Table Of Contents
Failover Configuration Commands
Upgrading from PIX Firewall Version 4.2(1) to the Current Version
Upgrading from PIX Firewall Version 4.1 to Version 4.2
Frequently Asked Failover Questions
Compiling Cisco Syslog MIB Files
Private Link to IPSec Conversion
Private Link Versus IPSec Commands
Advanced Configurations
This chapter includes the following sections:
•
SNMP
•
Private Link to IPSec Conversion
Failover
Failover lets you add a secondary PIX Firewall unit that takes control if the Primary unit fails.
This section includes the following topics:
•
This completes the upgrade procedure.
Understanding Failover
With version 5.0, you can choose the Stateful Failover option if you have 100 Mbps LAN interfaces so that connection states are automatically relayed between the two units.
Both units in a failover pair communicate through the failover cable, which is a modified RS-232 serial link cable that transfers data at 9600 baud. The data provides the unit identification of Primary or Secondary, the power status of the other unit, and serves as a communication link for various failover communications between the two units.
The two units send special failover "hello" packets to each other over all network interfaces and the failover cable every 15 seconds. The failover feature in PIX Firewall monitors failover communication, the power status of the other unit, and hello packets received at each interface. If two consecutive hello packets are not received within a time determined by the failover feature, failover starts testing the interfaces to determine which unit has failed, and transfers active control to the Standby unit.
When a failover occurs, each unit changes state. The newly Active unit assumes the IP and MAC addresses of the previously Active unit and begins accepting traffic. The new Standby unit assumes the failover IP and MAC addresses of the unit that was previously the Active unit. Because network devices see no change in these addresses, no ARP entries change or timeout anywhere on the network.
If you are using Stateful Failover, connection states are relayed from the Primary unit to the Secondary unit. Without Stateful Failover, the Standby unit does not maintain the state information of each connection. This means that all active connections will be dropped when failover occurs and that client systems must reestablish connections.
Stateful Failover
The Stateful Failover feature passes per-connection stateful information to the Standby unit. After a failover occurs, the same connection information is available at the new Active unit. End user applications are not required to do a reconnect to keep the same communication session. The state information passed to the Standby unit includes the global pool addresses and status, connection and translation information and status, the negotiated H.323 UDP ports, the port allocation bit map for PAT, and other details necessary to let the Standby unit take over processing if the Primary unit fails.
Depending on the failure, the PIX Firewall takes from 15 to 45 seconds to cause a switchover. Applications not handled by Stateful Failover will then require time to reconnect before the Active unit becomes fully functional.
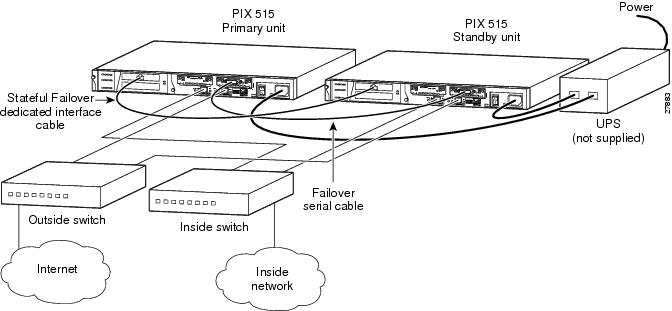
Stateful Failover requires 100 Mbps Ethernet interface to be used exclusively for passing state information between the two PIX Firewall units. This interface can be connected to any of the following:
•
Cat 5 crossover cable directly connecting the Primary unit to the Secondary unit.
•
100BaseTX half duplex hub using straight Cat 5 cables.
•
100BaseTX full duplex on a dedicated switch or dedicated VLAN of a switch.
PIX Firewall does not support use of either Token Ring or FDDI for the Stateful Failover dedicated interface. Data is passed over the dedicated interface using IP protocol 105. No hosts or routers should be on this interface.
shows two PIX Firewall units connected for use with Stateful Failover.
Figure 3-1 Stateful Failover Minimum Setup
Stateful Failover Summary
The following provides a summary of Stateful Failover features, configuration, and restrictions:
1
Feature description:
(a)
What causes a failover?
•
A power off or a power down condition on the Active PIX Firewall
•
Reboot of the Active PIX Firewall
•
A link goes down on the Active PIX Firewall for more than 30 seconds
•
"Failover active" on the Standby PIX Firewall
•
Block memory exhaustion for 15 consecutive seconds or more on the Active unit
(b)
What information is replicated to the Standby PIX Firewall?
