- Index
- Preface
- Overview
- Using the Command-Line Interface
- Assigning the Switch IP Address and Default Gateway
- Configuring Cisco IOS Configuration Engine
- Administering the Switch
- Configuring Web-Based Authentication
- Configuring Cisco TrustSec
- Clustering Switches
- Managing Switch Stacks
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring IEEE 802.1x Port-Based Authentication
- Configuring Interface Characteristics
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring Flex Links and the MAC Address-Table Move Update Feature
- Configuring DHCP Features and IP Source Guard
- Configuring Dynamic ARP Inspection
- Configuring IGMP Snooping and MVR
- Configuring Port-Based Traffic Control
- Configuring UDLD
- Configuring CDP
- Configuring LLDP, LLDP-MED, and Wired Location Service
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging and Smart Logging
- Configuring SNMP
- Configuring Cisco IOS IP SLAs Operations
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring Static IP Routing
- Configuring IPv6 Routing
- Configuring IPv6 MLD Snooping
- Configuring IPv6 ACLs
- Configuring EtherChannels and Link-State Tracking
- Troubleshooting
- Configuring Online Diagnostics
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 15.0(2)SE
Catalyst 2960 and 2960-S Switches Software Configuration Guide, Cisco IOS Release 15.2(1)E
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
- Updated:
- August 27, 2008
Chapter: Configuring Cisco IOS Configuration Engine
Configuring Cisco IOS Configuration Engine
This chapter describes how to configure the feature on the Catalyst switch.

