- Overview
- Installing Cisco Virtual Switch Update Manager
- Installing Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager
- Managing an Existing Cisco Nexus 1000V Switch
- Migrating Hosts to Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager
- Upgrading Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager
- Monitoring Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager
- Installing a License Using Cisco Virtual Switch Update Manager
- Dashboard-Cisco Nexus 1000V
Overview
This chapter contains the following sections:
- Information About the Cisco Virtual Switch Update Manager
- Information About Cisco Nexus 1000V
- Cisco Nexus 1000V Components
- Workflow for Installing Cisco Nexus 1000V
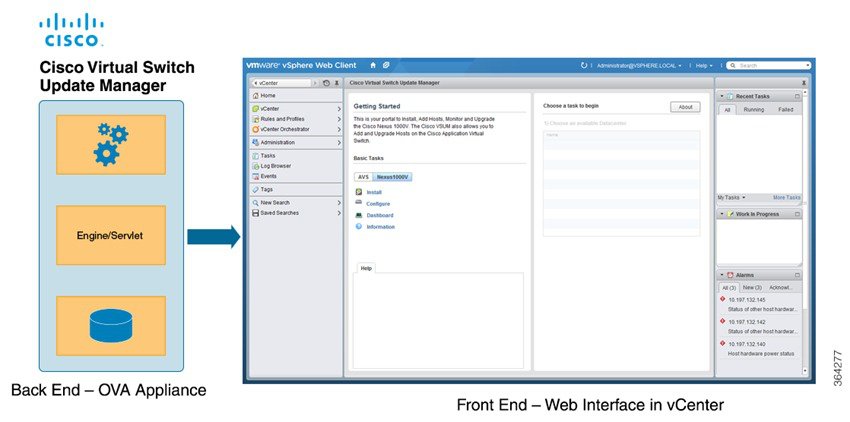
Information About the Cisco Virtual Switch Update Manager
Cisco Virtual Switch Update Manager enables you to install, upgrade, and monitor the Cisco Nexus 1000V for VMware vSphere and also migrate hosts to the Cisco Nexus 1000V, using the VMware vSphere Web Client .
Cisco Virtual Switch Update Manager enables you to do the following:
-
Install the Cisco Nexus 1000V switch.
-
Migrate the VMware vSwitch and VMware vSphere Distributed Switch (VDS) to the Cisco Nexus 1000V.
-
Monitor the Cisco Nexus 1000V.
-
Upgrade the Cisco Nexus 1000V and added hosts from an earlier version to the latest version.
-
Install the Cisco Nexus 1000V license.
-
View the health of the virtual machines in your datacenter using the Dashboard - Cisco Nexus 1000V.
Information About Cisco Nexus 1000V
The Cisco Nexus 1000V is a distributed virtual switch solution that is fully integrated within the VMware virtual infrastructure, including VMware vCenter, for the virtualization administrator. This solution offloads the configuration of the virtual switch and port groups to the network administrator to enforce a consistent data center network policy.
 Note | We recommend that you monitor and install the patch files for the VMware ESXi host software. |
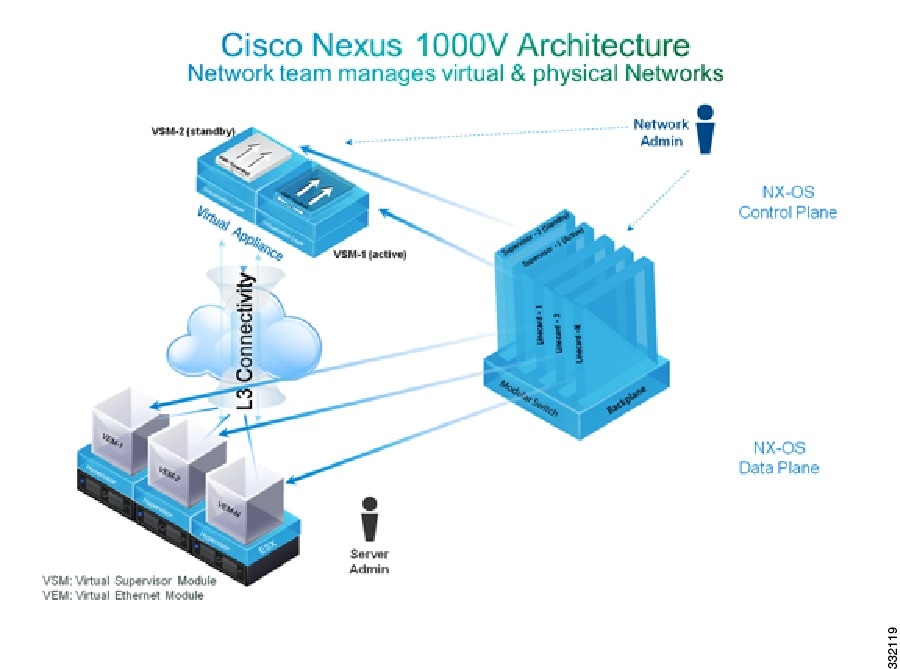
Cisco Nexus 1000V Components
The Cisco Nexus 1000V switch has the following components:
-
Virtual Supervisor Module (VSM)—The control plane of the switch and a VM that runs Cisco NX-OS.
