Testing Outbreak Filter URL Rewriting
Available Languages
Download Options
Bias-Free Language
The documentation set for this product strives to use bias-free language. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Exceptions may be present in the documentation due to language that is hardcoded in the user interfaces of the product software, language used based on RFP documentation, or language that is used by a referenced third-party product. Learn more about how Cisco is using Inclusive Language.
Contents
Introduction
This document describes how to test Outbreak Filters (OF) Message Modification option for URL Rewriting.
Background Information
If the message threat level exceeds the message modification threshold, the Outbreak Filters feature rewrites all URLs in the message to redirect the user to the Cisco web security proxy splash page if they click on any of them. AsyncOS rewrites all of the URLs inside a message except for the ones pointing to bypassed domains.
The following options are available for URL rewriting:
- Enable only for unsigned messages. This option allows AsyncOS to rewrite URLs in unsigned messages that meet or exceed the message modification threshold, but not signed messages. Cisco recommends using this setting for URL rewriting.
Note: The Email Security appliance may rewrite URLs in a DomainKeys/DKIM-signed message and invalidate the message signature if a server or appliance on your network other than the Email Security appliance is responsible for verifying the DomainKeys/DKIM signature. The appliance considers a message signed if it is encrypted using S/MIME or it contains an S/MIME signature.
-
The Email Security appliance may rewrite URLs in a DomainKeys/DKIM-signed message and invalidate the message signature if a server or appliance on your network other than the Email Security appliance is responsible for verifying the DomainKeys/DKIM signature.
The appliance considers a message signed if it is encrypted using S/MIME or it contains an S/MIME signature.
- Enable for all messages. This option allows AsyncOS to rewrite URLs in all messages that meet or exceed the message modification threshold, including signed ones. If AsyncOS modifies a signed message, the signature becomes invalid.
- Disable. This option disables URL rewriting for Outbreak Filters.
You can modify a policy to exclude URLs to certain domains from modification. To bypass domains, enter the IPv4 address, IPv6 address, CIDR range, hostname, partial hostname or domain in the Bypass Domain Scanning field. Separate multiple entries using commas.
The Bypass Domain Scanning feature is similar to, but independent of, the global Allowlist used by URL filtering. For more information about that Allowlist, see "Creating Whitelists for URL Filtering" in the ESA User Guide.
Testing Outbreak Filter URL Rewriting
There are two options to testing OF on ESA.
Testing OF Part One
Include a malicious URL in the email body. Safe test URL that can be used:
http://malware.testing.google.test/testing/malware/
When sent, mail logs example should contain similar to the following:
Tue Jul 3 09:31:38 2018 Info: MID 185843 Outbreak Filters: verdict positive
Tue Jul 3 09:31:38 2018 Info: MID 185843 Threat Level=5 Category=Malware Type=Malware
Tue Jul 3 09:31:38 2018 Info: MID 185843 rewritten URL u'http://malware.testing.google.test/testing/malware/'
Tue Jul 3 09:31:38 2018 Info: MID 185843 rewritten URL u'http://malware.testing.google.test/testing/malware/'
Tue Jul 3 09:31:38 2018 Info: MID 185843 rewritten URL u'http://malware.testing.google.test/testing/malware/'
Tue Jul 3 09:31:38 2018 Info: MID 185843 rewritten to MID 185844 by url-threat-protection filter 'Threat Protection'
Tue Jul 3 09:31:38 2018 Info: Message finished MID 185843 done
Tue Jul 3 09:31:38 2018 Info: MID 185844 Virus Threat Level=5
Tue Jul 3 09:31:38 2018 Warning: MID 185844 Failed to add disclaimer as header. Disclaimer has been added as attachment.
Tue Jul 3 09:31:38 2018 Info: MID 185844 rewritten to MID 185845 by add-heading filter 'Heading Stamping'
Tue Jul 3 09:31:38 2018 Info: Message finished MID 185844 done
Tue Jul 3 09:31:38 2018 Info: Message finished MID 185846 done
Tue Jul 3 09:31:38 2018 Info: MID 185845 enqueued for transfer to centralized quarantine "Outbreak" (Outbreak rule Malware: Malware)
Tue Jul 3 09:31:38 2018 Info: MID 185845 queued for delivery
Take note that the mail logs show us "rewritten URL", indicating OF has rewritten this URL through the Cisco web security proxy. Also, be aware that the message may be in the Outbreak Quarantine, as shown here in our example.
