About SPAN
SPAN analyzes all traffic between source ports by directing the SPAN session traffic to a destination port with an external analyzer attached to it.
You can define the sources and destinations to monitor in a SPAN session on the local device.
SPAN Sources
The interfaces from which traffic can be monitored are called SPAN sources. Sources designate the traffic to monitor and whether to copy ingress (Rx), egress (Tx), or both directions of traffic. SPAN sources include the following:
-
Ethernet ports (but not subinterfaces)
Characteristics of Source Ports
SPAN source ports have the following characteristics:
-
A port configured as a source port cannot also be configured as a destination port.
SPAN Destinations
SPAN destinations refer to the interfaces that monitor source ports. Destination ports receive the copied traffic from SPAN sources. SPAN destinations include the following:
-
Ethernet ports in either access or trunk mode
Characteristics of Destination Ports
SPAN destination ports have the following characteristics:
-
A port configured as a destination port cannot also be configured as a source port.
-
The same destination interface cannot be used for multiple SPAN sessions. However, an interface can act as a destination for a SPAN and an ERSPAN session.
-
Destination ports do not participate in any spanning tree instance. SPAN output includes bridge protocol data unit (BPDU) Spanning Tree Protocol hello packets.
SPAN Sessions
You can create SPAN sessions to designate sources and destinations to monitor.
See the Cisco Nexus 9000 Series NX-OS Verified Scalability Guide for information on the number of supported SPAN sessions.
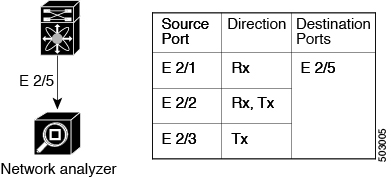
This figure shows a SPAN configuration. Packets on three Ethernet ports are copied to destination port Ethernet 2/5. Only traffic in the direction specified is copied.
Localized SPAN Sessions
A SPAN session is localized when all of the source interfaces are on the same line card. A session destination interface can be on any line card.
ACL TCAM Regions
You can change the size of the ACL ternary content addressable memory (TCAM) regions in the hardware. For information on the TCAM regions used by SPAN sessions, see the "Configuring IP ACLs" chapter of the Cisco Nexus 9000 Series NX-OS Security Configuration Guide.
High Availability
The SPAN feature supports stateless and stateful restarts. After a reboot or supervisor switchover, the running configuration is applied. For more information on high availability, see the Cisco Nexus 9000 Series NX-OS High Availability and Redundancy Guide.

 Feedback
Feedback