A modern, AI-enabled platform for advanced automation
Make your customers happier, reduce costs, and increase efficiency.
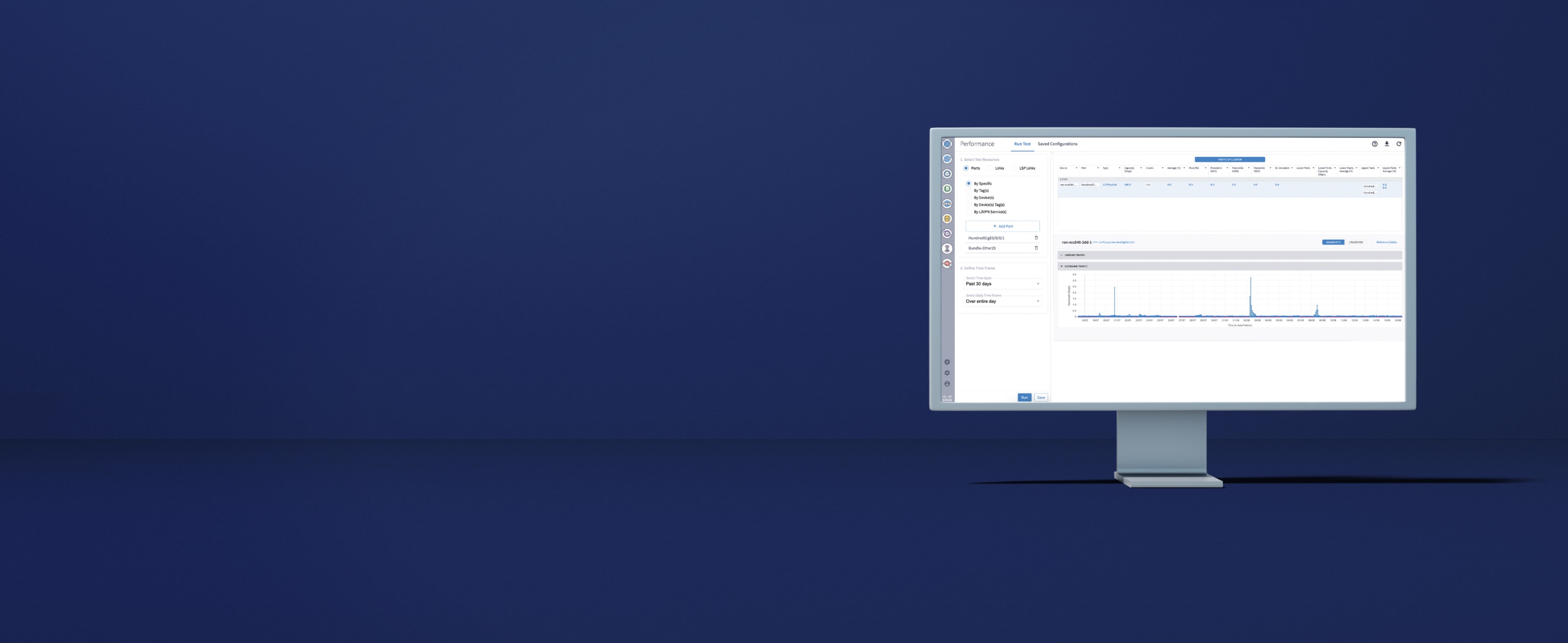
Accelerate efficiency with agentic AI
Get a multi-agentic framework and proactive AI capabilities with Cisco AI Assistant.
Toxic factor identification
Improve network reliability and cost efficiency with preventive AI agents that identify toxic network patterns and failure scenarios.
Configuration drift detection
Avoid outages and enhance service quality with AI agents that detect network configuration anomalies and deliver preventive insights.
Move quickly and precisely across dynamic environments
Software-defined and autonomous
Access actionable data, get programmatic network control, and drive towards zero-touch operations.
Scalable and adaptive
Adjust effortlessly to changes in size, volume, and cadence.
Multivendor, multidomain, cloud scale
Operate easily across technology boundaries and take advantage of SaaS and hybrid workflows.
See what customers have to say
Choose powerful solutions with proven ROI
Save on total cost of ownership
Explore Cisco Routed Optical Networking and the economic benefits of routed optical networks in DCI, metro, and long-haul applications.
Get potential benefits of $20.46 million
Learn how Cisco Crosswork Network Controller can simplify IP transport network management, lower operating expenses, and provide $20.46 million in annual benefits.