The final result will have the delivered email body showing the following:
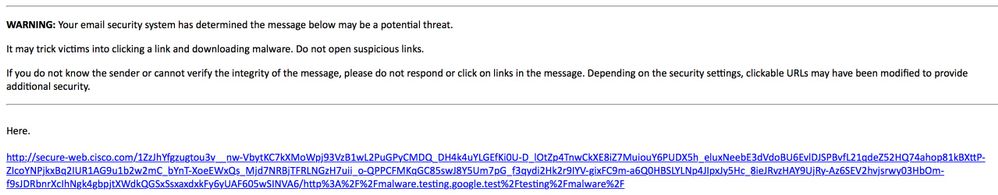
When the end-user now receives the email, clicks the rewritten URL, they are redirected to the Cisco web security proxy and see:
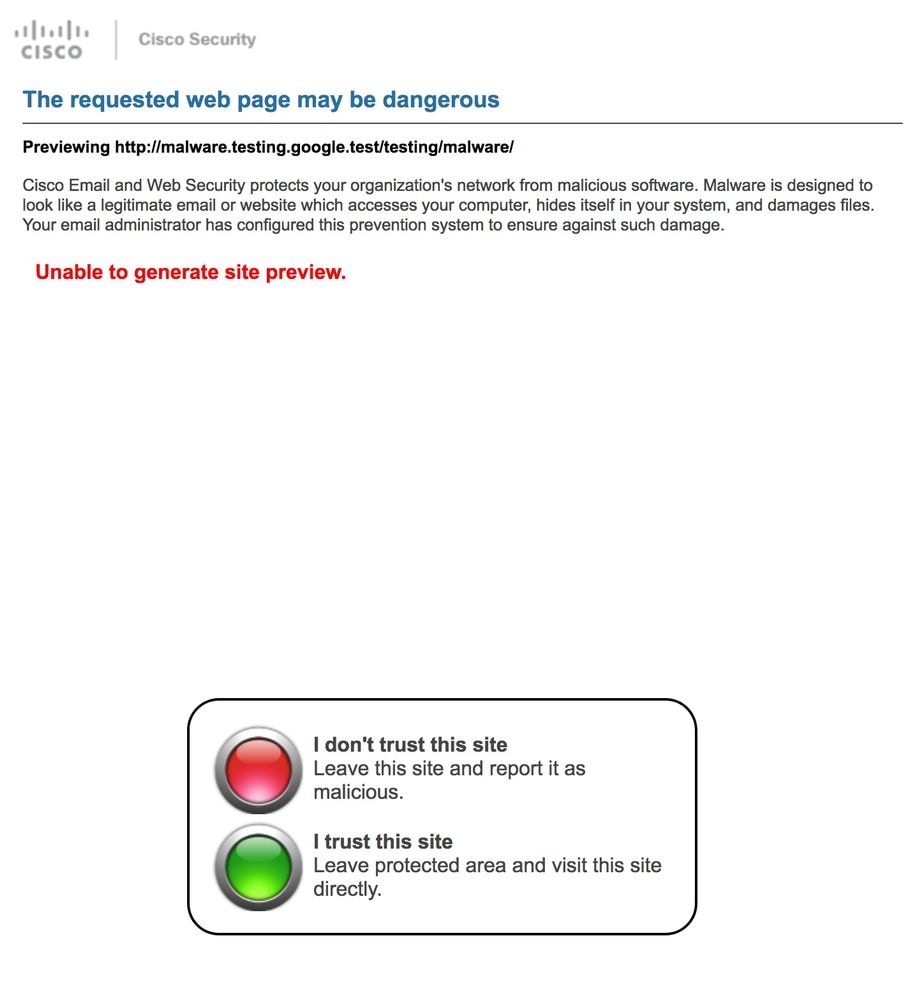
Note: "Unable to generate site preview" will be displayed based on the HTML/encoding of the original URL or website. A website with CSS, HTML panes, or complex rendering will not be able to generate a site preview.
Testing OF Part Two
The second option is to include data with-in the email body or attachment in order to have OF trigger.
There are two options in order to succeed:
- Create a file (simple text file will do) with the name "hello.voftest" between the size of 25000 and 30000 bytes, and attach that file to your test email. This will trigger the virus attachment rules.
- Place the following GTUBE ("Generic Test for Unsolicited Bulk Email") 72-byte test stringtext in the body of an email:
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTPHISH-STANDARD-ANTI-PHISH-TEST-EMAIL*C.34X
This will trigger OF and the phish rules. Mail logs example should contain similar to the following:
Tue Jul 3 09:44:12 2018 Info: MID 185880 Outbreak Filters: verdict positive
Tue Jul 3 09:44:12 2018 Info: MID 185880 Threat Level=5 Category=Phish Type=Phish
Tue Jul 3 09:44:12 2018 Info: MID 185880 rewritten URL u'https://www.simplesite.com/'
Tue Jul 3 09:44:12 2018 Info: MID 185880 rewritten URL u'https://www.simplesite.com/'
Tue Jul 3 09:44:12 2018 Info: MID 185880 rewritten URL u'https://www.simplesite.com/'
Tue Jul 3 09:44:12 2018 Info: MID 185880 rewritten to MID 185881 by url-threat-protection filter 'Threat Protection'
Tue Jul 3 09:44:12 2018 Info: Message finished MID 185880 done
Tue Jul 3 09:44:12 2018 Info: MID 185881 Virus Threat Level=5
Tue Jul 3 09:44:12 2018 Warning: MID 185881 Failed to add disclaimer as header. Disclaimer has been added as attachment.