•
The configuration
•
TCP (except HTTP) connection table including timeout information of each connection
•
Translation (xlate) table
•
System up time; that is, the system clock is synchronized on both PIX Firewall units
(c)
What information is not replicated to the Standby PIX Firewall:
•
The HTTP connection table
•
The user authentication (uauth) table
•
The ISAKMP and IPSec SA table
•
The ARP table
•
Routing information
2
Hardware requirements:
(a)
Two identical PIX Firewall units with a Fast Ethernet LAN port dedicated to Stateful Failover are required. You must connect the LAN ports for Stateful Failover on both PIX Firewall units with a crossover cable or through a hub or switch. Full duplex is required between the Stateful Failover ports.
(b)
For better performance, a PIX 520 or later model of PIX Firewall is recommended.
(c)
You need a failover cable to connect the two failover ports on both PIX Firewall units.
(d)
Hardware restrictions:
•
A PIX Firewall with two FDDI cards cannot use Stateful Failover because an additional Ethernet interface with FDDI is not supported
•
The failover cable must be installed and work correctly.
•
The dedicated Fast Ethernet ports on both PIX Firewall units must be connected and fully functional.
•
If you have six interfaces, one must be released from the network to be used as the dedicated Stateful Failover interface
3
Software requirements:
(a)
PIX Firewall version 5.0 or later is required for Stateful Failover.
(b)
Both PIX Firewall units have to run the same version of PIX Firewall software.
4
License requirements:
Stateful Failover requires a feature-based license key with failover feature support or connection based license key.
5
Commands for configuring Stateful Failover:
failover onfailover ip address if_name ip_addressfailover link if_nameConfiguring Failover
This section includes the following topics:
•
Failover Configuration Commands
Configuring Failover
To configure failover:
Step 1
If you have a PIX 515, obtain a PIX-515-UR feature license key that lets you add the failover option. Then purchase the failover option, which includes the Secondary unit. If you have a PIX 520 or older model, purchase a second unit with the same connection license as the Primary unit.
Step 2
Install the Secondary unit as described in the Installation Guide for the Cisco Secure PIX Firewall Version 5.0 available in your accessory kit. If you are using Stateful Failover, install both units on 100 Mbps full-duplex LAN interfaces.
Step 3
Connect the failover cable also described in the Installation Guide for the Cisco Secure PIX Firewall Version 5.0.
Step 4
Only configure the Primary unit. When you enter the write memory command to save the configuration to Flash memory, the Primary unit updates the Secondary unit.
The sections that follow describe how to configure the Primary unit.
Configuration Replication
The two PIX Firewall units must be configured exactly the same and running the same software release. Configuration replication occurs over the failover cable from the Active unit to the Standby unit in three ways:
•
When the Standby unit completes its initial bootup, the Active unit replicates its entire configuration to the Standby unit.
•
As commands are entered on the Active unit they are sent across the Failover Cable to the Standby unit.
•
By entering the write standby command on the Active unit, which forces the entire configuration in memory to be sent to the Standby unit.
The configuration replication only occurs from memory to memory. After replication, use the write memory command to write the configuration into Flash memory. Because the failover cable is used, the replication can take a long time to complete with a large configuration. If a switchover occurs during the replication, the new Active unit will have a partial configuration. The unit will reboot itself to recover the configuration from the Flash or re-synchronize with the other unit. When the replication starts, the PIX Firewall console displays the message "Sync Started," and when complete, displays the message "Sync Completed." During the replication, information cannot be entered on the PIX Firewall console.
Failover Configuration Commands
Note
Always enter configuration changes on the Active unit. Configuration changes entered on the Standby unit are not saved to the Active unit. Only use the default configuration initially to ensure both units are working correctly.
The following guidelines apply to configuring failover on the Active unit:
•
The unit that has the cable end labeled "primary" becomes the default Primary unit.
•
Configure a failover IP address for each interface on the Active unit using the ip address command. From the Active unit, configure a failover IP address for each interface on the Standby unit using the failover ip address command.
•
Use the failover command without an argument after you connect the optional failover cable between your primary firewall and a secondary firewall. The default is the failover off command.
•
Use the failover link command to enable Stateful Failover.
•
If you are not using the failover feature, enter the no failover command in the configuration file for the PIX Firewall if you will not be using the failover feature.
•
Use the failover timeout command to specify the length of time during which if a failover occurs, the Standby unit lets certain traffic through without requiring a prior xlate to exist.
•
Use the show failover command to verify the status of the connection and to determine which unit is active.
•
PIX Firewall configurations using failover require a separate IP address for each network interface on the Standby unit. The system IP address is the address of the Active unit. When the show ip address command is executed on the Active unit, the current IP address is the same as the system IP address. When the show ip address command is executed on the Standby unit, the system IP address is the failover IP address configured for the Standby unit.
•
Use the write standby command to manually save the configuration of the active failover unit to the standby failover unit from RAM to RAM.You can force an update by using the write standby command on the Active unit. If you make changes to the Standby unit, it displays a warning but does not update the Active unit.
•
To save the configuration of the Active unit to Flash memory (permanent memory) on the Standby unit, use the write memory command on the Active unit. The write memory command results are replicated on the Standby unit.
Use the show failover command to verify which unit is active and to provide Stateful Failover information.
If you want to force a PIX Firewall to be active or go to standby, you can use the failover active or no failover active command. Use this feature to force a PIX Firewall offline for maintenance or to return a failed unit to service.
Stateless TCP Failover
The failover timeout command lets you specify the length of time during which, if a failover occurs, the Standby unit lets connections started with the static command and the norandomseq option pass through the PIX Firewall without requiring a prior xlate to exist. This feature handles long-life connections during failover without requiring the connection to be reestablished.
The syntax for the failover command is:
failover timeout hh:mm:ss
If the hh:mm:ss is specified as -1, the length of time is indefinite.
AAA and user authentication connections are not supported by this feature.
When a stateless TCP connection is created, the following message is sent to syslog:
302009: Rebuilt TCP connection conn# for faddr foreign_ip/fport gaddr global_ip/gport laddr local_ip/lportUsage Notes
This section includes the following topics:
•
Upgrading from PIX Firewall Version 4.2(1) to the Current Version
•
Upgrading from PIX Firewall Version 4.1 to Version 4.2
Usage Notes
The following notes apply to the use of failover on the PIX Firewall:
1
Syslog messages indicate whether the Primary unit or Secondary unit failed. Refer to "Failover Syslog Messages" for more information.
2
If you are upgrading from a previous version, refer to "Upgrading from PIX Firewall Version 4.1 to Version 4.2" and "Upgrading from PIX Firewall Version 4.2(1) to the Current Version" before continuing.
3
The ACT indicator light on the front of the PIX 515 is on when the unit is the Active failover unit. If failover is not enabled, this light is on. If failover is present, the light is on when the unit is the Active unit and off when the unit is in standby mode.
4
The Cable Status that displays with the show failover command has these values:
(a)
Normal—Indicates that the Active unit is working and that the Standby unit is ready.
(b)
Waiting—Indicates that monitoring of the other unit's network interfaces has not yet started.
(c)
Failed—Indicates that the PIX Firewall has failed.
5
Changes made on the Standby unit are not replicated on the Active unit.
6
Failover works by passing control to the Standby unit should the Active unit fail. For Ethernet, failover detection should occur within 30 seconds. Token Ring requires additional time for failover.
7
Failover works in a switched environment. If the unit is attached to a switch running spanning tree, this will take twice the forward delay time configured in the switch (typically 15 seconds) plus 30 seconds. This is because at bootup (and immediately following a failover event) the network switch will detect a temporary bridge loop.
When this bridge loop is detected, the switch will stop forwarding packets for the duration of the forwarding delay time. It will then enter "listen" mode for an additional forward delay time during which time the switch is listening for bridge loops but still not forwarding traffic (and thus not forwarding failover hello packets). After twice the forward delay time (30 seconds) traffic should resume. The PIX Firewall will remain in "waiting" mode until it hears two hello packets (1 every 15 seconds for a total of 30 seconds). During this time the PIX Firewall passes traffic, and will not fail the unit if it does not hear the hello packets. All other failover monitoring is still occurring (power, interface, and failover cable hello).
8
Failover also works with the FDDI interface. Note that Port-B is on the top of the FDDI card, and Port-A is on the bottom.
9
The failover feature causes the PIX Firewall to ARP for itself every 15 seconds. If this adversely affects your ARP table, you can disable it with the no failover command.
10
If failover is disabled, the following messages display:
show failoverFailover OffCable Status: My side not connectedReconnect timeout: 0:00:00Upgrading from PIX Firewall Version 4.2(1) to the Current Version
Step 1
Connect a separate console to the Primary unit and one to the Secondary unit.
Step 2
Insert the PIX Firewall version 4.2 diskette into the Primary unit. Enter the reload command at the Primary unit.
Step 3
As the Primary unit reboots, PIX Firewall prompts you to write the diskette to Flash memory. Before entering a reply, read the next three substeps and be ready to move quickly to complete them. When ready, enter y for yes to write the diskette to Flash memory.
(a)
Immediately remove the diskette from the Primary unit and insert it into the Standby unit. Locate the reset button on the front of the Standby unit.
(b)
When the PIX Firewall Cisco banner appears on the console, press the reset button on the Standby unit to load the new image.
(c)
On the Primary unit, enter the show failover command and examine the output.
Step 4
On the Primary unit, observe the link lights on the network interface to determine that the unit is receiving traffic. Once the Standby unit completes its startup, the two units replicate the configuration. During the replication, the Primary console will not receive input.
Step 5
On the Standby unit, use the show failover command to monitor progress. When both PIX Firewall units report Normal, the replication is done.
Step 6
On each unit, enter the write memory command to store the new images in Flash memory.
This completes the upgrade procedure.
Upgrading from PIX Firewall Version 4.1 to Version 4.2
Step 1
Save the PIX Firewall version 4.1 configuration to a blank DOS-formatted diskette; write-protect, and label it.
Note
Keep the configuration diskette in a safe place. The PIX Firewall version 4.1 configuration is required if a downgrade is ever necessary.
Step 2
If failover is running, enter the no failover active command at the Primary unit.
Step 3
Remove the failover and network cables from the Standby unit. Do not remove the console cable.
Step 4
Insert the PIX Firewall version 4.2 diskette into the Standby unit and use the reload command to reboot the unit.
Step 5
After the Standby unit comes up, check the configuration and use the write memory command to store the configuration in Flash memory.
Step 6
Plug the failover and network cables into the Standby unit. Look for link lights on the network interface.
Step 7
On the Standby unit, enter the show interface command to ensure that traffic is moving through the PIX Firewall.
Step 8
Power off the Primary unit to force failover to the Standby unit.
Step 9
Enter the show conn command on the Standby unit to see if traffic is passing through the PIX Firewall.
Step 10
Disconnect the failover and network cables from the Primary unit which is now inactive.
Step 11
Insert the PIX Firewall version 4.2 diskette into the Primary unit.
Step 12
Check the configuration and use the write memory command to store the configuration in Flash memory.
Step 13
Plug in the failover and network cables. Look for link lights on the network interface.
Step 14
On the Primary unit, use the failover active command to restart failover.
Step 15
Enter the show conn command on the Primary unit to see if traffic is passing through the PIX Firewall.
This completes the upgrade procedure.
Failover Troubleshooting
This section includes the following topics:
•
Frequently Asked Failover Questions
After a Failover Occurs
If a failure is due to a condition other than a loss of power on the other unit, failover will begin a series of tests to determine which unit is failed. This series of tests will begin when hello messages are not heard for two consecutive 15-second intervals. Hello messages are sent over both network interfaces and the failover cable.
The purpose of these tests is to generate network traffic in order to determine which (if either) unit has failed. At the start of each test, each unit clears its received packet count for its interfaces. At the conclusion of each test, each unit looks to see if it has received any traffic. If it has, the interface is considered operational. If one unit receives traffic for a test and the other unit does not, the unit that received no traffic is considered failed. If neither unit has received traffic, then go to the next test.
Note
If the failover IP address has not been set, failover does not work and the Network Activity, ARP, and Broadcast ping tests are not performed.
Use the following tests for failover:
•
Link Up/Down test—This is a test of the NIC card itself. If an interface card is not plugged into an operational network, it is considered failed (for example, the hub or switch is failed, has a failed port, or a cable is unplugged).
•
Network Activity test—This is a received network activity test. The unit will count all received packets for up to 5 seconds. If any packets are received at any time during this interval, the interface is considered operational and testing stops. If no traffic is received, the ARP test begins.
•
ARP test—The ARP test consists of reading the unit's ARP cache for the 10 most recently acquired entries. One at a time the unit sends ARP requests to these machines attempting to stimulate network traffic. After each request the unit counts all received traffic for up to 5 seconds. If traffic is received, the interface is considered operational. If no traffic is received, an ARP request is sent to the next machine. If at the end of the list no traffic has been received, the ping test begins.
•
Broadcast Ping test—The ping test consists of sending out a broadcast ping request. The unit then counts all received packets for up to 5 seconds. If any packets are received at any time during this interval, the interface is considered operational and testing stops. If no traffic is received, the testing starts over again with the ARP test.
Frequently Asked Failover Questions
This section contains some frequently asked questions about the failover feature. Additional questions relating to installation are provided in the Installation Guide for the Cisco Secure PIX Firewall Version 5.0.
•
What happens when failover is triggered?
A switch can be initiated by either unit. When a switch takes place, each unit changes state. The newly Active unit assumes the IP address and MAC address of the previously Active unit and begins accepting traffic for it. The new Standby unit assumes the IP address and MAC address of the unit that was previously the Standby unit.
•
How is startup initialization accomplished between two units?
When a unit boots up, it defaults to Failover Off and Secondary, unless the failover cable is present or failover has been saved in the configuration. The configuration from the Active unit is also copied to the Standby unit. If the cable is not present, the unit automatically becomes the Active unit. If the cable is present, the unit that has the primary end of the failover cable plugged into it becomes the Primary unit by default.
•
How can both units be configured the same without manually entering the configuration twice?
Commands entered on the Active unit are automatically replicated on the Standby unit.
•
What happens if a Primary unit has a power failure?
When the Primary PIX Firewall unit experiences a power failure, the Standby PIX Firewall comes up in active mode. If the Primary unit is powered up again it will become the Standby unit.
•
What constitutes a failure?
Fault detection is based on the following:
•
Failover hello packets are received on each interface. If hello packets are not heard for two consecutive 15 second intervals, the interface will be tested to determine which unit is at fault.
•
Cable errors. The cable is wired so that each unit can distinguish between a power failure in the other unit, and an unplugged cable. If the Standby unit detects that the Active unit is turned off (or resets), it will take active control. If the cable is unplugged, a syslog is generated but no switching occurs. An exception to this is at bootup, at which point an unplugged cable will force the unit active. If both units are powered on without the failover cable installed they will both become active creating a duplicate IP address conflict on your network. The failover cable must be installed for failover to work correctly.
•
Failover communication. The two units share information every 15 seconds. If the Standby unit does not hear from the Active unit in two communication attempts (and the cable status is OK) the Standby unit will take over as active.
•
How long does it take to detect a failure?
•
Network errors are detected within 30 seconds (two consecutive 15-second intervals).
•
Power failure (and cable failure) is detected within 15 seconds.
•
Failover communications errors are detected within 30 seconds (two consecutive 15-second intervals).
•
What maintenance is required?
Syslog messages will be generated when any errors or switches occur. Evaluate the failed unit and fix or replace it.
Failover Syslog Messages
Failover messages always have a syslog priority level of 2, which indicates a critical condition. Refer to the logging command description in "," for more information on syslog messages. Refer to the System Log Messages for the Cisco Secure PIX Firewall Version 5.0, available online. PIX Firewall documentation is available online at:
http://www.cisco.com/univercd/cc/td/doc/product/iaabu/pix/index.htm
To receive SNMP syslog traps (SNMP failover traps), you must configure the SNMP agent to send SNMP traps to SNMP management stations, define a syslog host, and also have compiled the Cisco syslog MIB into your SNMP management station. See the snmp-server and logging command pages in "," for more information.
ActiveX Blocking
ActiveX controls, formerly known as OLE or OCX controls, are components you can insert in a web page or other application. These controls include custom forms, calendars, or any of the extensive third-party forms for gathering or displaying information. As a technology, ActiveX creates many potential problems for the network clients including causing workstations to fail, introducing network security problems, or being used to attack servers.
The PIX Firewall ActiveX feature blocks the HTML <object> commands by commenting them out within the HTML web page. This functionality has been added to the filter command with the activex option.
Note
The <object> tag is also used for Java applets, image files, and multimedia objects, which will also be blocked by the new command.
Note
If the <object> or </object> HTML tags split across network packets or if the code in the tags is longer than the number of bytes in the MTU, PIX Firewall cannot block the tag.
WebSENSE URL Filtering
If your network has a WebSENSE server on any network interface, you can provide URL filtering through the PIX Firewall.
To configure the PIX Firewall to use WebSENSE:
Step 1
Specify the interface and IP address of the WebSENSE server with the url-sever command as shown in this example:
url-server (dmz) host 192.168.1.42 timeout 10In this example, the WebSENSE host is on the dmz interface at IP address 192.168.1.42. A timeout value of 10 seconds is specified as maximum allowed idle time before the PIX Firewall switches to the next WebSENSE server.
Step 2
Use the filter url http command to tell the PIX Firewall how to filter requests. For example, to filter requests for all hosts, use:
filter url http 0 0 0 0 allow
Note
The allow option in the filter command is crucial to the use of PIX Firewall URL filtering feature. If you use the allow option and the WebSENSE server goes offline, the PIX Firewall lets all Web requests continue without filtering. If the allow option is not specified, all port 80 Web requests are stopped until the server is back online.
Step 3
If you want to disable URL filtering, use the no filter url command.
FTP and URL Logging
This section includes the following topics:
Logging FTP and URL Messages
You can log FTP commands and WWW URLs when syslog is enabled. FTP and URL messages are logged at syslog level 7. As of version 5.0, usernames are provided in the log information.
Refer to the section "Step 15 - Enable Syslog" in "," for more information on how to view syslog messages on a server, console session, or via Telnet to the console.
Use the show fixup command to ensure that the fixup protocol commands for FTP and HTTP are present in the configuration:
fixup protocol http 80fixup protocol ftp 21These commands are in the default configuration.
The sections that follow provide sample output displays for each logging type.
