generate the binary configuration file. If you wish to encrypt the binary file, see the "Using Encryption With the cfgfmt Tool" section.
Run the cfgfmt.exe tool, which is bundled with the Cisco ATA software, on the ata<macaddress>.txt text file to generate the binary configuration file. If you wish to encrypt the binary file, see the "Using Encryption With the cfgfmt Tool" section.
The syntax of the cfgfmt program follows:
Syntax
cfgfmt [Encryption options] -mgcp -tptag.dat input-text-file output-binary-file
–![]() Encryption options are described in the "Using Encryption With the cfgfmt Tool" section.
Encryption options are described in the "Using Encryption With the cfgfmt Tool" section.
–![]() mgcp (for MGCP) is the protocol you are using, which you must specify so that the cfgfmt tool will include only the applicable protocol in the converted output binary file.
mgcp (for MGCP) is the protocol you are using, which you must specify so that the cfgfmt tool will include only the applicable protocol in the converted output binary file.
–![]() The ptag.dat file, provided with the Cisco ATA software version you are running, is used by cfgfmt.exe to format a text input representation of the parameter/value pairs to its output binary representation. Be sure this file resides in the same directory from which you are running the cfgfmt program.
The ptag.dat file, provided with the Cisco ATA software version you are running, is used by cfgfmt.exe to format a text input representation of the parameter/value pairs to its output binary representation. Be sure this file resides in the same directory from which you are running the cfgfmt program.
–![]() input-text-file is the input text file representation of the Cisco ATA configuration file.
input-text-file is the input text file representation of the Cisco ATA configuration file.
–![]() output-binary-file is the final output binary file that Cisco ATA uses as the TFTP configuration file.
output-binary-file is the final output binary file that Cisco ATA uses as the TFTP configuration file.
Example
cfgfmt -mgcp -tptag.dat ata0a141e28323c.txt ata0a141e28323c
This example is based on a Cisco ATA MAC address of 10.20.30.40.50.60, which converts to the two-digit, lower-case hexadecimal representation of each integer as 0a141e28323c.
When you convert the ata<macaddress>.txt file to a binary file, the binary file will merge the two text files to form one Cisco ATA-specific binary configuration file for your Cisco ATA.
If the same parameter is configured with different values in these two files, the value in the ata<macaddress>.txt file takes precedence over the value in the common.txt file.
Step 7 ![]() Store all binary configuration file(s) in the TFTP server root directory. For information about possible configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
Store all binary configuration file(s) in the TFTP server root directory. For information about possible configuration file names, see the "Configuration Files that the cfgfmt Tool Creates" section.
When the Cisco ATA powers up, it will retrieve its configuration file(s) from the TFTP server.
Step 8 ![]() If you want to make configuration changes after boot up, repeat the process of creating or editing the text files containing the desired parameters, then converting the ata<macaddress>.txt text file to the binary file(s) and storing the binary file(s) on the TFTP server. For the configuration changes to take effect immediately, refresh the Cisco ATA. (See the "Refreshing or Resetting the Cisco ATA" section.)
If you want to make configuration changes after boot up, repeat the process of creating or editing the text files containing the desired parameters, then converting the ata<macaddress>.txt text file to the binary file(s) and storing the binary file(s) on the TFTP server. For the configuration changes to take effect immediately, refresh the Cisco ATA. (See the "Refreshing or Resetting the Cisco ATA" section.)
After being refreshed, the Cisco ATA will download the updated ata<macaddress> configuration file(s).

Note ![]() If you do not perform a refresh procedure, the Cisco ATA will update its configuration the next time it contacts the TFTP server, which is based on the configured value of the CfgInterval parameter.
If you do not perform a refresh procedure, the Cisco ATA will update its configuration the next time it contacts the TFTP server, which is based on the configured value of the CfgInterval parameter.
Using atapname.exe Tool to Obtain MAC Address
This bundled tool is useful for converting the dotted decimal version of the Cisco ATA MAC address (available on the Cisco ATA Web configuration page or from the voice configuration menu code 24#) to its default Cisco ATA profile name. This name has the following format:
ataxxxxxxxxxxxx
where each xx is the two-digit, lower-case hexadecimal representation of each integer in the dotted, decimal version of the Cisco ATA MAC address. This is the name you use for the unique Cisco ATA binary configuration file.
The following command and output show an example of this command.
Command Example
atapname.exe 10.20.30.40.50.60
Command Output
ata0a141e28323c

Note ![]() The same functionality is available from the voice configuration menu (voice menu code 84#), which will announce the Cisco ATA profile name.
The same functionality is available from the voice configuration menu (voice menu code 84#), which will announce the Cisco ATA profile name.
Using Encryption With the cfgfmt Tool
The EncryptKey or EncryptKeyEx parameter can be used to encrypt binary files that are transferred over TFTP. You can change encryption keys for each Cisco ATA so that only one specific Cisco ATA can decode the information.
Cisco strongly recommends using the EncryptKeyEx parameter for encryption because this parameter provides a stronger encryption than the EncryptKey parameter that was used in Cisco ATA software releases prior to release 2.16.
You must use version 2.3 of the cfgfmt configuration-file generation tool to use the new EncryptKeyEx parameter. This tools comes bundled with Cisco ATA software version 3.0. To verify that you have version 2.3 of the cfgfmt tool type the following command:
cfgfmt
The version number of the cfgfmt tool will be returned.
You can configure the EncryptKeyEx parameter by using the Cisco ATA Web configuration page or by using the TFTP configuration method. (For more information, see the "EncryptKeyEx" section.)
You can configure the EncryptKey parameter by using the Cisco ATA Web configuration page, the voice configuration menu, or by using the TFTP configuration method. (For more information, see the "EncryptKey" section.)
By default, the Cisco ATA-specific ata<macaddress> configuration file(s) are not encrypted. If encryption is required, however, you must manually configure the EncryptKeyEx or EncryptKey parameter before you boot up the Cisco ATA so that the TFTP method is secure. The Cisco ATA uses the RC4 cipher algorithm for encryption.

