IPv4 Unicast Generic Routing Encapsulation Tunnel Overview
IPv4 unicast Generic Routing Encapsulation Tunnel (GRE) tunneling protocol provides a simple generic approach to transport packets of one protocol over another protocol by means of encapsulation. The term GRE tunnels in this document implies only unicast IPv4 GRE tunnel that supports IPv4 payload.
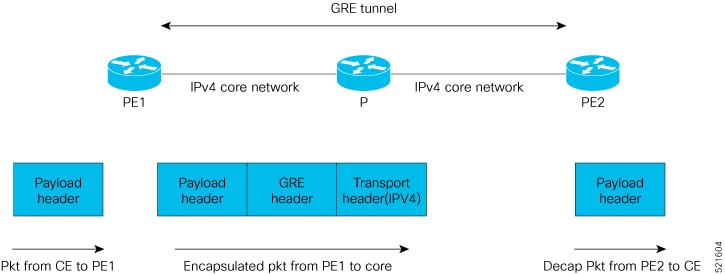
GRE encapsulates a payload, that is, an inner packet that needs to be delivered to a destination network inside an outer IP packet. GRE tunnel endpoints send payloads through GRE tunnels by routing encapsulated packets through intervening IP networks. Other IP routers along the way do not parse the payload (the inner packet); they only parse the outer IP packet as they forward it towards the GRE tunnel endpoint. Upon reaching the tunnel endpoint, GRE encapsulation is removed and the payload is forwarded to it’s ultimate destination.
Prior to Cisco IOS XE Gibraltar Release 16.12.x, GRE tunnels could provide a speed of 520 kbps for unidirectional and 250 kbps for bidirectional traffic. Starting with Cisco IOS XE Gibraltar Release 16.12.x, GRE tunnels enable the traffic to pass at a speed according to the size of the interface.
-
The unicast GRE tunnels work only with IPv4 as the transport protocol.
-
The payload protocol is of type IPv4.
IPv4 unicast GRE tunnels provide support to transport multiple protocols and packet types over the core network. More importantly, GRE tunnels can be used to form VPN networks by encapsulating the private addressing packets as payload with the tunnel header to transport the packet to the remote end. In the remote end, the packet is decapsulated and then routed based on private routing table. GRE tunnels can also carry multiple packet types such as unicast and multicast.
-
Payload packet or the passenger protocol
-
GRE header or the carrier protocol
-
Delivery header or the transport protocol

The following image shows a typical topology using GRE tunnel where IPv4 acts as both the transport protocol and the payload protocol.
Restrictions
-
Tunnel destination under VRF and command tunnel vrf is not supported. Tunnel destination prefix must be in global routing table for IPV4 unicast GRE to be functional.
-
Convergence lesser than 50 msec is not guaranteed.
-
Maximum supported GRE scale is 510.
-
Tunnel key is not supported. Hence, you must configure unique pair of source or destination IP address per tunnel.
-
ACL and QoS are not supported over GRE tunnel.
-
Time To Live (TTL) and Type of Service (TOS) are supported in Pipe mode.
-
Tunnel Interface Statistics is not supported.
-
Maximum Transmission Unit (MTU) is not supported for GRE tunnel and hence path MTU is also not supported.
-
Recursive routing is not supported as control plane support is not available.
-
Netflow and Policy-Based Routing (PBR) are not supported over the GRE tunnel.
-
GRE over Virtual Private LAN Services (VPLS) or PW is not supported.
-
GRE with indirection LB, Prefix Independent Convergence (PIC) core or PIC Edge, is not supported.
-
GRE over Traffic Engineering (TE) tunnel core (mid-chain pointing to mid-chain support) is not supported.
-
Equal-Cost Multi-Path Routing (ECMP or load balancing between GRE tunnels is not supported. But, when you can configure LB paths for a single GRE tunnel, the tunnel uses only one of the paths.
-
Bidirectional Forwarding Detection (BFD) over IPv4 unicast tunnel is not supported.
-
MPLS over GRE tunnel and GRE over MPLS are not supported.
-
GRE over MPLS core is supported provided explicit null command is disabled on the tunnel end routers.
-
GRE tunnel works with video, max-qos-video, and max-ipv4-tunnel templates only.
-
A maximum throughput of 70-75% line traffic can be achieved with GRE tunnel.
How to Configure IPv4 GRE Tunnel
-
Each IP address should be learned in global routing table.
-
The IPv4 GRE tunnel can be established using any routing protocols enabled between Provider Edge 1 (PE1) router and PE2 router.
-
Tunnel number should be identical in both the nodes.
Configure IPv4 Unicast Generic Routing Encapsulation Tunnel
configure terminal
interface tunnel101
ip vrf forwarding vrf name
ip address x.x.x.x x.x.x.x
tunnel source Loopback ip/int ip
tunnel Destination Loopback ip/int ip
Verification of IPv4 Unicast Generic Routing Encapsulation Tunnel Configuration
Use show interface tunnel101 command to verify IPv4 unicast GRE tunnel configuration.
PE1#show interface tunnel101
Tunnel1 is up, line protocol is up
Hardware is Tunnel
Internet address is 192.168.1.1/24
MTU 17916 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 2.2.2.2 (Loopback0), destination 3.3.3.3
Tunnel Subblocks:
src-track:
Tunnel1 source tracking subblock associated with Loopback0
Set of tunnels with source Loopback0, 1 member (includes iterators), on interface <OK>
Tunnel protocol/transport GRE/IP
Key disabled, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255, Fast tunneling enabled
Tunnel transport MTU 1476 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Last input 00:00:03, output 00:00:02, output hang never
Last clearing of "show interface" counters 20:25:52
Input queue: 0/375/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
19671 packets input, 1659853 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
19665 packets output, 1659405 bytes, 0 underruns
Output 0 broadcasts (0 IP multicasts)
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
 Feedback
Feedback