Tue Jul 3 09:44:12 2018 Info: MID 185881 rewritten to MID 185882 by add-heading filter 'Heading Stamping'
Tue Jul 3 09:44:12 2018 Info: Message finished MID 185881 done
Tue Jul 3 09:44:13 2018 Info: MID 185882 enqueued for transfer to centralized quarantine "Outbreak" (Outbreak rule Phish: Phish)
Tue Jul 3 09:44:13 2018 Info: MID 185882 queued for delivery
Take note that the mail logs show us "rewritten URL", indicating OF has rewritten this URL through the Cisco web security proxy. Also, be aware that the message may be in the Outbreak Quarantine, as shown here in our example.
The final result will have the delivered email body showing the following:
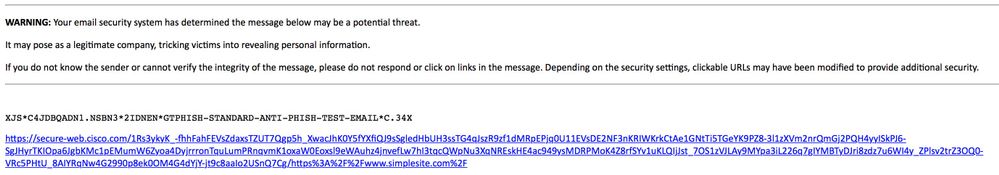
When the end-user now receives the email, clicks the rewritten URL, they are redirected to the Cisco web security proxy and see:
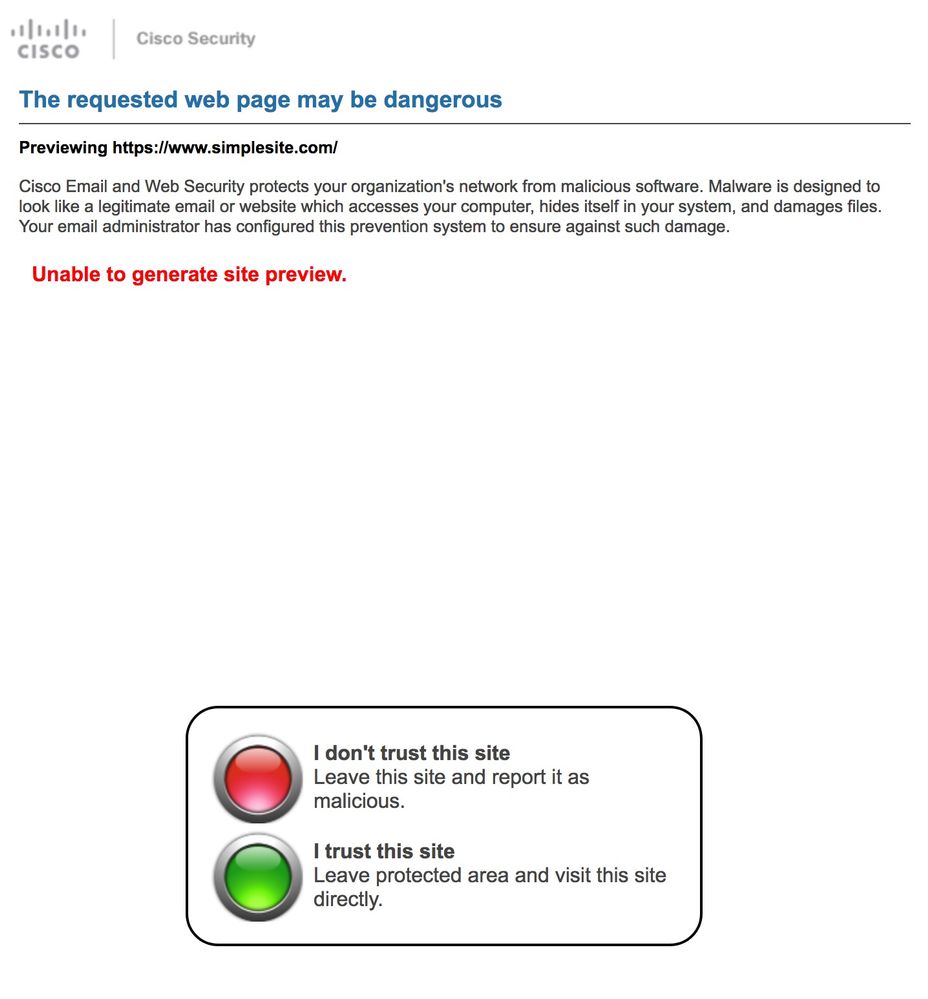
Note: "Unable to generate site preview" will be displayed based on the HTML/encoding of the original URL or website. A website with CSS, HTML panes, or complex rendering will not be able to generate a site preview.
Related Information
| Use: x-advertisement = outbreak |
Contributed by Cisco Engineers
- Robert SherwinCisco Email Security TME
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback