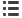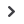
34
Cybersecurity in ASEAN: An Urgent Call to Action
Notes: HVA is high-value asset. NIST CF is the National Institute of Standards and Technology Cybersecurity Framework.
Source: A.T. Kearney analysis
Figure
De ine a cybersecurity strategy with a focus on four areas
•
Identify key business
drivers
•
Identify security
drivers that can assist in
accomplishing business
outcomes
•
Establish a working
deinition of high-value
information system assets
•
Establish a portfolio of
systems to be assessed
as HVAs
•
Analyze potential HVA
candidates to create a list
of recommended HVAs
for road-map planning
•
Review and validate the
HVA list to be used for
risk assessment
•
Establish primary threat
vectors facing HVAs
•
Establish a framework
for plotting the potential
risk and business impact
from cyber threats
•
For each identiied HVA:
–
Review against
industry’s common threats
–
Establish risk proile:
probability and impact
–
Prioritize the assets
into groups based on
the risk proile and
other criteria
•
Perform a cyber
health check
•
Assess capabilities by
HVA against NIST CF and
defense-in-depth model
•
Create a collective view
of current and planned
capability deployments
for coverage and gaps
•
Perform a gap analysis
of planned HVA initiatives
using the NIST CF
Align onbusiness
objectives
1
Identify
high-value
assets
2
Conduct cyber-
threat probability
and impact risk
assessment
3
Assess cyber
capabilities to
defendHVAs
4
•
Extend cyber resilience across the supply chain.
•
Forge public–private partnerships and industry alliances.
3.3.1 Foster a risk-centricmindset around cybersecurity for the corporate sector
The lack of a holistic approach around strategy, governance, organization, and culture often
results in organizations being highly vulnerable despite relying on the best vendors and products.
A four-step approach can help companies define their cybersecurity strategy (see figure 24).
Source: A.T. Kearney analysis
Figure
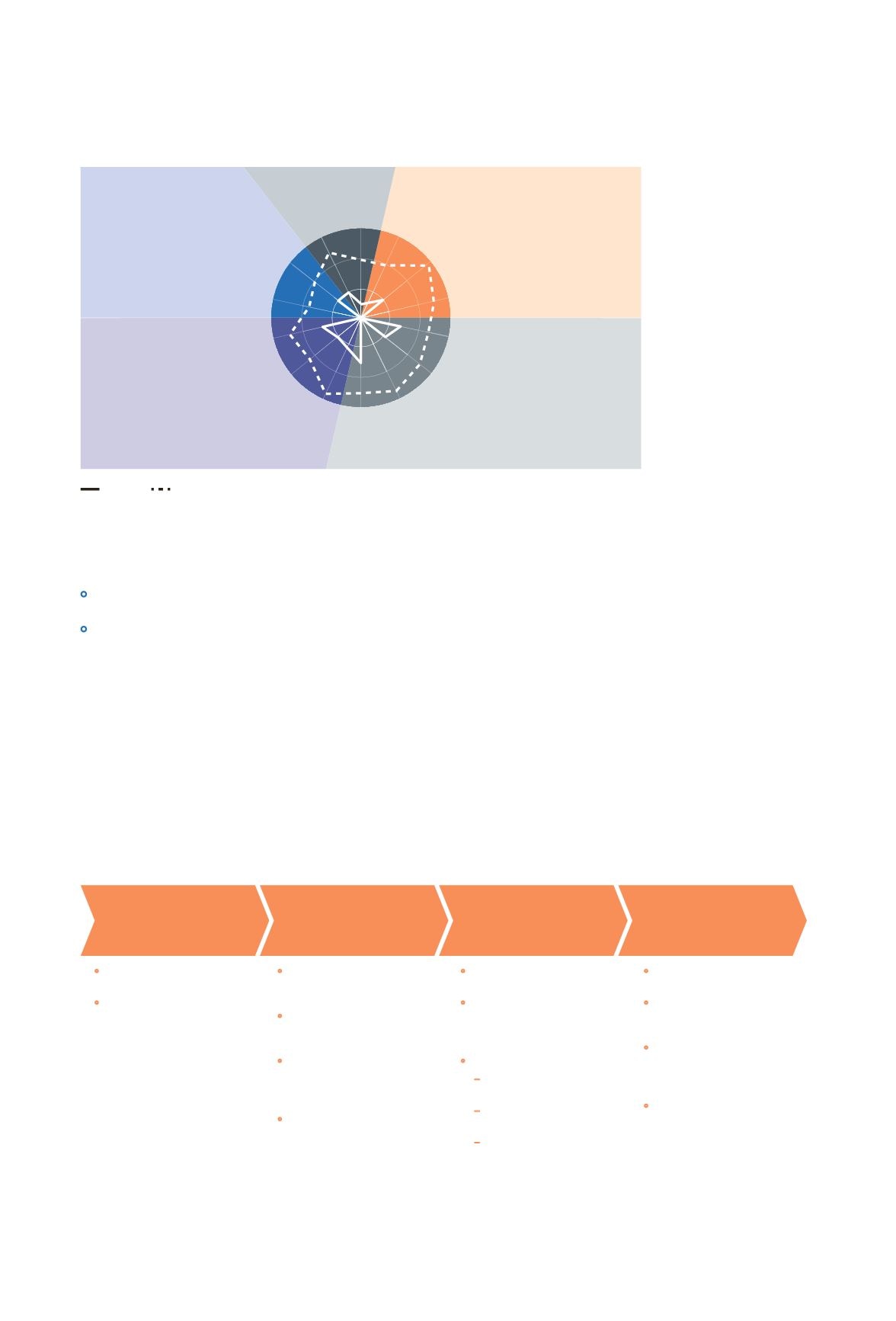
Deploy a cyber-hygiene dashboard
Strategy
Culture
Organization
Technology
Processes
Information security organization
External partners
Information security
management systems
Identity and access management
Operations
End points
Servers and applications
Network
Physical
protection
Cross-functionality
Management commitment
Awareness and behavior
Information security policy
Information
security strategy
As is
To be Center is “ignorant” level