Note ![]() Because the factory-fresh ATA cannot accept encrypted configuration files, the first unencrypted file, if intercepted, can easily be read. (You would still have to know the data structure format in order to decode the binary information from the unencrypted file.) Therefore, the new encryption key in the unencrypted file can be compromised.
Because the factory-fresh ATA cannot accept encrypted configuration files, the first unencrypted file, if intercepted, can easily be read. (You would still have to know the data structure format in order to decode the binary information from the unencrypted file.) Therefore, the new encryption key in the unencrypted file can be compromised.

Note ![]() For security reasons, Cisco recommends that you set the UIPassword parameter (if desired) in the configuration file and not by using one of the manual configuration methods.
For security reasons, Cisco recommends that you set the UIPassword parameter (if desired) in the configuration file and not by using one of the manual configuration methods.
This section contains the following topics:
•![]() Configuration Files that the cfgfmt Tool Creates
Configuration Files that the cfgfmt Tool Creates
•![]() cfgfmt Tool Syntax and Examples
cfgfmt Tool Syntax and Examples
Configuration Files that the cfgfmt Tool Creates
The number of output binary configuration files that the Cisco ATA produces is dependent on two factors:
•![]() Which encryption key parameter is used—EncryptKey or EncryptKeyEx
Which encryption key parameter is used—EncryptKey or EncryptKeyEx
•![]() The total size of the binary output
The total size of the binary output
Table 3-5 shows the names of the binary files that can be generated. One, two or four files can be generated.

Note ![]() <macaddress> in Table 3-5 is the MAC address of the Cisco ATA.
<macaddress> in Table 3-5 is the MAC address of the Cisco ATA.

Note ![]() If you are creating an atadefault configuration file, the generated binary file name will be atadefault.cfg.x if you encrypt the text file with the EncryptKeyEx parameter; the binary file name will be atadefault.cfg if you do not use the EncryptKeyEx parameter to encrypt the text file. For information on creating an atadefault configuration file, see the "atadefault.cfg Configuration File" section.
If you are creating an atadefault configuration file, the generated binary file name will be atadefault.cfg.x if you encrypt the text file with the EncryptKeyEx parameter; the binary file name will be atadefault.cfg if you do not use the EncryptKeyEx parameter to encrypt the text file. For information on creating an atadefault configuration file, see the "atadefault.cfg Configuration File" section.

