botnet
--Slang term for a collection of software robots, or bots, which run autonomously or to a network of compromised “zombie”
computers running distributed programs, which are usually referred to as worms, Trojan horses, or backdoors, under a common
command and control infrastructure.
CPE
--Customer Premises Equipment. Terminating equipment, such as a router installed at a customer site, and connected to a WAN.
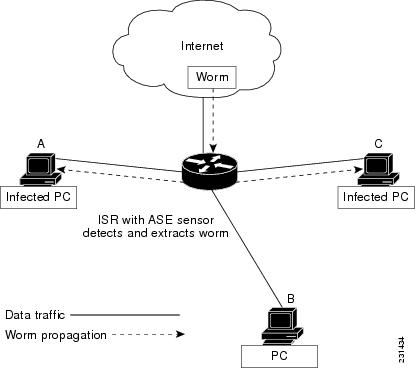
ISR
--Integrated Services Router. Router that supports integrated or multimedia services, including traffic management mechanisms.
malware
--Detrimental software designed to infiltrate or damage a computer system without the owner's informed consent. Examples of
malware include viruses, worms, botnets, spam, adware, etc.
signature
--The 40 bytes of packet data that can be used to identify a piece of malware.
TIDP
--Threat Information Distribution Protocol. Communication protocol used between the Linux-based Automatic Signature Extraction
collector and Cisco IOS-based ASE sensors.
TMS
--Threat Mitigation Service. TMS is used with the TIDP protocol to contain and mitigate the malware outbreak among TMS consumers
on a network.
Virus
--Hidden, self-replicating section of computer software, usually malicious logic, that propagates by infecting--that is, inserting
a copy of itself into and becoming part of--another program. A virus cannot run by itself; it requires that its host program
be run to make the virus active.
WAN
--wide-area network. Data communications network that serves users across a broad geographic area and often uses transmission
devices provided by common carriers. Frame Relay, SMDS, and X.25 are examples of WANs.
worm
--Computer program that can run independently, can propagate a complete working version of itself onto other hosts on a network,
and can consume computer resources destructively.
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone
numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown
for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and
coincidental.
© 2011 Cisco Systems, Inc. All rights reserved.

 Feedback
Feedback