Sample URL Log
The following is an example of a URL logging syslog message:
192.168.69.71 accessed URL 10.0.0.1/secrets.gifSample FTP Log
The following are examples of FTP logging syslog messages:
192.168.69.42 Retrieved 10.0.0.42:feathers.tar192.168.42.54 Stored 10.0.42.69:privacy.zipYou can view these messages at the PIX Firewall console with the show logging command.
SNMP
The snmp-server command causes the PIX Firewall to send SNMP traps so that the firewall can be monitored remotely. Use snmp-server host command to specify which systems receive the SNMP traps.
This section includes the following topics:
•
Compiling Cisco Syslog MIB Files
Introduction
The PIX Firewall SNMP MIB-II groups available are System and Interfaces.
All SNMP values are read only (RO).
Using SNMP, you can monitor system events on the PIX Firewall. SNMP events can be read, but information on the PIX Firewall cannot be changed with SNMP.
The PIX Firewall SNMP traps available to an SNMP management station are:
•
Generic traps:
•
Link up and link down (cable on outside interface working or not working)
•
Cold start
•
Security-related events sent via the Cisco syslog MIB:
•
Global access denied
•
Failover syslog messages
•
syslog messages
Use CiscoWorks for Windows (Product Number CWPC-2.0-WIN) or any other SNMP V1, MIB-II compliant browser to receive SNMP traps and browse a MIB. SNMP traps occur at UDP port 162.
MIB Support
Note
The PIX Firewall does not support browsing of the Cisco syslog MIB.
You can browse the System and Interface groups of MIB-II. Browsing a MIB is different from sending traps. Browsing means doing an snmpget or snmpwalk of the MIB tree from the management station to determine values.
SNMP Traps
Traps are different than browsing; they are unsolicited "comments" from the managed device to the management station for certain events, such as link up, link down, syslog event generated, and so on.
An SNMP object ID (OID) for PIX Firewall displays in SNMP event traps sent from the PIX Firewall. OID 1.3.6.1.4.1.9.1.227 was assigned as the PIX Firewall system object ID.
Two mechanisms work with SNMP, PIX Firewall responds to an SNMP request from a management state and the PIX Firewall sends a trap, which is an event notification. PIX Firewall supports two types of traps, generic and syslog traps.
The topics that follow include:
Receiving Requests
For the PIX Firewall to receive requests from an SNMP management station:
Step 1
Identify the IP address of the SNMP management station with the snmp-server host command.
Step 2
Set the snmp-server options for location, contact, and the community password as required.
Sending Syslog Traps
To send traps from the PIX Firewall to an SNMP management station:
Step 1
If not performed already, configure both steps described in "Receiving Requests."
If you only want to send the cold start, link up, and link down generic traps, no further configuration is required.
Step 2
Add an snmp-server enable traps command statement.
Step 3
Set the logging level with the logging trap command; for example:
logging trap debuggingCisco recommends that you use the debugging level during initial set up and during testing. Thereafter, set the level from debugging to a lower value for production use.
Step 4
Start sending syslog traps to the management station with the logging on command.
Step 5
To disable sending syslog traps, use the no logging on command or the no snmp-server enable traps command.
Compiling Cisco Syslog MIB Files
To receive security and failover SNMP traps from the PIX Firewall, compile the Cisco SMI MIB and the Cisco syslog MIB into your SNMP management application. If you do not compile the Cisco syslog MIB into your application, you only receive MIB-II traps for link up or down, and firewall cold start.
You can get the Cisco MIB files on the Web from:
http://www.cisco.com/public/sw-center/netmgmt/cmtk/mibs.shtml
To compile Cisco syslog MIB files into your browser using CiscoWorks for Windows (SNMPc), complete the following steps:
Step 1
Get the Cisco syslog MIB files.
Step 2
Start SNMPc.
Step 3
Click Config>Compile MIB.
Step 4
Scroll to the bottom of the list, and click the last entry.
Step 5
Click Add.
Step 6
Find the file CISCO-SMI.my and click OK.
Step 7
Scroll to the bottom of the list, and click the last entry.
Step 8
Click Add again.
Step 9
Find the file CISCO-SYSLOG-MIB.my and click OK.
Step 10
Click Load All.
Step 11
If there are no errors, restart SNMPc.
These instructions are only for SNMPc (CiscoWorks for Windows).
Private Link to IPSec Conversion
This section is intended for the Private Link users who are migrating from the PIX Firewall Private Link feature to the IPSec feature. It describes the main differences between the Private Link commands and the corresponding IPSec commands and provides a procedure on how to convert a Private Link configuration into an IPSec configuration using IKE to establish security associations.