Note ![]() Place all generated binary configuration files onto the TFTP server.
Place all generated binary configuration files onto the TFTP server.
cfgfmt Tool Syntax and Examples
The syntax of the cfgfmt tool follows:
Syntax
cfgfmt [options] input output
Syntax Definitions—Options
•![]() -eRc4Passwd—This option directs the Cisco ATA to use Rc4Passwd as the key (up to eight hexadecimal characters) to encrypt or decrypt the input text file. However, if the Cisco ATA EncryptKey parameter in the input text file is not 0, then the value of that parameter is used to encrypt the output binary file, and Rc4Passwd is ignored. The -e portion of this option means that the Cisco ATA will use the weaker encryption method.
-eRc4Passwd—This option directs the Cisco ATA to use Rc4Passwd as the key (up to eight hexadecimal characters) to encrypt or decrypt the input text file. However, if the Cisco ATA EncryptKey parameter in the input text file is not 0, then the value of that parameter is used to encrypt the output binary file, and Rc4Passwd is ignored. The -e portion of this option means that the Cisco ATA will use the weaker encryption method.
•![]() -E—This option directs the Cisco ATA to not use the value of the EncryptKey parameter, as set in the input text file, to encrypt the output binary configuration file.
-E—This option directs the Cisco ATA to not use the value of the EncryptKey parameter, as set in the input text file, to encrypt the output binary configuration file.
•![]() -xRc4Passwd—This option directs the Cisco ATA to use Rc4Passwd, which must be a hexadecimal string of as many as 64 characters, as the key to encrypt or decrypt the input text file. However, if the Cisco ATA EncryptKeyEx parameter in the input text file is not 0, then the value of that parameter is used to encrypt the output binary file, and Rc4Passwd is ignored. The -x portion of this option means that the Cisco ATA will use the stronger encryption method.
-xRc4Passwd—This option directs the Cisco ATA to use Rc4Passwd, which must be a hexadecimal string of as many as 64 characters, as the key to encrypt or decrypt the input text file. However, if the Cisco ATA EncryptKeyEx parameter in the input text file is not 0, then the value of that parameter is used to encrypt the output binary file, and Rc4Passwd is ignored. The -x portion of this option means that the Cisco ATA will use the stronger encryption method.
•![]() -X—This option directs the Cisco ATA to not use the value of the EncryptKeyEx parameter, as set in the input text file, to encrypt the output binary configuration file.
-X—This option directs the Cisco ATA to not use the value of the EncryptKeyEx parameter, as set in the input text file, to encrypt the output binary configuration file.
•![]() -tPtag.dat—This file, provided with the Cisco ATA software version you are running, is used by the cfgfmt tool to format a text input representation of the parameter/value pairs to its output binary representation. Be sure this file resides in the same directory from which you are running the cfgfmt program.
-tPtag.dat—This file, provided with the Cisco ATA software version you are running, is used by the cfgfmt tool to format a text input representation of the parameter/value pairs to its output binary representation. Be sure this file resides in the same directory from which you are running the cfgfmt program.
•![]() -sip—Specify this tag if you are using the SIP protocol so that the cfgfmt tool will include only the SIP protocol parameters in the converted output binary file.
-sip—Specify this tag if you are using the SIP protocol so that the cfgfmt tool will include only the SIP protocol parameters in the converted output binary file.
•![]() -h323—Specify this tag if you are using the H.323 protocol so that the cfgfmt tool will include only the H.323 protocol parameters in the converted output binary file.
-h323—Specify this tag if you are using the H.323 protocol so that the cfgfmt tool will include only the H.323 protocol parameters in the converted output binary file.
•![]() -mgcp—Specify this tag if you are using the MGCP protocol so that the cfgfmt tool will include only the MGCP protocol parameters in the converted output binary file.
-mgcp—Specify this tag if you are using the MGCP protocol so that the cfgfmt tool will include only the MGCP protocol parameters in the converted output binary file.
•![]() -sccp—Specify this tag if you are using the SCCP protocol so that the cfgfmt tool will include only the SCCP protocol parameters in the converted output binary file.
-sccp—Specify this tag if you are using the SCCP protocol so that the cfgfmt tool will include only the SCCP protocol parameters in the converted output binary file.
•![]() -g—This tag omits sensitive parameters in an ata<macaddress> file that was created with a version of the cfgfmt tool prior to version 2.3.
-g—This tag omits sensitive parameters in an ata<macaddress> file that was created with a version of the cfgfmt tool prior to version 2.3.
Some parameters, specified in the ptag.dat file used by the cfgfmt tool, are marked as sensitive information (these parameters could include UIPassword, UID, PWD0). These parameters are not included in the output binary file if the -g switch is specified in the cfgfmt syntax.
Syntax Definitions—Required Parameters
•![]() Input—This is the input text file representation of the Cisco ATA configuration file.
Input—This is the input text file representation of the Cisco ATA configuration file.
•![]() Output—This is the final output binary file that Cisco ATA uses as the TFTP configuration file.
Output—This is the final output binary file that Cisco ATA uses as the TFTP configuration file.
Syntax examples
The cfgfmt.exe syntax affects how the EncryptKeyEx or EncryptKey parameters are used, as shown in the following examples. In these examples, input-text-file is the ata<macaddress>.txt file that you will convert to binary to create the ata<macaddress> configuration file(s) for the Cisco ATA; output-binary-file is that binary ata<macaddress> file, and Secret is the encryption key.
•![]() cfgfmt -mgcp -tptag.dat input-text-file output-binary-file
cfgfmt -mgcp -tptag.dat input-text-file output-binary-file
If input-text-file sets the Cisco ATA EncryptKey parameter to 0, then output-binary-file is not encrypted. If the input-text-file sets EncryptKey to a non-zero value, then output-binary-file is encrypted with that value.
•![]() cfgfmt -X -mgcp -tptag.dat input-text-file output-binary-file
cfgfmt -X -mgcp -tptag.dat input-text-file output-binary-file
This is an example of how you might perform encryption on a first-time Cisco ATA.
The -X (uppercase) option means that any value specified for the Cisco ATA EncryptKeyEx parameter in input-text-file is ignored. However, because Secret is not specified in this example, output-binary-file is not encrypted. Nevertheless, the EncryptKeyEx parameter and its value, if specified in input-file-text, will be included in output-binary-file for possible encryption at a later time. The next time the Cisco ATA fetches the configuration file from the TFTP server, the file will be encrypted with Secret.
•![]() cfgfmt -X -xSecret -mgcp -tptag.dat input-text-file output-binary-file
cfgfmt -X -xSecret -mgcp -tptag.dat input-text-file output-binary-file
This is an example of changing the encryption key from one key to another key.
The -X (uppercase) option means that any value specified for the Cisco ATA EncryptKeyEx parameter in input-text-file is ignored and the output-binary-file is encrypted with the Secret key. However, the EncryptKeyEx parameter and its value, if specified in input-text-file, will be included in output-binary-file.
Examples of Upgrading to Stronger Encryption Key
This section contains two examples of how you would upgrade your Cisco ATA configuration to use the stronger encyrption method if the current Cisco ATA firmware version was a version earlier than version 2.16.2. Versions earlier than 2.16.2 do not support the stronger EncryptKeyEx parameter.
Example 1
In this example, the Cisco ATA has not yet been deployed, but its firmware version is earlier than 2.16.2. Therefore, the Cisco ATA will upgrade to to firmware version 3.0 to use the EncryptKeyEx parameter as its encryption key.
The Cisco ATA in this example has a MAC address of 102030405060.
Perform the following steps:
Procedure
Step 1 ![]() Create a file called ata102030405060.txt by using the applicable example.txt file provided with the Cisco ATA software. (For example, for MGCP, the example.txt file is called mgcp_example.txt.)
Create a file called ata102030405060.txt by using the applicable example.txt file provided with the Cisco ATA software. (For example, for MGCP, the example.txt file is called mgcp_example.txt.)
Step 2 ![]() Modify the ata102030405060.txt file with desired parameter values. The value of the EncryptKey parameter should be 0.
Modify the ata102030405060.txt file with desired parameter values. The value of the EncryptKey parameter should be 0.
Step 3 ![]() Set the value of the EncryptKeyEx parameter to the chosen encryption key with which you want the output binary file to be encrypted. In the EncryptKeyEx parameter specified in the configuration file, you can also restrict the EncryptKeyEx value to apply only to the Cisco ATA with a particular MAC address. For example, if the chosen key value is 231e2a7f10bd7fe, you can specify EncryptKeyEx as:
Set the value of the EncryptKeyEx parameter to the chosen encryption key with which you want the output binary file to be encrypted. In the EncryptKeyEx parameter specified in the configuration file, you can also restrict the EncryptKeyEx value to apply only to the Cisco ATA with a particular MAC address. For example, if the chosen key value is 231e2a7f10bd7fe, you can specify EncryptKeyEx as:
EncryptKeyEx:231e2a7f10bd7fe/102030405060
This means that only the Cisco ATA with the MAC address 102030405060 will be allowed to apply this EncryptKeyEx value to its internal configuration.
Step 4 ![]() Update the upgradecode parameter to instruct the Cisco ATA to upgrade to firmware version 3.0 by means of TFTP configuration. The upgradecode parameter is described in "Upgrading the Cisco ATA Signaling Image."
Update the upgradecode parameter to instruct the Cisco ATA to upgrade to firmware version 3.0 by means of TFTP configuration. The upgradecode parameter is described in "Upgrading the Cisco ATA Signaling Image."
Step 5 ![]() Run the cfgfmt tool as follows:
Run the cfgfmt tool as follows:
cfgfmt -g ata102030405060.txt ata102030405060
This will generate the following two binary configuration files:
•![]() ata102030405060
ata102030405060
•![]() ata102030405060.x
ata102030405060.x
ata102030405060 is unencrypted.
ata102030405060.x is encrypted with EncryptKeyEx value.
Step 6 ![]() Place these two files on the TFTP server that the Cisco ATA will contact for its configuration files.
Place these two files on the TFTP server that the Cisco ATA will contact for its configuration files.
When the Cisco ATA powers up, it will obtain its IP address from the DHCP server. If the DHCP server specifies the TFTP server address, the Cisco ATA will contact the TFTP server obtained from DHCP because the Cisco ATA is not preconfigured with a TFTP server address. The boot process is as follows:
a. ![]() The Cisco ATA downloads the configuration file ata102030405060 from the TFTP server.
The Cisco ATA downloads the configuration file ata102030405060 from the TFTP server.
b. ![]() The Cisco ATA applies parameter values in the file ata102030405060 to its internal configuration while ignoring the EncryptKeyEx parameter (because the older version of the Cisco ATA does not yet recognize the EncryptKeyEx parameter).
The Cisco ATA applies parameter values in the file ata102030405060 to its internal configuration while ignoring the EncryptKeyEx parameter (because the older version of the Cisco ATA does not yet recognize the EncryptKeyEx parameter).
c. ![]() The Cisco ATA upgrades to the 3.0 firmware load.
The Cisco ATA upgrades to the 3.0 firmware load.
d. ![]() The Cisco ATA reboots.
The Cisco ATA reboots.
e. ![]() The Cisco ATA again downloads the configuration file ata102030405060.
The Cisco ATA again downloads the configuration file ata102030405060.
f. ![]() The Cisco ATA applies the value of the EncryptKeyEx parameter to its internal configuration.
The Cisco ATA applies the value of the EncryptKeyEx parameter to its internal configuration.
g. ![]() The Cisco ATA reboots.
The Cisco ATA reboots.
h. ![]() The Cisco ATA EncryptKeyEx value is in effect, so from this point forward the Cisco ATA will download the ata102030405060.x file at each reboot and each time the value configured in the CfgInterval parameter expires.
The Cisco ATA EncryptKeyEx value is in effect, so from this point forward the Cisco ATA will download the ata102030405060.x file at each reboot and each time the value configured in the CfgInterval parameter expires.

Note ![]() Although EncryptKeyEx is encrypted in the ata<macaddress> file, and the ata<macaddress> file does not contain other sensitive information, Cisco recommends that for absolute security you pre-configure the Cisco ATA as described in this example for a private network. Alternatively, you should remove ata<macaddress> once EncryptKeyEx takes effect.
Although EncryptKeyEx is encrypted in the ata<macaddress> file, and the ata<macaddress> file does not contain other sensitive information, Cisco recommends that for absolute security you pre-configure the Cisco ATA as described in this example for a private network. Alternatively, you should remove ata<macaddress> once EncryptKeyEx takes effect.
Example 2
In this example, a new Cisco ATA has already b een deployed (with the EncryptKey value set) with a firmware version earlier than 2.16.2. The Cisco ATA needs to be upgraded to version 2.16.2 firmware or greater to use EncryptKeyEx parameter to encrypt its configuration file.
In this scenario, you would follow the same procedure as in Example 1, except that you would need to set the EncryptKey value to the previously configured EncryptKey value. The difference is that the ata<macaddress> file is now encrypted with EncryptKey because the Cisco ATA expects the ata<macaddress> file to be encrypted with EncryptKey.The Cisco ATA can then begin using the ata<macaddress>.x file that is encrypted with the EncryptKeyEx parameter.
atadefault.cfg Configuration File
You can create a configuration file, called atadefault.cfg, that is common to all Cisco ATAs. This configuration file is applied to a Cisco ATA only if a unique configuration file (such as ata<macaddress>) does not exist for the Cisco ATA on the TFTP server during the Cisco ATA power-up procedure.
You can use the atadefault.cfg file to provide limited functionality for when you first install the Cisco ATA. For example, if your service provider provides the ethernet connection and VoIP telephony service, you may need to call customer service to activate the service. If the atadefault.cfg file is configured to provide a direct connection to the customer service center, you can simply pick up the telephone and wait to be connected without using your regular phone.
The following procedure illustrates how to create the Cisco ATA default configuration file, convert it to the required binary format that the Cisco ATA can read, and store it on the TFTP server so that the Cisco ATA will download it during the boot-up process:
Procedure
Step 1 ![]() Make a copy of the mgcp_example.txt file and rename it atadefault.txt.
Make a copy of the mgcp_example.txt file and rename it atadefault.txt.
Step 2 ![]() Make the desired configuration changes by editing the atadefault.txt file, then save the file.
Make the desired configuration changes by editing the atadefault.txt file, then save the file.
Step 3 ![]() Convert the atadefault.txt file to a binary file by running the cfgfmt.exe tool, which is bundled with the Cisco ATA software.
Convert the atadefault.txt file to a binary file by running the cfgfmt.exe tool, which is bundled with the Cisco ATA software.

