Navigate your network transformation
Take the first step by digitizing your cable access network and turn your analog systems into digital networks. Next, scale your digital network—growing bandwidth, services, and subscribers. And finally, intelligently interconnect your network and your services as a seamless system. Navigating your network's transformation is a comprehensive end-to-end journey and we can guide the way.
The building blocks for your network's transformation
Products and solutions for digitizing, scaling, and interconnecting your network.
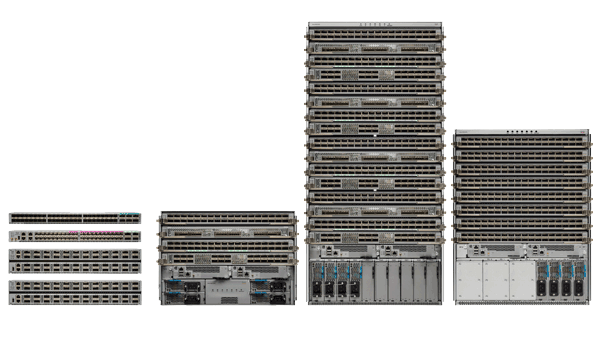
Cisco Remote PHY Shelves
- Small 1RU footprint
- Dual SFP+ ports per RPD
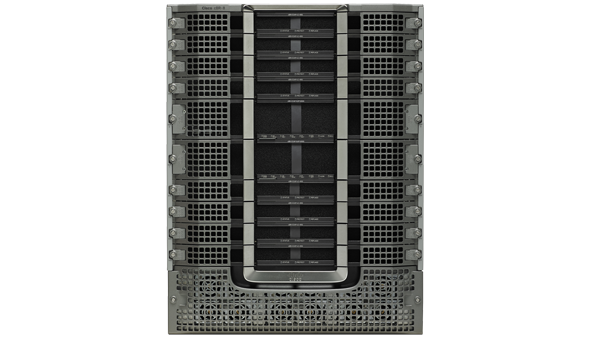
Cisco cBR-8
- Compact, high-capacity CCAP platform
- Highly available and resilient
- Remote PHY ready
Cisco NCS 5500 Series
- WAN aggregation solution
- High performance
- Scale up to 28-Tbps capacity
Cisco NCS 500 Series
- Highly scalable
- Zero-touch provisioning
- 5G ready
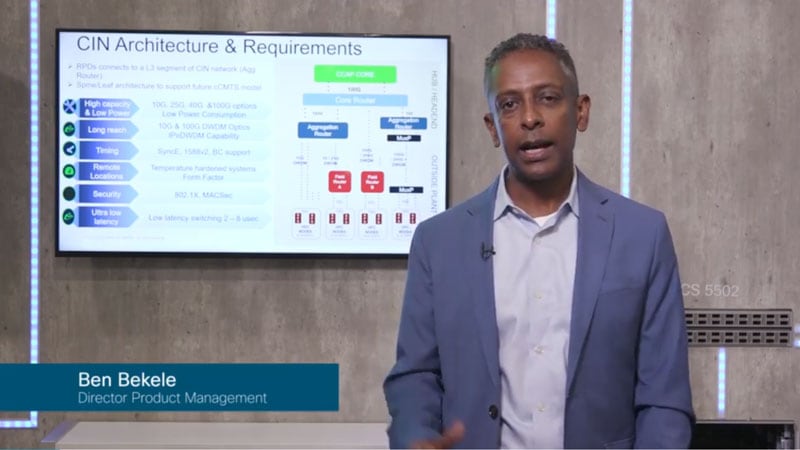
Cisco cable access in action
Network transformation comes one step at a time. First, digitize infrastructure. Next, virtualize at scale. Finally, intelligently interconnect everything.