Note![]() For complete configuration information for the Cisco Configuration Engine, go to
For complete configuration information for the Cisco Configuration Engine, go to
http://www.cisco.com/en/US/products/sw/netmgtsw/ps4617/tsd_products_support_series_home.html
For complete syntax and usage information for the commands used in this chapter, go to the Cisco IOS Network Management Command Reference, Release 12.4:
http://www.cisco.com/en/US/docs/ios/netmgmt/command/reference/nm_book.html
Understanding Cisco Configuration Engine Software
The Cisco Configuration Engine is network management software that acts as a configuration service for automating the deployment and management of network devices and services (see Figure 4-1). Each Configuration Engine manages a group of Cisco devices (switches and routers) and the services that they deliver, storing their configurations and delivering them as needed. The Configuration Engine automates initial configurations and configuration updates by generating device-specific configuration changes, sending them to the device, executing the configuration change, and logging the results.
The Configuration Engine supports standalone and server modes and has these CNS components:
- Configuration service (web server, file manager, and namespace mapping server)
- Event service (event gateway)
- Data service directory (data models and schema)
In standalone mode, the Configuration Engine supports an embedded Directory Service. In this mode, no external directory or other data store is required. In server mode, the Configuration Engine supports the use of a user-defined external directory.
Figure 4-1 Configuration Engine Architectural Overview
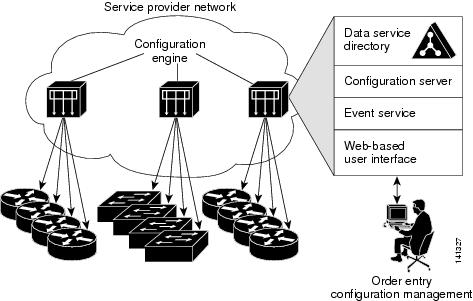
Configuration Service
The Configuration Service is the core component of the Cisco Configuration Engine. It consists of a configuration server that works with Cisco IOS CNS agents on the switch. The Configuration Service delivers device and service configurations to the switch for initial configuration and mass reconfiguration by logical groups. Switches receive their initial configuration from the Configuration Service when they start up on the network for the first time.
The Configuration Service uses the CNS Event Service to send and receive configuration change events and to send success and failure notifications.
The configuration server is a web server that uses configuration templates and the device-specific configuration information stored in the embedded (standalone mode) or remote (server mode) directory.
Configuration templates are text files containing static configuration information in the form of CLI commands. In the templates, variables are specified using Lightweight Directory Access Protocol (LDAP) URLs that reference the device-specific configuration information stored in a directory.
The Cisco IOS agent can perform a syntax check on received configuration files and publish events to show the success or failure of the syntax check. The configuration agent can either apply configurations immediately or delay the application until receipt of a synchronization event from the configuration server.
Event Service
The Cisco Configuration Engine uses the Event Service for receipt and generation of configuration events. The event agent is on the switch and facilitates the communication between the switch and the event gateway on the Configuration Engine.
The Event Service is a highly capable publish-and-subscribe communication method. The Event Service uses subject-based addressing to send messages to their destinations. Subject-based addressing conventions define a simple, uniform namespace for messages and their destinations.
NameSpace Mapper
The Configuration Engine includes the NameSpace Mapper (NSM) that provides a lookup service for managing logical groups of devices based on application, device or group ID, and event.
Cisco IOS devices recognize only event subject-names that match those configured in Cisco IOS software; for example, cisco.cns.config.load. You can use the namespace mapping service to designate events by using any desired naming convention. When you have populated your data store with your subject names, NSM changes your event subject-name strings to those known by Cisco IOS.
For a subscriber, when given a unique device ID and event, the namespace mapping service returns a set of events to which to subscribe. Similarly, for a publisher, when given a unique group ID, device ID, and event, the mapping service returns a set of events on which to publish.
What You Should Know About the CNS IDs and Device Hostnames
The Configuration Engine assumes that a unique identifier is associated with each configured switch. This unique identifier can take on multiple synonyms, where each synonym is unique within a particular namespace. The event service uses namespace content for subject-based addressing of messages.
The Configuration Engine intersects two namespaces, one for the event bus and the other for the configuration server. Within the scope of the configuration server namespace, the term ConfigID is the unique identifier for a device. Within the scope of the event bus namespace, the term DeviceID is the CNS unique identifier for a device.
Because the Configuration Engine uses both the event bus and the configuration server to provide configurations to devices, you must define both ConfigID and Device ID for each configured switch.
Within the scope of a single instance of the configuration server, no two configured switches can share the same value for ConfigID. Within the scope of a single instance of the event bus, no two configured switches can share the same value for DeviceID.
ConfigID
Each configured switch has a unique ConfigID, which serves as the key into the Configuration Engine directory for the corresponding set of switch CLI attributes. The ConfigID defined on the switch must match the ConfigID for the corresponding switch definition on the Configuration Engine.
The ConfigID is fixed at startup time and cannot be changed until the device restarts, even if the switch hostname is reconfigured.
DeviceID
Each configured switch participating on the event bus has a unique DeviceID, which is analogous to the switch source address so that the switch can be targeted as a specific destination on the bus. All switches configured with the cns config partial global configuration command must access the event bus. Therefore, the DeviceID, as originated on the switch, must match the DeviceID of the corresponding switch definition in the Configuration Engine.
The origin of the DeviceID is defined by the Cisco IOS hostname of the switch. However, the DeviceID variable and its usage reside within the event gateway adjacent to the switch.
The logical Cisco IOS termination point on the event bus is embedded in the event gateway, which in turn functions as a proxy on behalf of the switch. The event gateway represents the switch and its corresponding DeviceID to the event bus.
The switch declares its hostname to the event gateway immediately after the successful connection to the event gateway. The event gateway couples the DeviceID value to the Cisco IOS hostname each time this connection is established. The event gateway caches this DeviceID value for the duration of its connection to the switch.
Hostname and DeviceID
The DeviceID is fixed at the time of the connection to the event gateway and does not change even when the switch hostname is reconfigured.
When changing the switch hostname on the switch, the only way to refresh the DeviceID is to break the connection between the switch and the event gateway. Enter the no cns event global configuration command followed by the cns event global configuration command.
When the connection is re-established, the switch sends its modified hostname to the event gateway. The event gateway redefines the DeviceID to the new value.

Using Hostname, DeviceID, and ConfigID
In standalone mode, when a hostname value is set for a switch, the configuration server uses the hostname as the DeviceID when an event is sent on hostname. If the hostname has not been set, the event is sent on the cn=< value > of the device.
In server mode, the hostname is not used. In this mode, the unique DeviceID attribute is always used for sending an event on the bus. If this attribute is not set, you cannot update the switch.
These and other associated attributes (tag value pairs) are set when you run Setup on the Configuration Engine.