Note ![]() If you wish to encrypt the binary file for security reasons, see the "Using Encryption With the cfgfmt Tool" section. If you encrypt the file using the EncryptKeyEx parameter, the resulting binary file will be called atadefault.cfg.x; if not encrypted with the EncryptKeyEx parameter the resulting binary file name will be atadefault.cfg.
If you wish to encrypt the binary file for security reasons, see the "Using Encryption With the cfgfmt Tool" section. If you encrypt the file using the EncryptKeyEx parameter, the resulting binary file will be called atadefault.cfg.x; if not encrypted with the EncryptKeyEx parameter the resulting binary file name will be atadefault.cfg.
Step 4 ![]() Store the binary atadefault.cfg (or atadefault.cfg.x) configuration file in the TFTP server root directory.
Store the binary atadefault.cfg (or atadefault.cfg.x) configuration file in the TFTP server root directory.
During the boot-up process, the Cisco ATA will download this file as its configuration file unless it first finds a Cisco ATA-specific configuration file named for the MAC address of the Cisco ATA.
Configuring the Cisco ATA to Obtain its Configuration File from the TFTP Server
This section describes three methods for how the Cisco ATA contacts the TFTP server to obtain its configuration file:
–![]() The Cisco ATA contacts the DHCP server, which provides the IP address of the TFTP server
The Cisco ATA contacts the DHCP server, which provides the IP address of the TFTP server
–![]() The Cisco ATA uses the DHCP server but the DHCP server does not know about the TFTP server
The Cisco ATA uses the DHCP server but the DHCP server does not know about the TFTP server
Using a DHCP Server
When using a DHCP server, configuration settings vary depending on whether or not the DHCP server is under the control of the Cisco ATA system administrator or the service provider. The simplest configuration is when the DHCP server is under the control of the Cisco ATA administrator, in which case the DHCP server provides the IP address of the TFTP server. Depending on who controls the DHCP server, follow the applicable configuration procedure:
•![]() Procedure if DHCP Server is Under Control of Cisco ATA Administrator
Procedure if DHCP Server is Under Control of Cisco ATA Administrator
•![]() Procedure if DHCP Server is not Under Control of Cisco ATA Administrator
Procedure if DHCP Server is not Under Control of Cisco ATA Administrator
This section also includes the topic:
•![]() Other DHCP Options You Can Set
Other DHCP Options You Can Set

Note ![]() If no DHCP server is found and the Cisco ATA is programmed to find one, the function button continues to blink.
If no DHCP server is found and the Cisco ATA is programmed to find one, the function button continues to blink.
Procedure if DHCP Server is Under Control of Cisco ATA Administrator
Procedure
Step 1 ![]() On the DHCP server, set one of the following two options:
On the DHCP server, set one of the following two options:
•![]() DHCP option 150 (TFTP server IP address)
DHCP option 150 (TFTP server IP address)
•![]() Standard DHCP option 66 (TFTP server name)
Standard DHCP option 66 (TFTP server name)
If you use DHCP option 150, the Cisco ATA will ignore DHCP option 66. However, if you use DHCP option 66, you must turn off DHCP option 150 or set its value to 0.

Note ![]() You can turn off the DHCP option 150 request by using the Cisco ATA OpFlags parameter (see the "OpFlags" section).
You can turn off the DHCP option 150 request by using the Cisco ATA OpFlags parameter (see the "OpFlags" section).
Step 2 ![]() Make sure to use default values for the following Cisco ATA parameters:
Make sure to use default values for the following Cisco ATA parameters:
•![]() TftpURL=0
TftpURL=0
•![]() UseTftp=1
UseTftp=1
•![]() DHCP=1
DHCP=1
This completes the parameter settings and DHCP options you need to configure for this procedure. The Cisco ATA will contact the DHCP server for the IP address of the TFTP server that contains the Cisco ATA configuration file.
Procedure if DHCP Server is not Under Control of Cisco ATA Administrator
This is the procedure to use if the DHCP server is not under the control of the Cisco ATA administrator, which means that the URL of the TFTP server must be manually configured.
Procedure
Step 1 ![]() Using the voice configuration menu, set the parameter TftpURL to the IP address or URL of the TFTP server. For more information on setting the TftpURL parameter, see the "TftpURL" section. For information about using the Cisco ATA voice configuration menu, see the "Voice Configuration Menu" section.
Using the voice configuration menu, set the parameter TftpURL to the IP address or URL of the TFTP server. For more information on setting the TftpURL parameter, see the "TftpURL" section. For information about using the Cisco ATA voice configuration menu, see the "Voice Configuration Menu" section.