Private Link is no longer supported in the PIX Firewall starting with version 5.0. It is supported in version 4. The Private Link feature allows Virtual Private Networks (VPNs) to be established between PIX Firewall sites connected to the same public (or outside) network. It enables incoming Private Link packets to bypass the NAT and ASA features and terminate on the inside interface. With the use of the sysopt ipsec pl-compatible command, the IPSec feature simulates the Private Link feature by allowing IPSec packets to also bypass the NAT and ASA features and terminate on the inside interface. See the sysopt command page for more information regarding the sysopt ipsec pl-compatible command.
Note
Use of the sysopt ipsec pl-compatible command requires you to add a static route command statement for every host on every internal interface that needs access through the PIX Firewall for non-IPSec traffic. Without these static route command statements, adding the sysopt ipsec pl-compatible command to your configuration will stop all non-IPSec traffic through the PIX Firewall unit. (This restriction will be fixed in the next major release.)
Basic Difference
While IPSec is a much larger feature set than Private Link, the two feature sets do not have a complete parent-child inheritance relationship. The main difference between Private Link and IPSec is that a Private Link tunnel begins on the receiving interface and ends on the sending interface while an IPSec tunnel begins on the sending interface and terminates on the receiving interface.
Private Link Versus IPSec Commands
outlines the mapping of the core Private Link commands with the corresponding IPSec commands. A description of each command follows.
For more information about the IPSec related commands listed in , see "," under the following command pages:
Link
The link command creates an encrypted path between Private Link-equipped PIX Firewall units. This command also enables Private Link to associate the shared private keys between the local host with a remote peer. In IPSec, the isakmp key command enables the local host to associate a shared key with a remote peer.
Note
Private Link uses up to seven shared keys between two hosts and rotates among the seven keys. ISAKMP uses only one shared key between any two hosts to authenticate and dynamically negotiate other keys to protect the communication as necessary.
The link command allows for the configuration of per packet authentication protection. In IPSec, the analogous protection is provided by the transform-set combination of ah-md5-hmac or esp-md5-hmac. You configure a transform set using the crypto ipsec transform-set command.
Linkpath
The linkpath command identifies the internal and external network interfaces on the remote peer running Private Link. The linkpath address selectors are used to select inbound traffic at the inside interface to encrypt and tunnel to the remote peer. In the reverse direction, the linkpath address selectors are used to decrypt outbound traffic, which originated from the remote peer, at the inside interface.
In IPSec, the access-list address selectors in the crypto map are used to select outbound traffic from the interface to encrypt and tunnel to the remote peer. In the reverse direction, the access-list address selectors are used to decrypt inbound traffic, which originated from the remote peer, at the outside interface.
The following are the steps to use to convert from a linkpath tunnel into an IPSec tunnel. These steps are included within the Private Link to IPSec configuration conversion procedure.
Step 1
Define an access-list that has the same address selectors as your linkpath statement. (Step 7 in the conversion procedure.)
Step 2
Associate the defined access-list with a crypto map entry. (Step 8 in the conversion procedure.)
Step 3
Associate the linkpath remote peer as the crypto map peer. (Step 11 in the conversion procedure.)
Age
Private Link selects the next shared key in a "round-robin" method. The age command is used to define the number of minutes a current shared key is used before the rotation.
In IPSec, the crypto ipsec security-association lifetime second command is used to define how long the current shared key and the security association are used before their set time expires.
Conversion
Covered in this section are the steps to convert your Private Link configuration into an IPSec configuration. An example of a Private Link configuration between two PIX Firewalls is provided for reference.
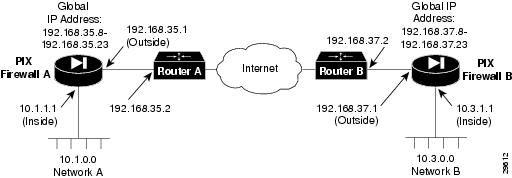
Figure 3-2 Example Private Link Network Diagram
shows the Private Link network diagram that corresponds to the following configurations.
On PIX Firewall A, the Private Link configuration is:
link 192.168.37.1 1 fadebacfadebaclink 192.168.37.1 2 bacfadefadebaclink 192.168.37.1 3 baabaaafadebaclink 192.168.37.1 4 beebeeefadebaclinkpath 10.3.0.0 255.255.255.0 192.168.37.1On PIX Firewall B, the Private Link configuration is:
link 192.168.35.1 1 fadebacfadebaclink 192.168.35.1 2 bacfadefadebaclink 192.168.35.1 3 baabaaafadebaclink 192.168.35.1 4 beebeeefadebaclinkpath 10.1.0.0 255.255.255.0 192.168.35.1In this configuration, the link command specifies 192.168.35.1 as the external network interface IP address of PIX Firewall B, and 192.168.37.1 as the external network interface IP address of PIX Firewall A. The key IDs are 1 through 4. The four keys to be shared between the two PIX firewall units are fadebacfadebac, bacfadefadebac, baabaaafadebac, and beebeeefadebac.