Note![]() For more information about running the setup program on the Configuration Engine, see the Configuration Engine setup and configuration guide:
For more information about running the setup program on the Configuration Engine, see the Configuration Engine setup and configuration guide:
http://www.cisco.com/en/US/products/sw/netmgtsw/ps4617/prod_installation_guides_list.html
Understanding Cisco IOS Agents
The CNS event agent feature allows the switch to publish and subscribe to events on the event bus and works with the Cisco IOS agent. The Cisco IOS agent feature supports the switch by providing these features:
Initial Configuration
When the switch first comes up, it attempts to get an IP address by broadcasting a DHCP request on the network. Assuming there is no DHCP server on the subnet, the distribution switch acts as a DHCP relay agent and forwards the request to the DHCP server. Upon receiving the request, the DHCP server assigns an IP address to the new switch and includes the TFTP server IP address, the path to the bootstrap configuration file, and the default gateway IP address in a unicast reply to the DHCP relay agent. The DHCP relay agent forwards the reply to the switch.
The switch automatically configures the assigned IP address on interface VLAN 1 (the default) and downloads the bootstrap configuration file from the TFTP server. Upon successful download of the bootstrap configuration file, the switch loads the file in its running configuration.
The Cisco IOS agents initiate communication with the Configuration Engine by using the appropriate ConfigID and EventID. The Configuration Engine maps the Config ID to a template and downloads the full configuration file to the switch.
Figure 4-2 shows a sample network configuration for retrieving the initial bootstrap configuration file by using DHCP-based autoconfiguration.
Figure 4-2 Initial Configuration Overview
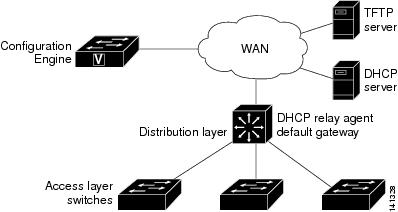
Incremental (Partial) Configuration
After the network is running, new services can be added by using the Cisco IOS agent. Incremental (partial) configurations can be sent to the switch. The actual configuration can be sent as an event payload by way of the event gateway (push operation) or as a signal event that triggers the switch to initiate a pull operation.
The switch can check the syntax of the configuration before applying it. If the syntax is correct, the switch applies the incremental configuration and publishes an event that signals success to the configuration server. If the switch does not apply the incremental configuration, it publishes an event showing an error status. When the switch has applied the incremental configuration, it can write it to NVRAM or wait until signaled to do so.
Synchronized Configuration
When the switch receives a configuration, it can defer application of the configuration upon receipt of a write-signal event. The write-signal event tells the switch not to save the updated configuration into its NVRAM. The switch uses the updated configuration as its running configuration. This ensures that the switch configuration is synchronized with other network activities before saving the configuration in NVRAM for use at the next reboot.
Configuring Cisco IOS Agents
The Cisco IOS agents embedded in the switch Cisco IOS software allow the switch to be connected and automatically configured as described in the “Enabling Automated CNS Configuration” section. If you want to change the configuration or install a custom configuration, see these sections for instructions:
Enabling Automated CNS Configuration
To enable automated CNS configuration of the switch, you must first complete the prerequisites in Table 4-1 . When you complete them, power on the switch. At the setup prompt, do nothing: The switch begins the initial configuration as described in the “Initial Configuration” section. When the full configuration file is loaded on your switch, you need to do nothing else.

Note![]() For more information about running the setup program and creating templates on the Configuration Engine, see the Cisco Configuration Engine Installation and Setup Guide, 1.5 for Linux:
For more information about running the setup program and creating templates on the Configuration Engine, see the Cisco Configuration Engine Installation and Setup Guide, 1.5 for Linux:
http://www.cisco.com/en/US/docs/net_mgmt/configuration_engine/1.5/installation_linux/guide/
setup_1.html
Enabling the CNS Event Agent

Note![]() You must enable the CNS event agent on the switch before you enable the CNS configuration agent.
You must enable the CNS event agent on the switch before you enable the CNS configuration agent.
Beginning in privileged EXEC mode, follow these steps to enable the CNS event agent on the switch:
To disable the CNS event agent, use the no cns event { ip-address | hostname } global configuration command.
This example shows how to enable the CNS event agent, set the IP address gateway to 10.180.1.27, set 120 seconds as the keepalive interval, and set 10 as the retry count.
Enabling the Cisco IOS CNS Agent
After enabling the CNS event agent, start the Cisco IOS CNS agent on the switch. You can enable the Cisco IOS agent with these commands:
- The cns config initial global configuration command enables the Cisco IOS agent and initiates an initial configuration on the switch.
- The cns config partial global configuration command enables the Cisco IOS agent and initiates a partial configuration on the switch. You can then use the Configuration Engine to remotely send incremental configurations to the switch.
Enabling an Initial Configuration
Beginning in privileged EXEC mode, follow these steps to enable the CNS configuration agent and initiate an initial configuration on the switch:
To disable the CNS Cisco IOS agent, use the no cns config initial { ip-address | hostname } global configuration command.
This example shows how to configure an initial configuration on a remote switch when the switch configuration is unknown (the CNS Zero Touch feature).
This example shows how to configure an initial configuration on a remote switch when the switch IP address is known. The Configuration Engine IP address is 172.28.129.22.
Enabling a Partial Configuration
Beginning in privileged EXEC mode, follow these steps to enable the Cisco IOS agent and to initiate a partial configuration on the switch:
To disable the Cisco IOS agent, use the no cns config partial { ip-address | hostname } global configuration command. To cancel a partial configuration, use the cns config cancel privileged EXEC command.
 Feedback
Feedback