Note ![]() If you are not using a DHCP server to provide the TFTP server location, you must manually configure the TftfURL. You can do this by using the voice configuration menu without first obtaining network connectivity for the Cisco ATA. If you want to configure this value using the Web configuration page, you first must obtain network connectivity by using the voice configuration menu to statically configure IP address information (see the "Voice Configuration Menu" section).
If you are not using a DHCP server to provide the TFTP server location, you must manually configure the TftfURL. You can do this by using the voice configuration menu without first obtaining network connectivity for the Cisco ATA. If you want to configure this value using the Web configuration page, you first must obtain network connectivity by using the voice configuration menu to statically configure IP address information (see the "Voice Configuration Menu" section).
Step 2 ![]() Use the default value of 1 for the Cisco ATA parameter DHCP.
Use the default value of 1 for the Cisco ATA parameter DHCP.
Step 3 ![]() Use the default value of 1 for the Cisco ATA parameter UseTftp.
Use the default value of 1 for the Cisco ATA parameter UseTftp.
This completes the parameter settings you need to configure for this procedure. The Cisco ATA will contact the manually configured TFTP server that contains the Cisco ATA configuration file.
Other DHCP Options You Can Set
The following parameters can also be configured with DHCP:
•![]() Boot file name of DHCP header—The ata<macaddress> binary Cisco ATA configuration file, which can have a maximum of 31 characters and can be any name with printable ASCII characters
Boot file name of DHCP header—The ata<macaddress> binary Cisco ATA configuration file, which can have a maximum of 31 characters and can be any name with printable ASCII characters
•![]() Client PC address
Client PC address
•![]() DHCP option 1—Client Subnet Mask
DHCP option 1—Client Subnet Mask
•![]() DHCP option 3—Routers on the client's subnet
DHCP option 3—Routers on the client's subnet
•![]() DHCP option 6—One or two Domain Name servers
DHCP option 6—One or two Domain Name servers
•![]() DHCP option 42—One or two Network Time Protocol servers
DHCP option 42—One or two Network Time Protocol servers

Note ![]() DHCP options 43 and 60 are set by the Cisco ATA. Option 43 specifies the protocol and option 60 identifies the vendor class of the Cisco ATA box.
DHCP options 43 and 60 are set by the Cisco ATA. Option 43 specifies the protocol and option 60 identifies the vendor class of the Cisco ATA box.
Without Using a DHCP Server
Use the following procedure if you are not using a DHCP server in your environment but are still using a TFTP server to obtain the Cisco ATA configuration file:
Procedure
Step 1 ![]() Set the DHCP parameter to 0.
Set the DHCP parameter to 0.
Step 2 ![]() Set the UseTFTP parameter to 1.
Set the UseTFTP parameter to 1.
Step 3 ![]() Set the Cisco ATA parameter TftpURL to the IP address or URL of the TFTP server. For more information on setting the TftpURL parameter, see the "TftpURL" section.
Set the Cisco ATA parameter TftpURL to the IP address or URL of the TFTP server. For more information on setting the TftpURL parameter, see the "TftpURL" section.

Note ![]() If you are not using a DHCP server to provide the TFTP server location, you must manually enter the TftpUrl using either the voice configuration menu or the Web configuration page.
If you are not using a DHCP server to provide the TFTP server location, you must manually enter the TftpUrl using either the voice configuration menu or the Web configuration page.
Step 4 ![]() If you have done already done so, statically configure the following parameters using the voice configuration menu (see the "Voice Configuration Menu" section). These are the parameters you need to configure for the Cisco ATA to obtain network connectivity:
If you have done already done so, statically configure the following parameters using the voice configuration menu (see the "Voice Configuration Menu" section). These are the parameters you need to configure for the Cisco ATA to obtain network connectivity:
•![]() StaticIP
StaticIP
•![]() StaticRoute
StaticRoute
•![]() StaticNetMask
StaticNetMask
Other parameters that are normally supplied by DHCP may be provided statically by configuring their values. These parameters are:
•![]() DNS1IP
DNS1IP
•![]() DNS2IP
DNS2IP
•![]() NTPIP
NTPIP
•![]() AltNTPIP
AltNTPIP
•![]() Domain
Domain
This completes the parameter settings you need to configure in order for the Cisco ATA to contact the TFTP server (without using DHCP) that will contain the configuration file for the Cisco ATA.
Voice Configuration Menu
The main reasons to use the voice configuration menu are to establish IP connectivity for the Cisco ATA if a DHCP server is not being used in your network environment, and to reset the Cisco ATA to its factory values if necessary. You can also use the voice configuration menu if you need to configure a small number of parameters or if the web interface and TFTP configuration are not available.

Note ![]() Do not use the voice configuration menu to attempt to change any values that you configured by means of the TFTP configuration file method. Whenever the Cisco ATA refreshes, it downloads its ata<macaddress> configuration file or atadefault.cfg default configuration file from the TFTP server, and the values in either of these files will overwrite the values of any corresponding parameters configured with the voice configuration menu.
Do not use the voice configuration menu to attempt to change any values that you configured by means of the TFTP configuration file method. Whenever the Cisco ATA refreshes, it downloads its ata<macaddress> configuration file or atadefault.cfg default configuration file from the TFTP server, and the values in either of these files will overwrite the values of any corresponding parameters configured with the voice configuration menu.
See "Parameters and Defaults," for a complete list of parameters and their definitions. Also see Table 4-1 for an alphabetical listing of configurable features and references to their corresponding parameters.
This section contains the following topics:
•![]() Using the Voice Configuration Menu
Using the Voice Configuration Menu
•![]() Resetting the Cisco ATA to Factory Default Values
Resetting the Cisco ATA to Factory Default Values
Using the Voice Configuration Menu
To manually configure the Cisco ATA by using the voice configuration menu and the telephone keypad, perform the following steps:
Procedure
Step 1 ![]() Connect an analog touch-tone phone to the port labeled Phone 1 on the back of the Cisco ATA.
Connect an analog touch-tone phone to the port labeled Phone 1 on the back of the Cisco ATA.
Step 2 ![]() Lift the handset and press the function button located on the top of the Cisco ATA. You should receive the initial voice configuration menu voice prompt.
Lift the handset and press the function button located on the top of the Cisco ATA. You should receive the initial voice configuration menu voice prompt.
Step 3 ![]() Using the telephone keypad, enter the voice menu code for the parameter that you want to configure or the command that you want to execute, then press #. For a list of voice menu codes, see "Voice Configuration Menu Codes."
Using the telephone keypad, enter the voice menu code for the parameter that you want to configure or the command that you want to execute, then press #. For a list of voice menu codes, see "Voice Configuration Menu Codes."
Table 3-6 lists the menu options that you need to configure basic IP connectivity for the Cisco ATA, after which you can use the Cisco ATA web configuration page to configure additional parameters.

