The device sensor is
used to gather raw endpoint data from network devices. The endpoint information
that is gathered helps in completing the profiling capability of devices.
Profiling is the determination of the endpoint type based on information
gleaned from various protocol packets from an endpoint during its connection to
a network.
The profiling
capability consists of two parts:
The device sensor
represents the embedded collector functionality. The illustration below shows
the Cisco sensor in the context of the profiling system and also features other
possible clients of the sensor.
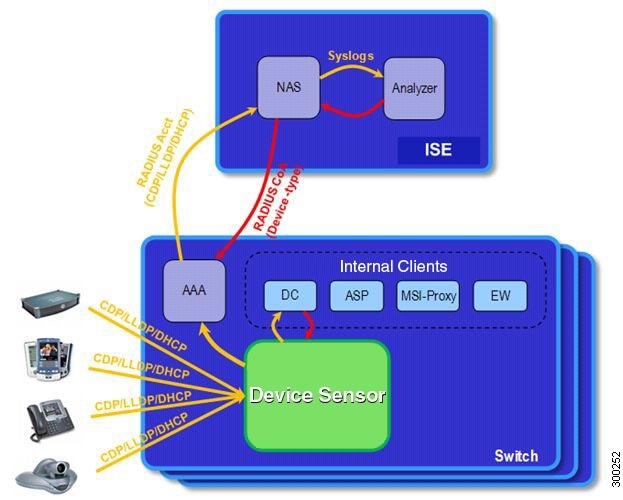
A device with sensor
capability gathers endpoint information from network devices using protocols
such as Cisco Discovery Protocol, LLDP, and DHCP, subject to statically
configured filters, and makes this information available to its registered
clients in the context of an access session. An access session represents an
endpoint’s connection to the network device.
The device sensor has
internal and external clients. The internal clients include components such as
the embedded Device Classifier (local analyzer), ATM switch processor (ASP),
MSI-Proxy, and EnergyWise (EW). The external client, that is the Identity
Services Engine (ISE) analyzer, will use RADIUS accounting to receive
additional endpoint data.
Client notifications
and accounting messages containing profiling data along with the session events
and other session-related data, such as the MAC address and the ingress port,
are generated and sent to the internal and external clients (ISE). By default,
for each supported peer protocol, client notifications and accounting events
are only generated where an incoming packet includes a TLV that has not
previously been received in the context of a given session. You can enable
client notifications and accounting events for all TLV changes, where either a
new TLV has been received or a previously received TLV has been received with a
different value using CLI commands.
The device sensor’s
port security protects the switch from consuming memory and crashing during
deliberate or unintentional denial-of-service (DoS) type attacks. The sensor
limits the maximum device monitoring sessions to 32 per port (access ports and
trunk ports). In case of lack of activity from hosts, the age session time is
12 hours.


 Feedback
Feedback