The linkpath command identifies the internal and external network interfaces belonging to the remote peer. So on the PIX Firewall A, PIX Firewall B's internal network interface IP address of 10.3.0.0 with a netmask of 255.255.255.0 and its external network interface IP address of 192.168.37.1 is set. On PIX Firewall B, PIX Firewall A's internal network interface IP address of 10.1.0.0 with a netmask of 255.255.255.0 and its external network interface IP address of 192.168.35.1 is set.
To convert your Private Link configuration into an IPSec configuration where IKE is used to establish security associations, perform the following steps. Perform your configuration on each PIX Firewall:
Step 1
Enable inside termination., For example:
PIX Firewall A:
sysopt ipsec pl-compatiblePIX Firewall B:
sysopt ipsec pl-compatibleStep 2
Explicitly list all routes. For example:
PIX Firewall A:
: connected routesroute inside 10.1.0.0 255.255.0.0 10.1.1.1route outside 192.168.35.0 255.255.255.0 192.168.35.1: nat routesroute inside 192.168.35.8 255.255.255.248 10.1.1.1route inside 192.168.35.16 255.255.255.248 10.1.1.1: reachability routesroute outside 10.3.0.0 255.255.0.0 192.168.35.2route outside 192.168.37.0 255.255.255.0 192.168.35.2route outside 0 0 192.168.35.2PIX Firewall B:
: connected routesroute inside 10.3.0.0 255.255.0.0 10.3.1.1route outside 192.168.37.0 255.255.255.0 192.168.37.1: nat routesroute inside 192.168.37.8 255.255.255.268 10.3.1.1route inside 192.168.37.16 255.255.255.268 10.3.1.1: reachability routesroute outside 10.1.0.0 255.255.0.0 192.168.37.2route outside 192.168.35.0 255.255.255.0 192.168.37.2route outside 0 0 192.168.37.2Step 3
Specify that a pre-shared key will be used between PIX Firewall A and PIX Firewall B for authentication:
PIX Firewall A:
isakmp policy 10 authentication pre-sharePIX Firewall B:
isakmp policy 10 authentication pre-shareStep 4
Specify a pre-shared key that PIX Firewall A and PIX Firewall B will share. For example:
PIX Firewall A:
isakmp key fadebacfadebac address 192.168.37.1PIX Firewall B:
isakmp key fadebacfadebac address 192.168.35.1Step 5
Define a crypto map entry that uses IKE to establish security associations. For example:
PIX Firewall A:
crypto map Firewall-A 10 ipsec-isakmpPIX Firewall B:
crypto map Firewall-B 10 ipsec-isakmpStep 6
Apply the crypto map set to the outside interface. For example:
PIX Firewall A:
crypto map Firewall-A interface outsidePIX Firewall B:
crypto map Firewall-B interface outsideStep 7
Create an access list to define the traffic to protect. Use the same address selectors used in your linkpath statement. For example:
PIX Firewall A:
access-list linkpath-aclA permit ip any 10.3.0.0 255.255.255.0PIX Firewall B:
access-list linkpath-aclB permit ip any 10.1.0.0 255.255.255.0Step 8
Assign the access list to the crypto map entry you defined. For example:
PIX Firewall A:
crypto map Firewall-A 10 match address linkpath-aclAPIX Firewall B:
crypto map Firewall-B 10 match address linkpath-aclBStep 9
Configure the transform set that defines how the traffic will be protected. Use either esp-des ah-md5-hmac or esp-md5-hmac. Either one provides the analogous Private Link standard encryption and authentication protection. For example:
PIX Firewall A:
crypto ipsec transform-set private-link-base esp-des ah-md5-hmacPIX Firewall B:
crypto ipsec transform-set private-link-base esp-des ah-md5-hmacStep 10
Specify the transform set to be used with the crypto map entry. For example:
PIX Firewall A:
crypto map Firewall-A 10 set transform-set private-link-basePIX Firewall B:
crypto map Firewall-B 10 set transform-set private-link-baseStep 11
Specify the remote peer to which the IPSec protected traffic can be forwarded. Specify the remote peer specified in your linkpath statement. For example:
PIX Firewall A:
crypto map Firewall-A 10 set peer 192.168.37.1PIX Firewall B:
crypto map Firewall-B 10 set peer 192.168.35.1Step 12
Apply the crypto map set to the outside interface. For example:
PIX Firewall A:
crypto map Firewall-A interface outsidePIX Firewall B:
crypto map Firewall-B interface outside

 Feedback
Feedback