Note ![]() If you are using the voice configuration menu to statically configure the Cisco ATA IP address, you must disable DHCP by setting its value to 0.
If you are using the voice configuration menu to statically configure the Cisco ATA IP address, you must disable DHCP by setting its value to 0.
Step 4 ![]() Follow the voice prompts and enter the appropriate values, then press the # key.
Follow the voice prompts and enter the appropriate values, then press the # key.

Note ![]() Use the * key to indicate a delimiter (dot). For example, to enter an IP address of 192.168.3.1, you would enter 192*168*3*1 on your telephone keypad.
Use the * key to indicate a delimiter (dot). For example, to enter an IP address of 192.168.3.1, you would enter 192*168*3*1 on your telephone keypad.

Note ![]() When entering values for a field that contains a hexadecimal value, you must convert the hexadecimal value to a decimal value in order to enter it into the voice configuration menu system. For example, to enter the hexadecimal value 0x6A, you would enter the number 106 on the telephone keypad.
When entering values for a field that contains a hexadecimal value, you must convert the hexadecimal value to a decimal value in order to enter it into the voice configuration menu system. For example, to enter the hexadecimal value 0x6A, you would enter the number 106 on the telephone keypad.
The voice configuration menu repeats the value you entered, then prompts you to press one of the following keys:
•![]() 1=Change your entered value
1=Change your entered value
•![]() 2=Review your entered value
2=Review your entered value
•![]() 3=Save your entered value
3=Save your entered value
•![]() 4=Review the current saved value
4=Review the current saved value
Step 5 ![]() Cisco strongly recommends that you set a password. Use the voice menu code 7387277 (SETPASS) to configure a password through the voice configuration menu, after which you are prompted for the password whenever you attempt to change a parameter value.
Cisco strongly recommends that you set a password. Use the voice menu code 7387277 (SETPASS) to configure a password through the voice configuration menu, after which you are prompted for the password whenever you attempt to change a parameter value.
Step 6 ![]() After completing the configuration through the voice configuration menu, press the # key to exit.
After completing the configuration through the voice configuration menu, press the # key to exit.
Step 7 ![]() Hang up the telephone. The Cisco ATA configuration refreshes. The function button fast-blinks when the refresh completes.
Hang up the telephone. The Cisco ATA configuration refreshes. The function button fast-blinks when the refresh completes.
Entering Alphanumeric Values
Some voice configuration menu options require you to enter alphanumeric characters. Alphanumeric entry differs from numeric entry because you must press # after each character selected.
If you need to enter an alphanumeric value, the voice prompt tells you to enter an alphanumeric value; otherwise, enter a numeric value (0 to 9).
Table 3-7 lists the keys on a telephone keypad and their respective alphanumeric characters.
Using Table 3-7 as a guide, enter the appropriate number key on the telephone keypad as many times as needed to select the number, letter, or symbol required. For example, to enter 58sQ, you would enter:
5 # 8 # 7 7 7 7 7 # 7 7 7 7 7 7 7 # #
Resetting the Cisco ATA to Factory Default Values
It is possible that you may, under some circumstances, want to reset the Cisco ATA to its factory default values. For example, this is the only way to recover a forgotten password without contacting your Cisco representative.
To perform a factory reset, you must use the voice configuration menu and follow these steps:
Procedure
Step 1 ![]() Press the function button on the Cisco ATA.
Press the function button on the Cisco ATA.
Step 2 ![]() Press the digits 322873738 (FACTRESET) then press # on your telephone keypad.
Press the digits 322873738 (FACTRESET) then press # on your telephone keypad.
Step 3 ![]() Press * on your telephone keypad to confirm that you want to reset the Cisco ATA, then hang up the phone.
Press * on your telephone keypad to confirm that you want to reset the Cisco ATA, then hang up the phone.
Cisco ATA Web Configuration Page
You can use the Cisco ATA web configuration page in a non-TFTP configuration environment, or in a TFTP configuration environment as a read-only record of individual customer parameters.
You can display the most recent Cisco ATA configuration file from the TFTP server by opening your web browser and typing the following:
http://<ipaddress>/refresh
where ipaddress is the IP address of the Cisco ATA.
Figure 3-1 shows and example of the Cisco ATA web configuration page, which displays all configurable parameters.