-
Virtual Ethernet Module (VEM)—A virtual line card that is embedded in each VMware vSphere (ESXi) host. The VEM is partly inside the kernel of the hypervisor and partly in a user-world process, called the VEM Agent.
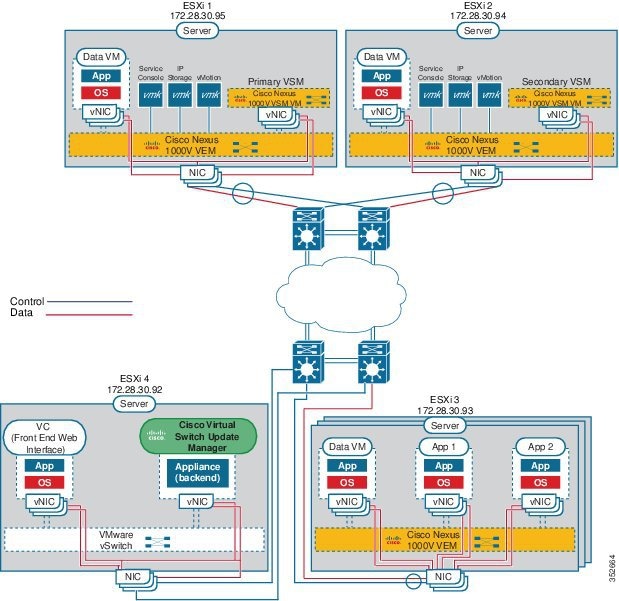
This figure shows the relationship between the VSM, VEMs and other Cisco Nexus 1000V components.
Layer 3 is the preferred method of communication between the VSM and the VEMs. This figure shows an example of a Layer 3 topology. The software for the primary VSM is installed on ESXi 1, and the software for the secondary VSM is installed on ESXi 2.
- Information About the Cisco Nexus 1000V Virtual Supervisor Module
- Information About the Virtual Ethernet Module
Information About the Cisco Nexus 1000V Virtual Supervisor Module
The Virtual Supervisor Module (VSM) is the control plane of the Cisco Nexus 1000V. It is deployed as a virtual machine.
You can install the VSM in either a standalone or active/standby high-availability (HA) pair. We recommend that you install two VSMs in an active-standby configuration for high availability.
VSM and VEM collectively represent the Cisco Nexus 1000V. The switch supports the following operations:
The VSM uses an external network fabric to communicate with the VEMs. The VSM runs the control plane protocols and configures the state of each VEM, but it never actually forwards packets. The physical NICs on the VEM server are the uplinks to the external fabric. VEMs switch traffic between the local virtual Ethernet ports that are connected to the VM vNICs but do not switch the traffic to other VEMs. Instead, a source VEM switches packets to the uplinks that the external fabric delivers to the target VEM.
A single Cisco Nexus 1000V instance, including dual-redundant VSMs and managed VEMs, forms a switch domain. Each Cisco Nexus 1000V domain within a VMware vCenter Server must be distinguished by a unique integer called the domain identifier.
See the Cisco Nexus 1000V Resource Availability Reference for information about scale limits.
The Cisco Nexus 1000V architecture is shown in this figure.
Information About the Virtual Ethernet Module
Each hypervisor is embedded with one VEM which replaces the virtual switch by performing the following functions:
-
Advanced networking and security
-
Switching between directly attached VMs
-
Uplinking to the rest of the network
 Note | Only one version of the VEM can be installed on an ESX/ESXi host at any given time. |
In the Cisco Nexus 1000V, the traffic is switched between VMs locally at each VEM instance. Each VEM also interconnects the local VM with the rest of the network through the upstream access-layer network switch (blade, top-of-rack, end-of-row, and so forth). The VSM runs the control plane protocols and configures the state of each VEM accordingly, but it never forwards packets.
In the Cisco Nexus 1000V, the module slots are for the primary module 1 and secondary module 2. Either module can act as active or standby. The first server or host is automatically assigned to module 3. The network interface card (NIC) ports are 3/1 and 3/2 (vmnic0 and vmnic1 on the ESX/ESXi host). The ports to which the virtual NIC interfaces connect are virtual ports on the Cisco Nexus 1000V where they are assigned with a global number.
Workflow for Installing Cisco Nexus 1000V
Installing Cisco Nexus 1000V using Cisco Virtual Switch Update Manager consists of the following steps:
| Step 1 | Installing Cisco Virtual Switch Update Manager. |
| Step 2 | Installing
Cisco Nexus 1000V
VSM.
See Installing the Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager. |
| Step 3 | Migrating hosts
to
Cisco Nexus 1000V.
See Migrating Hosts to the Cisco Nexus 1000V Using Cisco Virtual Switch Update Manager. |
 Feedback
Feedback