Note ![]() Do not use the web configuration page to attempt to change any values that you configured by means of the TFTP configuration file method. Whenever the Cisco ATA refreshes, it downloads its ata<macaddress> configuration file(s) or atadefault.cfg default configuration file from the TFTP server, and the values in either of these files will overwrite the values of any corresponding parameters configured with the web configuration method.
Do not use the web configuration page to attempt to change any values that you configured by means of the TFTP configuration file method. Whenever the Cisco ATA refreshes, it downloads its ata<macaddress> configuration file(s) or atadefault.cfg default configuration file from the TFTP server, and the values in either of these files will overwrite the values of any corresponding parameters configured with the web configuration method.
Figure 3-1 Cisco ATA Web Configuration Page
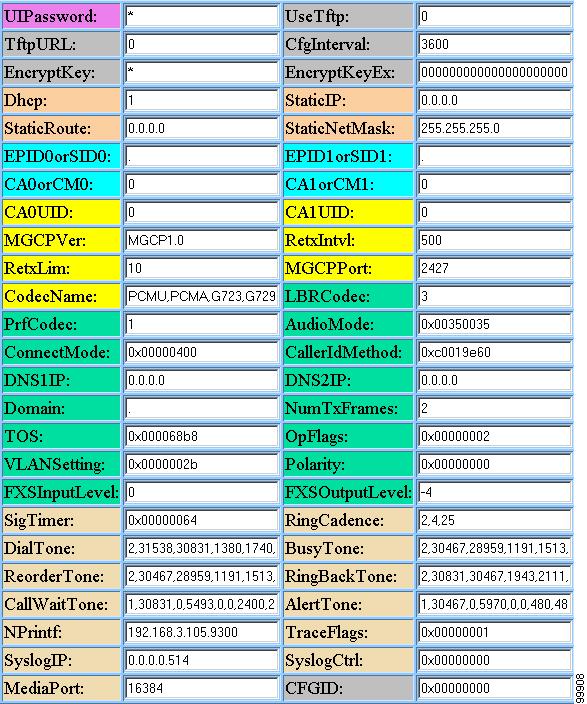
You can access the web configuration page from any graphics-capable browser, such as Microsoft Internet Explorer or Netscape. This provides easy initial access to the Cisco ATA configuration within the administrator's private network.
Follow these steps to set parameters using the web configuration page:
Procedure
Step 1 ![]() Make sure that your PC and the Cisco ATA are already networked and visible to each another.
Make sure that your PC and the Cisco ATA are already networked and visible to each another.
Step 2 ![]() Open your web browser.
Open your web browser.
Step 3 ![]() Enter the URL for your configuration page. The default URL for the web server is:
Enter the URL for your configuration page. The default URL for the web server is:
http://IP Address/dev
For example, the configuration page for a Cisco ATA with the IP address 192.168.3.225 is:
http://192.168.3.225/dev
Step 4 ![]() Select the values for the items that you want to configure. See "Parameters and Defaults," for a complete list of parameters and their definitions. Also see Table 4-1 for an alphabetical listing of configurable features and references to their corresponding parameters.
Select the values for the items that you want to configure. See "Parameters and Defaults," for a complete list of parameters and their definitions. Also see Table 4-1 for an alphabetical listing of configurable features and references to their corresponding parameters.

Note ![]() Cisco strongly recommends that you set a password. Use the UIPassword parameter to configure a password, after which you are prompted for the password whenever you attempt to change a parameter value. Configuration parameters cannot be accessed through the voice configuration menu if the password contains one or more letters and can be changed only by using the web interface or the TFTP configuration method.
Cisco strongly recommends that you set a password. Use the UIPassword parameter to configure a password, after which you are prompted for the password whenever you attempt to change a parameter value. Configuration parameters cannot be accessed through the voice configuration menu if the password contains one or more letters and can be changed only by using the web interface or the TFTP configuration method.
Step 5 ![]() Click apply to save your changes.
Click apply to save your changes.
The Cisco ATA automatically refreshes its configuration.
Step 6 ![]() Close your web browser.
Close your web browser.
Refreshing or Resetting the Cisco ATA
Whenever you make configuration changes to your Cisco ATA configuration file, you can refresh or reset the Cisco ATA for these configuration changes to immediately take effect. If you do not refresh or reset the Cisco ATA, the configuration changes will take effect the next time the Cisco ATA contacts the TFTP server, which occurs based on the configured value of the CfgInterval parameter.

Note ![]() A refresh procedure will update the Cisco ATA configuration file. A reset procedure will also update the Cisco ATA configuration file, and will additionally power-down and power-up the Cisco ATA. A reset should not be necessary if your only goal is to update the configuration file.
A refresh procedure will update the Cisco ATA configuration file. A reset procedure will also update the Cisco ATA configuration file, and will additionally power-down and power-up the Cisco ATA. A reset should not be necessary if your only goal is to update the configuration file.
Procedure to Refresh the Cisco ATA
To refresh the Cisco ATA, enter the following command from your web browser:
http://<ipaddress>/refresh
where ipaddress is the IP address of the Cisco ATA that you are refreshing.
Procedure to Reset the Cisco ATA
To reset the Cisco ATA, enter the following command from your web browser:
http://<ipaddress>/reset
where ipaddress is the IP address of the Cisco ATA that you are resetting.
Obtaining Cisco ATA Configuration File After Failed Attempt
The Cisco ATA uses the following formula for determining how soon to contact the TFTP server for the Cisco ATA configuration file after a failed attempt at getting the file. The result of the formula is called the random back-off amount.
random back-off amount = CfgInterval + random(min(1800, CfgInterval))
where
•![]() CfgInterval is the value of the CfgInterval configuration parameter (in seconds). For more information about this parameter, see the "CfgInterval" section.
CfgInterval is the value of the CfgInterval configuration parameter (in seconds). For more information about this parameter, see the "CfgInterval" section.
•![]() random(x) function yields a value between 0 and x-1.
random(x) function yields a value between 0 and x-1.
•![]() min(x,y) function yields the smaller value of x and y.
min(x,y) function yields the smaller value of x and y.
Upgrading the MGCP Signaling Image
For instructions on how to upgrade the Cisco ATA to the most recent MGCP signaling image, refer to the following list:
•![]() To use the recommended TFTP method of upgrading the Cisco ATA, see the "Upgrading the Signaling Image from a TFTP Server" section.
To use the recommended TFTP method of upgrading the Cisco ATA, see the "Upgrading the Signaling Image from a TFTP Server" section.
•![]() In the rare instance that you are not using the TFTP server to configure the Cisco ATA and to obtain software upgrades, you must manually upgrade to the latest signaling image immediately after the Cisco ATA boots up. In this case, see the "Upgrading the Signaling Image Manually" section.
In the rare instance that you are not using the TFTP server to configure the Cisco ATA and to obtain software upgrades, you must manually upgrade to the latest signaling image immediately after the Cisco ATA boots up. In this case, see the "Upgrading the Signaling Image Manually" section.
 Feedback
Feedback